sudo curl -L -o /etc/yum.repos.d/devel:kubic:libcontainers:stable.repo https://download.opensuse.org/repositories/devel:kubic:libcontainers:stable/CentOS_7/devel:kubic:libcontainers:stable.repo
sudo curl -L -o /etc/yum.repos.d/devel:kubic:libcontainers:stable:cri-o:${VERSION}.repo https://download.opensuse.org/repositories/devel:kubic:libcontainers:stable:cri-o:${VERSION}/CentOS_7/devel:kubic:libcontainers:stable:cri-o:${VERSION}.repo
aws s3 cp file2.txt s3://bucket1-077298724
aws s3 cp file2.txt s3://bucket2-077298724
aws s3 ls s3://bucket1-077298724
aws s3 ls s3://bucket2-077298724
ip link set cni0 down && ip link set flannel.1 down
ip link delete cni0 && ip link delete flannel.1
systemctl restart containerd && systemctl restart kubelet
ee8fedc3-a236-4280-9fab-93f30d9bf706
aws ssm list-command-invocations --details \
--query "CommandInvocations[*].[InstanceId,DocumentName,Status]" \
--command-id ee8fedc3-a236-4280-9fab-93f30d9bf706
aws inspector create-assessment-target \
--assessment-target-name GamesDevTargetGroupCLI \
--resource-group-arn arn:aws:inspector:us-east-1:261289530960:resourcegroup/0-e10qLHIm
[ssm-user@ip-10-96-10-150 ~] $ aws inspector create-assessment-target \
> --assessment-target-name GamesDevTargetGroupCLI \
> --resource-group-arn arn:aws:inspector:us-east-1:261289530960:resourcegroup/0-e10qLHIm
{
"assessmentTargetArn": "arn:aws:inspector:us-east-1:261289530960:target/0-RRC8TidP"
}
[ssm-user@ip-10-96-10-150 ~] $
