漏洞描述
近日,国外安全团队发布安全公告称,在 polkit 的 pkexec 程序中发现了一个本地权限提升漏洞。pkexec 应用程序是一个 setuid 工具,旨在允许非特权用户根据预定义的策略以特权用户身份运行命令。由于当前版本的 pkexec 无法正确处理调用参数计数,并最终会尝试将环境变量作为命令执行。攻击者可以通过控制环境变量,从而诱导 pkexec 执行任意代码。利用成功后,可导致非特权用户获得管理员权限。CVE-2021-4034
polkit 的 pkexec 存在本地权限提升漏洞,已获得普通权限的攻击者可通过此漏洞获取root权限。
目前漏洞POC已被泄露,攻击者利用该漏洞可导致恶意用户权限提升等危害
该漏洞CVSS评分:7.8
危害等级:高危
【受影响版本】
由于为系统预装工具,目前主流Linux版本均受影响
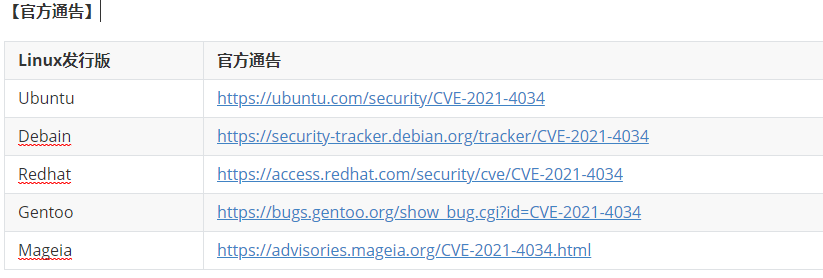
【官方通告】
CentOS系列:
CentOS 6:polkit-0.96-11.el6_10.2
CentOS 7:polkit-0.112-26.el7_9.1
CentOS 8.0:polkit-0.115-13.el8_5.1
CentOS 8.2:polkit-0.115-11.el8_2.2
CentOS 8.4:polkit-0.115-11.el8_4.2
Ubuntu系列:
Ubuntu 20.04 LTS:policykit-1 - 0.105-26ubuntu1.2
Ubuntu 18.04 LTS:policykit-1 - 0.105-20ubuntu0.18.04.6
Ubuntu 16.04 ESM:policykit-1 - 0.105-14.1ubuntu0.5+esm1
Ubuntu 14.04 ESM:policykit-1 - 0.105-4ubuntu3.14.04.6+esm1
【修复建议】
目前各Linux发行版官方均已给出安全补丁,建议用户尽快升级至安全版本,或参照官方说明措施进行缓解,CentOS、Ubuntu及Debian用户可参考以下链接:
https://ubuntu.com/security/CVE-2021-4034
https://access.redhat.com/security/cve/CVE-2021-4034
https://security-tracker.debian.org/tracker/CVE-2021-4034
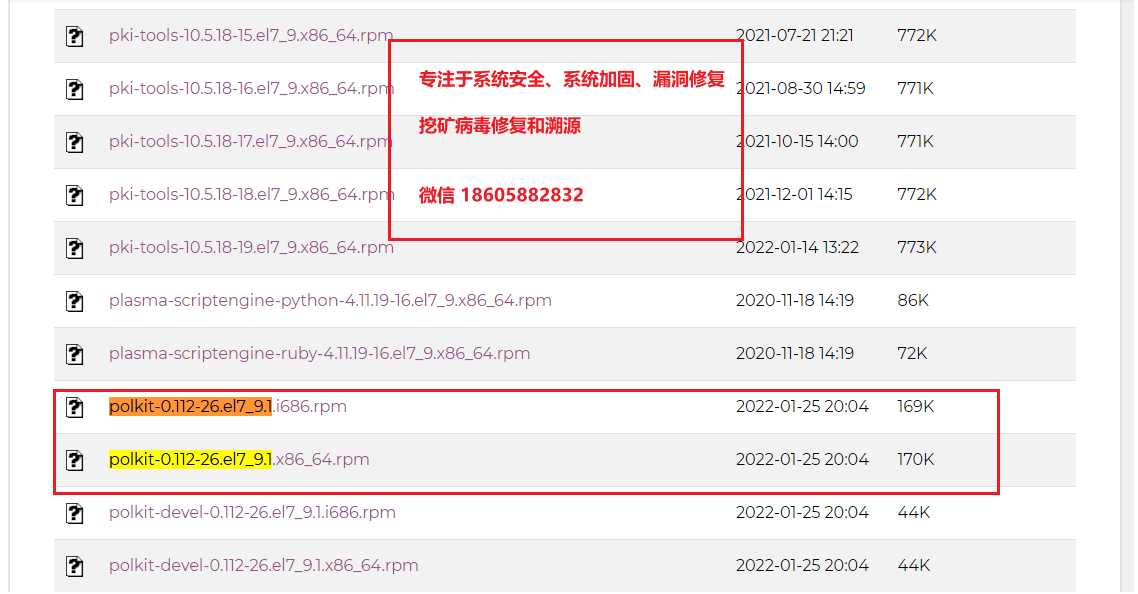
截止到目前2022/01/27, CentOS目前已提供安全更新包
下载地址:http://mirror.centos.org/centos/7/updates/x86_64/Packages/
版本漏洞验证
通过以下命令可查看Polkit是否为安全版本
[root@node01 ~]# rpm -qa polkit
polkit-0.112-26.el7_9.1.x86_64
漏洞复现POC--修复前
[root@node02 ~]# cat /etc/redhat-release
CentOS Linux release 7.6.1810 (Core)
[root@node02 ~]# uname -a
