INTERCEPTING & MODIFYING PACKETS
Scapy can be used to:
- Create packets.
- Analyze packets.
- Send/receive packets.
But it can't be used to intercept packets/flows.
CLASSIC MITM SCENARIO

MITM - SNIFFING DATA
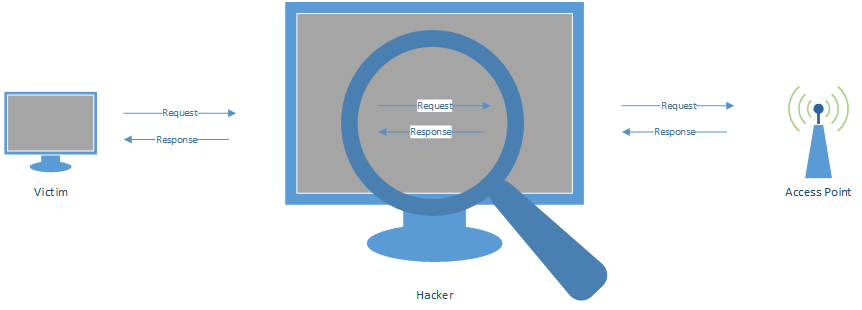
MITM - MODIFYING DATA


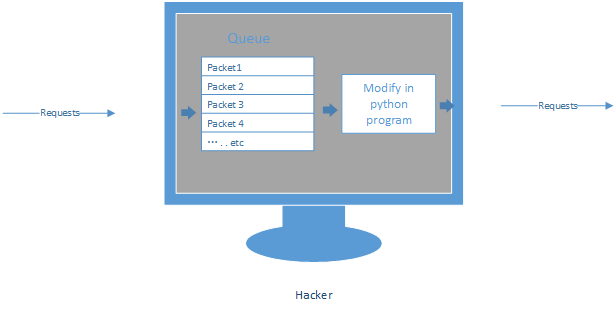
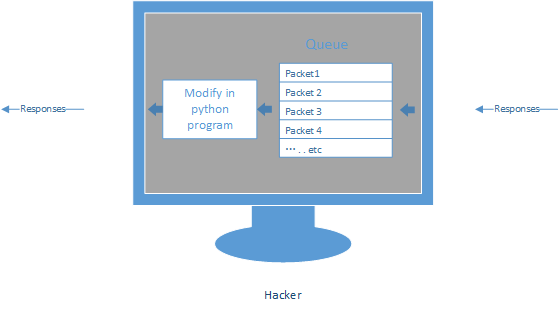
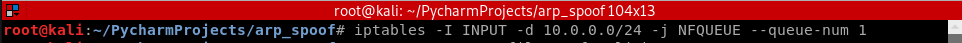
1. Execute the command - iptables to capture the packets into a queue.
iptables -I INPUT -d 10.0.0.0/24 -j NFQUEUE --queue-num 1
2. Access the Packets queue.
Install the module netfilterqueue first.
pip3 install -U git+https://github.com/kti/python-netfilterqueue

3. Write the Python script to intercept and process the packets.
#!/usr/bin/env python from netfilterqueue import NetfilterQueue def process_packet(packet): print(packet) packet.accept() queue = NetfilterQueue() queue.bind(1, process_packet) try: queue.run() except KeyboardInterrupt: print('')

