LDAP的术语:
entry:一个单独的单元,使用DN(distinguish name)区别
attribute:entry的属性,比如,如果entry是组织机构的话,那么它的属性包括地址,电话,传真号码等,属性分为可选和必选,必选的属性使用objectclass定义,这些属性可以在
/etc/openldap/slapd.d/cn=config/cn=schema/目录下面找到
LDIF: LDAP interchange format 是用来表示LDAP entry的文本格式,格式如下:
[id] dn: distinguished_nameattribute_type: attribute_value…attribute_type: attribute_value…
一、LDAP服务器端安装
准备安装测试环境:服务器IP:192.168.100.200
操作系统:RHEL7.4
在安装之前,服务器上配置好 yum 源。
要求:在服务器上安装openldap软件,然后把系统中已有的帐号和组信息转存到LDAP中。之后,我们在其它服务器上安装配置ldap客户端,到LDAP服务器认证登录,并通过NFS方式挂载用户目录。
1、安装openLDAP服务器端软件包
# yum install -y openldap openldap-clients openldap-servers migrationtools
说明:migrationtool工具用于将本地系统帐号迁移至openldap。
2、设置LDAP服务器全局连接密码
[root@server0 ~]# slappasswd -s Ynyd1234 -n > /etc/openldap/passwd [root@server0 ~]# cat /etc/openldap/passwd {SSHA}SjGeEJNdQFujSss9Z72U2CNTSXOgDV64
3、建立X509认证本地LDAP服务秘钥
因为LDAP目录服务是以明文的方式在网络中传输数据的(包括密码),这样真的很不安全,所以我们采用TLS加密机制来解决这个问题,使用openssl工具生成X509格式的证书文件。
# openssl req -new -x509 -nodes -out /etc/openldap/certs/cert.pem -keyout /etc/openldap/certs/priv.pem -days 365
参数说明:
req PKCS#10 X.509 Certificate Signing Request (CSR) Management.
-new new request.
-x509 output a x509 structure instead of a cert. req.
-nodes don't encrypt the output key
-out output file.
-keyout file to send the key to.
-days number of days a certificate generated by -x509 is valid for.
[root@server0 ~]# openssl req -new -x509 -nodes -out /etc/openldap/certs/cert.pem -keyout /etc/openldap/certs/priv.pem -days 365 Generating a 2048 bit RSA private key .............................+++ ..............................................................................+++ writing new private key to '/etc/openldap/certs/priv.pem' ----- You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Country Name (2 letter code) [XX]:CN State or Province Name (full name) []:BEIJING Locality Name (eg, city) [Default City]:BEIJING Organization Name (eg, company) [Default Company Ltd]:ultrapower Organizational Unit Name (eg, section) []:ultrapower Common Name (eg, your name or your server's hostname) []:server0.ultrapower.com Email Address []:rusking@live.cn
[root@server0 ~]# ll /etc/openldap/certs/ total 72 -rw-r--r--. 1 root root 65536 Dec 19 16:02 cert8.db -rw-r--r--. 1 root root 1464 Dec 19 17:03 cert.pem --公钥,需要拷贝到每一台客户机上。 -rw-r--r--. 1 root root 16384 Dec 19 16:02 key3.db -r--r-----. 1 root ldap 45 Sep 18 10:49 password -rw-r--r--. 1 root root 1704 Dec 19 17:03 priv.pem --私钥 -rw-r--r--. 1 root root 16384 Sep 18 10:49 secmod.db
4、设置LDAP秘钥权限
root@server0 certs]# chown ldap:ldap /etc/openldap/certs/* [root@server0 certs]# chmod 600 priv.pem [root@server0 certs]# ll total 72 -rw-r--r--. 1 ldap ldap 65536 Dec 19 16:02 cert8.db -rw-r--r--. 1 ldap ldap 1464 Dec 19 17:03 cert.pem -rw-r--r--. 1 ldap ldap 16384 Dec 19 16:02 key3.db -r--r-----. 1 ldap ldap 45 Sep 18 10:49 password -rw-------. 1 ldap ldap 1704 Dec 19 17:03 priv.pem -rw-r--r--. 1 ldap ldap 16384 Sep 18 10:49 secmod.db
