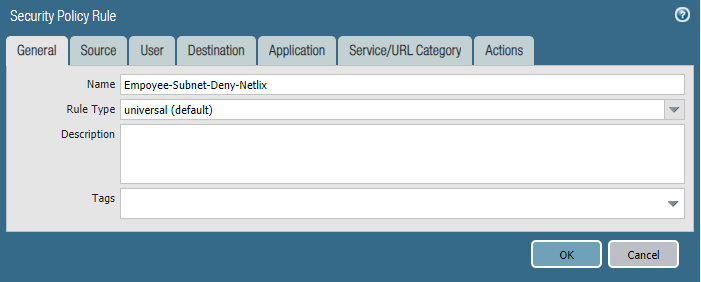
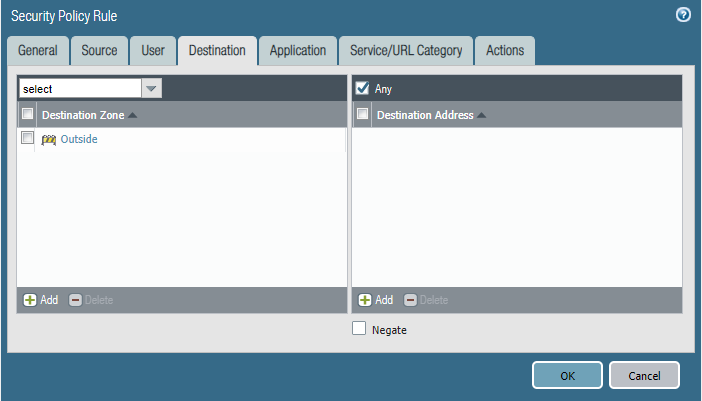
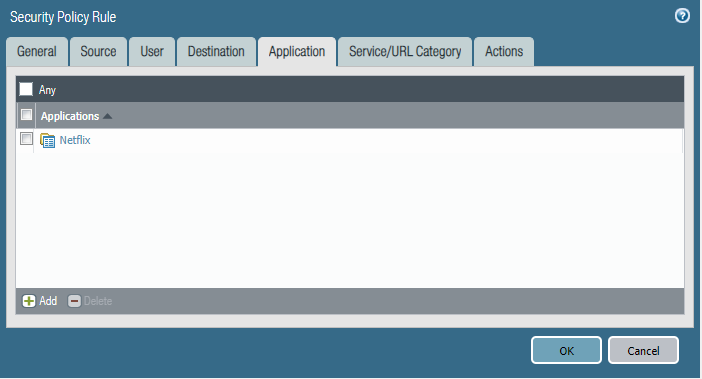
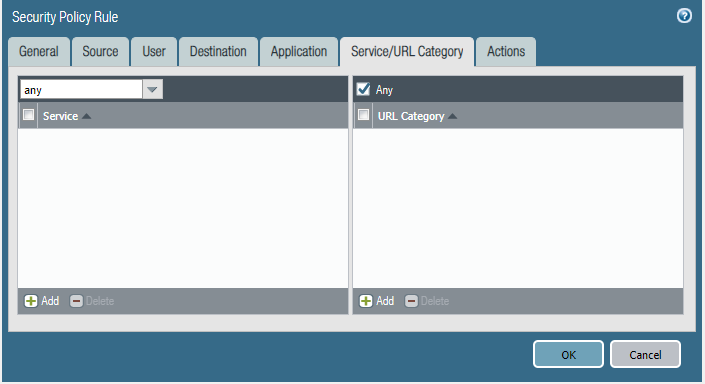
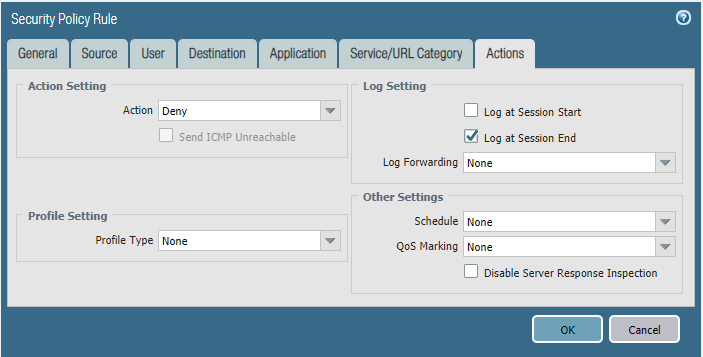
Security policies:
- Enforcing network traffic by configuring rules of what is allowed or denied to communicate between logical network segments (zones)
- Traffic can be policed with the following parameters:
- IP Address (source and/or destination)
- Users
- Services(ports)
- Applications

(From Packt)
- Enforcement hierarchy:
- Is essential to understand the security policy order of enforcement to avoid policy overruling
- "A clean policy table limits the possibility of policy overruling"
