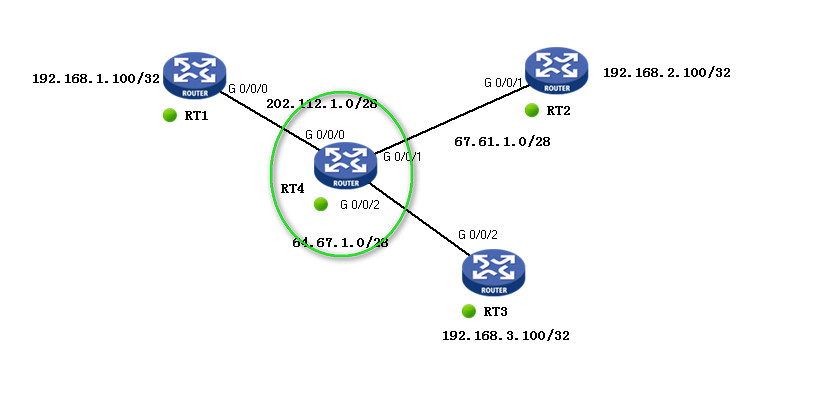
如图配置 两实验
R1模拟总部,R2 与R3模拟分部
实验一
要求使用 IPSec VPN 主模式,使得总部与两分部内网可相互通讯

步骤:
1、 配置默认路由
[RT1]ip route-static 0.0.0.0 0 202.112.1.2
[RT2]ip route-static 0.0.0.0 0 67.61.1.2
[RT3]ip route-static 0.0.0.0 0 64.67.1.2
2、 IKE peer配置
[RT1]ike proposal 1
[RT1-ike-peer-rt2]exchange-mode main
[RT1-ike-peer-rt2]pre-shared-key simple cisco
[RT1-ike-peer-rt2]id-type ip
[RT1-ike-peer-rt2]proposal 1
[RT1-ike-peer-rt2]local-address 202.112.1.1
[RT1-ike-peer-rt2]remote-address 67.61.1.1
[RT1-ike-peer-rt3]exchange-mode main
RT1-ike-peer-rt3]pre-shared-key simple cisco
[RT1-ike-peer-rt3]local-address 202.112.1.1
[RT1-ike-peer-rt3]remote-address 64.67.1.1
[RT1-ike-peer-rt3]id-type ip
[RT1-ike-peer-rt3]proposal 2
[RT2-ike-peer-rt1]exchange-mode main
[RT2-ike-peer-rt1]proposal 1
[RT2-ike-peer-rt1]local-address 67.61.1.1
[RT2-ike-peer-rt1]remote-address 202.112.1.1
[RT2-ike-peer-rt1]pre-shared-key simple cisco
[RT2-ike-peer-rt1]id-type ip
[RT3-ike-peer-rt1]exchange-mode main
[RT3-ike-peer-rt1]pre-shared-key simple cisco
[RT3-ike-peer-rt1]local-address 64.67.1.1
[RT3-ike-peer-rt1]remote-address 202.112.1.1
3、 创建安全ACL
[RT1]acl number 3001 match-order config
[RT1-acl-adv-3001]rule permit ip source 192.168.1.0 0.0.0.255 destination 192.168.2.0 0.0.0.255
[RT2]acl number 3000 match-order config
[RT2-acl-adv-3000]rule permit ip source 192.168.2.0 0.0.0.255 destination 192.168.1.0 0.0.0.255
[RT3]acl number 3000 match-order config
[RT3-acl-adv-3000]rule permit ip source 192.168.3.0 0.0.0.255 destination 192.168.1.0 0.0.0.255
[RT1-acl-adv-3002]rule permit ip source 192.168.1.0 0.0.0.255 destination 192.168.3.0 0.0.0.255
4、 创建ipsec 安全提议
[RT1]ipsec proposal rt2
[RT1]ipsec proposal rt3
[RT2]ipsec proposal rt1
[RT3]ipsec proposal rt1
5、 创建Ipsec policy
[RT1-ipsec-policy-isakmp-h3c-1]security acl 3001
[RT1-ipsec-policy-isakmp-h3c-1]proposal rt2
[RT1-ipsec-policy-isakmp-h3c-1]ike-peer rt2
[RT1-ipsec-policy-isakmp-h3c-2]security acl 3002
[RT1-ipsec-policy-isakmp-h3c-2]ike-peer rt3
[RT1-ipsec-policy-isakmp-h3c-2]proposal rt3
[RT2-ipsec-policy-isakmp-h3c-1]security acl 3000
[RT2-ipsec-policy-isakmp-h3c-1]ike-peer rt1
[RT2-ipsec-policy-isakmp-h3c-1]proposal rt1
[RT3-ipsec-policy-isakmp-h3c-1]security acl 3000
[RT3-ipsec-policy-isakmp-h3c-1]ike-peer rt1
[RT3-ipsec-policy-isakmp-h3c-1]proposal rt1
6、 接口上应用ipsec policy
[RT1-GigabitEthernet0/0/0]ipsec policy h3c
[RT2-GigabitEthernet0/0/1]ipsec policy h3c
[RT3-GigabitEthernet0/0/2]ipsec policy h3c
7、 测试
192.168.1.100 ping 192.168.2.100