5、生成LDAP基础数据并设置其权限
复制一份LDAP的配置模板(基础数据)
# cp /usr/share/openldap-servers/DB_CONFIG.example /var/lib/ldap/DB_CONFIG # chown ldap:ldap /var/lib/ldap/* # slaptest 测试
6、启动LDAP服务,并设置开机自启动
# systemctl start/restart slapd
# systemctl enable slapd
# systemctl status slapd
7、设置防火墙规则允许LDAP服务被连接
# firewall-cmd --permanet --add-service=ldap
# firewall-cmd --reload
8、设置LDAP日志文件,保存日志信息
# vi /etc/rsyslog.conf 添加如下一行
local4.* /var/log/ldap.log
# systemctl restart rsyslog --重启rsyslog服务
二、配置LDAP本地服务器域
1、配置基础用户认证结构
[root@server0 ~]# cd /etc/openldap/schema/ [root@server0 schema]# ldapadd -Y EXTERNAL -H ldapi:/// -D "cn=config" -f cosine.ldif SASL/EXTERNAL authentication started SASL username: gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth SASL SSF: 0 adding new entry "cn=cosine,cn=schema,cn=config" [root@server0 schema]# ldapadd -Y EXTERNAL -H ldapi:/// -D "cn=config" -f nis.ldif SASL/EXTERNAL authentication started SASL username: gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth SASL SSF: 0 adding new entry "cn=nis,cn=schema,cn=config"
2、配置自定义的结构文件并导入到LDAP服务器
2.1 创建/etc/openldap/changes.ldif文件,并将下面的信息复制进去
dn: olcDatabase={2}hdb,cn=config
changetype: modify
replace: olcSuffix
olcSuffix: dc=ultrapower,dc=com
dn: olcDatabase={2}hdb,cn=config
changetype: modify
replace: olcRootDN
olcRootDN: cn=Manager,dc=ultrapower,dc=com
dn: olcDatabase={2}hdb,cn=config
changetype: modify
replace: olcRootPW
olcRootPW: 此处输入之前生成的密码(如{SSHA}v/GJvGG8SbIuCxhfTDVhkmWEuz2afNIR)
dn: cn=config
changetype: modify
replace: olcTLSCertificateFile
olcTLSCertificateFile: /etc/openldap/certs/cert.pem
dn: cn=config
changetype: modify
replace: olcTLSCertificateKeyFile
olcTLSCertificateKeyFile: /etc/openldap/certs/priv.pem
dn: cn=config
changetype: modify
replace: olcLogLevel
olcLogLevel: -1
dn: olcDatabase={1}monitor,cn=config
changetype: modify
replace: olcAccess
olcAccess: {0}to * by dn.base="gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth" read by dn.base="cn=Manager,dc=ultrapower,dc=com" read by * none
2.2 将新的配置文件更新到slapd服务程序
[root@server0 openldap]# ldapmodify -Y EXTERNAL -H ldapi:/// -f /etc/openldap/changes.ldif SASL/EXTERNAL authentication started SASL username: gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth SASL SSF: 0 modifying entry "olcDatabase={2}hdb,cn=config" modifying entry "olcDatabase={2}hdb,cn=config" modifying entry "olcDatabase={2}hdb,cn=config" modifying entry "cn=config" modifying entry "cn=config" modifying entry "cn=config" modifying entry "olcDatabase={1}monitor,cn=config"