Linux node02 3.10.0-957.el7.x86_64 #1 SMP Thu Nov 8 23:39:32 UTC 2018 x86_64 x86_64 x86_64 GNU/Linux
[root@node02 ~]# rpm -aq | grep polkit
polkit-pkla-compat-0.1-4.el7.x86_64
polkit-0.112-18.el7.x86_64
[root@node02 ~]# useradd liangliang
[root@node02 ~]# passwd liangliang
Changing password for user liangliang.
New password:
Retype new password:
passwd: all authentication tokens updated successfully.
[root@node02 ~]# ls
10000.sh 1000.sh anaconda-ks.cfg cve-2021-4034-poc
[root@node02 ~]# cp cve-2021-4034-poc /home/liangliang/
[root@node02 ~]# chmod 755 /home/liangliang/cve-2021-4034-poc
[root@node02 ~]# su - liangliang
[liangliang@node02 ~]$ ./cve-2021-4034-poc
sh-4.2#
sh-4.2#
sh-4.2# id
uid=0(root) gid=0(root) groups=0(root),2334(liangliang)
sh-4.2# cat /etc/passwd
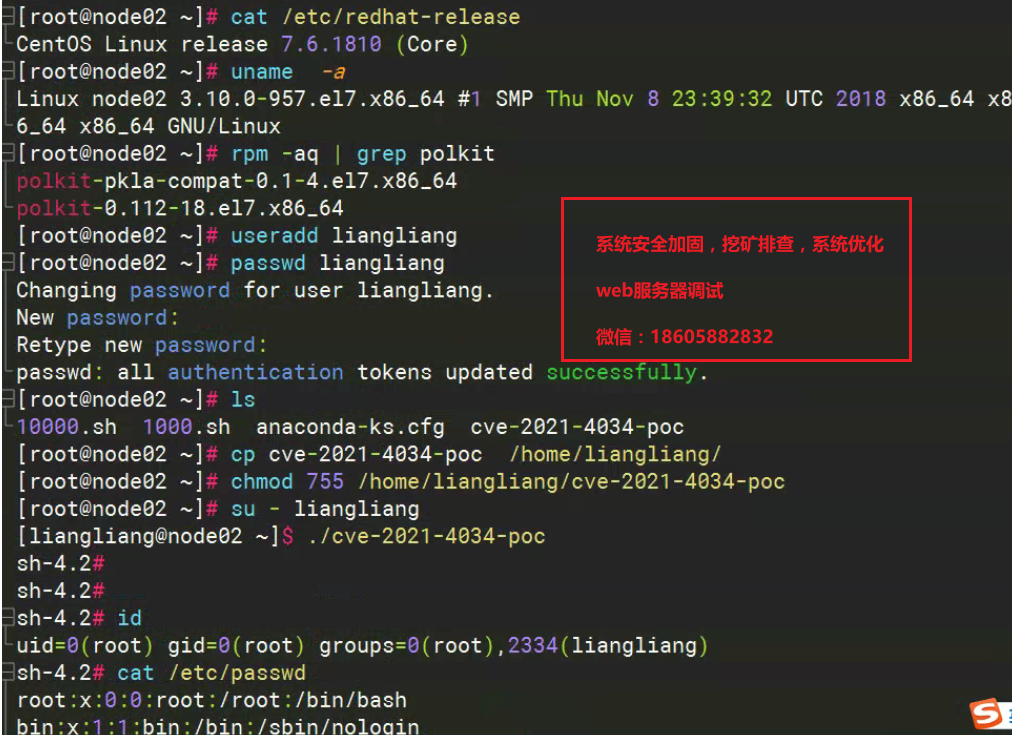
说明:普通用户可以使用POC程序可以直接提权到root,漏洞风险非常高。
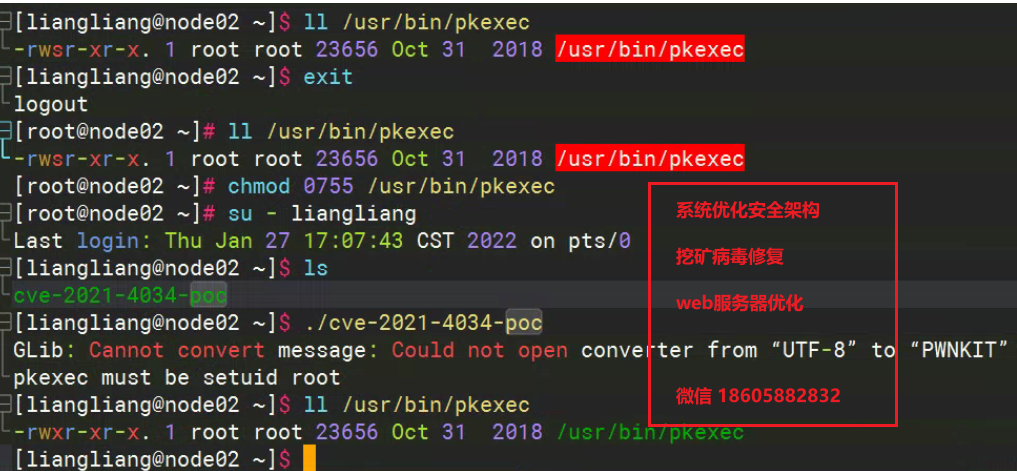
漏洞临时修复方案pkexec权限调整
漏洞临时缓解措施,调整pkexec权限,临时缓解措施修复前和修复后s位
[root@node02 ~]# stat /usr/bin/pkexec #####为修改之前信息
File: ‘/usr/bin/pkexec’
Size: 23656 Blocks: 48 IO Block: 4096 regular file
Device: 802h/2050d Inode: 201351697 Links: 1
Access: (4755/-rwsr-xr-x) Uid: ( 0/ root) Gid: ( 0/ root)
Access: 2022-01-27 17:20:13.235841977 +0800
Modify: 2018-10-31 06:26:01.000000000 +0800
Change: 2022-01-27 17:20:03.518723115 +0800
Birth: -
[root@node02 ~]# ll /usr/bin/pkexec
-rwsr-xr-x. 1 root root 23656 Oct 31 2018 /usr/bin/pkexec
[liangliang@node02 ~]$ ll /usr/bin/pkexec
