七.部署flannel网络
kubernetes支持基于vxlan方式的flannel与weave网络,基于BGP路由的Calico网络,本节采用flannel网络。
Flannel网络采用etcd等kv存储做集中控制,在每个host生成1个subnet,每个host上的subnet通过vxlan方式打通。
1. 创建flannel TLS证书与私钥
etcd集群启用了双向TLS认证,需要为flannel网络指定与etcd集群通信的CA与秘钥。
1)创建flannel证书签名请求
[root@kubenode1 ~]# mkdir -p /etc/kubernetes/flannel [root@kubenode1 ~]# cd /etc/kubernetes/flannel/ [root@kubenode1 flannel]# touch flanneld-csr.json # hosts字段留空 [root@kubenode1 flannel]# vim flanneld-csr.json { "CN": "flanneld", "hosts": [], "key": { "algo": "rsa", "size": 2048 }, "names": [ { "C": "CN", "ST": "ChengDu", "L": "ChengDu", "O": "k8s", "OU": "cloudteam" } ] }
2)生成flannel证书与私钥
[root@kubenode1 flannel]# cfssl gencert -ca=/etc/kubernetes/ssl/ca.pem -ca-key=/etc/kubernetes/ssl/ca-key.pem -config=/etc/kubernetes/ssl/ca-config.json -profile=kubernetes flanneld-csr.json | cfssljson -bare flanneld
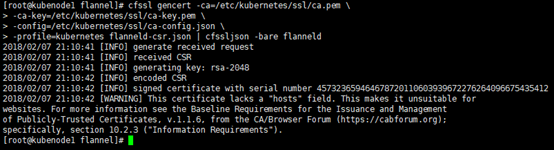
# 分发flanneld.pem,flanneld-key.pem [root@kubenode1 flannel]# scp flanneld.pem flanneld-key.pem root@172.30.200.22:/etc/kubernetes/flannel/ [root@kubenode1 flannel]# scp flanneld.pem flanneld-key.pem root@172.30.200.23:/etc/kubernetes/flannel/
2. 在etcd写入集群Pod网段信息
# 在etcd集群(1个节点操作即可)写入”key-value”,即Pod网段信息,”key”指”${FLANNEL_ETCD_PREFIX}/config”; # etcdctl采用的是etcd v2 api; # 注意其中使用的环境变量,${CLUSTER_CIDR}需要与kube-controller-manager的参数--cluster-cidr一致; [root@kubenode1 flannel]# etcdctl --endpoints=${ETCD_ENDPOINTS} --ca-file=/etc/kubernetes/ssl/ca.pem --cert-file=/etc/kubernetes/flannel/flanneld.pem --key-file=/etc/kubernetes/flannel/flanneld-key.pem set ${FLANNEL_ETCD_PREFIX}/config '{"Network":"'${CLUSTER_CIDR}'", "SubnetLen": 24, "Backend": {"Type": "vxlan"}}'

3. 下载部署flannel
[root@kubenode1 ~]# cd /usr/local/src/ [root@kubenode1 src]# wget https://github.com/coreos/flannel/releases/download/v0.10.0/flannel-v0.10.0-linux-amd64.tar.gz [root@kubenode1 src]# mkdir -p /usr/local/flannel [root@kubenode1 src]# tar -zxvf flannel-v0.10.0-linux-amd64.tar.gz [root@kubenode1 src]# cd /usr/local/flannel/
4. 配置flanneld的systemd unit文件
[root@kubenode1 src]# cd /usr/local/flannel/ [root@kubenode1 flannel]# touch /usr/lib/systemd/system/flanneld.service # EnvironmentFile:这里将flanneld的启动参数放在unit文件之外,修改后不用重载; # ExecStart:启动文件位置,并带上指定参数的变量; # ExecStartPost:启动后需要执行的操作,这里利用mk-docker-opts.sh脚本将分配到flanneld的Pod subnet信息写入到/run/flannel/docker文件中,docker服务启动时调用/run/flannel/docker文件中的参数设置docker0网桥; # RequiredBy:docker.service依赖与flanneld服务; # flanneld使用系统默认路由所在接口封装vxlan与其他节点通信,多网口时可使用--iface选项指定通信接口 [root@kubenode1 flannel]# vim /usr/lib/systemd/system/flanneld.service [Unit] Description=Flanneld overlay address etcd agent Documentation=https://github.com/coreos After=network.target After=network-online.target Wants=network-online.target After=etcd.service Before=docker.service [Service] Type=notify EnvironmentFile=/usr/local/flannel/flanneld.conf ExecStart=/usr/local/flannel/flanneld $FLANNELD_ARGS ExecStartPost=/usr/local/flannel/mk-docker-opts.sh -k DOCKER_NETWORK_OPTIONS -d /run/flannel/docker Restart=on-failure [Install] WantedBy=multi-user.target RequiredBy=docker.service # 启动参数文件,“-etcd-prefix”指定flannel网络配置存储路径,注意与写入etcd集群的“k-v”路径对应 [root@kubenode1 flannel]# touch /usr/local/flannel/flanneld.conf [root@kubenode1 flannel]# vim /usr/local/flannel/flanneld.conf FLANNELD_ARGS="-etcd-cafile=/etc/kubernetes/ssl/ca.pem -etcd-certfile=/etc/kubernetes/flannel/flanneld.pem -etcd-keyfile=/etc/kubernetes/flannel/flanneld-key.pem -etcd-endpoints=https://172.30.200.21:2379,https://172.30.200.22:2379,https://172.30.200.23:2379 -etcd-prefix=/kubernetes/network"
5. 修改docker的systemd unit文件
# 增加EnvironmentFile项:指定启动参数位置,注意与flanneld设定的文件对应; # 修改ExecStart项:unix为开放本地客户端调用dockerd接口,ip地址为开放远端客户端调用dockerd接口,指定参数注意与flanneld设定的参数名对应 [root@kubenode1 flannel]# vim /usr/lib/systemd/system/docker.service [Unit] Description=Docker Application Container Engine Documentation=https://docs.docker.com After=network.target [Service] Type=notify EnvironmentFile=-/run/flannel/docker ExecStart=/usr/bin/dockerd -H unix:///var/run/docker.sock -H 0.0.0.0:2375 $DOCKER_NETWORK_OPTIONS ExecReload=/bin/kill -s HUP $MAINPID LimitNOFILE=infinity LimitNPROC=infinity LimitCORE=infinity TimeoutStartSec=0 Delegate=yes KillMode=process [Install] WantedBy=multi-user.target # docker启动参数文件,创建相应的目录与文件即可,不用编辑; # mk-docker-opts.sh会利用从etcd分配到的信息编辑此文件 [root@kubenode1 flannel]# mkdir -p /run/flannel [root@kubenode1 flannel]# touch /run/flannel/docker
6. 启动flanneld
# docker服务应该在flanneld服务之后启动 [root@kubenode1 flannel]# systemctl daemon-reload [root@kubenode1 flannel]# systemctl enable flanneld [root@kubenode1 flannel]# systemctl stop docker [root@kubenode1 flannel]# systemctl start flanneld [root@kubenode1 flannel]# systemctl start docker
7. 验证
1)网口
# docker0已从etcd获取Pod网段内1个24位subnet的地址,取代默认的172.17.0.0/16的地址; # 对外(除跨主机的容器通信),采用默认的bridge网络,以nat的形式与外部通信; # 同时生成一个flannel.1网口,跨主机的通信即通过flannel.1做vxlan的封装发出; # flannel为每台主机分配独立的24位subnet,flannel.1将这些subnet连接起来,相互之间可路由; # flannel 没有提供隔离 [root@kubenode1 ~]# ip address show

