newsctf
周末一直被hxd缠着要我去帮他AK逆向,最后只出了四道,最后两道都拿了一血。(Q神太强了!!!
题目还算简单,不知道为啥没人做。。。。
2021.6.1萌新赛-re_signin
拿到文件解压,发现是个pyc文件。拿去反编译得到源码。

# uncompyle6 version 3.7.4
# Python bytecode 3.8 (3413)
# Decompiled from: Python 3.8.6 (tags/v3.8.6:db45529, Sep 23 2020, 15:52:53) [MSC v.1927 64 bit (AMD64)]
# Embedded file name: /home/mumuzi/����/flag.py
# Compiled at: 2021-05-28 16:16:08
# Size of source mod 2**32: 528 bytes
flag = 'xxxx{xxxxxxxxxxxxxxxxxx}'
import random
c = [0] * len(flag)
for i in range(len(flag)):
c[i] = ord(flag[i])
else:
print(c)
t = 0
for i in range(2000):
num = range(0, 100)
nums = random.sample(num, 22)
numss = nums.copy()
for i in range(len(nums) - 1):
for j in range(len(nums) - i - 1):
if nums[j] > nums[(j + 1)]:
nums[j], nums[j + 1] = nums[(j + 1)], nums[j]
if count == c[t]:
print(numss)
t += 1
if t == 24:
break
# okay decompiling flag.pyc
题目就是将冒泡排序的次数等于flag中字符的ascii码。
直接跑一次计数然后转chr输出就行了
numss= [[73, 69, 60, 20, 64, 68, 99, 4, 36, 9, 91, 42, 75, 43, 8, 77, 55, 70, 84, 37, 3, 93],
[85, 46, 47, 99, 58, 35, 83, 3, 57, 18, 52, 17, 97, 16, 6, 51, 84, 62, 1, 41, 88, 87],
[97, 34, 31, 80, 19, 57, 10, 84, 4, 50, 43, 63, 65, 88, 30, 72, 21, 36, 27, 41, 86, 79],