-rwxr-xr-x. 1 root root 23656 Oct 31 2018 /usr/bin/pkexec
[liangliang@node02 ~]$ exit
logout
[root@node02 ~]# stat /usr/bin/pkexec #####为修改之后信息
File: ‘/usr/bin/pkexec’
Size: 23656 Blocks: 48 IO Block: 4096 regular file
Device: 802h/2050d Inode: 201351697 Links: 1
Access: (0755/-rwxr-xr-x) Uid: ( 0/ root) Gid: ( 0/ root) ###s权限去掉
Access: 2022-01-27 17:22:13.235841977 +0800
Modify: 2018-10-31 06:26:01.000000000 +0800
Change: 2022-01-27 17:22:03.518723115 +0800
Birth: -
漏洞彻底修复方法之在线升级
修复建议:CentOS用户官方源更新采用如下命令升级到安全版本或更高版本:
yum clean all && yum makecache
yum update polkit -y
[root@node01 ~]# yum update polkit -y
Loaded plugins: fastestmirror
Loading mirror speeds from cached hostfile
Resolving Dependencies
--> Running transaction check
---> Package polkit.x86_64 0:0.112-18.el7 will be updated
---> Package polkit.x86_64 0:0.112-26.el7_9.1 will be an update
--> Finished Dependency Resolution
Dependencies Resolved
===================================================================================================
Package Arch Version Repository Size
===================================================================================================
Updating:
polkit x86_64 0.112-26.el7_9.1 updates 170 k
Transaction Summary
===================================================================================================
Upgrade 1 Package
Total download size: 170 k
Downloading packages:
Delta RPMs disabled because /usr/bin/applydeltarpm not installed.