2.3 创建/etc/openldap/base.ldif文件,并将下面的信息复制进去
[root@server0 schema]# vi /etc/openldap/base.ldif dn: dc=ultrapower,dc=com dc: ultrapower objectClass: top objectClass: domain dn: ou=People,dc=ultrapower,dc=com ou: People objectClass: top objectClass: organizationalUnit dn: ou=Group,dc=ultrapower,dc=com ou: Group objectClass: top objectClass: organizationalUnit
2.3 创建目录的结构服务
[root@server0 ~]# ldapadd -x -w Ynyd1234 -D cn=Manager,dc=ultrapower,dc=com -f /etc/openldap/base.ldif adding new entry "dc=ultrapower,dc=com" adding new entry "ou=People,dc=ultrapower,dc=com" adding new entry "ou=Group,dc=ultrapower,dc=com"
3、创建测试用户,并将本地用户认证信息导入到LDAP服务
3.1 创建测试用户
3.1 用脚本的方式批量创建10个测试用户
[root@server0 home]# mkdir /home/guests 创建guests目录
[root@server0 ~]# for i in $(seq 1 10) ; do useradd -d /home/guests/testldapuser$i -m testldapuser$i ; done [root@server0 ~]# for i in $(seq 1 10) ; do echo testldapuser$i | passwd --stdin testldapuser$i ; done
3.2 设置帐户的迁移(修改第71与74行)
使用我们一开始
[root@server0 ~]# vi /usr/share/migrationtools/migrate_common.ph # Default DNS domain $DEFAULT_MAIL_DOMAIN = "ultrapower.com"; # Default base $DEFAULT_BASE = "dc=ultrapower,dc=com";
3.3 将当前系统中的用户和组迁移至LDAP服务
[root@server0 ~]# cd /usr/share/migrationtools/
3.3.1 把用户信息转换成ldif文件,并导入到LDAP中
[root@server0 migrationtools]# grep ":10[0-9][0-9]" /etc/passwd > passwdtest [root@server0 migrationtools]# cat passwdtest rusky:x:1000:1000:rusky:/home/rusky:/bin/bash testldapuser1:x:1001:1001::/home/guests/testldapuser1:/bin/bash testldapuser2:x:1002:1002::/home/guests/testldapuser2:/bin/bash testldapuser3:x:1003:1003::/home/guests/testldapuser3:/bin/bash testldapuser4:x:1004:1004::/home/guests/testldapuser4:/bin/bash testldapuser5:x:1005:1005::/home/guests/testldapuser5:/bin/bash testldapuser6:x:1006:1006::/home/guests/testldapuser6:/bin/bash testldapuser7:x:1007:1007::/home/guests/testldapuser7:/bin/bash testldapuser8:x:1008:1008::/home/guests/testldapuser8:/bin/bash testldapuser9:x:1009:1009::/home/guests/testldapuser9:/bin/bash testldapuser10:x:1010:1010::/home/guests/testldapuser10:/bin/bash
[root@server0 migrationtools]# ./migrate_passwd.pl passwdtest users.ldif --执行该命令把上一步创建的passwd文件转换成LDAP能识别的ldif格式的文件。
[root@server0 migrationtools]# cat users.ldif
[root@server0 migrationtools]# cat user.ldif dn: uid=rusky,ou=People,dc=ultrapower,dc=com uid: rusky cn: rusky objectClass: account objectClass: posixAccount objectClass: top objectClass: shadowAccount userPassword: {crypt}$6$1pUcE65tSly517VY$sd5ht.PGvqQnLO8Rb3AyEswE1ZWX6QAYxo3q6PPkJ5mq0i0NZuy352GFwnUgLxiySdszCr7v5qebg50gVVOYQ. shadowMin: 0 shadowMax: 99999 shadowWarning: 7 loginShell: /bin/bash uidNumber: 1000 gidNumber: 1000 homeDirectory: /home/rusky gecos: rusky dn: uid=testldapuser1,ou=People,dc=ultrapower,dc=com uid: testldapuser1 cn: testldapuser1 objectClass: account objectClass: posixAccount objectClass: top objectClass: shadowAccount userPassword: {crypt}$6$TkAJZ5Dk$zhLV04HMvOsZghPFWZwonBNYB87Wd2KFDSPKfnDgqkcxRCsx06BTYKSvd3SgtGeIjeWDFBLj2L2.g0dtRPLGh1 shadowLastChange: 17524 shadowMin: 0 shadowMax: 99999 shadowWarning: 7 loginShell: /bin/bash uidNumber: 1001 gidNumber: 1001 homeDirectory: /home/guests/testldapuser1 dn: uid=testldapuser2,ou=People,dc=ultrapower,dc=com uid: testldapuser2 cn: testldapuser2 objectClass: account objectClass: posixAccount objectClass: top objectClass: shadowAccount userPassword: {crypt}$6$FAV0kLqI$zrbZZXu5.k/KJ0rWvX/yemdwcBE55FQ1PbnGmAZW7o.Ck7ru3oZZHTmWZaLLOjrD/BftPRBByYSnzoxUPKANL/ shadowLastChange: 17524 shadowMin: 0 shadowMax: 99999 shadowWarning: 7 loginShell: /bin/bash uidNumber: 1002 gidNumber: 1002 homeDirectory: /home/guests/testldapuser2 …省略…
导入user.ldif文件到LDAP中:
[root@server0 migrationtools]# ldapadd -x -w Ynyd1234 -D cn=Manager,dc=ultrapower,dc=com -f user.ldif adding new entry "uid=rusky,ou=People,dc=ultrapower,dc=com" adding new entry "uid=testldapuser1,ou=People,dc=ultrapower,dc=com" adding new entry "uid=testldapuser2,ou=People,dc=ultrapower,dc=com" adding new entry "uid=testldapuser3,ou=People,dc=ultrapower,dc=com" adding new entry "uid=testldapuser4,ou=People,dc=ultrapower,dc=com" adding new entry "uid=testldapuser5,ou=People,dc=ultrapower,dc=com" adding new entry "uid=testldapuser6,ou=People,dc=ultrapower,dc=com" adding new entry "uid=testldapuser7,ou=People,dc=ultrapower,dc=com" adding new entry "uid=testldapuser8,ou=People,dc=ultrapower,dc=com" adding new entry "uid=testldapuser9,ou=People,dc=ultrapower,dc=com" adding new entry "uid=testldapuser10,ou=People,dc=ultrapower,dc=com"
3.3.2 把用户组group信息转换成ldif文件,并导入到LDAP中
操作步骤同上:
[root@server0 migrationtools]# grep ":10[0-9][0-9]" /etc/group > grouptest [root@server0 migrationtools]# cat grouptest ruskyGroup:x:1000:rusky rusky:x:1000:rusky testldapuser1:x:1001: testldapuser2:x:1002: testldapuser3:x:1003: testldapuser4:x:1004: testldapuser5:x:1005: testldapuser6:x:1006: testldapuser7:x:1007: testldapuser8:x:1008: testldapuser9:x:1009: testldapuser10:x:1010:
[root@server0 migrationtools]# ./migrate_group.pl grouptest group.ldif [root@server0 migrationtools]# cat group.ldif dn: cn=ruskyGroup,ou=Group,dc=ultrapower,dc=com objectClass: posixGroup objectClass: top cn: ruskyGroup userPassword: {crypt}x gidNumber: 1000 memberUid: rusky dn: cn=rusky,ou=Group,dc=ultrapower,dc=com objectClass: posixGroup objectClass: top cn: rusky userPassword: {crypt}x gidNumber: 1000 dn: cn=testldapuser1,ou=Group,dc=ultrapower,dc=com objectClass: posixGroup objectClass: top cn: testldapuser1 userPassword: {crypt}x gidNumber: 1001
...略...
