Configure authentication
-
Authenticating users
-
IIS authentication
- Anonymous
- ASP.net impersonation
- Basic
transmit username/password between client/server in Base64 encoded but not encrypted. - Digest
username/password are encrypted - Forms
1: without using built-in windows security system
2: use FormsAuthentication.SetAuthCookie to make authentication token available for the rest of the session. - Windows
supported only in microsoft browser
use NTLM/Kerberos
straightforward and easy to implement, especially on intranet. - ASP.net impersonation authentication
independent of authentication mode configured in Web.config file
-
System.Security.Principal.IPrincipal / System.Security.Principal.IIdentity
- WindowsIdentity/WindowsPrincipal
- FormsIdentity/GenericPrincipal
- GenericIdentity/GenericPrinciapl
use AuthorizeAttribute to enforce authentication
- Form authentication + SimpleMembership + WebSecurity
Windows authentication- use Active directory to manage users
- all users are members of your domain
- require users to use IE or Microsoft browser
Form authentication - use standard ASP.net membership provider db schema or your own
Custom authentication - create a custom provider by implementing IIdentity or IPrincipal to interact with underlying authentication mechanism
-
-
Manage user session by cookies
FormsAuthenticationTicket authTicket = new FormsAuthenticationTicket(
1,
userName,
DateTime.Now,
DateTime.Now.AddDays(90),
createPersistentCookie, // a Boolean indicating whether a cookie
// should be created on the user's machine
String.Join(";",rolesArr) //user's roles
);
// add cookie to response stream
string encTicket = FormsAuthentication.Encrypt(authTicket);
System.Web.HttpCookie authCookie = new System.Web.HttpCookie(FormsAuthentication.
FormsCookieName, encTicket);
System.Web.HttpContext.Current.Response.Cookies.Add(authCookie);
-
Configuring membership providers
- use SimpleMembershipProvider/WebSecurity helper classes
-
Creating custom membership providers
- ActiveDirectoryProvider for app use windows authentication
- SqlMembershipProvider for form authentication
Configure and apply authorization
- create roles
- configure roles
configure a SQL membership role provider in Web.config file
use InitializeDatabaseConnection(...) for SimpleMembershipProvider with SimpleRole. - Authorizing roles programmatically
- applying Authorize attribute
- check in code via followings
*RoleProvider.GetRolesForUser, RoleProvider.IsUserInRole, HttpContext.User.IsInRole
*WebSecurity.RequireRoles(...)
- creating custom role providers
- Implementing WCF service authorization
Design and implement claims-based authentication across federated identity stores
- Implementing federated authentication by using Windows Azure Access Control Service (ACS)
ACS features includes:- integrates with Windows Identity Foundation (WIF)
- support well-known identity providers such as Facebook, Microsoft account, Yahoo and Google
- support Active Directory Federation Services (ADFS) 2.0
- support OAuth 2.0, WS-Trust and WS-Federation protocols
- support various token formats, include JSON Web Token (JWT), Security Assertion Markup Language (SAML) and Simple Web Token (SWT)
- provides a web-based management portal
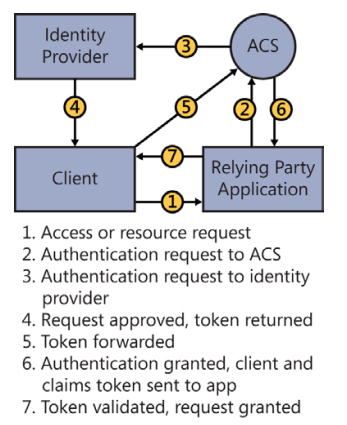
- Creating a custom security token by using WIF
- Handling token formats for SAML and SWT tokens
Manage data integrity
-
encryption terminology
- Encryption: DES, AES
- Hashing: MD5, SHA
- Salting
-
Applying encryption to application data
- Symmetric: AES, DES, RC2, Rijindael, TripleDES
- Asymmetric: DSA, ECDiffieHellman, ECDsa, RSA
using (RijndaelManaged rijndaelManaged = new RijndaelManaged())
{
// assumes that the key and initialization vectors are already configured
CryptoStream crypoStream = new CryptoStream(myManagedStream, rijndaelManaged.
CreateEncryptor(),CryptoStreamMode.Write);
};
using (RijndaelManaged rijndaelManaged = new RijndaelManaged())
{
// assumes that the key and initialization vectors are already configured
CryptoStream crypoStream = new CryptoStream(myManagedStream, rijndaelManaged.
CreateDecryptor(),CryptoStreamMode.Read);
};
-
Applying encryption to the configuraion sections of an application
- DPAPIProtectedConfigurationProvider
- RsaProtectedConfigurationProvider: allow export/import of the keys used for encryption/decryption
- use aspnet_regiis to encrypt/decrypt sections of the Web.confg file.
-
Signing application data to prevent tampering
// create the hash code of the text to sign
SHA1 sha = SHA1.Create();
byte[] hashcode = sha.ComputeHash(TextToConvert);
// use the CreateSignature method to sign the data
DSA dsa = DSA.Create();
byte[] signature = dsa.CreateSignature(hashcode);
// create the hash code of the text to verify
SHA1 sha = SHA1.Create();
byte[] hashcode = sha.ComputeHash(TextToVerify);
// use the VerifySignature method to verify the DSA signature
DSA dsa = DSA.Create();
bool isSignatureValid = dsa.VerifySignature(hashcode, signature);
Implement a secure site with ASP.NET
-
Securing communication by applying SSL/TLS certificates
setup site with certificate and https -
Salt and hash passwords for storage
-
Using HTML encoding to prevent cross-site scripting attacks (AntiXSS Library)
- use @Html.Encode()
- encode the data before saving to db
- use AntiXSS library from NuGet
-
Implementing deferred validation and handle unvalidated requests
-
Preventing SQL injection attacks by parameterizing queries
-
Preventing cross-site request forgeries (XSRFs)
[RequireSession]
[AcceptVerbs(HttpVerbs.Post)]
[HttpPost]
[ValidateAntiForgeryToken]
public ActionResult Login(string username, string password, string remember, string deviceToken, string apid)
{
}
@using (Html.BeginForm("Login", "Authorize"))
{
@Html.AntiForgeryToken();
}
internally cookie is used for XSRF validation.