polkit-0.112-26.el7_9.1.x86_64.rpm | 170 kB 00:00:00
Running transaction check
Running transaction test
Transaction test succeeded
Running transaction
Updating : polkit-0.112-26.el7_9.1.x86_64 1/2
Cleanup : polkit-0.112-18.el7.x86_64 2/2
Verifying : polkit-0.112-26.el7_9.1.x86_64 1/2
Verifying : polkit-0.112-18.el7.x86_64 2/2
Updated:
polkit.x86_64 0:0.112-26.el7_9.1
Complete!
[root@node01 ~]#
[root@node01 ~]# rpm -aq | grep polkit
polkit-pkla-compat-0.1-4.el7.x86_64
polkit-0.112-26.el7_9.1.x86_64
[root@node01 ~]#
验证结果
[lianglab@node01 tmp]$ ./cve-2021-4034-poc
touch: cannot touch ‘GCONV_PATH=./pwnkit’: Permission denied
chmod: changing permissions of ‘GCONV_PATH=./pwnkit’: Operation not permitted
sh: pwnkit/gconv-modules: Permission denied
Segmentation fault (core dumped)
[lianglab@node01 tmp]$
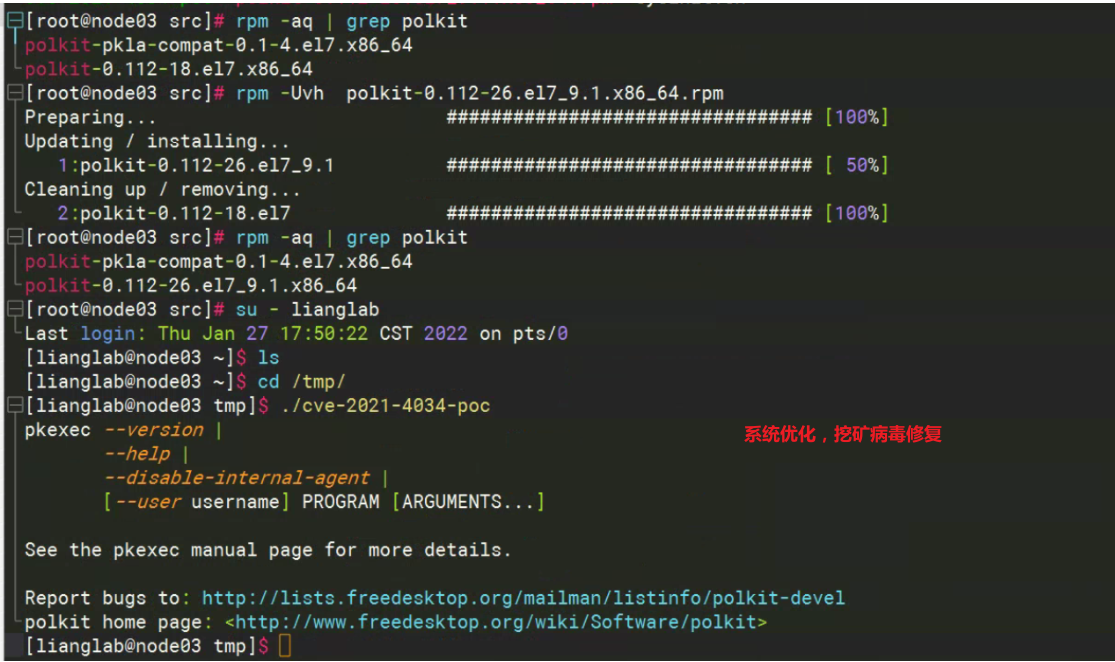
漏洞彻底修复方法之离线升级
wget http://mirror.centos.org/centos/7/updates/x86_64/Packages/polkit-0.112-26.el7_9.1.x86_64.rpm
rpm -Uvh polkit-0.112-26.el7_9.1.x86_64.rpm
rpm -aq | grep polkit #查看Polkit是否为安全版本
./cve-2021-4034-poc #验证漏洞poc
[root@node03 src]# ls
cve-2021-4034-poc polkit-0.112-26.el7_9.1.x86_64.rpm sysinit.sh
[root@node03 src]# rpm -aq | grep polkit
polkit-pkla-compat-0.1-4.el7.x86_64
polkit-0.112-18.el7.x86_64
[root@node03 src]# rpm -Uvh polkit-0.112-26.el7_9.1.x86_64.rpm
Preparing... ################################# [100%]
Updating / installing...
