Kubernetes dashboard是Kubernetes集群的基于Web的通用UI。它允许用户管理集群中运行的应用程序并对其进行故障排除,以及管理集群本身。
一、查看系统pod
[root@master69 kubernetes]# kubectl get pods -n kube-system -o wide NAME READY STATUS RESTARTS AGE IP NODE NOMINATED NODE READINESS GATES coredns-66bff467f8-7kbhf 1/1 Running 0 42h 10.244.8.164 redis-02.hlqxt <none> <none> coredns-66bff467f8-v6bw2 1/1 Running 0 42h 10.244.7.201 redis-01.hlqxt <none> <none> etcd-master69 1/1 Running 0 3d17h 172.28.18.69 master69 <none> <none> kube-apiserver-master69 1/1 Running 0 3d16h 172.28.18.69 master69 <none> <none> kube-controller-manager-master69 1/1 Running 1 3d17h 172.28.18.69 master69 <none> <none> kube-flannel-ds-5tthk 1/1 Running 0 41h 172.28.5.124 redis-02.hlqxt <none> <none> kube-flannel-ds-7mr6j 1/1 Running 0 41h 172.28.18.69 master69 <none> <none> kube-flannel-ds-9ml9m 1/1 Running 0 41h 172.28.5.120 redis-01.hlqxt <none> <none> kube-flannel-ds-ws8sc 1/1 Running 0 41h 172.28.5.125 redis-03.hlqxt <none> <none> kube-proxy-6pzzk 1/1 Running 0 41h 172.28.5.125 redis-03.hlqxt <none> <none> kube-proxy-99jjj 1/1 Running 1 41h 172.28.18.69 master69 <none> <none> kube-proxy-h7nl7 1/1 Running 0 41h 172.28.5.124 redis-02.hlqxt <none> <none> kube-proxy-lktgm 1/1 Running 0 41h 172.28.5.120 redis-01.hlqxt <none> <none> kube-scheduler-master69 1/1 Running 1 3d17h 172.28.18.69 master69 <none> <none>
二、下载recommended.yaml文件
[root@master69 kubernetes]# wget https://raw.githubusercontent.com/kubernetes/dashboard/v2.0.0/aio/deploy/recommended.yaml
三、修改recommended.yaml文件
修改service(nodeport)方式
[root@master69 kubernetes]# vim recommended.yaml
kind: Service apiVersion: v1 metadata: labels: k8s-app: kubernetes-dashboard name: kubernetes-dashboard namespace: kubernetes-dashboard spec:
type: NodePort #增加 ports: - port: 443 targetPort: 8443 nodePort: 31000 #增加 selector: k8s-app: kubernetes-dashboard
因为自动生成的证书很多浏览器无法使用,所以我们自己创建,注释掉kubernetes-dashboard-certs对象声明
#apiVersion: v1 #kind: Secret #metadata: # labels: # k8s-app: kubernetes-dashboard # name: kubernetes-dashboard-certs # namespace: kubernetes-dashboard #type: Opaque
四、创建证书
[root@master69 kubernetes]# mkdir /etc/kubernetes/dashboard-certs
[root@master69 kubernetes]# cd dashboard-certs/
1、创建namespace
[root@master69 dashboard-certs]# kubectl create namespace kubernetes-dashboard
2、创建私钥key文件