We can also drop the packets through function packet.drop().
4. Use the following command to stop the packet capturing.
iptables --flush
Converting Packets to Scapy Packets
1. Execute the iptables command to capture the OUTPUT and INPUT packets.
iptables -I OUTPUT -j NFQUEUE --queue-num 0 iptables -I INPUT -j NFQUEUE --queue-num 0
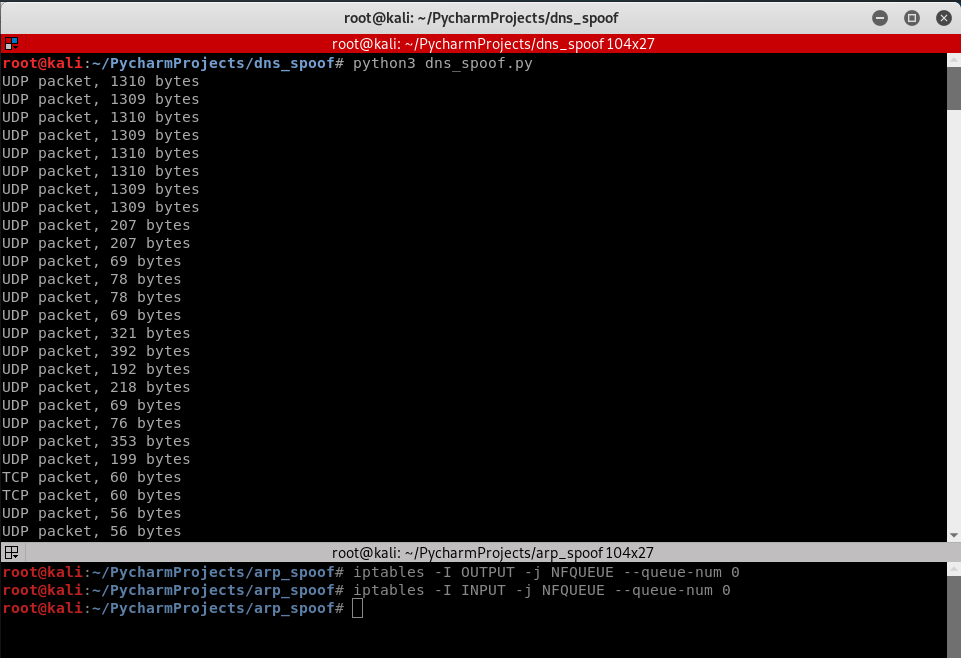
2. Execute the following Python script to process the captured packets.
#!/usr/bin/env python from netfilterqueue import NetfilterQueue def process_packet(packet): print(packet) packet.accept() queue = NetfilterQueue() queue.bind(0, process_packet) try: queue.run() except KeyboardInterrupt: print('')
3. Convert the packet to scapy packet and show on the screen.
#!/usr/bin/env python from netfilterqueue import NetfilterQueue from scapy.layers.inet import IP def process_packet(packet): scapy_packet = IP(packet.get_payload()) print(scapy_packet.show()) packet.accept() queue = NetfilterQueue() queue.bind(0, process_packet) try: queue.run() except KeyboardInterrupt: print('')
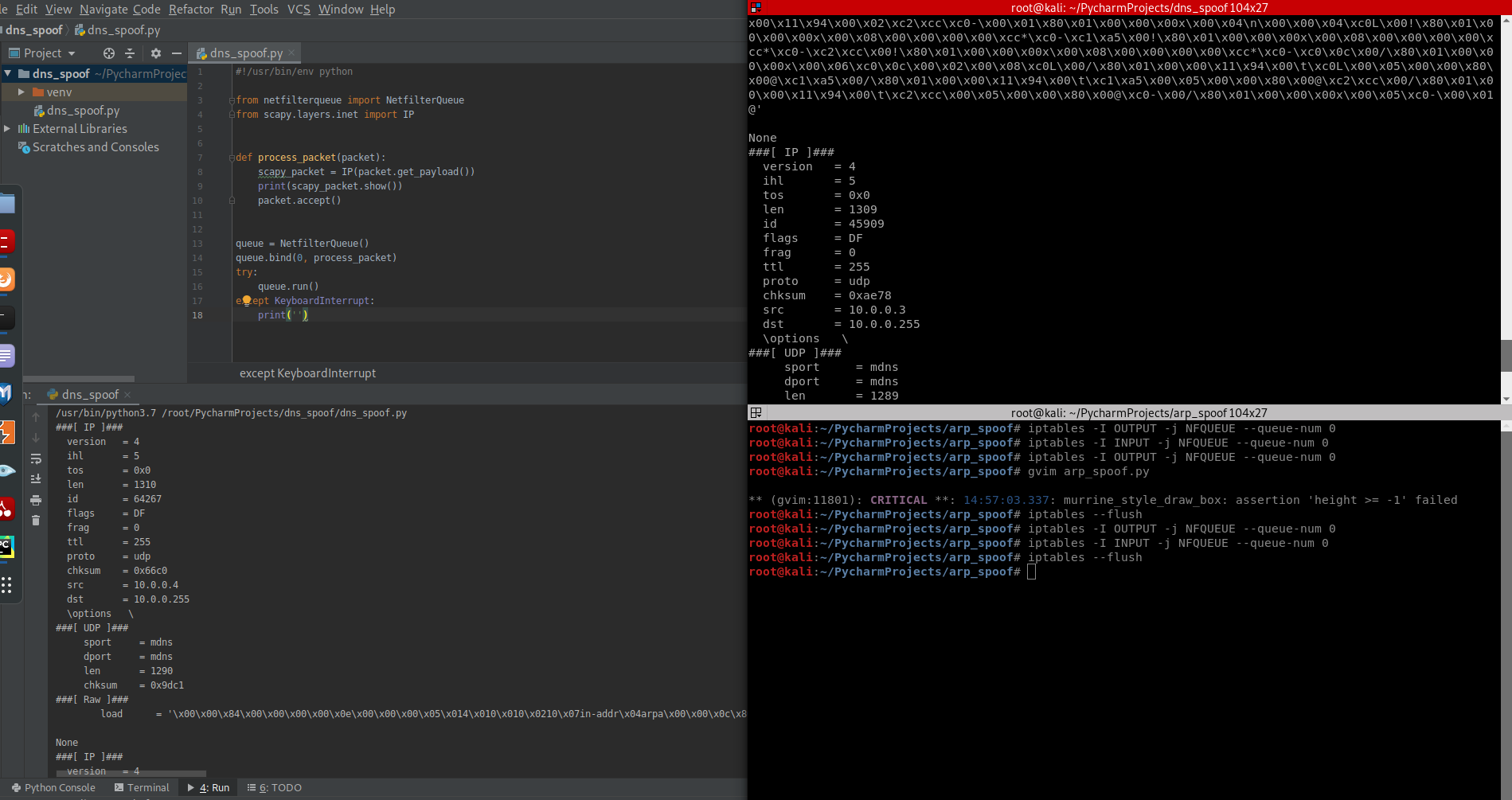
4. Stop the capture of the packet by the command.
iptables --flush