aws inspector describe-rules-packages --query rulesPackages[*].[name,description] --output text --rules-package-arns ”arn:aws:inspector:us-east-1:316112463485:rulespackage/0-PmNV0Tcd“
aws inspector describe-rules-packages --query rulesPackages[*].[name,description] --output text --rules-package-arns ”arn:aws:inspector:us-east-1:316112463485:rulespackage/0-R01qwB5Q“
aws inspector describe-rules-packages --query rulesPackages[*].[name,description] --output text --rules-package-arns ”arn:aws:inspector:us-east-1:316112463485:rulespackage/0-gEjTy7T7“
aws inspector describe-rules-packages --query rulesPackages[*].[name,description] --output text --rules-package-arns “arn:aws:inspector:us-east-1:316112463485:rulespackage/0-rExsr2X8”
aws ssm send-command --targets Key=tag:SecurityScan,Values=true \
--document-name "AmazonInspector-ManageAWSAgent" \
--query Command.CommandId \
--output-s3-bucket-name qls-5241349-96bc6c5a086b7a19-logbucket-12xk0yanx58c4
b2994ed2-b0d0-4808-8f3c-043f42e2fa02
ssm-user@ip-10-96-10-52 ~] $ aws ssm list-command-invocations --details \
> --query "CommandInvocations[*].[InstanceId,DocumentName,Status]" \
> --command-id b2994ed2-b0d0-4808-8f3c-043f42e2fa02
[
[
"i-0a6bd7b2c3f08a969",
"AmazonInspector-ManageAWSAgent",
"Success"
],
[
"i-0d42a24bd7f7619fb",
"AmazonInspector-ManageAWSAgent",
"Success"
]
]
[ssm-user@ip-10-96-10-52 ~] $ aws inspector create-resource-group --resource-group-tags key=SecurityScan,value=true
{