[31, 23, 68, 67, 30, 47, 27, 40, 73, 63, 11, 89, 18, 5, 9, 74, 88, 38, 8, 20, 50, 83],
[88, 5, 85, 82, 36, 74, 6, 15, 40, 55, 95, 8, 84, 47, 96, 33, 25, 29, 77, 67, 26, 39],
[54, 53, 0, 37, 66, 91, 39, 38, 57, 6, 47, 28, 49, 92, 29, 85, 88, 84, 90, 13, 35, 52],
[80, 18, 26, 91, 10, 52, 11, 99, 85, 75, 60, 48, 36, 74, 55, 51, 86, 49, 89, 29, 82, 16],
[35, 70, 42, 44, 18, 65, 84, 71, 26, 14, 38, 28, 21, 86, 20, 54, 30, 11, 66, 10, 69, 77],
[71, 25, 43, 23, 29, 6, 33, 44, 5, 30, 32, 18, 47, 13, 76, 8, 83, 87, 57, 26, 16, 19],
[29, 51, 7, 62, 94, 32, 57, 1, 71, 84, 92, 16, 18, 19, 56, 52, 40, 80, 98, 44, 82, 33],
[67, 14, 93, 91, 78, 80, 7, 37, 10, 82, 38, 83, 23, 27, 17, 76, 74, 18, 66, 24, 99, 43],
[29, 56, 44, 54, 70, 31, 10, 38, 8, 85, 18, 22, 32, 49, 2, 21, 50, 5, 25, 48, 90, 84],
[23, 33, 90, 7, 42, 71, 25, 58, 5, 47, 54, 18, 97, 72, 2, 1, 68, 64, 76, 85, 69, 49],
[77, 67, 52, 31, 35, 6, 56, 94, 81, 23, 78, 50, 15, 10, 28, 69, 43, 91, 82, 72, 99, 38],
[20, 47, 52, 27, 73, 64, 9, 62, 3, 57, 2, 97, 44, 35, 89, 10, 18, 29, 58, 56, 74, 84],
[66, 11, 76, 91, 70, 9, 6, 75, 32, 71, 44, 48, 88, 20, 98, 97, 79, 63, 47, 78, 60, 81],
[43, 13, 70, 23, 31, 69, 52, 30, 2, 78, 0, 37, 73, 93, 18, 1, 51, 62, 25, 68, 65, 87],
