配置CAS基本步骤:
1、使用java自带keytool创建本地密钥库
2、将创建过的证书导入到java证书库
3、在tomcat配置文件中配置https证书访问
4、导入cas-server到eclipse
5、创建并配置cas-client
完成
下面开始逐步介绍:
1、使用java自带keytool创建本地密钥库
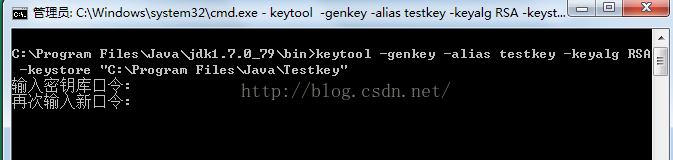
创建本地密钥库命令:
keytool -genkey -alias testkey -keyalg RSA -keystore "C:Program FilesJavaTestkey"
-alias : 这里的testkey是别名,根据个人自定义
-keystore :这里是声明生成key的位置(稍后会用到)
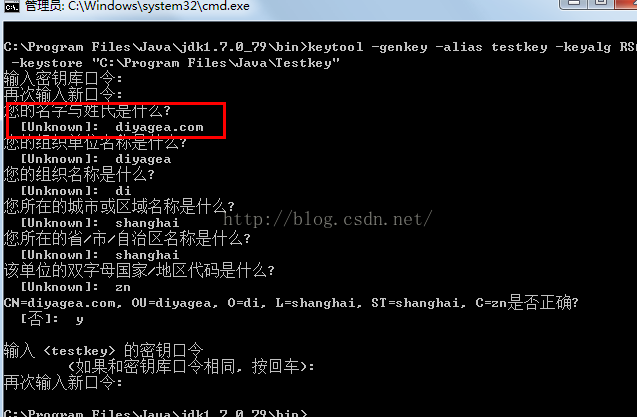
输入上述命令后,会让你输入密钥库口令(记住密码)
确认密码之后,会让你输入一些证书信息(注意:红框这里一定要输入你的域名)如何创建域名请看此文章
把密钥库导出成证书文件,输入命令:
keytool -export -file "C:Program FilesJava estkey.crt" -alias testkey -keystore "C:Program FilesJavaTestkey"
-file:定义输出文件的路径和名称
-alias:证书的别名(之前定义的)
-keystore:密钥库的存储路径
2、将创建过的证书导入到java证书库
把上面的证书导入到客户端JDK密钥库中(JDK证书密钥库默认密码:changeit):
keytool -import -keystore "C:Program FilesJavajdk1.7.0_79jrelibsecuritycacerts" -file "C:Program FilesJava estkey.crt" -alias testkey
3、在tomcat配置文件中配置https证书访问
在你tomcat安装路径conf目录下,修改server.xml配置文件中添加如下配置:
- <Connector SSLEnabled="true" clientAuth="false"
- keystoreFile="C:/Program Files/Java/Testkey" keystorePass="testkey"
- maxThreads="150" port="8443" protocol="org.apache.coyote.http11.Http11Protocol"
- scheme="https" secure="true" sslProtocol="TLS"/>
<Connector SSLEnabled="true" clientAuth="false" keystoreFile="C:/Program Files/Java/Testkey" keystorePass="testkey" maxThreads="150" port="8443" protocol="org.apache.coyote.http11.Http11Protocol" scheme="https" secure="true" sslProtocol="TLS"/>
keystoreFile:刚刚创建的密钥库路径
keystorePass : 密钥库口令
4、导入cas-server到eclipse
下载cas-server的zip包,解压后在modules目录下可以找到 cas-server-webapp-3.4.10.war
导入到eclipse中,改名为cas-server
启动tomcat,测试一下访问cas-server(在你第一次访问的时候会出现一个拦截页面,这是你只需要选择继续访问即可)
输入相同的帐号密码即可,因为默认的cas校验是允许帐号密码相同的登录成功
5、创建并配置cas-client
创建一个web project
在index.jsp中随便写点什么
修改web.xml
- <!-- ======================== 单点登录开始 ======================== -->
- <!-- 用于单点退出,该过滤器用于实现单点登出功能,可选配置 -->
- <listener>
- <listener-class>org.jasig.cas.client.session.SingleSignOutHttpSessionListener</listener-class>
- </listener>
- <!-- 该过滤器用于实现单点登出功能,可选配置。 -->
- <filter>
- <filter-name>CAS Single Sign Out Filter</filter-name>
- <filter-class>org.jasig.cas.client.session.SingleSignOutFilter</filter-class>
- </filter>
- <filter-mapping>
- <filter-name>CAS Single Sign Out Filter</filter-name>
- <url-pattern>/*</url-pattern>
- </filter-mapping>
- <!-- 该过滤器负责对Ticket的校验工作,必须启用它 -->
- <filter>
- <filter-name>CAS Validation Filter</filter-name>
- <filter-class>
- org.jasig.cas.client.validation.Cas20ProxyReceivingTicketValidationFilter</filter-class>
- <init-param>
- <param-name>casServerUrlPrefix</param-name>
- <param-value>https://diyagea.com:8443/cas-server</param-value>
- </init-param>
- <init-param>
- <param-name>serverName</param-name>
- <param-value>http://diyagea.com:8080/</param-value>
- </init-param>
- </filter>
- <filter-mapping>
- <filter-name>CAS Validation Filter</filter-name>
- <url-pattern>/*</url-pattern>
- </filter-mapping>
- <!-- 该过滤器负责用户的认证工作,必须启用它 -->
- <filter>
- <filter-name>CASFilter</filter-name>
- <filter-class>org.jasig.cas.client.authentication.AuthenticationFilter</filter-class>
- <init-param>
- <param-name>casServerLoginUrl</param-name>
- <param-value>https://diyagea.com:8443/cas-server/login</param-value>
- <!--这里的server是服务端的IP -->
- </init-param>
- <init-param>
- <param-name>serverName</param-name>
- <param-value>http://diyagea.com:8080/</param-value>
- </init-param>
- </filter>
- <filter-mapping>
- <filter-name>CASFilter</filter-name>
- <url-pattern>/*</url-pattern>
- </filter-mapping>
- <!-- 该过滤器负责实现HttpServletRequest请求的包裹, 比如允许开发者通过HttpServletRequest的getRemoteUser()方法获得SSO登录用户的登录名,可选配置。 -->