Task 1
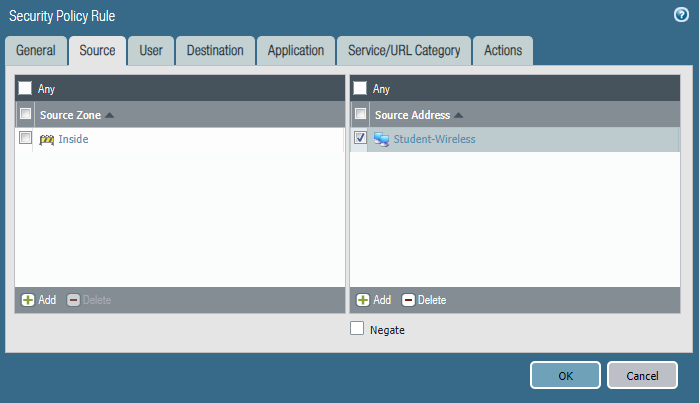
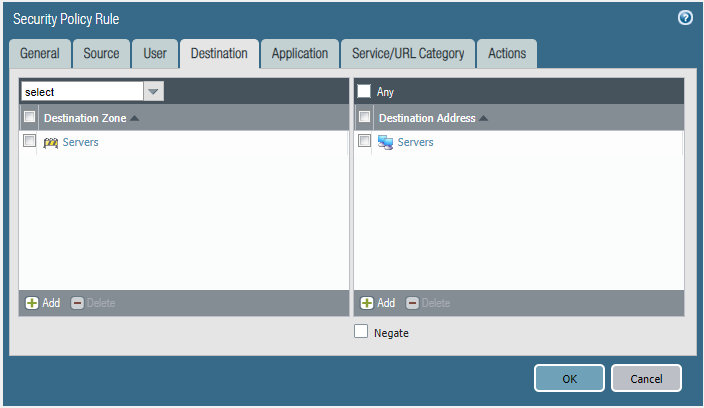
Please block the student wireless network from reaching the server subnet.
Source Zone Source Address Student Wireless: 10.10.0.0/22 Server Subnet: 10.30.0.0/23 Destination Zone Destination Address
Configure the firewall policy.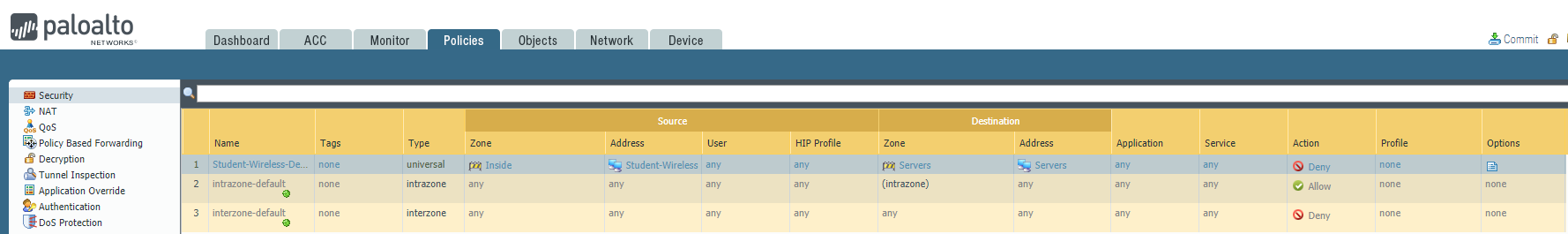


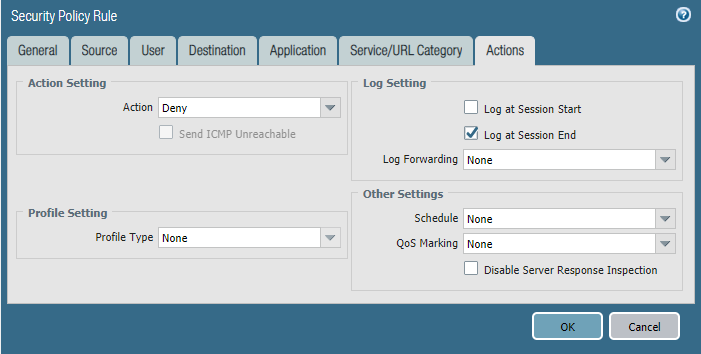
Task 2
We are getting complaints of employees watching Netflix during work hours and it's causing our internet connection to crawl.
- Please block the employee subnet 10.25.0.0/23 from accessing Netflix.
Configure the firewall policy.