[24, 86, 29, 0, 93, 51, 53, 47, 16, 40, 94, 98, 88, 64, 41, 83, 44, 35, 45, 75, 17, 46],
[33, 12, 63, 77, 25, 24, 47, 58, 6, 89, 97, 27, 21, 96, 92, 50, 82, 76, 5, 62, 56, 44],
[12, 36, 16, 44, 19, 62, 43, 80, 58, 98, 69, 97, 1, 7, 49, 26, 70, 34, 53, 13, 65, 48],
[51, 74, 76, 98, 33, 78, 44, 45, 4, 65, 99, 84, 80, 93, 37, 56, 77, 9, 6, 94, 52, 88],
[80, 38, 88, 66, 7, 40, 70, 24, 2, 12, 76, 18, 57, 73, 58, 83, 33, 17, 89, 69, 77, 67],
[18, 53, 14, 24, 94, 42, 61, 75, 62, 60, 73, 2, 65, 48, 80, 23, 44, 91, 7, 0, 31, 71],
[16, 54, 87, 75, 8, 23, 33, 56, 22, 63, 1, 2, 25, 6, 84, 80, 4, 49, 17, 42, 14, 43]]
for k in range(len(numss)):
nums=numss[k]
count=0
for i in range(len(nums) - 1):
for j in range(len(nums) - i - 1):
if nums[j] > nums[(j + 1)]:
nums[j], nums[j + 1] = nums[(j + 1)], nums[j]
count+=1
print(chr(count),end='')
#synt{jrypbzr_gb_arjfpgs}
发现字符串怪怪的,有点像凯撒,拿去,发现偏移为13出现flag。
#flag{welcome_to_newsctf}
2021.6.1萌新赛-1+1的签到题
ida打开发现,upx加壳了。
使用upx -d 脱壳,
再用ida打开。发现,程序写得乱糟糟的。。
首先是一个换表base58.
???又得到一个表
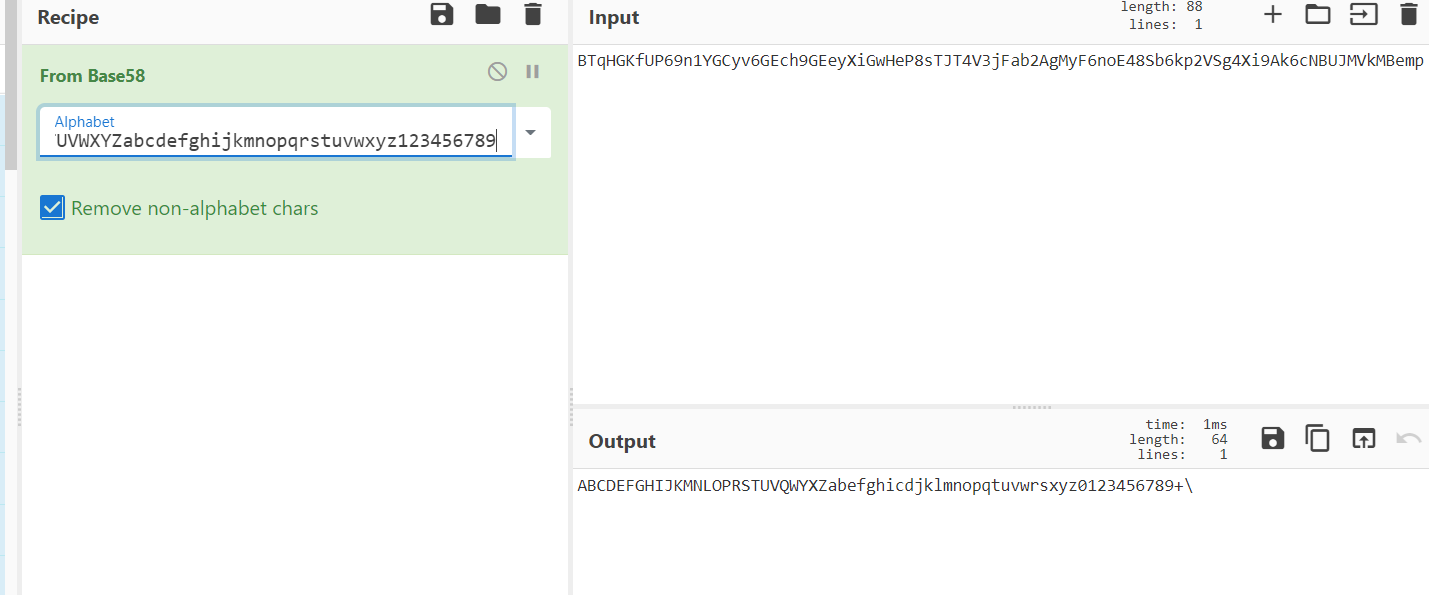
发现,还有两串奇怪得编码
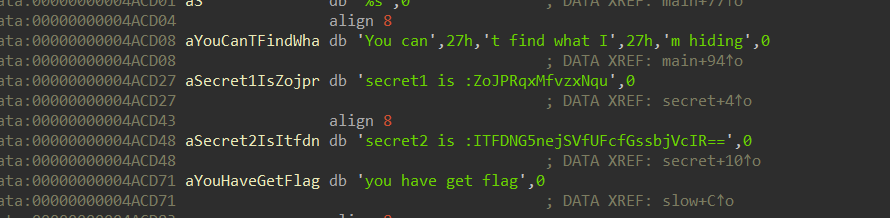
想到上面得到了一串表好像base64,再拿去解码。
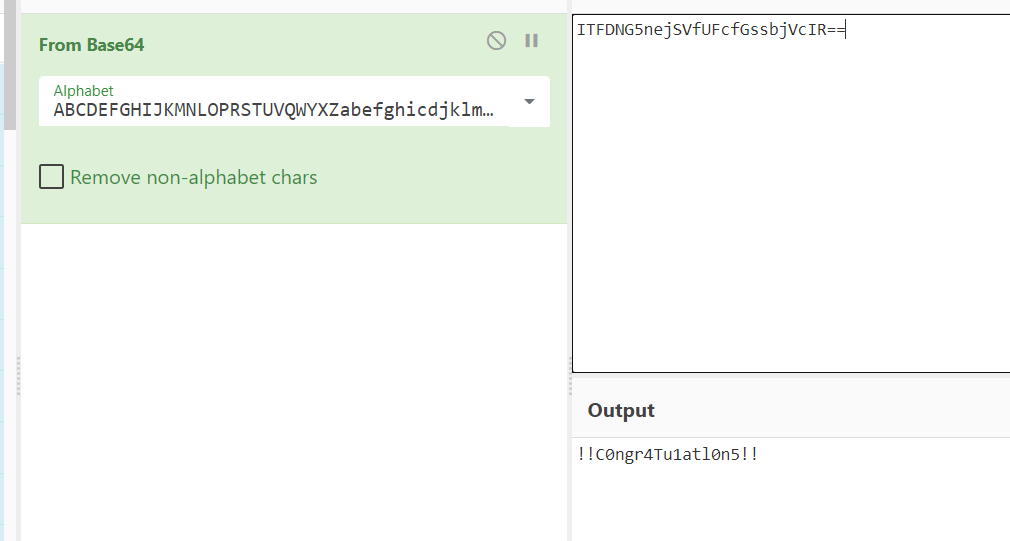
secret2能解码出:
!!C0ngr4Tu1atl0n5!!