- <filter>
- <filter-name>CAS HttpServletRequest Wrapper Filter</filter-name>
- <filter-class>
- org.jasig.cas.client.util.HttpServletRequestWrapperFilter</filter-class>
- </filter>
- <filter-mapping>
- <filter-name>CAS HttpServletRequest Wrapper Filter</filter-name>
- <url-pattern>/*</url-pattern>
- </filter-mapping>
- <!-- 该过滤器使得开发者可以通过org.jasig.cas.client.util.AssertionHolder来获取用户的登录名。 比如AssertionHolder.getAssertion().getPrincipal().getName()。 -->
- <filter>
- <filter-name>CAS Assertion Thread Local Filter</filter-name>
- <filter-class>org.jasig.cas.client.util.AssertionThreadLocalFilter</filter-class>
- </filter>
- <filter-mapping>
- <filter-name>CAS Assertion Thread Local Filter</filter-name>
- <url-pattern>/*</url-pattern>
- </filter-mapping>
- <!-- ======================== 单点登录结束 ======================== -->
<!-- ======================== 单点登录开始 ======================== -->
<!-- 用于单点退出,该过滤器用于实现单点登出功能,可选配置 -->
<listener>
<listener-class>org.jasig.cas.client.session.SingleSignOutHttpSessionListener</listener-class>
</listener>
<!-- 该过滤器用于实现单点登出功能,可选配置。 -->
<filter>
<filter-name>CAS Single Sign Out Filter</filter-name>
<filter-class>org.jasig.cas.client.session.SingleSignOutFilter</filter-class>
</filter>
<filter-mapping>
<filter-name>CAS Single Sign Out Filter</filter-name>
<url-pattern>/*</url-pattern>
</filter-mapping>
<!-- 该过滤器负责对Ticket的校验工作,必须启用它 -->
<filter>
<filter-name>CAS Validation Filter</filter-name>
<filter-class>
org.jasig.cas.client.validation.Cas20ProxyReceivingTicketValidationFilter</filter-class>
<init-param>
<param-name>casServerUrlPrefix</param-name>
<param-value>https://diyagea.com:8443/cas-server</param-value>
</init-param>
<init-param>
<param-name>serverName</param-name>
<param-value>http://diyagea.com:8080/</param-value>
</init-param>
</filter>
<filter-mapping>
<filter-name>CAS Validation Filter</filter-name>
<url-pattern>/*</url-pattern>
</filter-mapping>
<!-- 该过滤器负责用户的认证工作,必须启用它 -->
<filter>
<filter-name>CASFilter</filter-name>
<filter-class>org.jasig.cas.client.authentication.AuthenticationFilter</filter-class>
<init-param>
<param-name>casServerLoginUrl</param-name>
<param-value>https://diyagea.com:8443/cas-server/login</param-value>
<!--这里的server是服务端的IP -->
</init-param>
<init-param>
<param-name>serverName</param-name>
<param-value>http://diyagea.com:8080/</param-value>
</init-param>
</filter>
<filter-mapping>
<filter-name>CASFilter</filter-name>
<url-pattern>/*</url-pattern>
</filter-mapping>
<!-- 该过滤器负责实现HttpServletRequest请求的包裹, 比如允许开发者通过HttpServletRequest的getRemoteUser()方法获得SSO登录用户的登录名,可选配置。 -->
<filter>
<filter-name>CAS HttpServletRequest Wrapper Filter</filter-name>
<filter-class>
org.jasig.cas.client.util.HttpServletRequestWrapperFilter</filter-class>
</filter>
<filter-mapping>
<filter-name>CAS HttpServletRequest Wrapper Filter</filter-name>
<url-pattern>/*</url-pattern>
</filter-mapping>
<!-- 该过滤器使得开发者可以通过org.jasig.cas.client.util.AssertionHolder来获取用户的登录名。 比如AssertionHolder.getAssertion().getPrincipal().getName()。 -->
<filter>
<filter-name>CAS Assertion Thread Local Filter</filter-name>
<filter-class>org.jasig.cas.client.util.AssertionThreadLocalFilter</filter-class>
</filter>
<filter-mapping>
<filter-name>CAS Assertion Thread Local Filter</filter-name>
<url-pattern>/*</url-pattern>
</filter-mapping>
<!-- ======================== 单点登录结束 ======================== -->
好了现在,copy一下,复制出另一个web project,修改一下index.jsp中内容,做一下对比
现在重启tomcat可以访问client的web project了
这时 访问你的web project路径时,会自动跳转到刚才的页面
登录成功后:
这个时候在输入第二个web project,已经不需要认证了,直接可以访问到index.jsp
好了,现在已经配置成功了,之后我会发出使用数据库认证方式,这样就可以应用到我的项目中去了