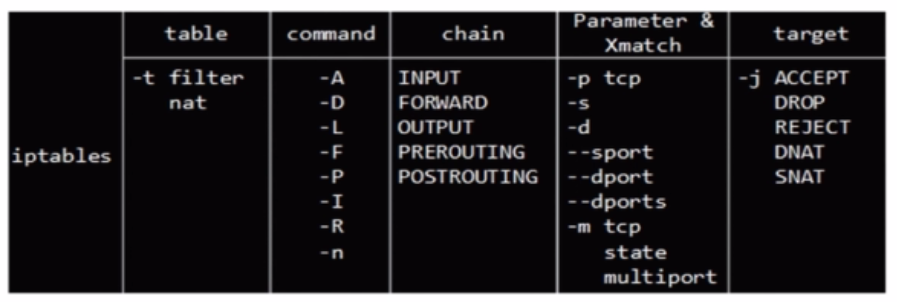
4张表:filter nat mangle raw
filter:协议过滤;
nat:地址转换,端口映射等;
mangle:协议修改 TTL等;
raw:This table is used mainly for configuring exemptions from connection tracking in combination with the NOTRACK target.
It registers at the netfilter hooks with higher priority and is thus called before ip_conntrack, or any other IP tables.
It provides the following built-in chains: PREROUTING (for packets arriving via any network interface) OUTPUT (for packets generated by local processes)
5条链:PREROUTING INPUT OUTPUT FORWARD POSTROUTING
PREROUTING:数据包进入路由表之前
INPUT:通过路由表后目的地为本机
FORWARDING:通过路由表后,目的地不为本机
OUTPUT:由本机产生,向外转发
POSTROUTIONG:发送到网卡接口之前。

数据包访问控制:ACCEPT DROP REJECT
数据包改写:SNAT DNAT
信息记录:LOG
COMMAND:
-A, --append chain rule-specification Append one or more rules to the end of the selected chain. When the source and/or destination names resolve to more than one address, a rule will be added for each possible address combination. -D, --delete chain rule-specification -D, --delete chain rulenum Delete one or more rules from the selected chain. There are two versions of this command: the rule can be specified as a number in the chain (starting at 1 for the first rule) or a rule to match. -I, --insert chain [rulenum] rule-specification Insert one or more rules in the selected chain as the given rule number. So, if the rule number is 1, the rule or rules are inserted at the head of the chain. This is also the default if no rule number is specified. -R, --replace chain rulenum rule-specification Replace a rule in the selected chain. If the source and/or destination names resolve to multiple addresses, the command will fail. Rules are numbered starting at 1. -L, --list [chain] List all rules in the selected chain. If no chain is selected, all chains are listed. Like every other iptables command, it applies to the specified table (filter is the default), so NAT rules get listed by iptables -t nat -n -L Please note that it is often used with the -n option, in order to avoid long reverse DNS lookups. It is legal to specify the -Z (zero) option as well, in which case the chain(s) will be atomically listed and zeroed. The exact output is affected by the other arguments given. The exact rules are suppressed until you use iptables -L -v -S, --list-rules [chain] Print all rules in the selected chain. If no chain is selected, all chains are printed like iptables-save. Like every other iptables command, it applies to the specified table (filter is the default). -F, --flush [chain] Flush the selected chain (all the chains in the table if none is given). This is equivalent to deleting all the rules one by one. -Z, --zero [chain [rulenum]] Zero the packet and byte counters in all chains, or only the given chain, or only the given rule in a chain. It is legal to specify the -L, --list (list) option as well, to see the counters immediately before they are cleared. (See above.) -N, --new-chain chain Create a new user-defined chain by the given name. There must be no target of that name already. -X, --delete-chain [chain] Delete the optional user-defined chain specified. There must be no references to the chain. If there are, you must delete or replace the referring rules before the chain can be deleted. The chain must be empty, i.e. not contain any rules. If no argument is given, it will attempt to delete every non-builtin chain in the table. -P, --policy chain target Set the policy for the chain to the given target. See the section TARGETS for the legal targets. Only built-in (non-user-defined) chains can have policies, and neither built-in nor user-defined chains can be policy targets. -E, --rename-chain old-chain new-chain Rename the user specified chain to the user supplied name. This is cosmetic, and has no effect on the structure of the table.