"resourceGroupArn": "arn:aws:inspector:us-east-1:821036605433:resourcegroup/0-N5osqgQM"
}
[ssm-user@ip-10-96-10-52 ~] $ aws inspector create-assessment-target \
> --assessment-target-name GamesDevTargetGroupCLI \
> --resource-group-arn arn:aws:inspector:us-east-1:821036605433:resourcegroup/0-N5osqgQM
{
"assessmentTargetArn": "arn:aws:inspector:us-east-1:821036605433:target/0-bN9wuvSn"
}
[ssm-user@ip-10-96-10-52 ~] $ aws inspector list-rules-packages
{
"rulesPackageArns": [
"arn:aws:inspector:us-east-1:316112463485:rulespackage/0-PmNV0Tcd",
"arn:aws:inspector:us-east-1:316112463485:rulespackage/0-R01qwB5Q",
"arn:aws:inspector:us-east-1:316112463485:rulespackage/0-gEjTy7T7",
"arn:aws:inspector:us-east-1:316112463485:rulespackage/0-rExsr2X8"
]
}
aws inspector describe-rules-packages --query rulesPackages[*].[name,description] --output text --rules-package-arns "arn:aws:inspector:us-east-1:316112463485:rulespackage/0-PmNV0Tcd"
aws inspector describe-rules-packages --query rulesPackages[*].[name,description] --output text --rules-package-arns "arn:aws:inspector:us-east-1:316112463485:rulespackage/0-R01qwB5Q"
aws inspector describe-rules-packages --query rulesPackages[*].[name,description] --output text --rules-package-arns "arn:aws:inspector:us-east-1:316112463485:rulespackage/0-gEjTy7T7"
aws inspector describe-rules-packages --query rulesPackages[*].[name,description] --output text --rules-package-arns "arn:aws:inspector:us-east-1:316112463485:rulespackage/0-rExsr2X8"
