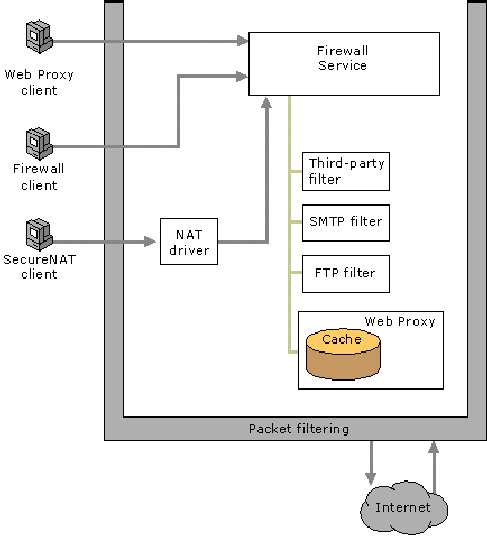
Internal Client Concepts in ISA Server 2006
Microsoft® Internet Security and Acceleration (ISA) Server 2006 uses various communication layers to protect the corporate network. At the packet layer, ISA Server implements a firewall policy, to control data on the network interface and evaluate traffic before it reaches any resource. Data is allowed to pass only after the Microsoft Firewall service processes rules to determine whether the request will be serviced.
ISA Server protects three types of clients: Firewall clients, SecureNAT clients, and Web Proxy clients, as illustrated in the figure.
Deployment Considerations
Choosing which ISA Server clients to support depends on the ISA Server deployment scenario and existing network infrastructure. The following table summarizes client requirements and deployment details.
| Feature | SecureNAT client | Firewall client | Web Proxy client |
|
Deployment details |
No software deployment required. To configure a computer as a SecureNAT client, set the computer's default gateway address to route Internet requests to the ISA Server computer. |
Firewall Client software must be installed on client computers. |
No software deployment required. To configure a computer as a Web Proxy client, configure Web browser settings on the computer to use the ISA Server computer as a Web proxy. For automatic detection of Web browser settings, Web Proxy Automatic Discovery (WPAD) must be configured in Domain Name System (DNS) or Dynamic Host Configuration Protocol (DHCP). |
|
Operating system support |
Any operating system that supports TCP/IP can be used. |
Windows operating systems. For a detailed list of supported operating systems, see Automatic Detection Concepts in ISA Server 2006. |
All platforms are supported, but by way of the Web application. Web browsers that can be configured to use a proxy server can act as Web Proxy clients. |
|
Protocol support |
Supports all simple protocols. Complex protocols requiring multiple primary or secondary connections require an application filter on the ISA Server computer. |
All Winsock applications are supported. |
The Web Proxy client supports Hypertext Transfer Protocol (HTTP), HTTP over SSL (HTTPS), and File Transfer Protocol (FTP) for download requests. |
|
User-level authentication |
SecureNAT clients cannot be authenticated by ISA Server. |
The Firewall client automatically sends client credentials with requests to the ISA Server computer. |
Web Proxy clients can be authenticated if ISA Server requests credentials. No credentials are supplied if anonymous access is enabled. |
|
Other considerations |
Use for clients that are not Windows clients. Use if support for protocols other than TCP or UDP (such as ICMP or GRE) is required. Configure published servers as SecureNAT clients if you want to forward the original source IP address of the client to the published server. |
Use when support for secondary protocols is required. Use for strong access controls. Records user names in logs. |
Use for user-based Web access, Web proxy chaining, and automatic detection of configuration settings. Good performance because Web requests are forwarded directly to Web Proxy Filter. |
The way in which ISA Server handles a request from a client in its internal networks depends on how the client computer is configured, and the type of request being made. For example:
•
On a Firewall client computer (with Firewall Client software installed and enabled), requests generated by applications that use Winsock application programming interfaces (APIs) are intercepted by the Firewall Client software. If the address requested is local, the connection is made directly. Otherwise, it is sent to the Firewall service on the ISA Server computer.
•
On a Firewall client computer or a SecureNAT client computer that does not have Web Proxy client settings configured, Web requests (HTTP, HTTPS, or FTP for downloads) from the client are passed transparently to the Web proxy listener for the network on which the request is received. This is known as transparent network address translation (NAT).
