官网更新了新的2.*版本,废弃了Heapster。也试着安装了一下感觉还不错,就是执行kubectl proxy的时候要改成kubectl proxy --address='node-ip' --accept-hosts='^*$',其他机器就可以访问了,否则只有安装dashboadr的机器才能访问界面。
安装方法参考的文档见本文末尾,个人感觉一步一步安装一下还是挺有意思的~~
1.安装dashboard:
dashboad的yaml文件贴在这里~
# Copyright 2017 The Kubernetes Authors.
#
# Licensed under the Apache License, Version 2.0 (the "License");
# you may not use this file except in compliance with the License.
# You may obtain a copy of the License at
#
# http://www.apache.org/licenses/LICENSE-2.0
#
# Unless required by applicable law or agreed to in writing, software
# distributed under the License is distributed on an "AS IS" BASIS,
# WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
# See the License for the specific language governing permissions and
# limitations under the License.
# ------------------- Dashboard Secret ------------------- #
apiVersion: v1
kind: Secret
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard-certs
namespace: kube-system
type: Opaque
---
# ------------------- Dashboard Service Account ------------------- #
apiVersion: v1
kind: ServiceAccount
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard
namespace: kube-system
---
# ------------------- Dashboard Role & Role Binding ------------------- #
kind: Role
apiVersion: rbac.authorization.k8s.io/v1
metadata:
name: kubernetes-dashboard-minimal
namespace: kube-system
rules:
# Allow Dashboard to create 'kubernetes-dashboard-key-holder' secret.
- apiGroups: [""]
resources: ["secrets"]
verbs: ["create"]
# Allow Dashboard to create 'kubernetes-dashboard-settings' config map.
- apiGroups: [""]
resources: ["configmaps"]
verbs: ["create"]
# Allow Dashboard to get, update and delete Dashboard exclusive secrets.
- apiGroups: [""]
resources: ["secrets"]
resourceNames: ["kubernetes-dashboard-key-holder", "kubernetes-dashboard-certs"]
verbs: ["get", "update", "delete"]
# Allow Dashboard to get and update 'kubernetes-dashboard-settings' config map.
- apiGroups: [""]
resources: ["configmaps"]
resourceNames: ["kubernetes-dashboard-settings"]
verbs: ["get", "update"]
# Allow Dashboard to get metrics from heapster.
- apiGroups: [""]
resources: ["services"]
resourceNames: ["heapster"]
verbs: ["proxy"]
- apiGroups: [""]
resources: ["services/proxy"]
resourceNames: ["heapster", "http:heapster:", "https:heapster:"]
verbs: ["get"]
---
apiVersion: rbac.authorization.k8s.io/v1
kind: RoleBinding
metadata:
name: kubernetes-dashboard-minimal
namespace: kube-system
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: Role
name: kubernetes-dashboard-minimal
subjects:
- kind: ServiceAccount
name: kubernetes-dashboard
namespace: kube-system
---
# ------------------- Dashboard Deployment ------------------- #
kind: Deployment
apiVersion: apps/v1
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard
namespace: kube-system
spec:
replicas: 1
revisionHistoryLimit: 10
selector:
matchLabels:
k8s-app: kubernetes-dashboard
template:
metadata:
labels:
k8s-app: kubernetes-dashboard
spec:
containers:
- name: kubernetes-dashboard
image: hati/kubernetes-dashboard-amd64:v1.10.1
ports:
- containerPort: 8443
protocol: TCP
args:
- --auto-generate-certificates
# Uncomment the following line to manually specify Kubernetes API server Host
# If not specified, Dashboard will attempt to auto discover the API server and connect
# to it. Uncomment only if the default does not work.
# - --apiserver-host=http://my-address:port
volumeMounts:
- name: kubernetes-dashboard-certs
mountPath: /certs
# Create on-disk volume to store exec logs
- mountPath: /tmp
name: tmp-volume
livenessProbe:
httpGet:
scheme: HTTPS
path: /
port: 8443
initialDelaySeconds: 30
timeoutSeconds: 30
volumes:
- name: kubernetes-dashboard-certs
secret:
secretName: kubernetes-dashboard-certs
- name: tmp-volume
emptyDir: {}
serviceAccountName: kubernetes-dashboard
# Comment the following tolerations if Dashboard must not be deployed on master
tolerations:
- key: node-role.kubernetes.io/master
effect: NoSchedule
---
# ------------------- Dashboard Service ------------------- #
kind: Service
apiVersion: v1
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard
namespace: kube-system
spec:
ports:
- port: 443
targetPort: 8443
selector:
k8s-app: kubernetes-dashboard
wget -O kubernetes-dashboard.yaml https://raw.githubusercontent.com/kubernetes/dashboard/master/aio/deploy/recommended/kubernetes-dashboard.yaml
突然发现上面链接失效了……
sed -i "s/k8s.gcr.io/hati/g" kubernetes-dashboard.yaml
kubectl apply -f kubernetes-dashboard.yaml
kubectl get pods -n kube-system
2.创建服务账户,绑定集群角色:
service_account.yaml
1 apiVersion: v1 2 kind: ServiceAccount 3 metadata: 4 name: admin-user 5 namespace: kube-system
clusterrolebinding.yaml
1 apiVersion: rbac.authorization.k8s.io/v1 2 kind: ClusterRoleBinding 3 metadata: 4 name: admin-user 5 roleRef: 6 apiGroup: rbac.authorization.k8s.io 7 kind: ClusterRole 8 name: cluster-admin 9 subjects: 10 - kind: ServiceAccount 11 name: admin-user 12 namespace: kube-system
kubectl apply -f service_account.yaml
kubectl apply -f clusterrolebinding.yaml #Bearer Token kubectl -n kube-system describe secret $(kubectl -n kube-system get secret | grep admin-user | awk '{print $1}')
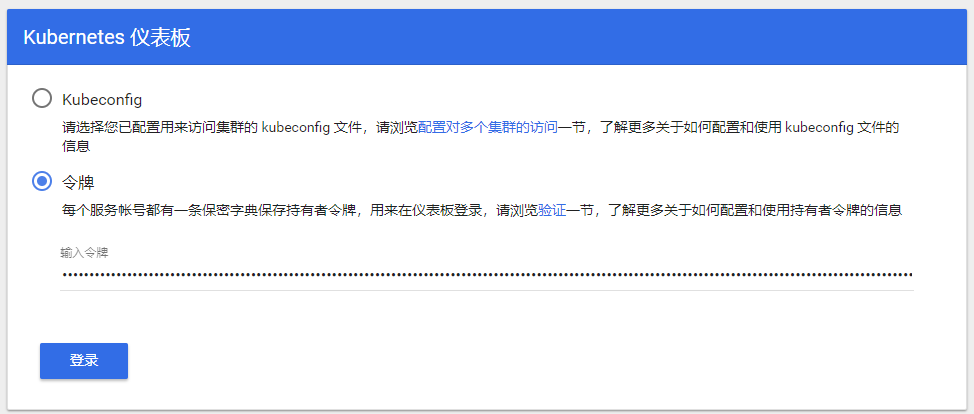
备注:copy生成的token,用于登录dashboad。
3.生成用户证书
过程中会要求输入导出证书时用到的密钥,请务必记住。
grep 'client-certificate-data' ~/.kube/config | head -n 1 | awk '{print $2}' | base64 -d >> kubecfg.crt grep 'client-key-data' ~/.kube/config | head -n 1 | awk '{print $2}' | base64 -d >> kubecfg.key openssl pkcs12 -export -clcerts -inkey kubecfg.key -in kubecfg.crt -out kubecfg.p12 -name "kubernetes-client" echo "Please install the kubecfg.p12 certificate in your browser, and then restart browser."
4.安装图形化插件heapster
wget -O grafana.yaml https://raw.githubusercontent.com/kubernetes/heapster/master/deploy/kube-config/influxdb/grafana.yaml wget -O heapster.yaml https://raw.githubusercontent.com/kubernetes/heapster/master/deploy/kube-config/influxdb/heapster.yaml wget -O influxdb.yaml https://raw.githubusercontent.com/kubernetes/heapster/master/deploy/kube-config/influxdb/influxdb.yaml wget -O heapster-rbac.yaml https://raw.githubusercontent.com/kubernetes/heapster/master/deploy/kube-config/rbac/heapster-rbac.yaml # Set port ype as "NodePort" for test environment sed -i "s/# type: NodePort/type: NodePort/g" grafana.yaml # Set only use API server proxy to access grafana sed -i "s/value: //#value: //g" grafana.yaml sed -i "s/# #value: /api/value: /api/g" grafana.yaml sed -i "s/name: ca-certificates/name: ca-certs/g" grafana.yaml sed -i "s/heapster-grafana-amd64:v5.0.4/heapster-grafana-amd:v4.4.3/g" grafana.yaml sed -i "s/https://kubernetes.default/https://kubernetes.default:443?useServiceAccount=true&kubeletHttps=true&kubeletPort=10250&insecure=true/g" heapster.yaml sed -i "s/name: system:heapster/name: cluster-admin/g" heapster-rbac.yaml #Replace k8s.gcr.io image with hati sed -i "s/k8s.gcr.io/hati/g" grafana.yaml sed -i "s/k8s.gcr.io/hati/g" heapster.yaml sed -i "s/k8s.gcr.io/hati/g" influxdb.yaml
kubectl apply -f grafana.yaml
kubectl apply -f heapster.yaml
kubectl apply -f influxdb.yaml
kubectl apply -f heapster-rbac.yaml
kubectl get pods -n kube-system
kubectl cluster-info
将生成的用户证书kubecfg.p12导入到浏览器中(以Chrome为例,设置->高级->管理证书->导入),然后访问地址(ip和port做相应的更改):
https://<master-ip>:<apiserver-port>/api/v1/namespaces/kube-system/services/https:kubernetes-dashboard:/proxy/
在令牌处输入保存的token登录dashboard:

参考文档:
https://blog.csdn.net/nklinsirui/article/details/80806131