kuberbetes的web界面
官方文档:https://kubernetes.io/docs/tasks/access-application-cluster/web-ui-dashboard/
安装方式也是执行下yaml文件即可,按照官方默认的文件安装后需要在需要在客户机上执行 kubetcl proxy 命令后才可以访问
这里采用的是nodeport的方式,kubernetes版本V1.17
- 下载配置文件
下载文件 # wget https://raw.githubusercontent.com/kubernetes/dashboard/v2.0.0-beta8/aio/deploy/recommended.yaml
- 修改配置
kind: Service apiVersion: v1 metadata: labels: k8s-app: kubernetes-dashboard name: kubernetes-dashboard namespace: kubernetes-dashboard spec: type: NodePort ###增加类型 ports: - port: 443 targetPort: 8443 nodePort: 32567 ###增加端口
selector: k8s-app: kubernetes-dashboard
- 生成svc
kubectl apply -f recommended.yaml
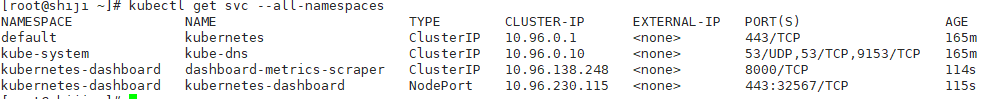
#安装成功后可以查看service状态
kubectl get svc --all-namespaces
- 因为证书过期的问题,这里只能使用firefox浏览器访问,重新生成证书,参考文档 https://www.cnblogs.com/panwenbin-logs/p/10052554.html
# cd /etc/kubernetes/pki/ # (umask 077; openssl genrsa -out dashboard.key 2048) #创建一个证书 Generating RSA private key, 2048 bit long modulus ............................................................................................+++ .............+++ e is 65537 (0x10001) # openssl req -new -key dashboard.key -out dashboard.csr -subj "/O=qiangungun/CN=kubernetes-dashboard" #建立证书的签署请求 # openssl x509 -req -in dashboard.csr -CA ca.crt -CAkey ca.key -CAcreateserial -out dashboard.crt -days 3650 #使用集群的ca来签署证书 Signature ok subject=/O=qiangungun/CN=kubernetes-dashboard Getting CA Private Key # kubectl create secret generic kubernetes-dashboard-certs --from-file=dashboard.crt=./dashboard.crt --from-file=dashboard.key=./dashboard.key -n kubernetes-dashboard #我们需要把我们创建的证书创建为secret给k8s使用,这里注意更改名称空间 secret "kubernetes-dashboard-certs" created
- 创建管理用户(为了保护群集数据,默认情况下,Dashboard会使用最少的RBAC配置进行部署。当前,仪表板仅支持使用Bearer令牌登录。),https://github.com/kubernetes/dashboard/blob/master/docs/user/access-control/creating-sample-user.md