•
On any computer that is configured as a Web Proxy client, Web requests are sent directly to the Web proxy listener.
Firewall Clients
A Firewall client is a computer with Firewall Client software installed and enabled, residing in a network protected by ISA Server. Firewall Client can be installed on each individual client computer, or you use the Windows Software Installation snap-in to centrally manage distribution of Firewall Client software. For more installation and deployment information, see "Deploying the Firewall Client for ISA Server 2006" at Microsoft TechNet.
Firewall Client uses a common Winsock provider. Setting up Firewall Client does not configure individual Winsock applications. Instead, a dynamic-link library (FwcWsp.dll) in the Firewall Client software becomes a Winsock layered service provider that all Winsock applications use transparently. The Firewall Client layered service provider intercepts Winsock function calls from client applications and routes requests to the original underlying base service provider for local destinations, or transparently to the Firewall service on the ISA Server computer for remote destinations.
Support for Older Versions of Firewall Client
The Firewall Client version included with ISA Server 2006 (version 4.0) and Firewall Client for ISA Server 2004 support a more secure means of communication between the Firewall client and ISA Server. The Firewall client credentials sent transparently with each request, using a TCP control channel, are encrypted so that they cannot be intercepted.
This setting prevents earlier versions of Firewall Client software from connecting. It also prevents any Firewall client running Windows NT® Server 4.0, Windows Millennium Edition, or Windows 98 from connecting. You can configure ISA Server to accept connections only from clients communicating in this secure way, or choose to support connections from older clients.
Configuring Firewall Client Settings
Firewall Client settings can be configured as follows:
•
In ISA Server Management, you can specify application settings that apply to all Firewall clients, and configuration settings to be applied to Firewall clients on a specific network. During Firewall client installation, settings specified in ISA Server Management are stored in configuration files that are created on client computers, and applied to all users on the client computer. Following installation, Firewall client settings modified in ISA Server Management are propagated to a client computer each time a client computer is restarted, when a manual refresh is activated on the Firewall client computer, or every six hours after an initial refresh is made.
•
Following Firewall client installation, you can modify application settings and configuration settings on a specific client computer.
The following configuration files are created on the client computer during Firewall Client installation:
•
Common.ini. This file holds common configuration settings for all Winsock applications.
•
Management.ini. This file contains Firewall Client configuration settings.
The location of the configuration files on the client computer is dependent on the operating system. For example, on Windows XP computers, the files are copied to two locations:
•
\Documents and Settings\All Users\Application Data\Microsoft\Firewall Client 2004
•
\Documents and Settings\username\Local Settings\Application Data\Microsoft\Firewall Client 2004
When modifications are made to Firewall client settings, the following order of preference is applied:
1.
The .ini files in the user's folder take precedence.
2.
Firewall Client looks next in the All Users folder. If a configuration setting is specified that contradicts the user-specific settings, it is ignored.
3.
Firewall Client then detects the ISA Server computer to which it should connect, in accordance with the settings specified in the Firewall Client Management dialog box.
4.
Firewall Client examines the server-level settings. Any configuration settings specified in ISA Server are applied. If a configuration setting is specified that contradicts the user-specific or computer-specific settings, it is ignored.
Modifying Configuration Settings in ISA Server Management
In ISA Server Management, you can modify settings for all Firewall clients in all networks, or modify Firewall client properties for the default Internal network, or user-defined internal or perimeter networks. The following table summarizes Firewall client settings in ISA Server Management.
Setting
Location in ISA Server Management
Details
Allow non-encrypted Firewall client connections
In Define Firewall Client Settings in the General node of the ISA Server Management console tree
This is a global setting that applies to all Firewall clients in all networks.
Allows non-encrypted connections to support Firewall Client versions earlier than Firewall Client for ISA Server 2004, or to enable Firewall clients running on Windows NT 4.0, Windows Me, or Windows 98 to connect.
When you select this option, non-encrypted traffic from authenticated users will be blocked. Note that users are only authenticated if firewall policy rules specifically require authentication.
