先推荐一下GDAhttps://bbs.pediy.com/thread-220111.htm
Java逆向解密
class,找了个在线网站:http://javare.cn
import java.util.ArrayList;
import java.util.Scanner;
public class Reverse {
public static void main(String[] args) {
Scanner s = new Scanner(System.in);
System.out.println("Please input the flag 锛�");
String str = s.next();
System.out.println("Your input is 锛�");
System.out.println(str);
char[] stringArr = str.toCharArray();
Encrypt(stringArr);
}
public static void Encrypt(char[] arr) {
ArrayList Resultlist = new ArrayList();
for(int KEY = 0; KEY < arr.length; ++KEY) {
int KEYList = arr[KEY] + 64 ^ 32;
Resultlist.add(Integer.valueOf(KEYList));
}
int[] var5 = new int[]{180, 136, 137, 147, 191, 137, 147, 191, 148, 136, 133, 191, 134, 140, 129, 135, 191, 65};
ArrayList var6 = new ArrayList();
for(int j = 0; j < var5.length; ++j) {
var6.add(Integer.valueOf(var5[j]));
}
System.out.println("Result:");
if(Resultlist.equals(var6)) {
System.out.println("Congratulations锛�");
} else {
System.err.println("Error锛�");
}
}
}
a=[180, 136, 137, 147, 191, 137, 147, 191, 148, 136, 133, 191, 134, 140, 129, 135, 191, 65]
b=[]
for i in range(len(a)):
b.append(a[i]-64^32)
for i in b:
print(chr(i),end="")
findit
apk,使用GDA打开,找到mainactivity
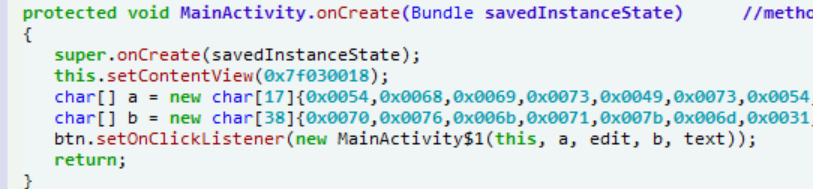
有两个数组,找到
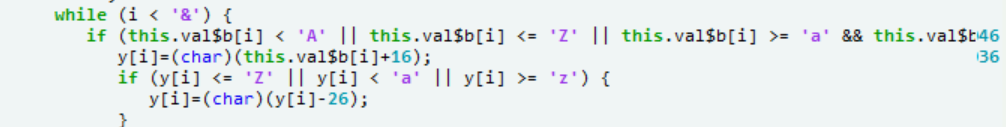
变形的凯撒密码
a=[0x0054,0x0068,0x0069,0x0073,0x0049,0x0073,0x0054,0x0068,0x0065,0x0046,0x006c,0x0061,0x0067,0x0048,0x006f,0x006d,0x0065]
x=""
b=[0x0070,0x0076,0x006b,0x0071,0x007b,0x006d,0x0031,0x0036,0x0034,0x0036,0x0037,0x0035,0x0032,0x0036,0x0032,0x0030,0x0033,0x0033,0x006c,0x0034,0x006d,0x0034,0x0039,0x006c,0x006e,0x0070,0x0037,0x0070,0x0039,0x006d,0x006e,0x006b,0x0032,0x0038,0x006b,0x0037,0x0035,0x007d]
for i in range(len(a)):
x+=chr(a[i])
print(x)
x=""
for i in range(len(b)):
if(chr(b[i]).isalpha()):
x+=chr(b[i]-10)
else:
x+=chr(b[i])
print(x)
简单注册器
GDA打开
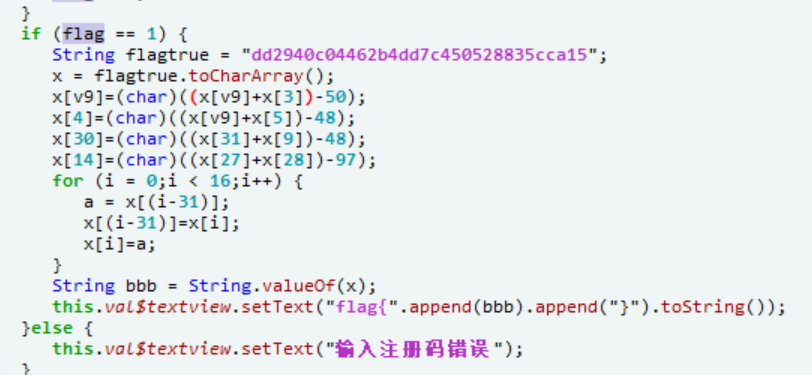
a="dd2940c04462b4dd7c450528835cca15"
x=[]
for i in a:
x.append(i)
x[2]=chr(ord(x[2])+ord(x[3])-50);
x[4]=chr(ord(x[2])+ord(x[5])-48);
x[30]=chr(ord(x[31])+ord(x[9])-48);
x[14]=chr(ord(x[27])+ord(x[28])-97);
print(x)
for i in range(31,-1,-1):
print(x[i],end="")
相册
apk病毒,要求找到邮箱,拖进GDA
Malscan看看
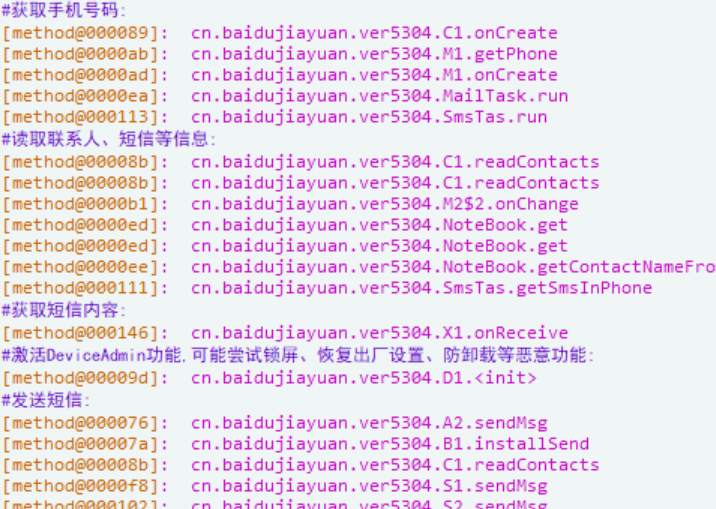
没找到邮箱相关,但从类里找到一个Mail类
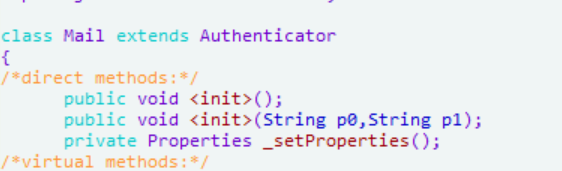
按x查看交叉引用找到
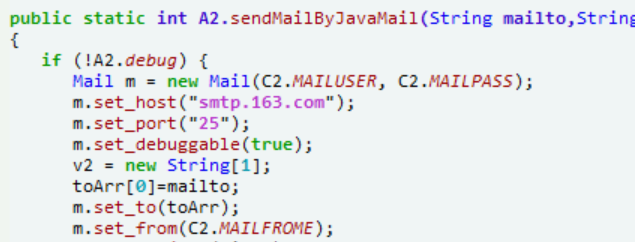
去c2看看
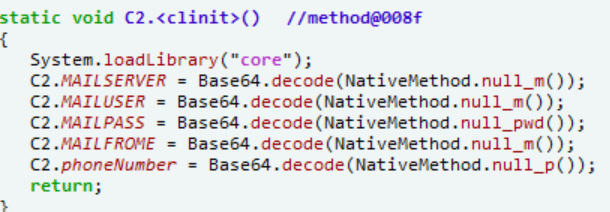
NativeMethod,要去so里找找base64密文

[SCTF2019]Strange apk
拖进GDA
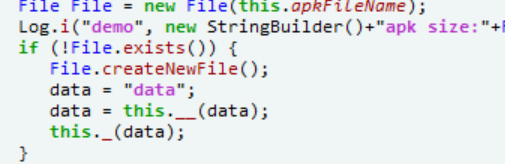
这里对一个名为data的文件进行了操作
public byte[] c.__(String fileName) //method@3ebd
{
InputStream in = in.open(fileName);
int lenght = in.available();
byte[] buffer = new byte[lenght];
in.read(buffer);
return buffer;
}
private void c._(byte[] apkdata) //method@3ebb
{
apkdata = this._0_(apkdata);
File file = new File(this.apkFileName);
FileOutputStream localFileOutputStream = new FileOutputStream(file);
localFileOutputStream.write(apkdata);
localFileOutputStream.close();
return;
}
private byte[] c._0_(byte[] srcdata) //method@3ebc
{
String src = "syclover";
for (int i = 0;i < srcdata.length();i++) {
srcdata[i]=(byte)(src.charAt((i%src.length()))^srcdata[i]);
}
return srcdata;
}
在assets里找到data文件
x=b"syclover"
with open(r"data","rb") as f:
f=f.read()
with open(r"data_","wb") as F:
for i in range(len(f)):
F.write((f[i]^x[i%len(x)]).to_bytes(length=1, byteorder='big'))
得到文件为zip,后缀改为apk拖进GDA
有两处加密
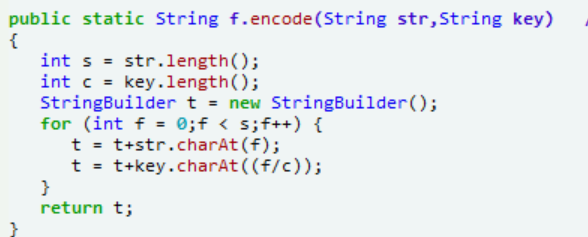
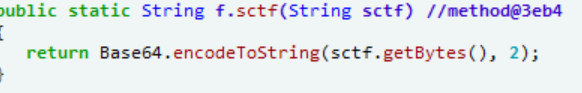
找到调用的位置
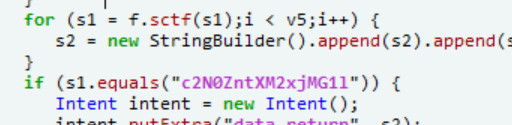
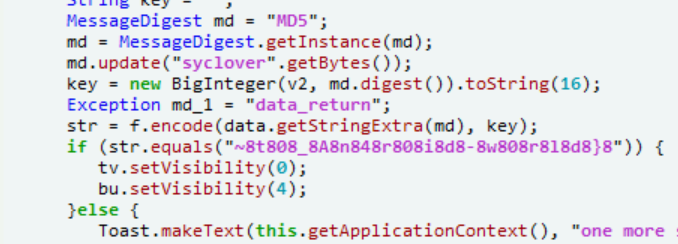
出题者大概是写错了%,只要把“8”去除就行了
[BSidesSF2019]blink
拖进GDA,main中没看到什么,在函数列表上翻翻
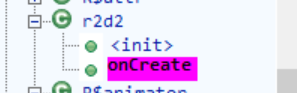
有个图片,解得flag