CTF-安恒19年二月月赛部分writeup
MISC1-来玩个游戏吧
题目:


第一关,一眼可以看出是盲文,之前做过类似题目

拿到在线网站解一下

??41402abc4b2a76b9719d911017c592,那么就奇怪了,这个??是什么东西,数一下加上??正好32位,应该是个MD5了,索性直接百度一下,
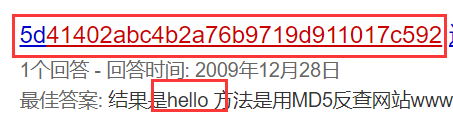
第一关答案出来了,试过了MD5值不对,hello是正确的,下一关。
第二关提示
没见过这种的,还是百度一下,

下载了这个脚本后执行命令
fastcoll_v1.0.0.5.exe -p C:windows otepad.exe -o D: otepad1.exe D: otepad2.exe
(因为没有规定文件名啥的就直接复制他的命令了)
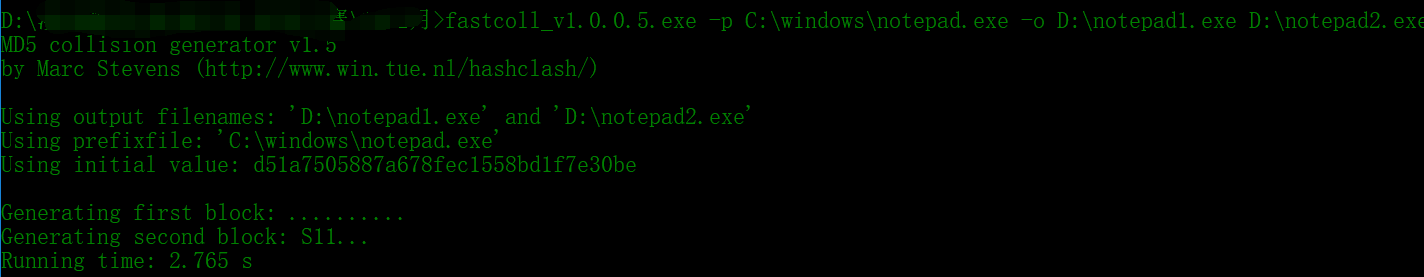
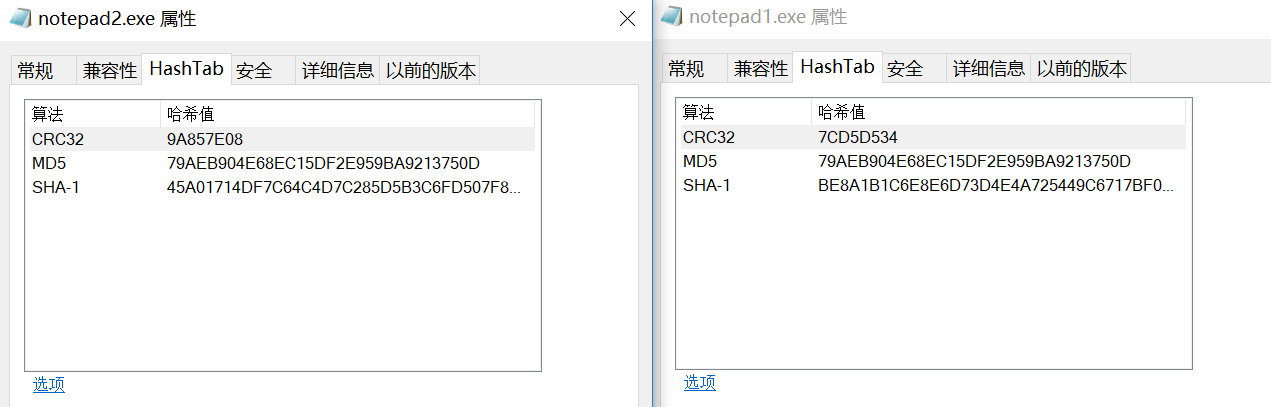
直接将文件路径复制到文本框即可

