一、实验目的
在实验 2 的基础上进一步熟悉 Mininet 自定义拓扑脚本,以及与损耗率相关的设
定;初步了解 Mininet 安装时自带的 POX 控制器脚本编写,测试路径损耗率。
二、实验任务
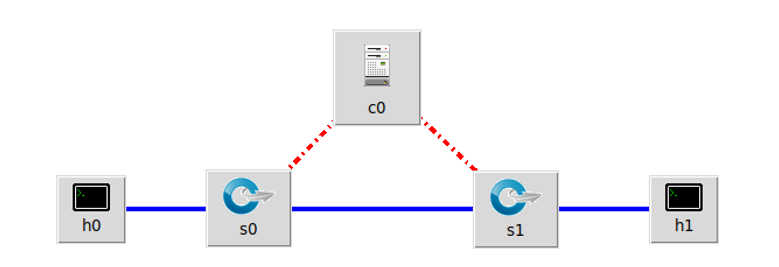
h0 向 h1 发送数据包,由于在 Mininet 脚本中设置了连接损耗率,在传输过程中
会丢失一些包,本次实验的目的是展示如何通过控制器计算路径损耗速率(h0
s0-s1-h1)。这里假设控制器预先知道网络拓扑。控制器将向 s0 和 s1 发送
flow_stats_request,当控制器接收到来自 s0 的 response 时,将特定流的数据包
数保存在 input_pkts 中,当控制器接收到来自 s1 的 response 时,将接收到特定
流的数据包数保存在 output_pkts 中,差值就是丢失的数据包数量。
基于上述拓扑,编写 Mininet 脚本,设置特定的交换机间的路径损耗速率,然后
编写 POX 控制器脚本,实现对路径的损耗率的测量。
三、实验步骤
1. 实验环境
安装了 Ubuntu 18.04.5 Desktop amd64 的虚拟机
2. 实验过程
SDNLAB 实验参考资料:https://www.sdnlab.com/15100.html
(1)新建并编辑 pox 脚本 flowstat.py:
在 pox 安装目录下(Mininet 完整安装包含了 pox)执行以下命令运行 pox 脚本
$ ./pox.py flowstat
现在一起看下 flowstat.py 的关键代码:
第 7 行开始,让 h0 ping h1,监测 s0 和 s1 之间的链路。
如果匹配到以太网类型的包头(0x0800),并且数据包的目的 IP 地址是192.168.123.2(对照后面 Mininet 的脚本发现是 h1), 并且连接到控制器的数据平面设备 id 是 s0(h0 ping h1,链路 s0-s1 上数据包是从 s0 流向 s1,s0 为源,s1 为目的地), 执行 input_pkts = f.packet_count,把数据包数量存入input_pkts;
同理,如果连接到控制器的数据平面设备 id 是 s1,执行 output_pkts = f.packet_count,把数据包数量存入 output_pkts。
最后求 input_pkts 和 output_pkts 的差值。一般情况下差值为正,说明链路上数据包有损耗。
#!/usr/bin/python
# Copyright 2012 William Yu
# wyu@ateneo.edu
#
# This file is part of POX.
#
# POX is free software: you can redistribute it and/or modify
# it under the terms of the GNU General Public License as published by
# the Free Software Foundation, either version 3 of the License, or
# (at your option) any later version.
#
# POX is distributed in the hope that it will be useful,
# but WITHOUT ANY WARRANTY; without even the implied warranty of
# MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
# GNU General Public License for more details.
#
# You should have received a copy of the GNU General Public License
# along with POX. If not, see <http://www.gnu.org/licenses/>.
#
"""
This is a demonstration file created to show how to obtain flow
and port statistics from OpenFlow 1.0-enabled switches. The flow
statistics handler contains a summary of web-only traffic.
"""
# standard includes
from pox.core import core
from pox.lib.util import dpidToStr
import pox.openflow.libopenflow_01 as of
from pox.lib.addresses import IPAddr, EthAddr
# include as part of the betta branch
from pox.openflow.of_json import *
from pox.lib.recoco import Timer
import time
log = core.getLogger()
src_dpid = 0
dst_dpid = 0
input_pkts = 0
output_pkts = 0
def getTheTime(): #fuction to create a timestamp
flock = time.localtime()
then = "[%s-%s-%s" %(str(flock.tm_year),str(flock.tm_mon),str(flock.tm_mday))
if int(flock.tm_hour)<10:
hrs = "0%s" % (str(flock.tm_hour))
else:
hrs = str(flock.tm_hour)
if int(flock.tm_min)<10:
mins = "0%s" % (str(flock.tm_min))
else:
mins = str(flock.tm_min)
if int(flock.tm_sec)<10:
secs = "0%s" % (str(flock.tm_sec))
else:
secs = str(flock.tm_sec)
then +="]%s.%s.%s" % (hrs,mins,secs)