"arn:aws:inspector:us-east-1:316112463485:rulespackage/0-R01qwB5Q",
"arn:aws:inspector:us-east-1:316112463485:rulespackage/0-gEjTy7T7",
"arn:aws:inspector:us-east-1:316112463485:rulespackage/0-rExsr2X8"
ssm-user@ip-10-96-10-52 ~] $ aws inspector help
[ssm-user@ip-10-96-10-52 ~] $ aws inspector list-assessment-templates
{
"assessmentTemplateArns": [
"arn:aws:inspector:us-east-1:821036605433:target/0-bN9wuvSn/template/0-XGd8JbdJ"
]
}
[ssm-user@ip-10-96-10-52 ~] $ aws inspector delete-assessment-template --assessment-template-arn arn:aws:inspector:us-east-1:821036605433:target/0-bN9wuvSn/template/0-XGd8JbdJ
[ssm-user@ip-10-96-10-52 ~] $ aws inspector create-assessment-template \
> --assessment-target-arn arn:aws:inspector:us-east-1:821036605433:target/0-bN9wuvSn \
> --assessment-template-name CISCommonVulerBestPract-Short \
> --duration-in-seconds 900 --rules-package-arns arn:aws:inspector:us-east-1:316112463485:rulespackage/0-R01qwB5Q arn:aws:inspector:us-east-1:316112463485:rulespackage/0-gEjTy7T7 arn:aws:inspector:us-east-1:316112463485:rulespackage/0-rExsr2X8
{
"assessmentTemplateArn": "arn:aws:inspector:us-east-1:821036605433:target/0-bN9wuvSn/template/0-1o8jFMlh"
}
ssm-user@ip-10-96-10-52 ~] $ aws inspector preview-agents --preview-agents-arn arn:aws:inspector:us-east-1:821036605433:target/0-bN9wuvSn
{
"agentPreviews": [
{
"kernelVersion": "4.15.0-1044-aws",
"ipv4Address": "52.87.190.219",
"agentHealth": "HEALTHY",