[root@server0 migrationtools]# ldapadd -x -w Ynyd1234 -D cn=Manager,dc=ultrapower,dc=com -f group.ldif
4、测试LDAP服务器上的用户认证信息
[root@server0 migrationtools]# ldapsearch -x cn=testldapuser3 -b dc=ultrapower,dc=com 随便查一个用户信息,看是否能查到。 # extended LDIF # # LDAPv3 # base <dc=ultrapower,dc=com> with scope subtree # filter: cn=testldapuser3 # requesting: ALL # # testldapuser3, People, ultrapower.com dn: uid=testldapuser3,ou=People,dc=ultrapower,dc=com uid: testldapuser3 cn: testldapuser3 objectClass: account objectClass: posixAccount objectClass: top objectClass: shadowAccount userPassword:: e2NyeXB0fSQ2JEFNcHZTanhWJEdvMzVHVGU3Lm0xWG8xMTlWejJBaklTVnlDTjl 2a00uQVRoNWcuV0k1QnNzSmVjbGd4cjRqV3ZWbXBHWlF6RFNGWDVYMVQ3VE9yNjFyTVhjU0JUQkUx shadowLastChange: 17524 shadowMin: 0 shadowMax: 99999 shadowWarning: 7 loginShell: /bin/bash uidNumber: 1003 gidNumber: 1003 homeDirectory: /home/guests/testldapuser3 # testldapuser3, Group, ultrapower.com dn: cn=testldapuser3,ou=Group,dc=ultrapower,dc=com objectClass: posixGroup objectClass: top cn: testldapuser3 userPassword:: e2NyeXB0fXg= gidNumber: 1003 # search result search: 2 result: 0 Success # numResponses: 3 # numEntries: 2
或者通过LDAP-browser工具连接到LDAP服务器上查看:
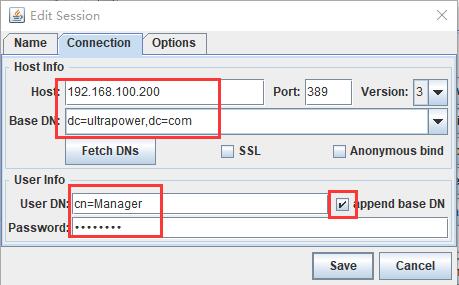
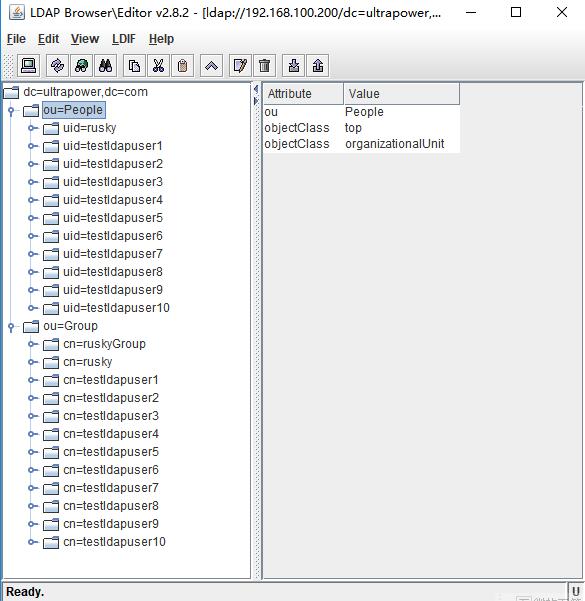
5、安装httpd服务程序,并上传密钥文件到网站目录
这是为了方便客户机通过http方式下载公钥文件cert.pem。你也可以使用ftp方式;或者手动scp拷贝也行。
[root@server0 ~]# yum install httpd -y [root@server0 ~]# cp /etc/openldap/certs/cert.pem /var/www/html/ [root@server0 ~]# systemctl enable httpd [root@server0 ~]# firewall-cmd --permanent --add-service=http [root@server0 ~]# firewall-cmd --reload [root@server0 ~]# systemctl restart httpd
至此,openldap软件在服务器端的安装与配置已完成,下一篇文章我们将使用另外一台服务器做为客户机,安装 openldap-client软件,到服务器端完成认证,并登录和通过NFS方式挂载用户目录。
参考文档:
http://www.linuxfuckprobe.com/chapter-12.html
https://www.certdepot.net/ldap-configure-ldap-server-for-user-connection/
https://www.cnblogs.com/lemon-le/p/6266921.html