Dear Professional ; Especially for you - this cutting-edge intelligence ! If you no longer wish to receive our publications simply reply with a Subject: of "REMOVE" and you will immediately be removed from our club . This mail is being sent in compliance with Senate bill 2216 , Title 9 ; Section 306 ! THIS IS NOT MULTI-LEVEL MARKETING . Why work for somebody else when you can become rich as few as 35 weeks . Have you ever noticed more people than ever are surfing the web and people will do almost anything to avoid mailing their bills . Well, now is your chance to capitalize on this ! WE will help YOU decrease perceived waiting time by 120% & decrease perceived waiting time by 140% . You can begin at absolutely no cost to you . But don't believe us ! Mrs Jones of Minnesota tried us and says "I was skeptical but it worked for me" . We assure you that we operate within all applicable laws . Because the Internet operates on "Internet time" you must act now ! Sign up a friend and your friend will be rich too . Warmest regards . Dear Cybercitizen , We know you are interested in receiving red-hot announcement ! We will comply with all removal requests ! This mail is being sent in compliance with Senate bill 1619 ; Title 2 ; Section 301 . This is NOT unsolicited bulk mail ! Why work for somebody else when you can become rich within 53 MONTHS ! Have you ever noticed more people than ever are surfing the web and more people than ever are surfing the web . Well, now is your chance to capitalize on this . We will help you use credit cards on your website plus decrease perceived waiting time by 150% . The best thing about our system is that it is absolutely risk free for you ! But don't believe us ! Mrs Simpson of Washington tried us and says "Now I'm rich, Rich, RICH" . We assure you that we operate within all applicable laws ! We beseech you - act now ! Sign up a friend and your friend will be rich too . Thank-you for your serious consideration of our offer ! Dear Friend ; This letter was specially selected to be sent to you ! If you no longer wish to receive our publications simply reply with a Subject: of "REMOVE" and you will immediately be removed from our mailing list . This mail is being sent in compliance with Senate bill 2716 , Title 2 ; Section 306 ! This is a ligitimate business proposal . Why work for somebody else when you can become rich inside 33 weeks . Have you ever noticed more people than ever are surfing the web plus more people than ever are surfing the web . Well, now is your chance to capitalize on this ! WE will help YOU SELL MORE and process your orders within seconds . You can begin at absolutely no cost to you . But don't believe us ! Mrs Jones of Kentucky tried us and says "I was skeptical but it worked for me" ! This offer is 100% legal ! We implore you - act now . Sign up a friend and you'll get a discount of 50% . God Bless .
题目提示了:需要一个在线的网站去解密,而这个网站使用了栅格密码。
栅格密码也没听说过,还是百度
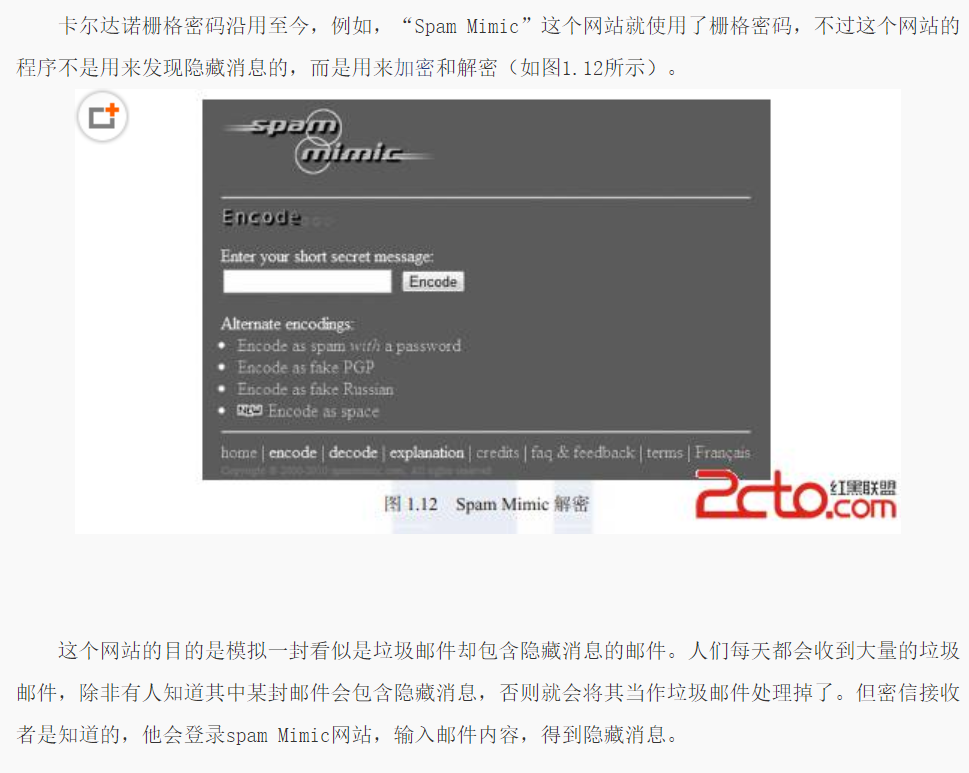
搜索关键字Spam Mimic到网站 http://www.spammimic.com/解码