尝试发现,secret1还是用最开始的那个表解base58
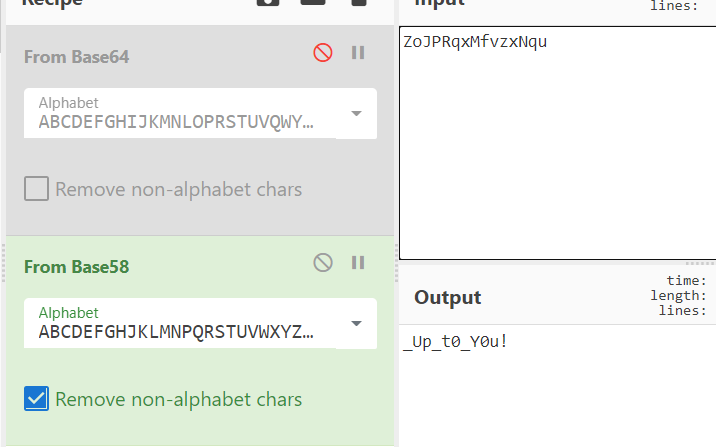
然后审计程序,发现还有一处输入,发现是利用srand()生成一个种子,然后随机出来的值,异或操作等于一个固定的值,那么我们可以动调或者写源码调用这个种子生成的随机值,然后异或,得到最后的值。
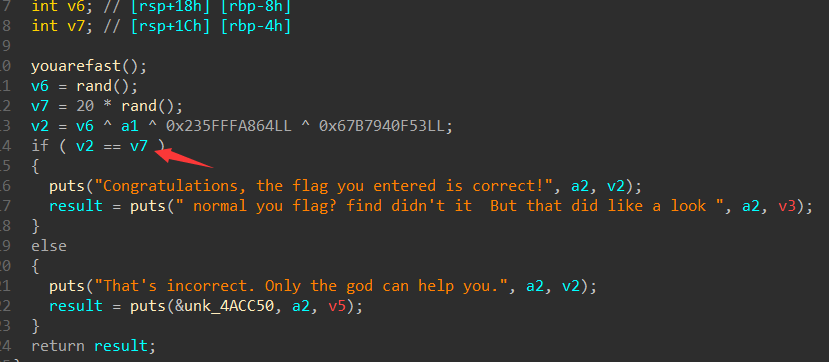
得到两个数分别为 198469000 395774304
然后算出a1
0x453473793fv6=198469000
v7=395774304*20
print(hex(v6^v7 ^ 0x235FFFA864 ^ 0x67B7940F53))
print(long_to_bytes(0x453473793f))
#b'E4sy?'
合并起来就是:
#flag{E4sy?_Up_t0_Y0u!!!C0ngr4Tu1atl0n5!!}
2021.6.1萌新赛-开门啊-2
安卓逆向,
so层分析
总得来说就是一个输入用户名,注册码,,且用户名用于注册码的生成.