# vim user.yaml ####编辑yaml文件
apiVersion: v1 kind: ServiceAccount metadata: name: admin-user namespace: kubernetes-dashboard --- apiVersion: rbac.authorization.k8s.io/v1 kind: ClusterRoleBinding metadata: name: admin-user roleRef: apiGroup: rbac.authorization.k8s.io kind: ClusterRole name: cluster-admin subjects: - kind: ServiceAccount name: admin-user namespace: kubernetes-dashboard
- kubectl apply -f user.yaml
- kubectl -n kubernetes-dashboard describe secret $(kubectl -n kubernetes-dashboard get secret | grep admin-user | awk '{print $1}') ###执行命令显示登录的token
Name: admin-user-token-pzcfj Namespace: kubernetes-dashboard Labels: <none> Annotations: kubernetes.io/service-account.name: admin-user kubernetes.io/service-account.uid: 266dab12-3ab6-4fec-b068-c01d3ffcbb02 Type: kubernetes.io/service-account-token Data ==== token: eyJhbGciOiJSUzI1NiIsImtpZCI6Ilgtb0hyNlpLSHd1TEpTVGVWR25MckJtcVFqVGJyTG5idnprTktkT3d0cUUifQ.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJrdWJlcm5ldGVzLWRhc2hib2FyZCIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VjcmV0Lm5hbWUiOiJhZG1pbi11c2VyLXRva2VuLXB6Y2ZqIiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZXJ2aWNlLWFjY291bnQubmFtZSI6ImFkbWluLXVzZXIiLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC51aWQiOiIyNjZkYWIxMi0zYWI2LTRmZWMtYjA2OC1jMDFkM2ZmY2JiMDIiLCJzdWIiOiJzeXN0ZW06c2VydmljZWFjY291bnQ6a3ViZXJuZXRlcy1kYXNoYm9hcmQ6YWRtaW4tdXNlciJ9.L-VrFuN5tX6Xnmj1tROk-lBwlYkmLFP8nCXMyqBwsD48ChN3YaZFsaKVlR_tGn7fF9vR2rX3lKtx6SMGjT9cC7iolZ_fw_9M_Gyiav84mPwIx9K0g17OAX7NCZbuUHPjtmk77fkjUNhbcZz6V1_79JJJJa4vo8orYyNOq9AGSart8-IfJ9v_R1KA2LPO9K9U4lzqJAil7WpVZASciAz1LJprGJcRqry2D1Ei34S0wa2aovSa3f5k-UTMcTzscKg ca.crt: 1025 bytes namespace: 20 bytes
- 浏览器访问 https://任意一节点的IP:32567
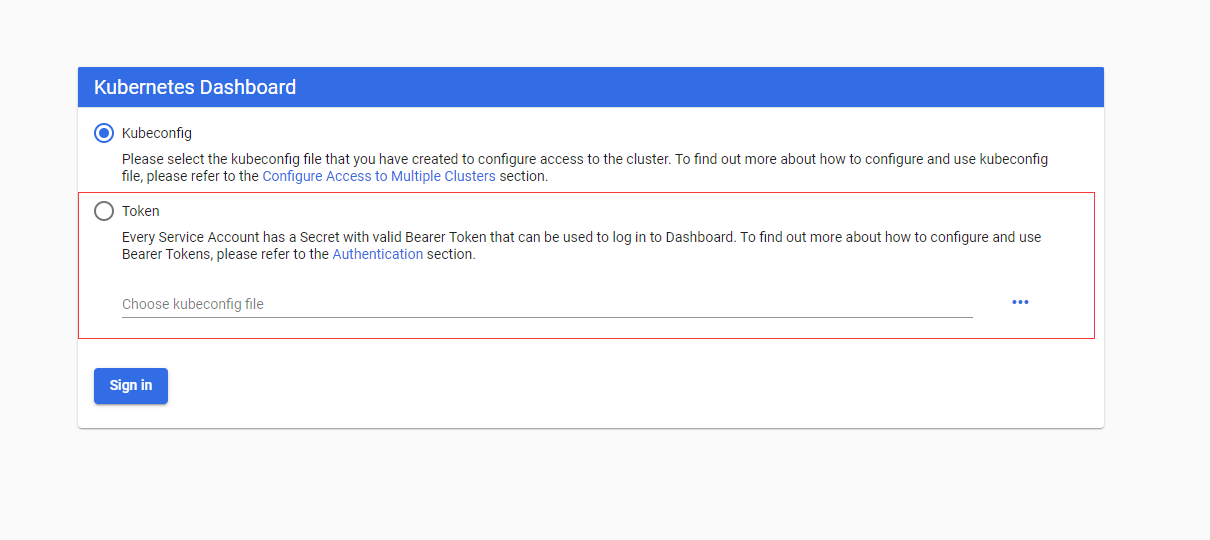
- 输入Token访问
- 至此,初步的设置算是完成了,但是创建的admin-user用户拥有很高的权限,如果需要创建分级权限可以参考 https://www.cnblogs.com/panwenbin-logs/p/10052554.html