1. Introduction
- 保护软件的安全性措施,作为值得信赖的安全锚,
- 安全地生成,存储和处理安全性关键材料屏蔽任何潜在的恶意软件,?
- 通过运用有效的限制硬件篡改攻击的可能性篡改保护措施,?
- 加快保障措施,通过应用专门的加密硬件,
- 通过应用高度优化的专用电路,而不是昂贵的通用硬件减少对大批量的安保费用。
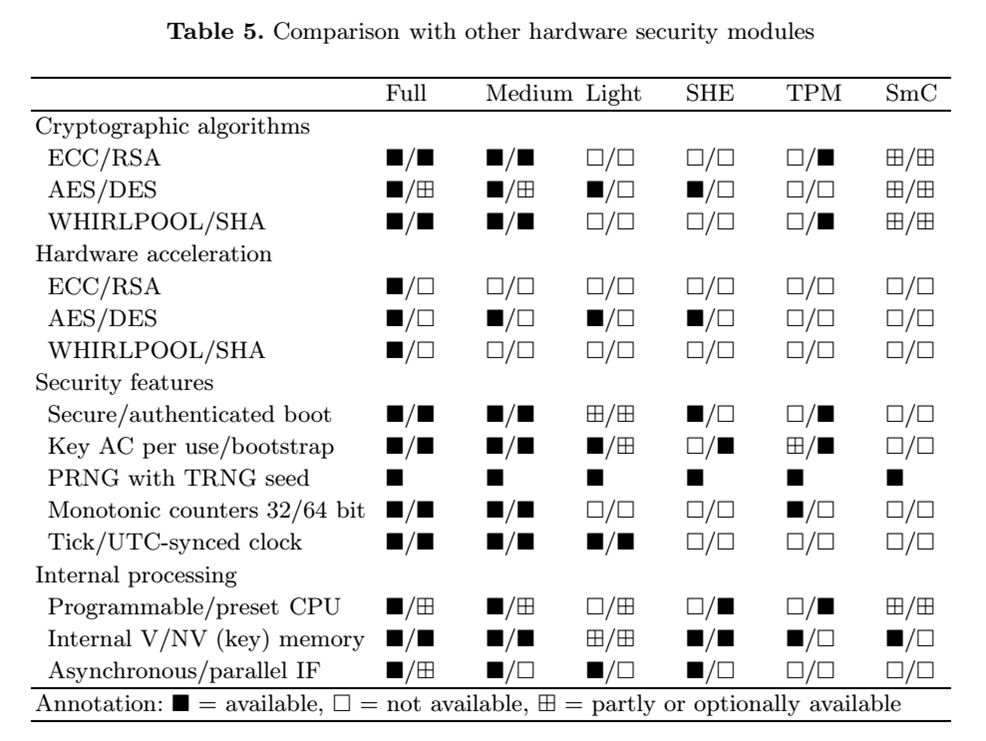
1.2. 对比
2. Architecture
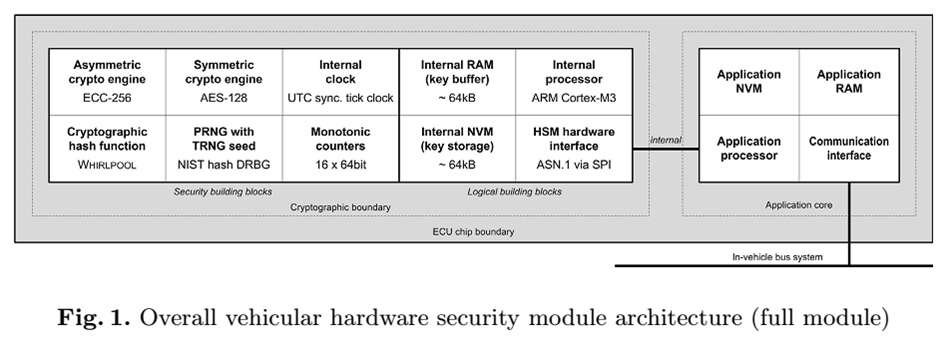
2.1. Hardware Security Building Blocks
- §Asymmetric crypto engine
- §Symmetric crypto engine
- §Cryptographic hash function
- §Pseudo random number generator (PRNG)
- §Internal clock
- §Monotonic counters
2.2. Hardware Security Logic and Functionality
- §Key management
- §Secure boot and authenticated boot
- §Secure clock
- §Administration and audit
References:
- Wolf, Marko, and Timo Gendrullis. "Design, implementation, and evaluation of a vehicular hardware security module." Information Security and Cryptology-ICISC 2011. Springer Berlin Heidelberg, 2012. 302-318.
版权所有,侵权必究,如需使用请与作者本人联系。