Application Settings
In Define Firewall Client Settings in the General node of ISA Server Management
Firewall client application settings are global and apply to all Firewall clients in all networks. In ISA Server 2006 Enterprise Edition, it applies to all networks in an array.
Application settings consist of {key, value} pairs that specify how the Firewall Client software behaves with a specific application.
Enable Firewall client support for this network
On the Firewall Client tab of the network properties page
Enables a specific network to listen for requests from Firewall clients on port 1745.
Name
On the General tab of the network properties page
For a specific network, specifies the fully qualified domain name (FQDN) of the ISA Server computer for Firewall clients. Ensures that there is a DNS entry available for clients to resolve this name. If there is no DNS server available, the IP address is specified.
Use a Web proxy server
On the Firewall Client tab of the network properties page
Manually specifies the ISA Server computer that Firewall clients in the network should use as a Web proxy.
Automatically detect settings
On the Firewall Client tab of the network properties page
Indicates that the Web browser on Firewall client computers in the network should use a WPAD entry obtained from a DHCP or DNS server to automatically discover a WPAD server on which the file Wspad.dat is available. Wspad.dat contains information about the proxy server that should be used to service URL requests, and other Firewall client settings.
Use automatic configuration script
On the Firewall Client tab of the network properties page
Specifies that the Web browser on Firewall client computers in the network should obtain settings from a configuration file. The ISA Server default configuration file holds information about the proxy server that should be used for the URL request, and for the settings specified on the Web Browser tab and the Domains tab. In ISA Server 2006 Enterprise Edition, this script also contains a list of array members that can be used for a specific URL request, and the Cache Array Routing Protocol (CARP) algorithm used for distributed cache functionality. You can also create a custom proxy automatic configuration file.
Bypass proxy for Web servers in this network
On the Web Browser tab of the network properties page
Specifies that the Web browser should directly access resources located in its own network.
Directly access computers specified in the Domains tab
On the Web Browser tab of the network properties page
Indicates that the Web browser will bypass the proxy for destinations specified on the Domains tab of the network properties page.
Directly access these servers or domains
On the Web Browser tab of the network properties page
Provides a list of addresses or domains to be accessed directly.
If ISA Server is unavailable, use this backup route to connect to the Internet
On the Web Browser tab of the network properties page
Specifies that the Web browser should use a backup route to service Web proxy requests when ISA Server is unavailable.
Domain names
On the Domains tab of the network properties page
Specifies domains that are accessed directly. This ensures that clients connect directly to servers in the local network without looping back through ISA Server. Web browsers can use this list to bypass the Web proxy when connecting to specific external sites, connecting instead as Firewall clients or SecureNAT clients. This list is used when Directly access computers specified in the Domains tab is enabled on the Web Browser tab. To bypass the proxy, a request must match both the IP address range and the server or domain name specified in the list.
Modifying Settings on the Firewall Client Computer
You can configure settings on a Firewall client computer using the Microsoft Firewall Client Management dialog box, or by modifying the configuration files. Note the following:
•
Settings specified in the Microsoft Firewall Client dialog box on the client computer are applied to all users and services on the Firewall client computer.
•
You can also modify settings for all users in the .ini files in the Documents and Settings\All Users\Application Data\Microsoft\Firewall Client 2004 folder.
•
To modify Firewall client settings for a specific user, modify the .ini files in the \Documents and Settings\username\Local Settings\Application Data\Microsoft\Firewall Client 2004 folder.
Modifying Application Settings
Application settings can be modified in ISA Server Management to apply to all Firewall clients, or to a specific Firewall client computer. The following table lists the entries that you can include when configuring the Firewall Client application settings. The first column lists the keys that can be included in the configuration files. The second column describes the values to which the keys can be set. Note that some settings can be configured only on the Firewall client computer.
Keys
Value
ServerName
Specifies the name of the ISA Server computer to which the Firewall client should connect. (Can only be set on a Firewall client computer.)
Disable
Possible values: 0 or 1. When the value is set to 1, the Firewall Client application is disabled for the specific client application, except when the Firewall Client configuration explicitly exempts the process initiating traffic.
DisableEx
Possible values: 0 or 1. When the value is set to 1, the Firewall Client application is disabled for the specific client application. Applies to Firewall Client for ISA Server 2006. When set, overrides the Disable setting. For example, for svchost, DisableEx is enabled by default.