主要分析三个函数
前两个只是赋值,
第三个才是关键函数,
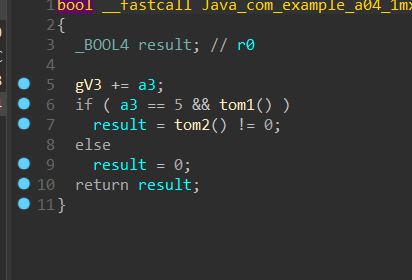
点击要等于5次,此时gV3=15且tom1()要返回1,
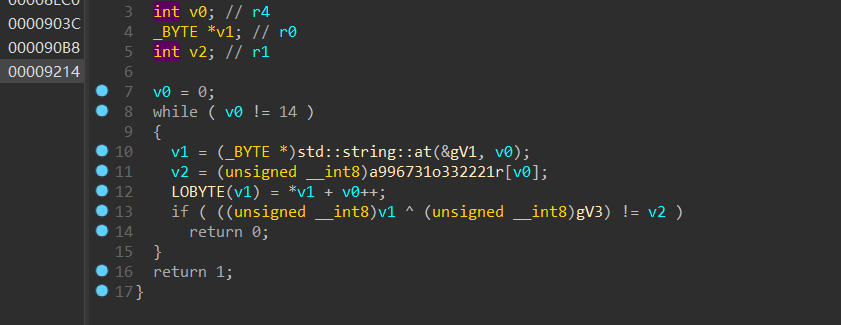
tom1只是将
输入的字符串1异或后与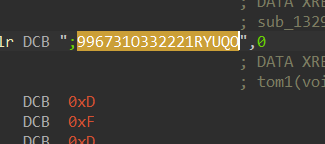 这个数组前十四位进行比较。
这个数组前十四位进行比较。
全相同则返回一。
tom2()
函数则是对注册码的比较
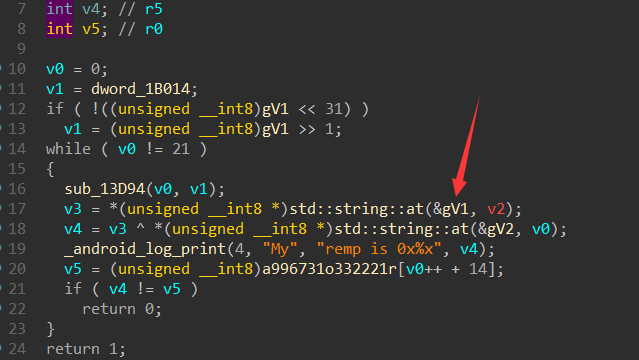
讲第一个输入的字符串,逐个异或后,与一个数组进行逐个比较。
dd=[ 0x3B, 0x39, 0x39, 0x36, 0x37, 0x33, 0x31, 0x4F, 0x33, 0x33,
0x32, 0x32, 0x32, 0x31]
key=[]
for i in range(len(dd)):
for k in range(0x20,0x7f):
if (k+i)^15==dd[i]:
key.append(k)
dd2=[ 0x52, 0x59, 0x55, 0x51, 0x4F, 0x00,
0x0D, 0x0F, 0x0D, 0x02, 0x01, 0x01, 0x06, 0x05, 0x01, 0x03,
0x03, 0x00, 0x00, 0x02, 0x45]
for i in range(len(dd2)):
print(chr(dd2[i]^key[i%len(key)]),end='')
#flag{756912374567645}
2021.6.1萌新赛-开门啊-1
程序有点绕,不过动调后可以得到,g.0=15,然后输入的字符串,每一个字符的ascii加15。然后对比下图的那个数组。
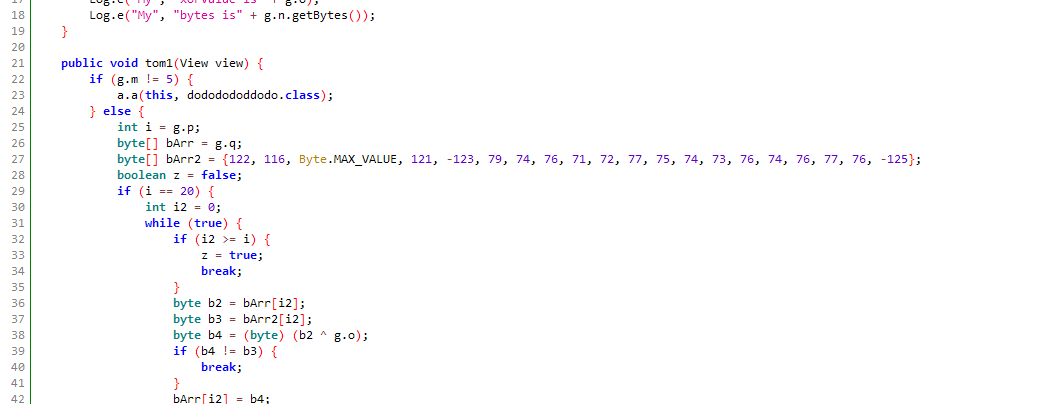
异或后然后再减去15就是输入的字符串。
flag{16498356746434}