PARAMETERS
The following parameters make up a rule specification (as used in the add, delete, insert, replace and append commands).
[!] -p, --protocol protocol
The protocol of the rule or of the packet to check. The specified protocol can be one of tcp, udp, udplite, icmp, esp, ah, sctp or all, or it can be a numeric
value, representing one of these protocols or a different one. A protocol name from /etc/protocols is also allowed. A "!" argument before the protocol inverts
the test. The number zero is equivalent to all. Protocol all will match with all protocols and is taken as default when this option is omitted.
[!] -s, --source address[/mask][,...]
Source specification. Address can be either a network name, a hostname, a network IP address (with /mask), or a plain IP address. Hostnames will be resolved once
only, before the rule is submitted to the kernel. Please note that specifying any name to be resolved with a remote query such as DNS is a really bad idea. The
mask can be either a network mask or a plain number, specifying the number of 1’s at the left side of the network mask. Thus, a mask of 24 is equivalent to
255.255.255.0. A "!" argument before the address specification inverts the sense of the address. The flag --src is an alias for this option. Multiple addresses
can be specified, but this will expand to multiple rules (when adding with -A), or will cause multiple rules to be deleted (with -D).
[!] -d, --destination address[/mask][,...]
Destination specification. See the description of the -s (source) flag for a detailed description of the syntax. The flag --dst is an alias for this option.
-j, --jump target
This specifies the target of the rule; i.e., what to do if the packet matches it. The target can be a user-defined chain (other than the one this rule is in), one
of the special builtin targets which decide the fate of the packet immediately, or an extension (see EXTENSIONS below). If this option is omitted in a rule (and
-g is not used), then matching the rule will have no effect on the packet’s fate, but the counters on the rule will be incremented.
-g, --goto chain
This specifies that the processing should continue in a user specified chain. Unlike the --jump option return will not continue processing in this chain but
instead in the chain that called us via --jump.
[!] -i, --in-interface name
Name of an interface via which a packet was received (only for packets entering the INPUT, FORWARD and PREROUTING chains). When the "!" argument is used before
the interface name, the sense is inverted. If the interface name ends in a "+", then any interface which begins with this name will match. If this option is
omitted, any interface name will match.
[!] -o, --out-interface name
Name of an interface via which a packet is going to be sent (for packets entering the FORWARD, OUTPUT and POSTROUTING chains). When the "!" argument is used
before the interface name, the sense is inverted. If the interface name ends in a "+", then any interface which begins with this name will match. If this option
is omitted, any interface name will match.
[!] -f, --fragment
This means that the rule only refers to second and further fragments of fragmented packets. Since there is no way to tell the source or destination ports of such
a packet (or ICMP type), such a packet will not match any rules which specify them. When the "!" argument precedes the "-f" flag, the rule will only match head
fragments, or unfragmented packets.
-c, --set-counters packets bytes
This enables the administrator to initialize the packet and byte counters of a rule (during INSERT, APPEND, REPLACE operations).
| 分类 | 功能 | 作用链 |
| SNAT | 源地址转换 |
出口 POSTROUTING |
| DNAT | 目标地址转换 |
入口 PREROUTING |
Limit模块
作用:限速,控制流量
如:iptables -A INPUT-m limit --limit 4/hour
--limit-burst(初始的缓存区的大小)默认值为5
connlimit模块
作用:用于现在每一个客户端IP的并发连接数。
参数:--connlimit-above n #限制并发个数
例:iptables -I INPUT -p tcp --syn --dport 80 -m connlimit --connlimit-above 100 -j REJECT
参考:
http://www.imooc.com/video/7604/0
http://blog.itpub.net/312079/viewspace-245368/
http://linux.chinaunix.net/techdoc/net/2007/06/02/959143.shtml