Autodetection
Possible values: 0 or 1. When the value is set to 1, the Firewall Client application automatically finds the ISA Server computer to which it should connect. (Can only be set on a Firewall client computer.)
NameResolution
Possible values: L or R. By default, dotted domain names are redirected to the ISA Server computer for name resolution and all other names are resolved on the local computer. When the value is set to R, all names are redirected to the ISA Server computer for resolution. When the value is set to L, all names are resolved on the local computer.
LocalBindTcpPorts
Specifies a TCP port, list, or range that is bound locally.
LocalBindUdpPorts
Specifies a UDP port, list, or range that is bound locally.
DontRemoteOutboundTcpPorts
Specifies an outbound TCP port, list, or range that will not be connected through ISA Server (connect requests that will not be sent to ISA Server). Use this entry to specify the ports on which clients should not communicate with ISA Server. This is useful when protecting the ISA Server firewall from attacks on the Internal network, which are spread by accessing a fixed port at random locations.
DontRemoteOutboundUdpPorts
Specifies an outbound UDP port, list, or range that is bound locally.
RemoteBindTcpPorts
Specifies a TCP port, list, or range that is bound remotely.
RemoteBindUdpPorts
Specifies a UDP port, list, or range that is bound remotely.
ProxyBindIP
Specifies an IP address or list that is used when binding with a corresponding port. Use this entry when multiple servers that use the same port need to bind to the same port on different IP addresses on the ISA Server computer. The syntax of the entry is:
ProxyBindIp=[port]:[IP address], [port]:[IP address]
The port numbers apply to both TCP and UDP ports.
ServerBindTcpPorts
Specifies a TCP port, list, or range for all ports that should accept more than one connection.
Persistent
Possible values: 0 or 1. When the value is set to 1, a specific server state can be maintained on the ISA Server computer if a service is stopped and restarted and if the server is not responding. The client sends a keep-alive message to the server periodically during an active session. If the server is not responding, the client tries to restore the state of the bound and listening sockets upon server restart.
ForceCredentials
Used when running a Windows service or server application such as a Firewall Client application. When the value is set to 1, it forces the use of alternate user authentication credentials that are stored locally on the computer that is running the service. The user credentials are stored on the client computer using the FwcCreds.exe application that is provided with the Firewall Client software. User credentials must reference a user account that can be authenticated by ISA Server, either local to ISA Server or in a domain trusted by ISA Server. The user account is normally set not to expire. Otherwise, user credentials need to be renewed each time the account expires. (Can only be set on a Firewall client computer.)
NameResolutionForLocalHost
Possible values: L (default), P, or E. Used to specify how the local (client) computer name is resolved, when the gethostbyname API is called.
The LocalHost computer name is resolved by calling the Winsock API function gethostbyname() using the LocalHost string, an empty string, or a NULL string pointer. Winsock applications call gethostbyname(LocalHost) to find their local IP address and send it to an Internet server.
When this option is set to L, gethostbyname() returns the IP addresses of the local host computer. When this option is set to P, gethostbyname() returns the IP addresses of the ISA Server computer. When this option is set to E, gethostbyname() returns only the external IP addresses of the ISA Server computer—those IP addresses that are not in the local address table.
ControlChannel
Possible values: Wsp.udp or Wsp.tcp (default). Specifies the type of control channel used.
EnableRouteMode
Possible values: 0 or 1 (default). When EnableRouteMode is set to 1 and a route relationship is configured between the Firewall client computer and the requested destination, the IP address of the Firewall client is used as the source address. When the value is set to 0, the IP address of the ISA Server computer is used.
This flag does not apply to older versions of Firewall Client.