"hostname": "ec2-52-87-190-219.compute-1.amazonaws.com",
"agentVersion": "1.1.1712.0",
"agentId": "i-0a6bd7b2c3f08a969",
"operatingSystem": "\"Ubuntu 18.04.2 LTS\""
},
{
"kernelVersion": "4.14.252-195.483.amzn2.x86_64",
"ipv4Address": "54.158.64.227",
"agentHealth": "HEALTHY",
"hostname": "ec2-54-158-64-227.compute-1.amazonaws.com",
"agentVersion": "1.1.1712.0",
"agentId": "i-0d42a24bd7f7619fb",
"operatingSystem": "Amazon Linux release 2 (Karoo)"
}
]
}
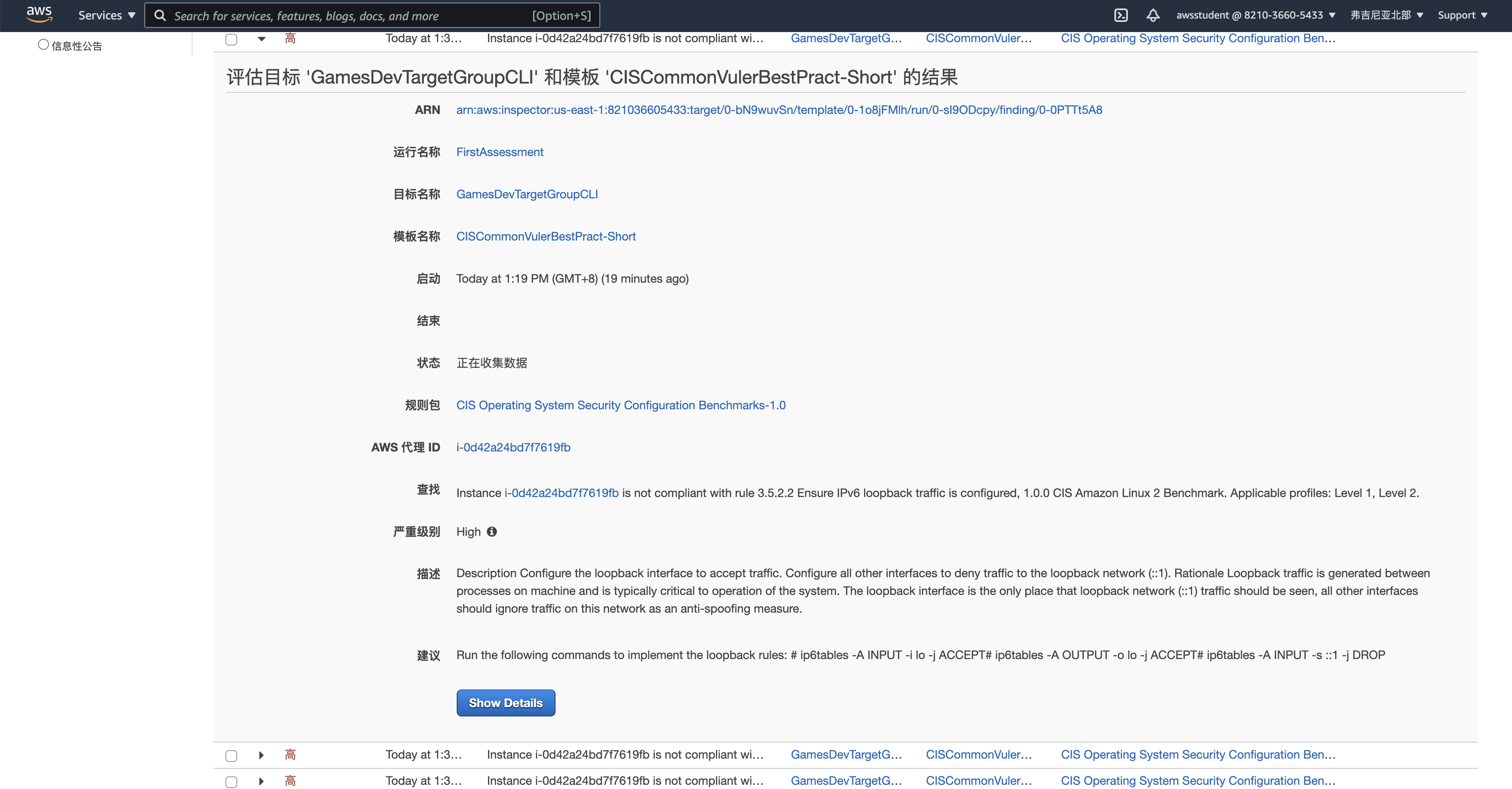
[ssm-user@ip-10-96-10-52 ~] $ aws inspector start-assessment-run \
> --assessment-run-name FirstAssessment \
> --assessment-template-arn arn:aws:inspector:us-east-1:821036605433:target/0-bN9wuvSn/template/0-1o8jFMlh
{
"assessmentRunArn": "arn:aws:inspector:us-east-1:821036605433:target/0-bN9wuvSn/template/0-1o8jFMlh/run/0-sI9ODcpy"
}
ssm-user@ip-10-96-10-52 ~] $ aws inspector describe-assessment-runs --assessment-run-arn arn:aws:inspector:us-east-1:821036605433:target/0-bN9wuvSn/template/0-1o8jFMlh/run/0-sI9ODcpy
{
"failedItems": {},
"assessmentRuns": [
{
"dataCollected": false,
"name": "FirstAssessment",
"userAttributesForFindings": [],
"stateChanges": [
{
"state": "CREATED",
"stateChangedAt": 1640495971.991
},
{
"state": "START_DATA_COLLECTION_PENDING",
"stateChangedAt": 1640495972.077
},
{
"state": "COLLECTING_DATA",
"stateChangedAt": 1640495972.713
}
],
"createdAt": 1640495971.991,
"notifications": [],
"state": "COLLECTING_DATA",
"stateChangedAt": 1640495972.713,
