这两天记录两个案例,其分析方法是很巧妙的,将来应该会用得上:
1、崩溃

1 Version:ANDA5.3.0.100473/9000001 2 DEBUG MODE LOG !!! 3 dic:C04010001001 4 diu:a1341481c8f080f45527fb6c4e3c2d79 5 diu2:45dfdb870bdfffffffe8 6 diu3:3148609ec457402285194e2ff46f9f35-a47c8a008a86e4ba302eb234e80bbd40 7 adiu:hhqhfikoqfccd662d0000ec239a894 8 session:331125965 9 GLogSpyInitializationID:5683370993648546693 10 tid:YJu/abds14gDACIebqvgz0w9 11 DeviceName:tucana 12 Manufacture:Xiaomi 13 Model:MI CC9 Pro Premium Edition 14 FeatureCode:F42EE6129BEAB77316266BF2F84CBF18_795210673A3E1500D555A194EDA2AA99 15 Cpu:Qualcomm Technologies, Inc SM7150/8/300-1804MHZ 16 Memorysize:7567MB 17 Resolution:2268*1036 18 Android-Version:11 19 Android-SDK_INT:30 20 DumpcrashVersion:2.0.0.10025 21 encrypt:nb 22 DeviceID: 23 DeviceRoot:false 24 Foreground:true 25 BuildPlatform:android_armeabi_v7a 26 InstalledTime:2021-06-29 09:57:41.4 27 ExceptionTime:2021-06-29 11:26:25 28 AmapProcessStartTime:2021-06-29 11:26:04 29 ApplicationInitTime:2021-06-29 11:26:04 30 DataFreeSize:107653976064 31 PID:15768 32 ProcessMemeryInfo:235546/9575/102023/123392/536870912/1097,0,1660,964,612,0,84,120,2,3032,0,3040,3032,8,0,0,8,0,0,0,0,0,0,0,0,0,0,6,0,24,0,12,0,12,0,0,49516,0,49516,49516,0,0,0,0,0,44,0,388,0,348,40,0,4,0,54583,42820,86136,3380,516,42820,39420,2364,11,2487,720,31812,0,0,720,31092,0,0,131,0,3068,0,0,0,3068,0,0,2908,2072,5816,0,0,2072,3744,0,0,4677,1492,7024,928,0,1492,4604,12,0,719,0,13040,0,8,0,13032,88,0,3074,24,11980,2568,8220,24,1168,4064,158,198,0,2060,8,16,4,2032,4,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,4624,0,4624,4624,0,0,0,0,0,3920,0,3948,3920,12,0,16,1612,52,963,0,1576,920,460,8,188,1872,73,68,0,68,68,0,0,0,0,0,606,0,904,592,228,0,84,112,2,137,0,184,136,48,0,0,8,0,2,0,96,0,96,0,0,0,0,120,0,236,4,232,0,0,0,0,0,0,0,0,0,0,0,0,0,232,0,240,232,8,0,0,0,0,0,0,16,0,0,0,16,0,0,1826,40,2752,928,0,40,1784,12,0,2851,1452,4256,0,0,1452,2804,0,0,1136,0,1140,1132,0,0,8,0,0,1938,24,10840,1436,8220,24,1160,4064,158 33 ExternalStoragePath:unknown 34 ExternalStorageSize:0 35 InternalStoragePath:/storage/emulated/0/amapauto9/Log 36 InternalStorageSize:107653976064 37 ABI:arm64-v8a 38 VMHeap:512m 39 NetworkType:4 40 Operator:46000 41 CurrentCity:110000 42 Debugable:0 43 FingerPrint:Xiaomi/tucana/tucana:11/RKQ1.200826.002/V12.5.2.0.RFDCNXM:user/release-keys 44 Tag:6729ff5a7f14abc45c3061b614d5d404:1bbb8da5d87998e99ffdd88620371ebe 45 Exception:(5.3.0.100473)Build fingerprint: 'Xiaomi/tucana/tucana:11/RKQ1.200826.002/V12.5.2.0.RFDCNXM:user/release-keys' 46 Revision: '0' 47 pid: 15768, tid: 15907, name: Map-Logical-0 >>> com.autonavi.amapauto <<< 48 signal 11 (SIGSEGV), code -6 (SI_TKILL), fault addr -------- 49 r0 b471b1a0 r1 c59504dc r2 00000000 r3 bafd8aa8 50 r4 c04a1e5c r5 c04a0664 r6 b8ec96e0 r7 bafd8b80 51 r8 b59e25d0 r9 c4d6c760 r10 b8ec96e0 