return then
# handler for timer function that sends the requests to all the
# switches connected to the controller.
def _timer_func ():
for connection in core.openflow._connections.values():
connection.send(of.ofp_stats_request(body=of.ofp_flow_stats_request()))
connection.send(of.ofp_stats_request(body=of.ofp_port_stats_request()))
log.debug("Sent %i flow/port stats request(s)", len(core.openflow._connections))
# handler to display flow statistics received in JSON format
# structure of event.stats is defined by ofp_flow_stats()
def _handle_flowstats_received (event):
#stats = flow_stats_to_list(event.stats)
#log.debug("FlowStatsReceived from %s: %s", dpidToStr(event.connection.dpid), stats)
global src_dpid, dst_dpid, input_pkts, output_pkts
#print "src_dpid=", dpidToStr(src_dpid), "dst_dpid=", dpidToStr(dst_dpid)
for f in event.stats:
if f.match.dl_type==0x0800 and f.match.nw_dst==IPAddr("192.168.123.2") and f.match.nw_tos==0x64 and event.connection.dpid==src_dpid:
#print "input: ", f.byte_count, f.packet_count
input_pkts = f.packet_count
if f.match.dl_type==0x0800 and f.match.nw_dst==IPAddr("192.168.123.2") and f.match.nw_tos==0x64 and event.connection.dpid==dst_dpid:
#print "output: ", f.byte_count, f.packet_count
output_pkts = f.packet_count
if input_pkts !=0:
print getTheTime(), "Path Loss Rate =", (input_pkts-output_pkts)*1.0/input_pkts*100, "%"
# handler to display port statistics received in JSON format
def _handle_portstats_received (event):
#print "
<<<STATS-REPLY: Return PORT stats for Switch", event.connection.dpid,"at ",getTheTime()
#for f in event.stats:
#if int(f.port_no)<65534:
#print " PortNo:", f.port_no, " Fwd's Pkts:", f.tx_packets, " Fwd's Bytes:", f.tx_bytes, " Rc'd Pkts:", f.rx_packets, " Rc's Bytes:", f.rx_bytes
#print " PortNo:", f.port_no, " TxDrop:", f.tx_dropped, " RxDrop:", f.rx_dropped, " TxErr:", f.tx_errors, " RxErr:", f.rx_errors, " CRC:", f.rx_crc_err, " Coll:", f.collisions
stats = flow_stats_to_list(event.stats)
log.debug("PortStatsReceived from %s: %s", dpidToStr(event.connection.dpid), stats)
def _handle_ConnectionUp (event):
global src_dpid, dst_dpid
print "ConnectionUp: ", dpidToStr(event.connection.dpid)