[root@master69 dashboard-certs]# openssl genrsa -out dashboard.key 2048 Generating RSA private key, 2048 bit long modulus .......+++ ...............................+++ e is 65537 (0x10001) [root@master69 dashboard-certs]# ll 总用量 4 -rw-r--r-- 1 root root 1675 1月 13 13:48 dashboard.key
3、使用openssl req 生成证书请求文件
生成证书请求文件需要将申请者的私钥以及公钥放入证书请求中,但在实际操作中,只需要提供私钥,openssl会自动从私钥中提取公钥另外,还需要将提供的数据进行数字签名(使用单向加密),保证该证书请求文件的完整性和一致性,防止他人盗取后进行篡改,例如黑客将为www.baidu.com所申请的证书请求文件中的公司名改成对方的公司名称,如果能够篡改成功,则签署该证书请求时,所颁发的证书信息中将变成他人信息。
根据私钥生成一个证书请求文件
[root@master69 dashboard-certs]# openssl req -days 36000 -new -out dashboard.csr -key dashboard.key -subj '/CN=dashboard-cert'
查看证书请求文件
[root@master69 dashboard-certs]# openssl req -in dashboard.csr -text
验证证书请求文件
[root@master69 dashboard-certs]# openssl req -verify -in dashboard.csr verify OK -----BEGIN CERTIFICATE REQUEST----- MIICXjCCAUYCAQAwGTEXMBUGA1UEAwwOZGFzaGJvYXJkLWNlcnQwggEiMA0GCSqG SIb3DQEBAQUAA4IBDwAwggEKAoIBAQDRK3gJoOGpB+cxJJNvE0dl4/6xZgVFS1Sq sx35t6dmiysf7Za+GwYWQbfHHXOjMvRMVSmBpodyQJirXUn0pnV+q2QIihOAub9f 8jsQO2e2uTSWKZ08OnAFqGaGQLMtzwHdsG1wqytVtA82afQsBkMK/rhACHxEwz8L jesfeUqHc5jO86rjxN/AI70ndFMhq66L9WJGVVh5AAvfttQJC2TmYMlAC/nQesBi L60TasrqB1NvyS0ko/VWAjqEIAeO93kEL2kx0GoOVwsddfI25POEsgTGjbAx+ir1 QLa8eyfl6nqrb/zKdQHVHBd/5Bsz/2ST2sbtsjqgDXoVY9NXV5AbAgMBAAGgADAN BgkqhkiG9w0BAQsFAAOCAQEAYisttfpJfmyrkKej6Cvxq9VaW2OwBPX8z31fECU1 sGi7nCgk97mYMUqkhuVG6VzEw6ddrVMn4yCxssmKX4cGP0yJ8WeqjzygVGY7GDRc HFucNqF2sljYHppSPgGWzxwCVGfq9RKc2bQPndY0FZbV97m2O5I5Rl81yz3NxEoO vlN3G6h5KahAvv6LmwCowDGoBkn7is892EMZHHyhm3qLCBvFDQTuy/xwKcbIIJc7 yS57125PxoJNf/d3Ay75d+ABtiRGCkX7BalcGvLbnoNQnhKy2+1FBxBT+yFOAHvx geBHvVxJP1rCCsu9yPnga6/mHpAfOLDQ+wQcPusO32xi7A== -----END CERTIFICATE REQUEST-----
4、自签证书
[root@master69 dashboard-certs]# openssl x509 -req -in dashboard.csr -signkey dashboard.key -out dashboard.crt -days 3650 Signature ok subject=/CN=dashboard-cert Getting Private key [root@master69 dashboard-certs]#
查看证书有效期
[root@master69 dashboard-certs]# openssl x509 -in dashboard.crt -noout -dates notBefore=Jan 13 06:47:32 2021 GMT notAfter=Jan 11 06:47:32 2031 GMT [root@master69 dashboard-certs]#
六、创建kubernetes-dashboard-certs对象
[root@master69 dashboard-certs]# kubectl create secret generic kubernetes-dashboard-certs --from-file=dashboard.key --from-file=dashboard.crt -n kubernetes-dashboard secret/kubernetes-dashboard-certs created
[root@master69 dashboard-certs]# kubectl get secrets -n kubernetes-dashboard NAME TYPE DATA AGE default-token-nnxdk kubernetes.io/service-account-token 3 65m kubernetes-dashboard-certs Opaque 2 22s