"durationInSeconds": 900,
"rulesPackageArns": [
"arn:aws:inspector:us-east-1:316112463485:rulespackage/0-gEjTy7T7",
"arn:aws:inspector:us-east-1:316112463485:rulespackage/0-rExsr2X8",
"arn:aws:inspector:us-east-1:316112463485:rulespackage/0-R01qwB5Q"
],
"startedAt": 1640495972.713,
"assessmentTemplateArn": "arn:aws:inspector:us-east-1:821036605433:target/0-bN9wuvSn/template/0-1o8jFMlh",
"arn": "arn:aws:inspector:us-east-1:821036605433:target/0-bN9wuvSn/template/0-1o8jFMlh/run/0-sI9ODcpy"
}
]
}
ssm-user@ip-10-96-10-52 ~] $ aws inspector list-assessment-run-agents --assessment-run-arn arn:aws:inspector:us-east-1:821036605433:target/0-bN9wuvSn/template/0-1o8jFMlh/run/0-sI9ODcpy
{
"assessmentRunAgents": [
{
"agentHealthCode": "RUNNING",
"assessmentRunArn": "arn:aws:inspector:us-east-1:821036605433:target/0-bN9wuvSn/template/0-1o8jFMlh/run/0-sI9ODcpy",
"agentId": "i-0a6bd7b2c3f08a969",
"agentHealth": "HEALTHY",
"telemetryMetadata": [
{
"count": 456,
"dataSize": 245851,
"messageType": "Total"
},
{
"count": 1,
"dataSize": 0,
"messageType": "InspectorSplitMsgBegin"
},
{
"count": 1,
"dataSize": 85,
"messageType": "InspectorTimeEventMsg"
},
{
"count": 56,
"dataSize": 5098,
"messageType": "InspectorGroup"
},
{
"count": 1,
"dataSize": 713,
"messageType": "InspectorListeningProcess"
},
{
"count": 1,
"dataSize": 354,
"messageType": "InspectorOperatingSystem"
},
{
"count": 2,
"dataSize": 129984,
"messageType": "InspectorOvalCISMsg"
},
{
"count": 1,