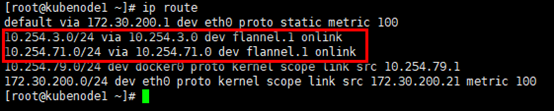
2)路由
# 在其余节点启动flanneld服务后,相关路由会被推送到各host主机; # 以下是kubenode1到kubenode2&kubenode3的路由,通过flannel.1做封装 [root@kubenode1 ~]# ip route
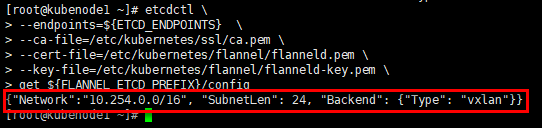
3)查看etcd分配到各flanneld的Pod网段信息
# 集群Pod网段,即写入etcd的Pod网段信息 [root@kubenode1 ~]# etcdctl --endpoints=${ETCD_ENDPOINTS} --ca-file=/etc/kubernetes/ssl/ca.pem --cert-file=/etc/kubernetes/flannel/flanneld.pem --key-file=/etc/kubernetes/flannel/flanneld-key.pem get ${FLANNEL_ETCD_PREFIX}/config
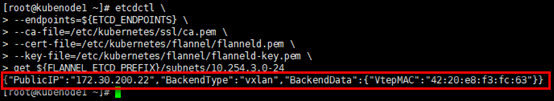
# 已分配的Pod subnet列表 [root@kubenode1 ~]# etcdctl --endpoints=${ETCD_ENDPOINTS} --ca-file=/etc/kubernetes/ssl/ca.pem --cert-file=/etc/kubernetes/flannel/flanneld.pem --key-file=/etc/kubernetes/flannel/flanneld-key.pem ls ${FLANNEL_ETCD_PREFIX}/subnets

# 某Pod subnet对应的flanneld进程监听的ip与网络参数; # 任选1个Pod subnet列表,如10.254.3.0/24,可查询到其所在host节点与vtep mac地址 [root@kubenode1 ~]# etcdctl --endpoints=${ETCD_ENDPOINTS} --ca-file=/etc/kubernetes/ssl/ca.pem --cert-file=/etc/kubernetes/flannel/flanneld.pem --key-file=/etc/kubernetes/flannel/flanneld-key.pem get ${FLANNEL_ETCD_PREFIX}/subnets/10.254.3.0-24
4)ping测试
# iptables input链最后一条规则“-A INPUT -j REJECT --reject-with icmp-host-prohibited”,即不满足input已定义放行的规则,到链的最后则拒绝访问,同时返回"icmp-host-prohibited"消息;而flannel.1之间是通过udp封装的vxlan通信,input链默认未放行udp,导致docker0之间的ping包会被丢弃;
# 不能重启iptables,docker服务启动,或Pod subnet有变更时会向iptables添加规则,重启会使相关规则丢失;
# 同时可以将/etc/sysconfig/iptables中下面两条规则注释掉
[root@kubenode1 ~]# iptables -D INPUT -j REJECT --reject-with icmp-host-prohibited
[root@kubenode1 ~]# iptables -D FORWARD -j REJECT --reject-with icmp-host-prohibited
# ping测试
[root@kubenode1 ~]# ping 10.254.3.1
[root@kubenode1 ~]# ping 10.254.71.1