r11 c4d6c760 52 ip c27ca29d sp bafd8b18 lr bffc6087 pc c59504dc 53 backtrace: 54 #00 pc 003884dc /data/app/~~d8KzEkZTtsSssN_B4vVMcg==/com.autonavi.amapauto-kFJ1sDolAyzDUG6nLuIaKw==/lib/arm/libbase_utils.so 55 stack: 56 bafd8ad8 00000001 57 bafd8adc 00000001 58 bafd8ae0 00000000 59 bafd8ae4 00000003 60 bafd8ae8 00000000 61 bafd8aec ba000101 [anon:libc_malloc] 62 bafd8af0 bd2e32fc [anon:libc_malloc] 63 bafd8af4 50399d07 [anon:dalvik-main space (region space)] 64 bafd8af8 b59e25d0 [anon:libc_malloc] 65 bafd8afc bafd8bb4 [anon:stack_and_tls:15907] 66 bafd8b00 c4d6c760 [anon:libc_malloc] 67 bafd8b04 c04a1e5c /data/app/~~d8KzEkZTtsSssN_B4vVMcg==/com.autonavi.amapauto-kFJ1sDolAyzDUG6nLuIaKw==/lib/arm/libGbl.so 68 bafd8b08 c04a0664 /data/app/~~d8KzEkZTtsSssN_B4vVMcg==/com.autonavi.amapauto-kFJ1sDolAyzDUG6nLuIaKw==/lib/arm/libGbl.so 69 bafd8b0c b8ec96e0 [anon:libc_malloc] 70 bafd8b10 bafd8b80 [anon:stack_and_tls:15907] 71 bafd8b14 bffc6011 /data/app/~~d8KzEkZTtsSssN_B4vVMcg==/com.autonavi.amapauto-kFJ1sDolAyzDUG6nLuIaKw==/lib/arm/libGbl.so (_ZNK2bl24AreaCollisionCombination9IntersectEPNS_13CollisionItemES2_+64) 72 #00 bafd8b18 00000000 73 bafd8b1c 00000000 74 bafd8b20 00000000 75 bafd8b24 00000000 76 bafd8b28 00000000 77 bafd8b2c 00000000 78 bafd8b30 00000000 79 bafd8b34 00000000 80 bafd8b38 5f4c4247 81 bafd8b3c 4559414c [anon:dalvik-main space (region space)] 82 bafd8b40 5d5b5d52 83 bafd8b44 3935315b [anon:dalvik-main space (region space)] 84 bafd8b48 c4cc0300 [anon:libc_malloc] 85 bafd8b4c b94dae60 [anon:libc_malloc] 86 bafd8b50 00000000 87 bafd8b54 00000000
这个backtrace反解出来是乱码,很容易让人摸不着头脑。但是大神发现了问题痕迹:
(1)stack 信息一般不容易直接看出什么问题,但是这次仔细一看,可以发现 _ZNK2bl24AreaCollisionCombination9IntersectEPNS_13CollisionItemES2_ 和 __dynamic_cast 的痕迹,说明仍然触发过动态类型转换,与虚表地址相关;
(2)通过IDA查看so地址,发现 003884dc 位于一个虚表内,说明是触发了虚表地址错误,进一步确认了就是 dynamic_cast 引起的问题。与另一个清晰问题栈的问题雷同。
2、ANR
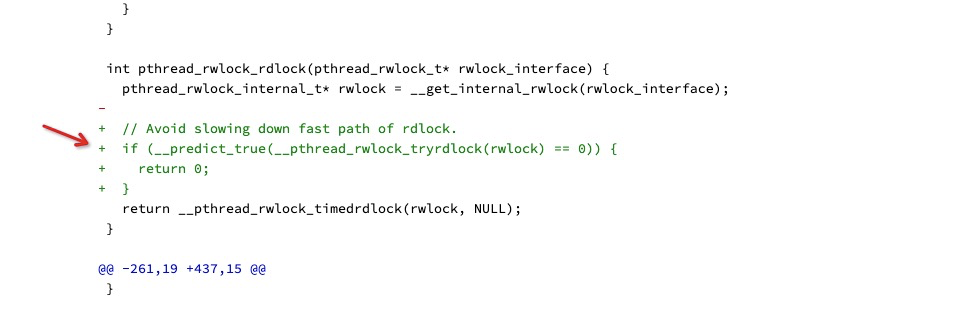
Android 4.4特定平台启动卡死,知道是 pthread_rwlock_timedrdlock 相关的,我们都猜测是读写锁的计数在特定平台(低版本Android)存在问题,具体啥问题不清楚。

1 DALVIK THREADS: 2 (mutexes: tll=0 tsl=0 tscl=0 ghl=0) 3 4 "main" prio=5 tid=1 NATIVE 5 | group="main" sCount=1 dsCount=0 obj=0x41e246d0 self=0x4016e010 6 | sysTid=5137 nice=0 sched=0/0 cgrp=apps handle=1075562576 7 | schedstat=( 0 0 0 ) utm=76 stm=27 core=0 8 #00 pc 0000dca0 /system/lib/libc.so (__futex_syscall3+8) 9 #01 pc 0001214c /system/lib/libc.so 10 #02 pc 00017550 /system/lib/libc.so (pthread_rwlock_timedrdlock+20) 11 #03 pc 0019ce3b /data/data/com.autonavi.amapauto/lib/libbase_utils.so (asl::ThreadManager::enterWait()+38) 12 #04 pc 0013d5ad /data/data/com.autonavi.amapauto/lib/libbase_utils.so (asl::ReadWriteLock::rLock()+10) 13 #05 pc 00162b05 /data/data/com.autonavi.amapauto/lib/libbase_utils.so 14 #06 pc 00163387 /data/data/com.autonavi.amapauto/lib/libbase_utils.so 15 #07 pc 00163259 /data/data/com.autonavi.amapauto/lib/libbase_utils.so 16 #08 pc 00118171 /data/data/com.autonavi.amapauto/lib/libbase_utils.so (alc::ALCManager::record(ALCLogLevel, unsigned long long, char const*, char const*, int, char const*, ...)