"dataSize": 95,
"messageType": "InspectorMonitoringStart"
},
{
"count": 31,
"dataSize": 7096,
"messageType": "InspectorUser"
},
{
"count": 12,
"dataSize": 2742,
"messageType": "InspectorDirectoryInfoMsg"
},
{
"count": 2,
"dataSize": 294,
"messageType": "InspectorErrorMsg"
},
{
"count": 30,
"dataSize": 50783,
"messageType": "InspectorConfigurationInfo"
},
{
"count": 318,
"dataSize": 48607,
"messageType": "InspectorPackageInfo"
}
]
},
{
"agentHealthCode": "RUNNING",
"assessmentRunArn": "arn:aws:inspector:us-east-1:821036605433:target/0-bN9wuvSn/template/0-1o8jFMlh/run/0-sI9ODcpy",
"agentId": "i-0d42a24bd7f7619fb",
"agentHealth": "HEALTHY",
"telemetryMetadata": [
{
"count": 390,
"dataSize": 126714,
"messageType": "Total"
},
{
"count": 1,
"dataSize": 85,
"messageType": "InspectorTimeEventMsg"
},
{
"count": 50,
"dataSize": 4578,
"messageType": "InspectorGroup"
},
{
"count": 1,
"dataSize": 64992,
"messageType": "InspectorOvalCISMsg"
},
{
"count": 1,
"dataSize": 378,
"messageType": "InspectorOperatingSystem"
},
{
"count": 1,
"dataSize": 95,
"messageType": "InspectorMonitoringStart"
},
{
"count": 28,
"dataSize": 5979,
"messageType": "InspectorUser"
},
{
"count": 307,
"dataSize": 50427,
"messageType": "InspectorPackageInfo"
},
{
"count": 1,
"dataSize": 180,
"messageType": "InspectorErrorMsg"
}
]
}
]
}

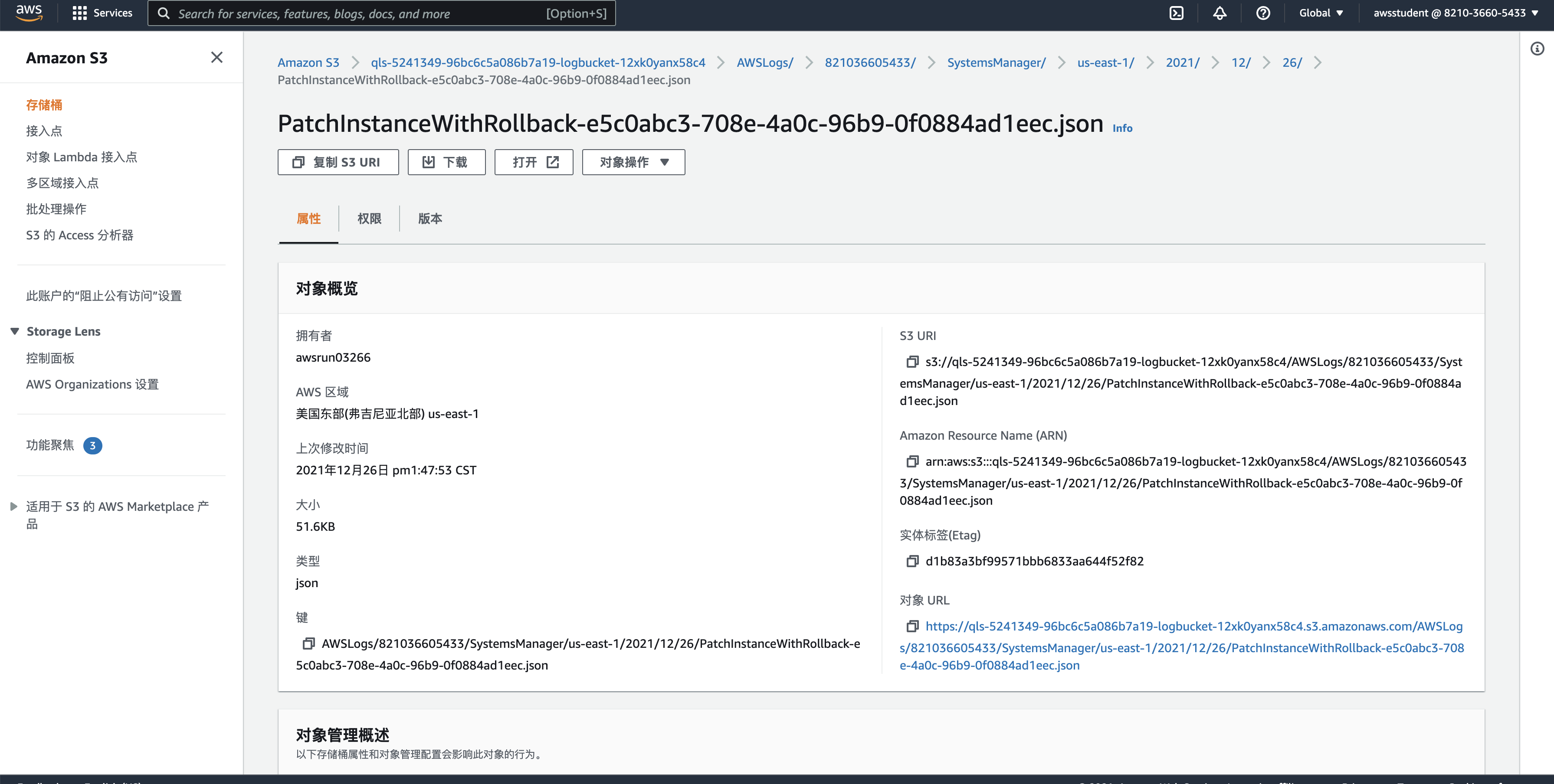
sh-4.2$ aws ssm describe-document --name "AWS-PatchInstanceWithRollback" --query "Document.[Name,Description,PlatformTypes]"
