flask 模仿csrf攻击 与 保护
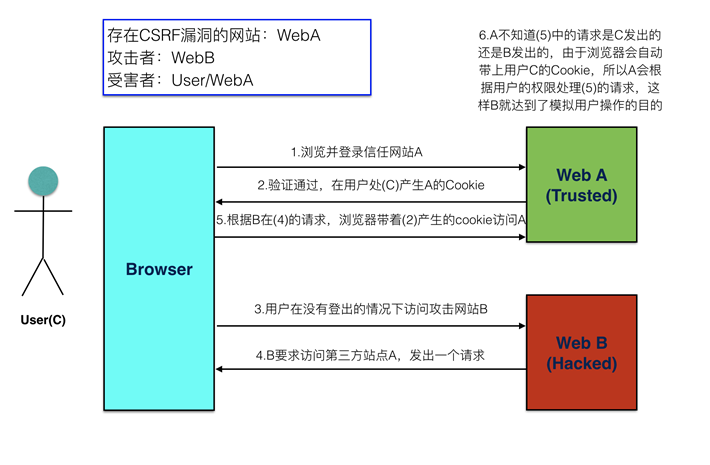
csrf攻击示意图:
现在我们有webA文件如下
login.html
<!DOCTYPE html> <html lang="en"> <head> <meta charset="UTF-8"> <title>登录</title> </head> <body> <h1>我是网站A,登录页面</h1> <form method="post"> <label>用户名:</label><input type="text" name="username" placeholder="请输入用户名"><br/> <label>密码:</label><input type="password" name="password" placeholder="请输入密码"><br/> <input type="submit" value="登录"> </form> </body> </html>
transfer.html
<!DOCTYPE html> <html lang="en"> <head> <meta charset="UTF-8"> <title>转账</title> </head> <body> <h1>我是网站A,转账页面</h1> <form method="post"> <label>账户:</label><input type="text" name="to_account" placeholder="请输入对方账户"><br/> <label>金额:</label><input type="number" name="money" placeholder="请输入转账金额"><br/> <input type="submit" value="转账"> </form> </body> </html>
webA.py
from flask import Flask, render_template, make_response from flask import redirect from flask import request from flask import url_for app = Flask(__name__) @app.route('/', methods=["POST", "GET"]) def index(): if request.method == "POST": # 取到表单中提交上来的参数 username = request.form.get("username") password = request.form.get("password") if not all([username, password]): print('参数错误') else: print(username, password) if username == 'laowang' and password == '1234': # 状态保持,设置用户名到cookie中表示登录成功 response = redirect(url_for('transfer')) response.set_cookie('username', username) return response else: print('密码错误') return render_template('login.html') @app.route('/transfer', methods=["POST", "GET"]) def transfer(): # 从cookie中取到用户名 username = request.cookies.get('username', None) # 如果没有取到,代表没有登录 if not username: return redirect(url_for('index')) if request.method == "POST": to_account = request.form.get("to_account") money = request.form.get("money") print('假装执行转操作,将当前登录用户的钱转账到指定账户') return '转账 %s 元到 %s 成功' % (money, to_account) # 渲染转换页面 response = make_response(render_template('transfer.html')) return response if __name__ == '__main__': app.run(debug=True, port=9000)
webB文件如下
index.html
<!DOCTYPE html> <html lang="en"> <head> <meta charset="UTF-8"> <title>Title</title> </head> <body> <h1>我是网站B</h1> <form method="post" action="http://127.0.0.1:9000/transfer"> <input type="hidden" name="to_account" value="999999"> <input type="hidden" name="money" value="190000"> <input type="submit" value="点击领取优惠券"> </form> </body> </html>
webB.py
from flask import Flask from flask import render_template app = Flask(__name__) @app.route('/') def index(): return render_template('index.html') if __name__ == '__main__': app.run(debug=True, port=8000)
现在我们启动webA.py文件 输入用户名密码
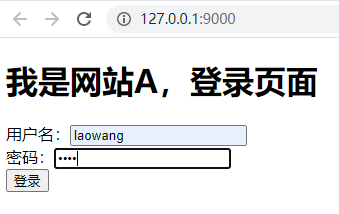
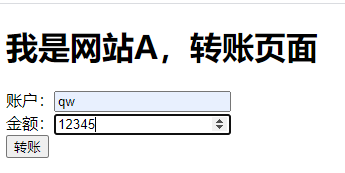
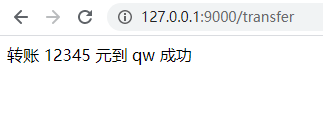
可以看到转账成功
webA不要关闭让用户处于登录状态 然后启动恶意攻击的webB.py

点击一下
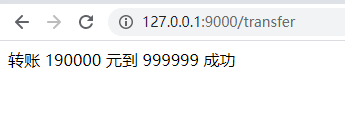
可以看到我们直接让他跳转到用户的转账界面 直接就转账成功了 那有什么秘密呢
<form method="post" action="http://127.0.0.1:9000/transfer"> <input type="hidden" name="to_account" value="999999"> <input type="hidden" name="money" value="190000"> <input type="submit" value="点击领取优惠券"> </form>