flag为:flag{a0dd1e2e6b87fe47e5ad0184dc291e04}
MISC2-简单的流量分析
题目:
过滤http协议,按照info排序一下
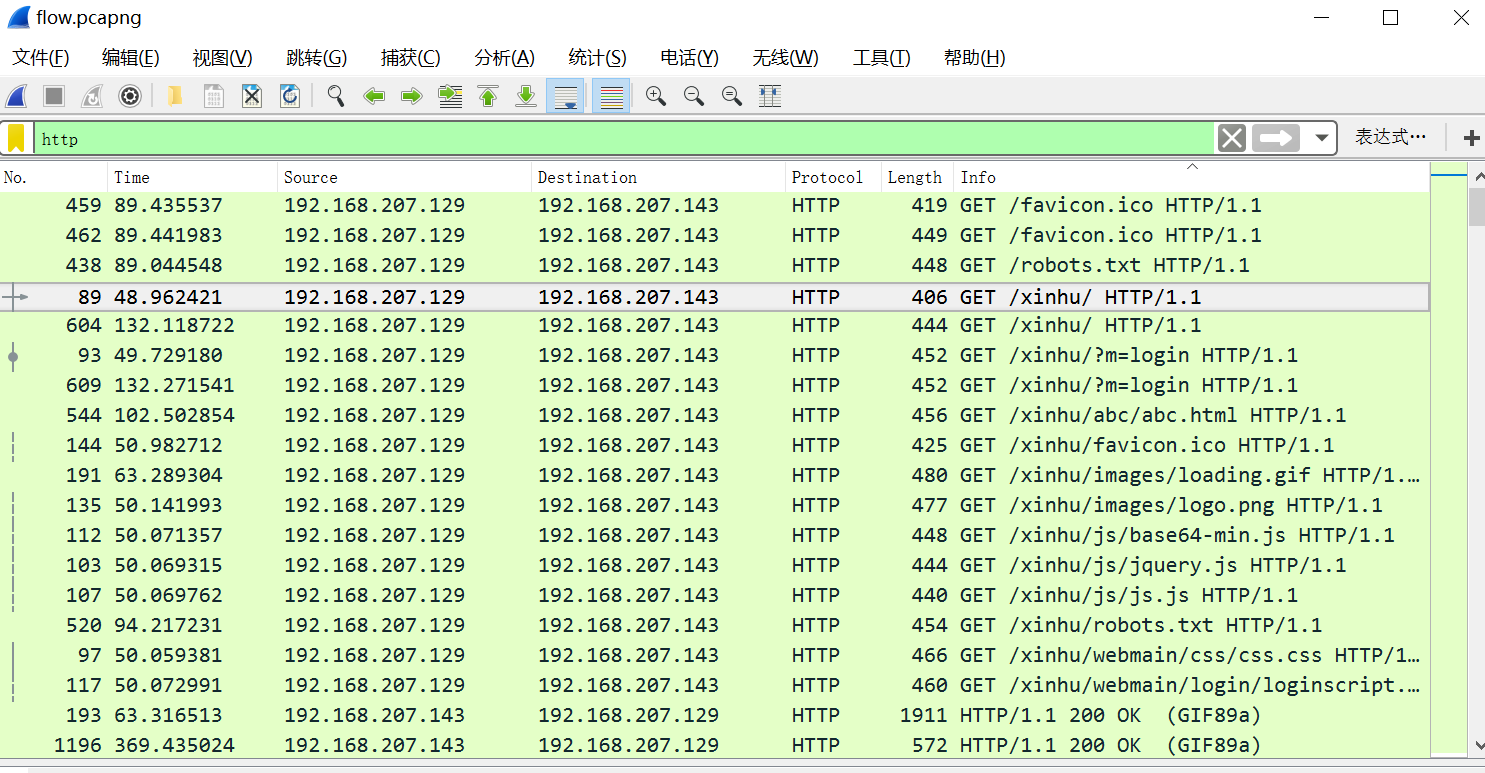
发现存在/xinhu/robots.txt
追踪http流到/xinhu/robots.txt
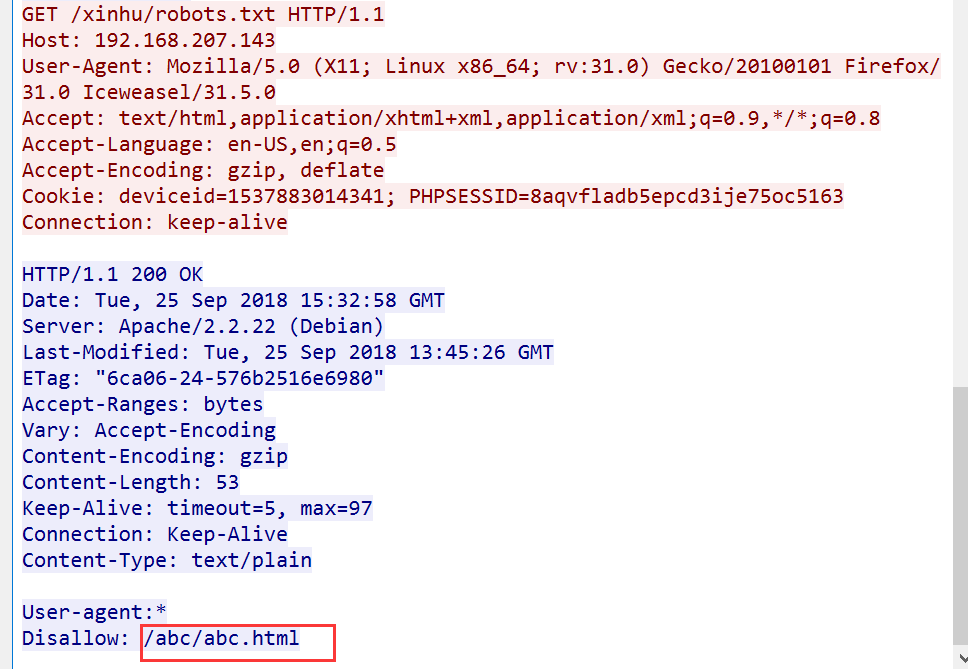
发现abc.html,继续跟进