1:polkit-0.112-26.el7_9.1 ################################# [ 50%]
Cleaning up / removing...
2:polkit-0.112-18.el7 ################################# [100%]
[root@node03 src]# rpm -aq | grep polkit
polkit-pkla-compat-0.1-4.el7.x86_64
polkit-0.112-26.el7_9.1.x86_64
[root@node03 src]# su - lianglab
Last login: Thu Jan 27 17:50:22 CST 2022 on pts/0
[lianglab@node03 ~]$ ls
[lianglab@node03 ~]$ cd /tmp/
[lianglab@node03 tmp]$ ./cve-2021-4034-poc
pkexec --version |
--help |
--disable-internal-agent |
[--user username] PROGRAM [ARGUMENTS...]
See the pkexec manual page for more details.
Report bugs to: http://lists.freedesktop.org/mailman/listinfo/polkit-devel
polkit home page: <http://www.freedesktop.org/wiki/Software/polkit>
[lianglab@node03 tmp]$
漏洞复现POC--修复后
1、临时缓解措施,修改/usr/bin/pkexec后
[liangliang@node02 ~]$ ./cve-2021-4034-poc
GLib: Cannot convert message: Could not open converter from “UTF-8” to “PWNKIT”
pkexec must be setuid root
[liangliang@node02 ~]$ ll /usr/bin/pkexec
-rwxr-xr-x. 1 root root 23656 Oct 31 2018 /usr/bin/pkexec
2、安装官方提供的升级包
[root@node01 tmp]# ./cve-2021-4034-poc
pkexec --version |
--help |
--disable-internal-agent |
[--user username] PROGRAM [ARGUMENTS...]
See the pkexec manual page for more details.
Report bugs to: http://lists.freedesktop.org/mailman/listinfo/polkit-devel
polkit home page: <http://www.freedesktop.org/wiki/Software/polkit>
[root@node01 tmp]# rpm -aq | grep polkit
polkit-pkla-compat-0.1-4.el7.x86_64
polkit-0.112-26.el7_9.1.x86_64
[root@node01 tmp]# stat /usr/bin/pkexec
File: ‘/usr/bin/pkexec’
Size: 27672 Blocks: 56 IO Block: 4096 regular file
Device: 802h/2050d Inode: 201732651 Links: 1
Access: (4755/-rwsr-xr-x) Uid: ( 0/ root) Gid: ( 0/ root)
Access: 2022-01-27 17:38:54.182253858 +0800
Modify: 2022-01-26 03:42:49.000000000 +0800
Change: 2022-01-27 14:22:41.682719484 +0800
Birth: -
[root@node01 tmp]#
[lianglab@node01 tmp]$ ./cve-2021-4034-poc
touch: cannot touch ‘GCONV_PATH=./pwnkit’: Permission denied
chmod: changing permissions of ‘GCONV_PATH=./pwnkit’: Operation not permitted
sh: pwnkit/gconv-modules: Permission denied
Segmentation fault (core dumped)
[lianglab@node01 tmp]$
https://access.redhat.com/errata/RHSA-2022:0274
截止到目前2022/01/26, CentOS目前已提供安全更新包
广告时间
- 关于我 :全国7*24高效代维服务
- 微信:foreverops
- QQ:867266199
- 淘宝店:全国7*24高效代维服务
- 全国高效代维:为中小型企业,提供云计算咨询代维、架构设计、降低成本。