其实就是网站b用form表单直接action跳转到了网站a的转账界面 然后将input标签的type设置成了隐藏 当我们点击按钮的时候他就将转账金额和用户提交到了服务器(因为访问输入跟网站a同样的ip及端口默认浏览器也会带上他的cookie所以就能访问成功)
那怎么解决这个问题呢?(只需要更改webA就可以了)
第一步:
利用base64和os创建一个生成48为的随机字符串
def random_csrf_token(): return bytes.decode(base64.b64encode(os.urandom(48)))
第二步:
然后将调用函数并将生成的字符串响应出去并向cookie里面也写入生成的48随机数
csrf_token = random_csrf_token() # 渲染转换页面 response = make_response(render_template('transfer.html', csrf_token=csrf_token))
response.set_cookie("csrf_token", csrf_token)
第三步:
将转账界面加入一个隐藏标签接收生成的48位随机数
<input type="hidden" name="csrf_token" value="{{ csrf_token }}">
第四步:
最后将从前端页面和cookie分别取到的48位随机数进行校验
if request.method == "POST": token1 = request.form.get("csrf_token") token2 = request.cookies.get("csrf_token") if not token1 == token2: return "爬"
再次运行webB 就可以看到转账已经不成功了
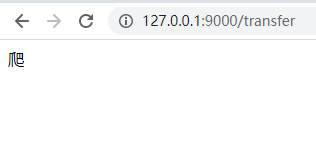
webA更改完代码
login.html
<!DOCTYPE html> <html lang="en"> <head> <meta charset="UTF-8"> <title>登录</title> </head> <body> <h1>我是网站A,登录页面</h1> <form method="post"> <label>用户名:</label><input type="text" name="username" placeholder="请输入用户名"><br/> <label>密码:</label><input type="password" name="password" placeholder="请输入密码"><br/> <input type="submit" value="登录"> </form> </body> </html>
transfer.html
<!DOCTYPE html> <html lang="en"> <head> <meta charset="UTF-8"> <title>转账</title> </head> <body> <h1>我是网站A,转账页面</h1> <form method="post"> <input type="hidden" name="csrf_token" value="{{ scrf_token }}"> <label>账户:</label><input type="text" name="to_account" placeholder="请输入对方账户"><br/> <label>金额:</label><input type="number" name="money" placeholder="请输入转账金额"><br/> <input type="submit" value="转账"> </form> </body> </html>
webA.py
from flask import Flask, render_template, make_response from flask import redirect from flask import request from flask import url_for import base64 import os app = Flask(__name__) def random_csrf_token(): return bytes.decode(base64.b64encode(os.urandom(48))) @app.route('/', methods=["POST", "GET"]) def index(): if request.method == "POST": # 取到表单中提交上来的参数 username = request.form.get("username") password = request.form.get("password") if not all([username, password]): print('参数错误') else: print(username, password) if username == 'laowang' and password == '1234': # 状态保持,设置用户名到cookie中表示登录成功 response = redirect(url_for('transfer')) response.set_cookie('username', username) return response else: print('密码错误') return render_template('login.html') @app.route('/transfer', methods=["POST", "GET"]) def transfer(): # 从cookie中取到用户名 username = request.cookies.get('username', None) # 如果没有取到,代表没有登录 if not username: return redirect(url_for('index')) if request.method == "POST": token1 = request.form.get("csrf_token") token2 = request.cookies.get("csrf_token") if not token1 == token2: return "爬" to_account = request.form.get("to_account") money = request.form.get("money") print('假装执行转操作,将当前登录用户的钱转账到指定账户') return '转账 %s 元到 %s 成功' % (money, to_account) csrf_token = random_csrf_token() # 渲染转换页面 response = make_response(render_template('transfer.html', csrf_token=csrf_token)) response.set_cookie("csrf_token", csrf_token) return response if __name__ == '__main__': app.run(debug=True, port=9000)