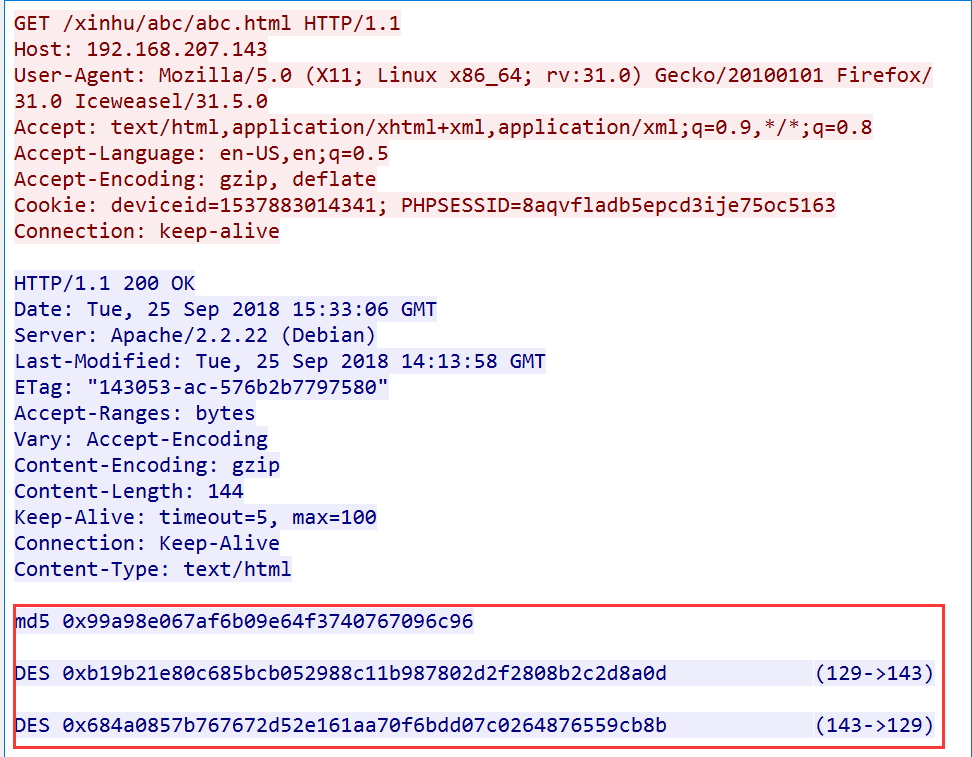
发现MD5和两串DES
md5 0x99a98e067af6b09e64f3740767096c96 DES 0xb19b21e80c685bcb052988c11b987802d2f2808b2c2d8a0d (129->143) DES 0x684a0857b767672d52e161aa70f6bdd07c0264876559cb8b (143->129)
继续向下分析,发现都是IPSec加密后的流量,尝试使用前面给的MD5和DES解密