192.168.1.100 ping 192.168.3.100

RT1 IKE SA查看

RT1 ipsec SA查看

实验二
要求使用
IPSec VPN 野蛮模式,使得总部与两分部内网可相互通讯 (R2 R3两分部公网接口为动态获得地址情况)
步骤:
1、 配置静态路由
[RT1]ip route-static 0.0.0.0 0 202.112.1.2
[RT2]ip route-static 0.0.0.0 0 67.61.1.2
[RT3]ip route-static 0.0.0.0 0 64.67.1.2
2、 配置IKE Peer
[RT1-ike-peer-rt2]exchange-mode aggressive
[RT1-ike-peer-rt2]id-type name
[RT1-ike-peer-rt2]pre-shared-key simple cisco
[RT1-ike-peer-rt3]exchange-mode aggressive
[RT1-ike-peer-rt3]id-type name
[RT1-ike-peer-rt3]pre-shared-key simple cisco
[RT1-ike-peer-rt3]remote-name rt3
[RT2-ike-peer-rt1]exchange-mode aggressive
[RT2-ike-peer-rt1]id-type name
[RT2-ike-peer-rt1]remote-address 202.112.1.1
3、 配置ipsec policy
[RT1-ipsec-policy-isakmp-h3c-1]security acl 3001
[RT1-ipsec-policy-isakmp-h3c-1]security acl 3001
[RT1-ipsec-policy-isakmp-h3c-1]proposal rt2
[RT1-ipsec-policy-isakmp-h3c-2]security acl 3002
[RT1-ipsec-policy-isakmp-h3c-2]ike-peer rt3
[RT1-ipsec-policy-isakmp-h3c-2]proposal rt3
[RT2-ipsec-policy-isakmp-h3c-1]security acl 3000
[RT2-ipsec-policy-isakmp-h3c-1]ike-peer rt1
[RT2-ipsec-policy-isakmp-h3c-1]proposal rt1
[RT2-ike-peer-rt1]pre-shared-key simple cisco
[RT3-ike-peer-rt1]exchange-mode aggressive
[RT3-ike-peer-rt1]id-type name
[RT3-ike-peer-rt1]remote-address 202.112.1.1
[RT3-ike-peer-rt1]remote-name rt1
[RT3-ike-peer-rt1]pre-shared-key simple cisco
[RT3-ipsec-policy-isakmp-h3c-1]security acl 3000
[RT3-ipsec-policy-isakmp-h3c-1]ike-peer rt1
[RT3-ipsec-policy-isakmp-h3c-1]proposal rt1
4、 接口应用ipsec policy
[RT1-GigabitEthernet0/0/0]ipsec policy h3c
[RT2-GigabitEthernet0/0/1]ipsec policy h3c
[RT3-GigabitEthernet0/0/2]ipsec policy h3c
5、 测试
192.168.2.100 ping 192.168.1.100

192.168.3.100 ping 192.168.1.100

RT1查看ike sa

RT1查看ipsec sa

RT2和RT3分别更换接口地址后测试,并在RT1查看IKE SA