七、创建dashboard
[root@master69 kubernetes]# kubectl create -f recommended.yaml namespace/kubernetes-dashboard created serviceaccount/kubernetes-dashboard created service/kubernetes-dashboard created secret/kubernetes-dashboard-csrf created secret/kubernetes-dashboard-key-holder created configmap/kubernetes-dashboard-settings created role.rbac.authorization.k8s.io/kubernetes-dashboard created rolebinding.rbac.authorization.k8s.io/kubernetes-dashboard created deployment.apps/kubernetes-dashboard created service/dashboard-metrics-scraper created deployment.apps/dashboard-metrics-scraper created Error from server (AlreadyExists): error when creating "recommended.yaml": clusterroles.rbac.authorization.k8s.io "kubernetes-dashboard" already exists Error from server (AlreadyExists): error when creating "recommended.yaml": clusterrolebindings.rbac.authorization.k8s.io "kubernetes-dashboard" already exists
结尾的报错信息,是因为前面创建证书时,已经手动建立了namespace空间。
查看kubernetes-dashboard空间的资源
[root@master69 kubernetes]# kubectl get all -n kubernetes-dashboard NAME READY STATUS RESTARTS AGE pod/dashboard-metrics-scraper-6b4884c9d5-dzhdh 1/1 Running 0 5m29s pod/kubernetes-dashboard-7b544877d5-f9kg8 0/1 ContainerCreating 0 5m29s NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE service/dashboard-metrics-scraper ClusterIP 10.105.4.217 <none> 8000/TCP 5m29s service/kubernetes-dashboard NodePort 10.98.91.216 <none> 443:31000/TCP 5m29s NAME READY UP-TO-DATE AVAILABLE AGE deployment.apps/dashboard-metrics-scraper 1/1 1 1 5m29s deployment.apps/kubernetes-dashboard 0/1 1 0 5m29s NAME DESIRED CURRENT READY AGE replicaset.apps/dashboard-metrics-scraper-6b4884c9d5 1 1 1 5m29s replicaset.apps/kubernetes-dashboard-7b544877d5 1 1 0 5m29s [root@master69 kubernetes]#
八、创建dashboard管理员
1、创建dashboard-admin.yaml文件
[root@master69 kubernetes]# vim dashboard-admin.yaml
apiVersion: v1 kind: ServiceAccount metadata: labels: k8s-app: kubernetes-dashboard name: dashboard-admin namspace: kubernetes-dashboard
保存退出,创建用户
[root@master69 kubernetes]# kubectl create -f dashboard-admin.yaml serviceaccount/dashboard-admin created [root@master69 kubernetes]#
[root@master69 kubernetes]# kubectl get ServiceAccount -n kubernetes-dashboard NAME SECRETS AGE dashboard-admin 1 40s default 1 15m kubernetes-dashboard 1 15m
2、为用户分配权限
创建dashboard-admin-bind-cluster-role.yaml文件