On Firewall client computers, in addition to modifying the Common.ini and Management.ini files, you can create another file called Application.ini for all users or a specific user, to specify configuration information for specific applications. For example, to specify entries for a specific application (FW_Client_App.exe), the following sample might appear in the Application.ini file:
[fw_Client_App] Disable=0 NameResolution=R LocalBindTcpPorts=7777 LocalBindUdpPorts=7000-7022, 7100-7170 RemoteBindTcpPorts=30 RemoteBindUdpPorts=3000-3050 ServerBindTcpPorts=100-300 ProxyBindIp=80:100.52.144.103, 82:110.51.0.0 Persistent=1 ForceCredentials=1 NameResolutionForLocalHost=L
Firewall Client Local Addresses
Whenever a Winsock application running on a Firewall client attempts to send a request to a computer, the Firewall Client layered service provider determines whether the destination IP address is local. If it is, the Firewall client sends the request directly to the destination. If the destination is remote, the request is sent to the Firewall service on an ISA Server computer, which handles the request in accordance with ISA Server access rules. By default, Firewall Client considers the following addresses as local:
•
All addresses on the network on which it is located. ISA Server supplies the set of IP address ranges included in the network to all Firewall clients residing in the network. These IP address ranges are stored in memory by the Firewall Client Agent.
•
All addresses specified in the local routing table on the Firewall client computer.
•
All domain suffixes specified on the Domains tab of the network properties page for the network in which the Firewall client is located. When Firewall clients connect to a domain specified in this local domain table, the request bypasses the Firewall client configuration. This enables such clients to connect directly to servers in the local network without looping back through ISA Server.
•
All IP addresses contained in a local address table (Locallat.txt), configured on the Firewall client computer. The Locallat.txt file may be created locally in the \Documents and Settings\All Users\Application Data\Microsoft\Firewall Client 2004 folder. When you create the Locallat.txt file, enter IP address pairs in the file. Each address pair defines either a range of IP addresses or a single IP address. The following example shows a Locallat.txt file that has two entries. The first entry is an IP address range and the second entry is a single IP address. Note that the second entry is an IP address and not a subnet mask:
•
10.51.255.25510.51.255.255
•
10.52.144.10310.52.144.103
Request Handling
The Firewall client deals with IP address requests as follows:
•
When a Winsock application on the client computer tries to connect to an IP address, the Firewall client examines the local domain table to determine whether the IP address is on the Internal network or is external to the network. If the domain name is found in the local domain table, name resolution is completed by the client. Otherwise, the client requests that ISA Server resolve the name on its behalf by passing the request to an external DNS server.
•
When client requests are resolved by ISA Server on behalf of the Firewall client, name resolution is completed in line with the DNS settings configured on the network adapter associated with the network on which the Firewall client request is received. The resolved IP address is returned to the Firewall client computer, which then sends a request to the destination. ISA Server caches the result of DNS queries it makes for Firewall clients, in accordance with the DNS Time to Live (TTL) settings configured for the network adapter.
•
After name resolution returns the IP address of the destination server, the Firewall client checks the local address table and Locallat.txt to determine whether the address is local. For internal addresses, the client connects directly. Otherwise, the request goes through the Firewall service on the ISA Server computer.
Name Resolution
Computers with Firewall Client installed have settings for each application that specify whether ISA Server does name resolution on behalf of the client. By default, name resolution for Winsock application requests running on a Firewall client computer is handled as follows:
•
Dotted decimal notation or Internet domain names are redirected to the ISA Server computer for name resolution.
•
Unqualified names are resolved on the local computer.
You can change this default behavior by modifying the NameResolution configuration setting with the following values:
•
NameResolution=L. Use this setting to specify that an application request should be resolved on the local computer.
•
NameResolution=R. Use this setting to specify that an application request should be resolved by the ISA Server computer.
It may be useful to modify this setting if you want to be sure where name resolution for an application is taking place. You can specify that settings should apply to all applications by modifying the setting in the Common.ini file. To specify the setting for a specific application, set the application name and the value in the Application.ini file.
When domains and computers are specified for direct access, Firewall client computers will attempt to resolve the name without going through ISA Server. Client computers will need a DNS server specified in the TCP/IP parameters so that they can resolve names correctly. In particular, they must be able to resolve the name of published resources to an internal IP address.
If applications have the NameResolution setting specified to L or R, this setting overrides any direct access settings. For example, if you specify that the NameResolution setting for FWC_Application.exe = R, FQDN resolution requests are always handled by ISA Server for that application, regardless of any entries in the ISA Server Firewall Client configuration files that specify the request destination as local.