for m in event.connection.features.ports:
if m.name == "s0-eth0":
src_dpid = event.connection.dpid
elif m.name == "s1-eth0":
dst_dpid = event.connection.dpid
msg = of.ofp_flow_mod()
msg.priority =1
msg.idle_timeout = 0
msg.match.in_port =1
msg.actions.append(of.ofp_action_output(port = of.OFPP_ALL))
event.connection.send(msg)
msg = of.ofp_flow_mod()
msg.priority =1
msg.idle_timeout = 0
msg.match.in_port =2
msg.actions.append(of.ofp_action_output(port = of.OFPP_ALL))
event.connection.send(msg)
msg = of.ofp_flow_mod()
msg.priority =10
msg.idle_timeout = 0
msg.hard_timeout = 0
msg.match.dl_type = 0x0800
msg.match.nw_tos = 0x64
msg.match.in_port=1
msg.match.nw_dst = "192.168.123.2"
msg.actions.append(of.ofp_action_output(port = 2))
event.connection.send(msg)
msg = of.ofp_flow_mod()
msg.priority =10
msg.idle_timeout = 0
msg.hard_timeout = 0
msg.match.dl_type = 0x0800
msg.match.nw_tos = 0x64
msg.match.nw_dst = "192.168.123.1"
msg.actions.append(of.ofp_action_output(port = 1))
event.connection.send(msg)
# main functiont to launch the module
def launch ():
# attach handsers to listners
core.openflow.addListenerByName("FlowStatsReceived",
_handle_flowstats_received)
core.openflow.addListenerByName("PortStatsReceived",
_handle_portstats_received)
core.openflow.addListenerByName("ConnectionUp", _handle_ConnectionUp)
# timer set to execute every five seconds
Timer(1, _timer_func, recurring=True)

再执行命令运行 Mininet 脚本 mymininet3.py
$ sudo python mymininet3.py

如果修改代码中 s0 和 s1 之间链路的丢包率为 10。
info( "*** Creating links " ) linkopts0=dict(bw=100, delay='1ms', loss=0) linkopts1=dict(bw=100, delay='1ms', loss=10) link0=TCLink( h0, switch, **linkopts0) link1 = TCLink( switch, switch1, **linkopts1) link2 = TCLink( h1, switch1, **linkopts0)
重新运行 Mininet 脚本 mymininet3.py,20 秒时间的 ping 过程中有 icmp_seq ping 不通
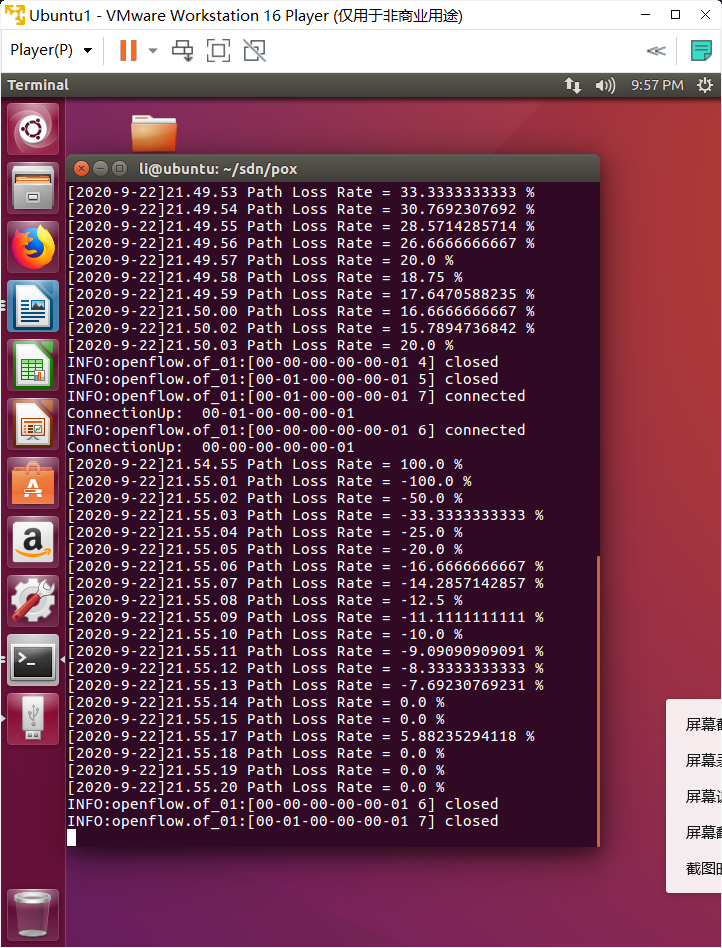
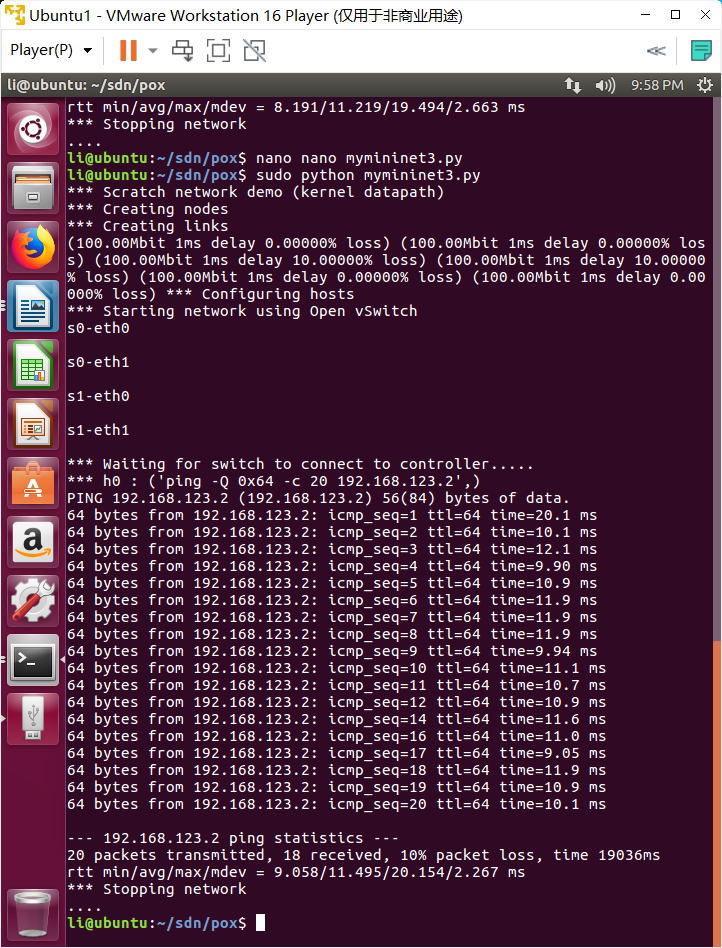
四、实验要求
(已在实验步骤中体现)
-
根据实验步骤重复上述实验。
-
在博客园发表一篇博客,记录主要步骤。
五、实验总结
这次实验总体来说较为简单,遇到的一个最大问题就是在输入./pox.py flowstat 之后,运行了控制器,但是却不知道怎么继续运行mymininet3.py,经过半小时的冥思苦想,最终我凭借自己过人的智慧想到了可以新建一个terminal,然后在新的terminal里面运行mymininet3.py,虽然这个问题非常简单,但是对于类似我这样的计算机小白来说,还是略有深度的。这次实验也是收获满满,期待下次实验能给我带来不一样的惊喜。