wireshark进入Preference菜单下的Profile,找到ESP, 配置如下:
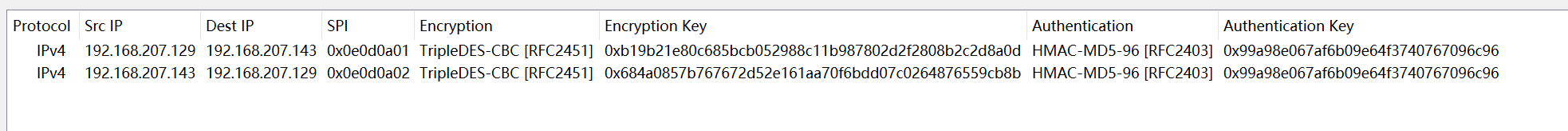
此时再次过滤http发现有部分响应包带上了数字,102 108 转换为ASCII码则为f l 所以统一提取转换。

a = [102,108,97,103,123,50,55,98,48,51,98,55,53,56,102,50,53,53,50,55,54,101,53,97,57,56,100,97,48,101,49,57,52,55,98,101,100,125] flag = '' for i in a: flag +=chr(i) print flag

flag:flag{27b03b758f255276e5a98da0e1947bed}
CRYPTO1-hahaha
题目:
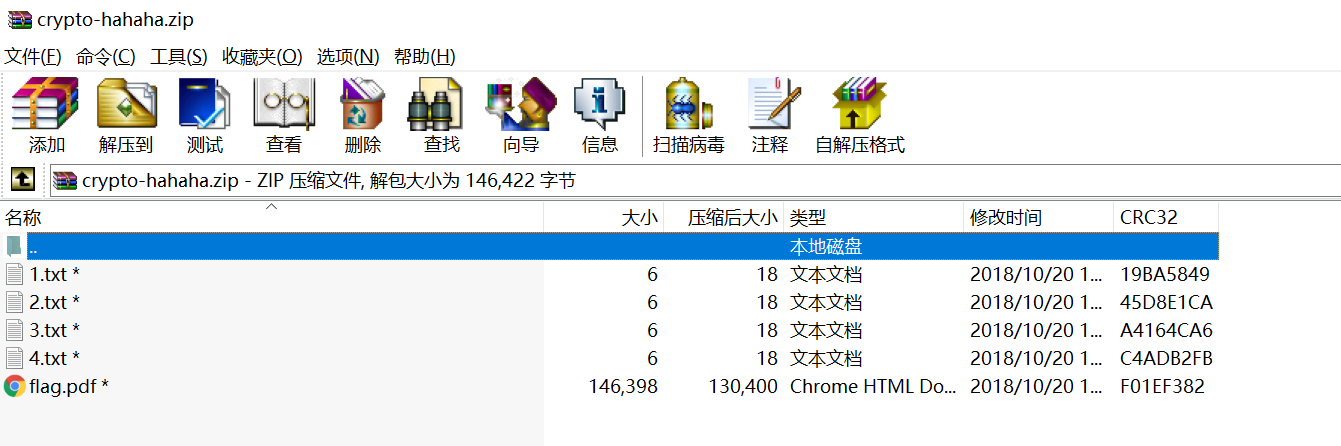
压缩包题目,其实看到这压缩包里的短位CRC32应该就能猜出是CRC32爆破了
当然也可以一步一步排除一下
首先binwalk分析得出非伪加密,爆破的话没有提示,不理想。
所以直接上脚本
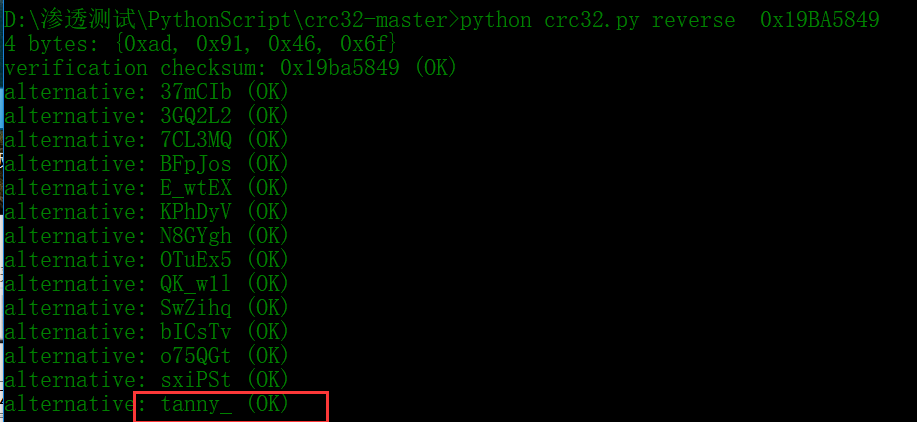