Authentication
The Firewall client sends user information to the ISA Server computer with each request. This allows you to create access rules that apply to specific groups and users. Users must be logged on with an Active Directory® directory service user account, or in a workgroup scenario, with a user account that is mirrored on the ISA Server computer. When the user name is sent to the ISA Server computer, it is logged in the ISA Server Firewall logs. This makes tracking easy for Firewall client traffic.
SecureNAT Clients
The next sections provide information about SecureNAT clients, including request handling, configuring SecureNAT clients, name resolution, authentication, and server publishing.
Request Handling
ISA Server has no knowledge of SecureNAT clients except in the context of the IP address and protocol used in requests. Requests from SecureNAT clients are directed first to the network address translation (NAT) driver, which substitutes a global IP address that is valid on the Internet for the internal IP address of the SecureNAT client. The client request is then directed to the Microsoft Firewall service to determine if access is allowed. The Firewall service may also cache the requested object or deliver the object from the ISA Server cache. Because requests from SecureNAT clients are handled by the Firewall service, SecureNAT clients benefit from the Firewall service security features. All ISA Server rules can be applied to SecureNAT clients, and policies regarding protocol usage, destination, and content type are also applied to SecureNAT clients. Also, the request may be filtered by application filters and other extensions.
To allow handling of complex protocols (those requiring multiple primary or secondary connections), Microsoft Windows NAT uses NAT editors, which are written as kernel-mode NAT editor drivers. ISA Server application filters replace the functionality generally available through Windows-based NAT editors, and can modify the protocol stream to allow handling of complex protocols. Note the following limitations:
•
SecureNAT clients can only use protocols that have a protocol definition in ISA Server.
•
SecureNAT clients can access resources through ISA Server using complex protocols with secondary connections if an application filter is available on the ISA Server computer.
Configuring SecureNAT Clients
SecureNAT clients do not require special software, but are dependent on the organizational routing structure to forward requests to ISA Server. You must configure the default gateway of the client computer so that all traffic destined to the Internet is sent by way of ISA Server, either directly or indirectly, through a router. When setting the default gateway property, identify which type of network topology you are configuring:
•
Simple network. In a simple network scenario, without routers between the SecureNAT client and the ISA Server computer, you should set the SecureNAT client's default gateway to the IP address of the ISA Server network in which the client is located (usually the Internal network). You can set this manually, using the TCP/IP settings on the client. (These settings can be accessed by clicking the Network icon in Control Panel.)
•
Complex network. In a complex network, one or more routers bridge multiple subnets between the SecureNAT client and the ISA Server computer. The default gateway settings on the last router in the chain should point to ISA Server. Optimally, the router should use a default gateway that routes along the shortest path to the ISA Server computer. Also, the router should not be configured to discard packets destined for addresses outside the corporate network. ISA Server determines how to route the packets.
Name Resolution
SecureNAT clients can request objects both from computers in the local network and from the Internet. Thus, SecureNAT clients require DNS servers that can resolve names both for external and internal computers. The following is recommended:
•
For Internet access only, you should configure TCP/IP settings on the client to use DNS servers on the Internet. You should create an access rule that allows SecureNAT clients to use the DNS protocol and configure the DNS filter for the SecureNAT clients.
•
If SecureNAT clients request data both from the Internet and internal resources, the clients should use a DNS server located on the Internal network. You should configure the DNS server to resolve both internal addresses and Internet addresses.
In particular, when configuring name resolution for SecureNAT clients, it is important to avoid looping back requests for internal resources through the ISA Server computer. For example, if a SecureNAT client makes a request to an internal resource published by ISA Server on the External network, name resolution should not resolve the request to a public IP address on the External network. If it does, and the SecureNAT client sends a request to the external IP address, the publishing server may respond directly to the SecureNAT client, and the response is dropped. The source IP address of the client is replaced with the IP address of the ISA Server internal network adapter, which is recognized as internal by the published server, which may therefore respond directly to the SecureNAT client. This creates a scenario is which packets in one direction go through a route that does not involve ISA Server, and packets in the other direction go through ISA Server, and ISA Server will drop the response as invalid.