[
"AWS-PatchInstanceWithRollback",
"Brings EC2 Instance into compliance with standing Baseline; rolls back root Volume on failure.",
[
"Windows",
"Linux",
"MacOS"
]
]
sh-4.2$ aws ssm describe-instance-information --query "InstanceInformationList[*]" --filters "Key=tag:SecurityScan,Values=true"
[
{
"IsLatestVersion": false,
"ComputerName": "ip-10-96-10-124.ec2.internal",
"PingStatus": "Online",
"InstanceId": "i-0d42a24bd7f7619fb",
"IPAddress": "10.96.10.124",
"ResourceType": "EC2Instance",
"AgentVersion": "3.0.1124.0",
"PlatformVersion": "2",
"PlatformName": "Amazon Linux",
"PlatformType": "Linux",
"LastPingDateTime": 1640497264.48
},
{
"IsLatestVersion": false,
"ComputerName": "ip-10-96-10-8.ec2.internal",
"PingStatus": "Online",
"InstanceId": "i-0a6bd7b2c3f08a969",
"IPAddress": "10.96.10.8",
"ResourceType": "EC2Instance",
"AgentVersion": "2.3.662.0",
"PlatformVersion": "18.04",
"PlatformName": "Ubuntu",
"PlatformType": "Linux",
"LastPingDateTime": 1640497316.34
}
]
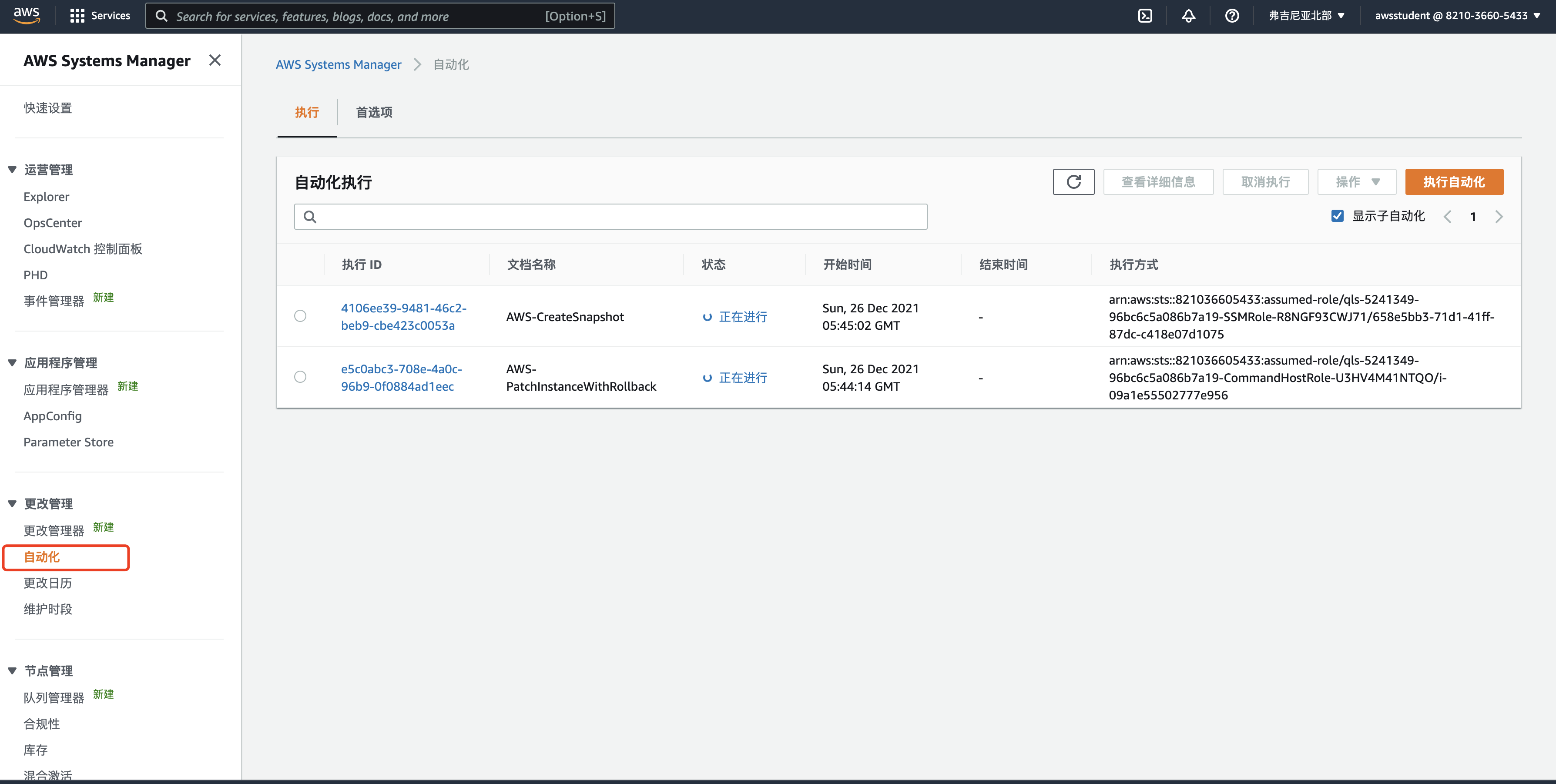
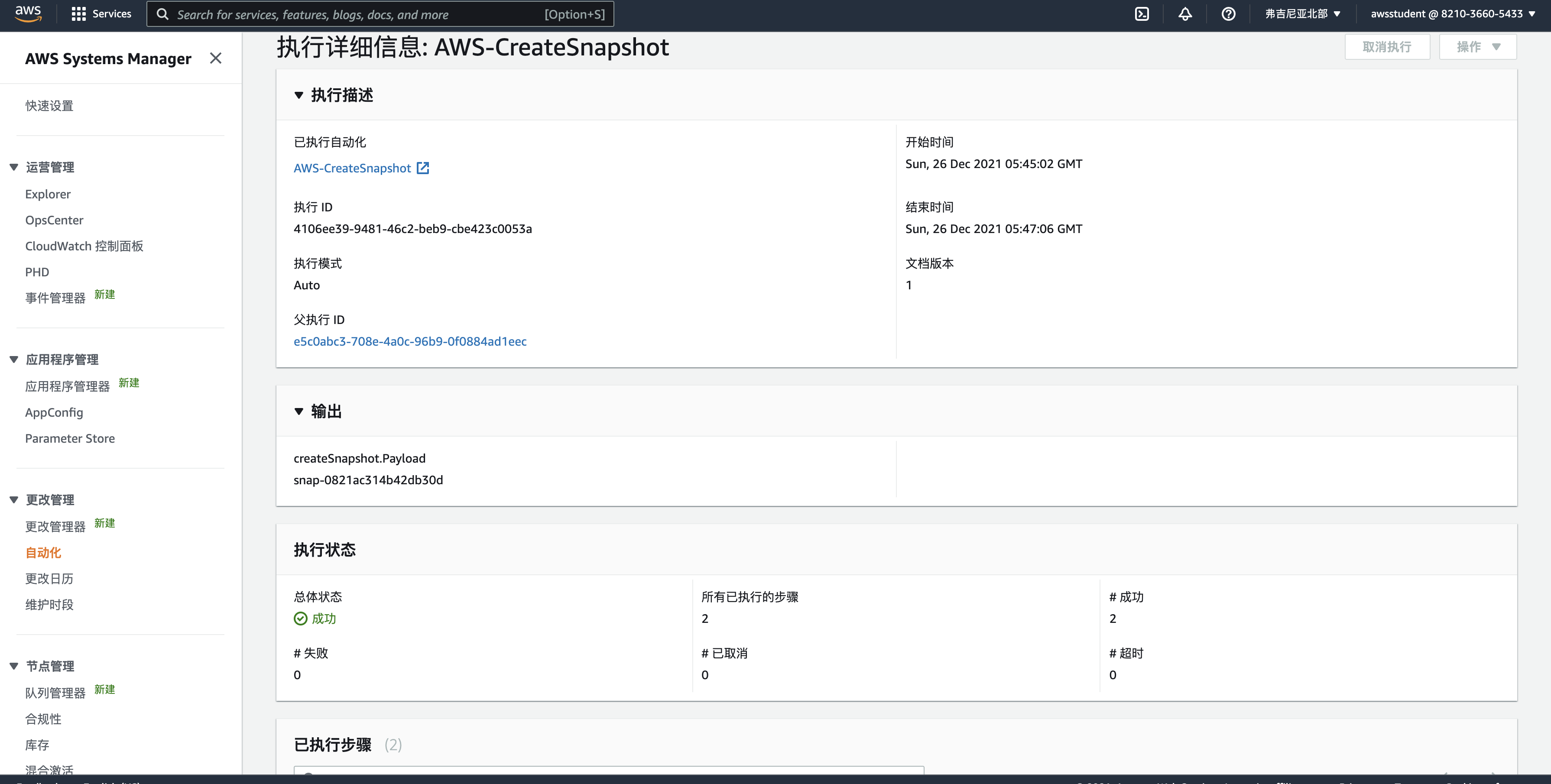
sh-4.2$ aws ssm start-automation-execution \
> --document-name "AWS-PatchInstanceWithRollback" \
> --parameters "InstanceId=i-0d42a24bd7f7619fb,ReportS3Bucket=qls-5241349-96bc6c5a086b7a19-logbucket-12xk0yanx58c4,AutomationAssumeRole=arn:aws:iam::821036605433:role/qls-5241349-96bc6c5a086b7a19-SSMRole-R8NGF93CWJ71"
{
"AutomationExecutionId": "e5c0abc3-708e-4a0c-96b9-0f0884ad1eec"
}
sh-4.2$