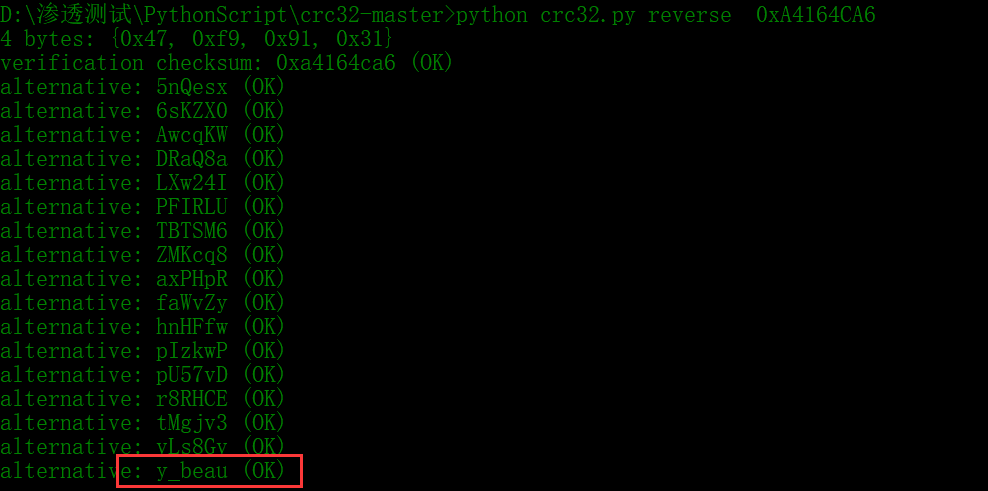

所以加起来就是tanny_is_very_beautifu1_
哈哈

按照给的提示,flag应该是flag{1or! 2or@ sechn}
然后给了sha1值,应该是要爆破了。。。
当时做到这里就停了,因为不会写脚本了
下面献上一叶飘零大佬的脚本
import itertools import hashlib def sha1(str): sha = hashlib.sha1(str) encrypts = sha.hexdigest() return encrypts a1 = '1!' a2 = '2@' a3 = '{' a4 = '}' for str1 in itertools.combinations(a1,1): for str2 in itertools.combinations(a2,1): str3 = str1[0]+str2[0]+'sechn' for i in itertools.permutations(str3): tmp = (''.join(i)) res = 'flag{'+tmp+'}' # print sha1(res) if sha1(res) == 'e6079c5ce56e781a50f4bf853cdb5302e0d8f054': print res break
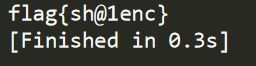
flag:flag{sh@1enc}
小结:web没做出来太菜,pwn刚起步,压根没看,密码2也没做出来,需要的脑洞太大了,另外膜飘零师傅。
参考:https://www.anquanke.com/post/id/171543