Authentication
SecureNAT clients cannot send credentials to ISA Server. The only control available for authenticating outgoing requests for SecureNAT clients is based on IP addresses. If an ISA Server access rule requires authentication, the user may see an authentication message or a failure message.
SecureNAT Clients and Server Publishing
Internal servers published using ISA Server server publishing are usually configured as SecureNAT clients.
In a server publishing scenario, ISA Server listens on a specific IP address and port for requests for the internal server. When a request arrives, ISA Server forwards it to the published server in accordance with the server publishing rule. If ISA Server is configured to forward the request to the published server with the original source IP address of the external client with which the packet originated, the published server must be configured as a SecureNAT client. The internal server requires a default route to the Internet through ISA Server, so that reply packets can be translated by ISA Server and returned to the source IP address. Configure a published server as a SecureNAT client to ensure that it has a default gateway to the Internet through the ISA Server computer that is server publishing it. If the published server cannot be configured as a SecureNAT client (it has no default route to the Internet), ensure that the server publishing rule has the setting Requests appear to come from the ISA Server computer selected.
Web Proxy Clients
A Web Proxy client is a client application or computer that sends requests to either of the following:
•
Port 80 on an ISA Server computer.
•
The port on which ISA Server listens for outgoing Web requests from the network in which the client computer resides. By default, ISA Server listens for outgoing Web requests from clients in the Internal network on port 8080.
Web Proxy clients are typically Web browser applications that comply with HTTP 1.1, and have proxy settings configured to send Web requests to ISA Server. Firewall clients and SecureNAT clients with Web proxy settings configured also make Web requests as Web Proxy clients.
You enable the ISA Server default Internal network, and user-defined internal and perimeter networks, to listen for requests from Web Proxy clients. You configure network properties to be applied to all Web Proxy clients in the network. For Web browsers that are not running on computers installed with Firewall Client software, these settings are applied when the Web browser is enabled for automatic detection, or when the Web browser is configured with the location of an automatic configuration script.
Configuring Browser Settings for Web Proxy Clients
The following table summarizes Web browser settings that can be applied to Web Proxy clients.
Setting
Location in ISA Server Management
Details
Enable Web Proxy client connections for this network
On the Web Proxy tab of the network properties page
Enables a network to listen for requests from Web Proxy clients.
Bypass proxy for Web servers in this network
On the Web Browser tab of the network properties page
Specifies that the Web browser should directly access resources located in its own network.
Directly access computers specified in the Domains tab
On the Web Browser tab of the network properties page
Specifies that the Web browser bypass the proxy for destinations specified on the Domains tab of the network properties page.
Directly access these servers or domains
On the Web Browser tab of the network properties page
Specifies a list of domains and addresses that bypass the proxy. You can enable this setting in addition to bypassing the domain list specified on the Domains tab. Any destinations added to this list should be specified with both the IP address and FQDN, or the FQDN only. For example, to configure the Internal network for direct access, add the IP address range of the Internal network, and the Internal network domain name.
The specified list of IP address ranges, computers, and site URLs for direct access is sent to the Web browser in the automatic configuration script when the browser makes a request to ISA Server—either using a WPAD call (\http://wpad.dat) to locate ISA Server, or using a call to the automatic configuration script location (by default, http://ISAServer_Name:8080/array.dll?Get.Routing.Script).
Web Proxy Filter
Web Proxy Filter in ISA Server 2006 works at the application level on behalf of clients residing in networks protected by ISA Server that request HTTP and HTTPS objects. Such Web requests benefit from application-layer inspection and caching, and may be from a number of sources:
•
Requests from Web Proxy clients. Web requests (HTTP, HTTPS, or FTP for downloads) from Web Proxy clients that specify ISA Server as a proxy server in browser settings are passed directly to Web Proxy Filter.
•
Requests from SecureNAT or Firewall clients not configured as Web Proxy clients. By default, HTTP is bound to Web Proxy Filter. With this setting in place, Web requests from clients that are not Web Proxy clients are passed transparently from the Firewall service to Web Proxy Filter for handling. This is known as transparent NAT. Applying NAT substitutes a global IP address that is valid on the Internet for the internal IP address of the client request, thus protecting internal addresses.