+332) 17 #09 pc 00019ce7 /data/data/com.autonavi.amapauto/lib/libGAdaptor.so 18 #10 pc 0001f3b0 /system/lib/libdvm.so (dvmPlatformInvoke+112) 19 #11 pc 0004eb6f /system/lib/libdvm.so (dvmCallJNIMethod(unsigned int const*, JValue*, Method const*, Thread*)+394) 20 #12 pc 00028860 /system/lib/libdvm.so 21 #13 pc 0002d3c8 /system/lib/libdvm.so (dvmInterpret(Thread*, Method const*, JValue*)+180) 22 #14 pc 000615a7 /system/lib/libdvm.so (dvmInvokeMethod(Object*, Method const*, ArrayObject*, ArrayObject*, ClassObject*, bool)+374) 23 #15 pc 00068b71 /system/lib/libdvm.so 24 #16 pc 00028860 /system/lib/libdvm.so 25 #17 pc 0002d3c8 /system/lib/libdvm.so (dvmInterpret(Thread*, Method const*, JValue*)+180) 26 #18 pc 000612e1 /system/lib/libdvm.so (dvmCallMethodV(Thread*, Method const*, Object*, bool, JValue*, std::__va_list)+272) 27 #19 pc 0004b0a7 /system/lib/libdvm.so 28 #20 pc 0004d969 /system/lib/libandroid_runtime.so 29 #21 pc 0004eadf /system/lib/libandroid_runtime.so (android::AndroidRuntime::start(char const*, char const*)+390) 30 #22 pc 00000dcf /system/bin/app_process 31 #23 pc 00017113 /system/lib/libc.so (__libc_init+38) 32 #24 pc 00000b34 /system/bin/app_process 33 at com.autonavi.amapauto.jni.GAdaAndroid.nativeOnKeyDown(Native Method) 34 at g2.onKeyDown(BaseNativeActivity.java:5) 35 at android.view.KeyEvent.dispatch(KeyEvent.java:2715) 36 at android.app.Activity.dispatchKeyEvent(Activity.java:2432) 37 at com.android.internal.policy.impl.PhoneWindow$DecorView.dispatchKeyEvent(PhoneWindow.java:2071) 38 at android.view.ViewRootImpl.deliverKeyEventPostIme(ViewRootImpl.java:3992) 39 at android.view.ViewRootImpl.handleImeFinishedEvent(ViewRootImpl.java:3940) 40 at android.view.ViewRootImpl$ViewRootHandler.handleMessage(ViewRootImpl.java:3060) 41 at android.os.Handler.dispatchMessage(Handler.java:99) 42 at android.os.Looper.loop(Looper.java:137) 43 at android.app.ActivityThread.main(ActivityThread.java:4960) 44 at java.lang.reflect.Method.invokeNative(Native Method) 45 at java.lang.reflect.Method.invoke(Method.java:511) 46 at com.android.internal.os.ZygoteInit$MethodAndArgsCaller.run(ZygoteInit.java:1038) 47 at com.android.internal.os.ZygoteInit.main(ZygoteInit.java:805) 48 at dalvik.system.NativeStart.main(Native Method)
怎么办呢?查低版本Android 的读写锁实现,可能是个好主意,但也不能说明啥问题,毕竟之前也用过读写锁,并没有啥问题。
大神有办法:
(1)用Frida来监听读写锁的使用情况
(2)找高低版本Android的读写锁实现差异
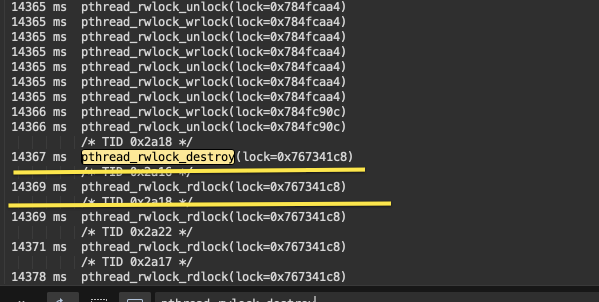
果然,意外的释放了读写锁实例,再次读取就出问题了。问题代码随之浮出水面:

进一步搜索一下高低版本Android读写锁实现差异,发现了Android commit log:
https://android.googlesource.com/platform/bionic/+/76615da%5E%21/