[root@master69 kubernetes]# vim dashboard-admin-bind-cluster-role.yaml apiVersion: rbac.authorization.k8s.io/v1 kind: ClusterRoleBinding metadata: name: dashboard-admin-bind-cluster-role labels: k8s-app: kubernetes-dashboard roleRef: apiGroup: rbac.authorization.k8s.io kind: ClusterRole name: cluster-admin #绑定到cluster-admin角色 subjects: - kind: ServiceAccount name: dashboard-admin namespace: kubernetes-dashboard
执行分配权限
[root@master69 kubernetes]# kubectl create -f dashboard-admin-bind-cluster-role.yaml clusterrolebinding.rbac.authorization.k8s.io/dashboard-admin-bind-cluster-role created [root@master69 kubernetes]#
3、查看用户的token数据
首先查看kubernetes-admin用户的secret
[root@master69 kubernetes]# kubectl get secret -n kubernetes-dashboard -o wide|grep dashboard-admin dashboard-admin-token-znrr4 kubernetes.io/service-account-token 3 23m [root@master69 kubernetes]#
查看详细信息
[root@master69 kubernetes]# kubectl describe secret dashboard-admin-token-znrr4 -n kubernetes-dashboard Name: dashboard-admin-token-znrr4 Namespace: kubernetes-dashboard Labels: <none> Annotations: kubernetes.io/service-account.name: dashboard-admin kubernetes.io/service-account.uid: 24dd4aab-75fa-40dc-9d9b-851c4efa0c2d Type: kubernetes.io/service-account-token Data ==== token: eyJhbGciOiJSUzI1NiIsImtpZCI6ImktcWNVbUZtdkZ1VGxsbEJINld0ZW9YZzdua0JJRmNmNlhrR005eERDc00ifQ.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJrdWJlcm5ldGVzLWRhc2hib2FyZCIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VjcmV0Lm5hbWUiOiJkYXNoYm9hcmQtYWRtaW4tdG9rZW4tem5ycjQiLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC5uYW1lIjoiZGFzaGJvYXJkLWFkbWluIiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZXJ2aWNlLWFjY291bnQudWlkIjoiMjRkZDRhYWItNzVmYS00MGRjLTlkOWItODUxYzRlZmEwYzJkIiwic3ViIjoic3lzdGVtOnNlcnZpY2VhY2NvdW50Omt1YmVybmV0ZXMtZGFzaGJvYXJkOmRhc2hib2FyZC1hZG1pbiJ9.WaDgJJmVIUy78-YhBqDojhpG_swWUksa9bbxOHdyHX3bEitB1ccttEhD-CwonMcNPH1R0rdx5QJTZIKeKlYbIqJ_eJ7dtfKE-DO-pxnbd6JpeyKW9nIcVs5iCFgyL_rFVEiuYYgEVu-CRaIVaqb0zQCmzQPaeTiy_vzS0QCUHj4TYvpmZWclyE_BruuH57BS24-n2EA0iyvbHDwfb-t5aS87c9nhCeZ1XIPYVE8hF_nbKvbGdzd5PGUvvjV-5a2Q-SHFIau7JZFb2DenopnDlzMhPt_S_vrEOXJujCfeEV_28ovCvfgSZo1ITSRbeRkVHxoxs3O41Dd1RZ93gERtfg ca.crt: 1025 bytes namespace: 20 bytes [root@master69 kubernetes]#
将token值复制出来
九、浏览器打开https://masterip:31000
输入token,登录
我们查看工作量-pods
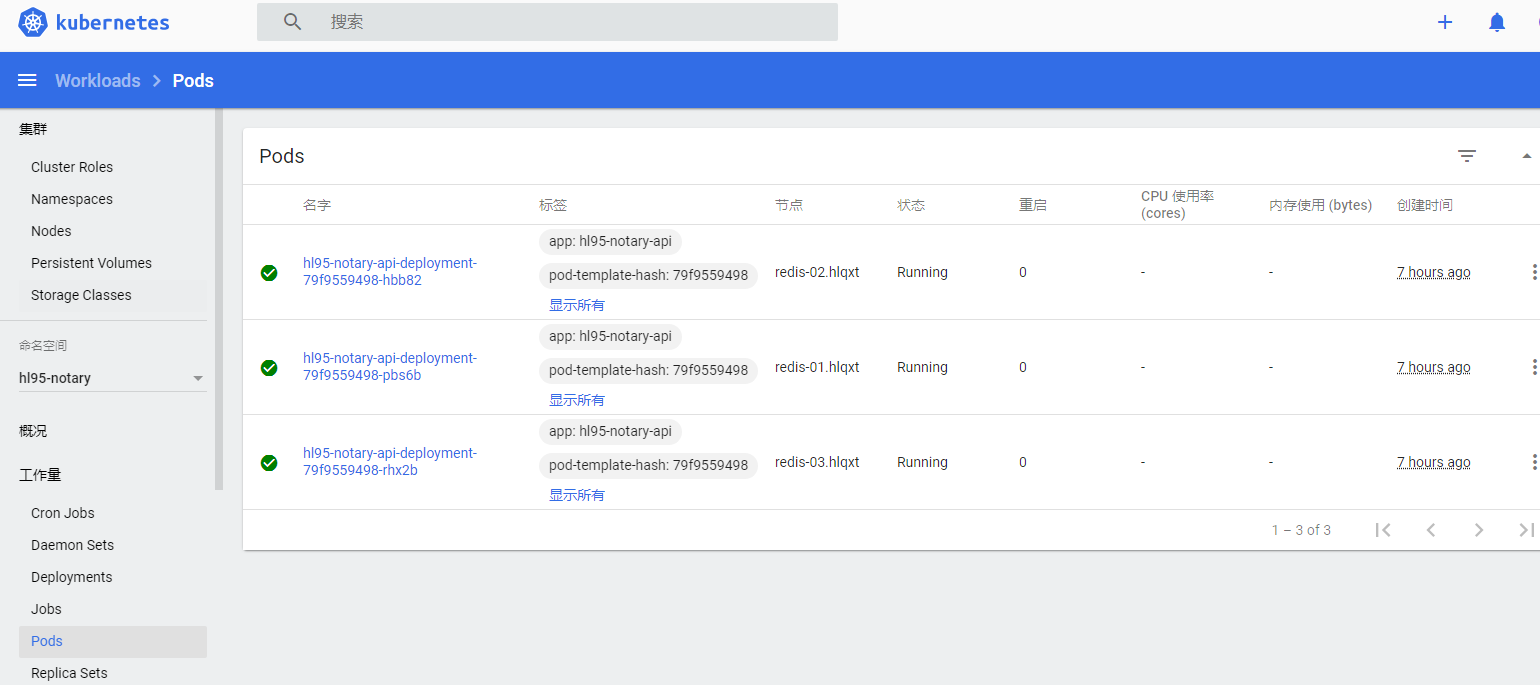
CPU和内存使用率没有显示,因为我们还没有安装Metrics-Server服务,请参考: kubernetes1.18安装metrics-server服务
安装以后,显示如下