[2019红帽杯]easyRE
这题有点坑。。。
两次输入,第一次
a=[0x49,0x6f,0x64,0x6c,0x3e,0x51,0x6e,0x62,0x28,0x6f,0x63,0x79,0x7f,0x79,0x2e,0x69,0x7f,0x64,0x60,0x33,0x77,0x7d,0x77,0x65,0x6b,0x39,0x7b,0x69,0x79,0x3d,0x7e,0x79,0x4c,0x40,0x45,0x43]
for i in range(len(a)):
print(chr(a[i]^i),end="")
得到Info:The first four chars are `flag`
第二次是一个经过多次base64的密文,解密得https://bbs.pediy.com/thread-254172.htm
这文章看看,字里行间写满了坑人二字,也知道自己被带到沟里了,但如何找到正确的函数有点困难,在进行了两次输出后,fini里用了个sub_400D35
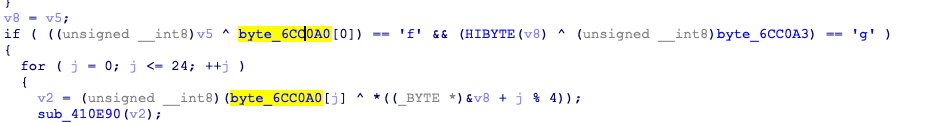
有f和g,结合第一次输入的提示,大概可猜到是这个函数
byte_6CC0A0=[0x40,0x35,0x20,0x56,0x5D,0x18,0x22,0x45,0x17,0x2F,0x24,0x6E,0x62,0x3C,0x27,0x54,0x48,0x6C,0x24,0x6E,0x72,0x3C,0x32,0x45,0x5B]
f="flag"
v5=[0,0,0,0]
b=[0x40,0x35,0x20,0x56]
flag=[]
for i in range(4):
v5[i]=b[i]^ord(f[i])
for i in range(len(byte_6CC0A0)):
flag.append(v5[i%4]^byte_6CC0A0[i])
for i in flag:
print(chr(i),end="")
得到flag
[SUCTF2019]SignIn
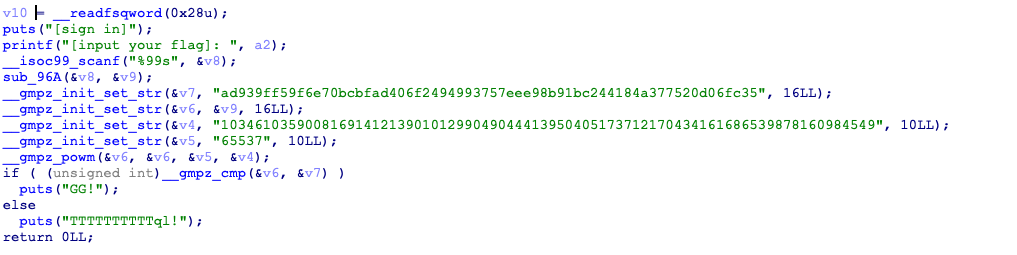
看到65537就大概可以猜到是rsa了,比较v6,v7,前面是一些字符串的赋值,给了n和e的值,v7是密文,v6为输入的明文
import gmpy2
import rsa
e=65537
n=103461035900816914121390101299049044413950405173712170434161686539878160984549
p=282164587459512124844245113950593348271
q=366669102002966856876605669837014229419
phin = (p-1) * (q-1)
d=gmpy2.invert(e, phin)
key=rsa.PrivateKey(n,e,int(d),p,q)
c=0xad939ff59f6e70bcbfad406f2494993757eee98b91bc244184a377520d06fc35
m=gmpy2.powmod(c,d,n)
print hex(m)[2:].decode('hex')
[GUET-CTF2019]re
elf,upx壳,脱壳后发现关键部分

体力活
flag = [] flag.append(166163712/1629056) flag.append(731332800/6771600) flag.append(357245568/3682944) flag.append(1074393000/10431000) flag.append(489211344/3977328) flag.append(518971936/5138336) flag.append(406741500/7532250) flag.append(294236496/5551632) flag.append(177305856/3409728) flag.append(650683500/13013670) flag.append(298351053/6088797) flag.append(386348487/7884663) flag.append(438258597/8944053) flag.append(249527520/5198490) flag.append(445362764/4544518) flag.append(981182160/10115280) flag.append(174988800/3645600) flag.append(493042704/9667504) flag.append(257493600/5364450) flag.append(767478780/13464540) flag.append(312840624/5488432) flag.append(1404511500/14479500) flag.append(316139670/6451830) flag.append(619005024/6252576) flag.append(372641472/7763364) flag.append(373693320/7327320) flag.append(498266640/8741520) flag.append(452465676/8871876) flag.append(208422720/4086720) flag.append(515592000/9374400) flag.append(719890500/5759124) for i in range(len(flag)): print(chr(int(flag[i])),end="") print(len(flag))
注:这里少给了一位a[6]=1
[FlareOn4]login
emm,给了个网页,可看见关键代码为
document.getElementById("prompt").onclick = function () { var flag = document.getElementById("flag").value; var rotFlag = flag.replace(/[a-zA-Z]/g, function(c){return String.fromCharCode((c <= "Z" ? 90 : 122) >= (c = c.charCodeAt(0) + 13) ? c : c - 26);}); if ("PyvragFvqrYbtvafNerRnfl@syner-ba.pbz" == rotFlag) { alert("Correct flag!"); } else { alert("Incorrect flag, rot again"); } }
就是一个移13位的加密,按凯撒密码解就行,得到ClientSideLoginsAreEasy@flare-on.com
[GWCTF 2019]xxor
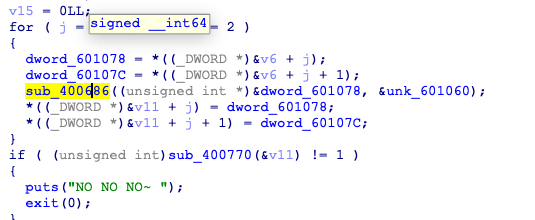
输入6个数,在加密后在sub_400770进行验证
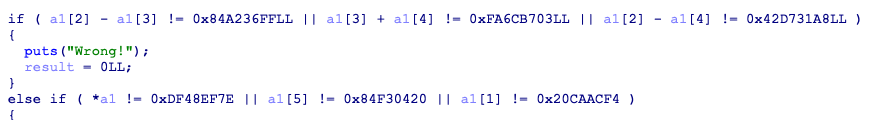
from z3 import*
f=Solver()
x=[Int('x%d'%i) for i in range(6)]
f.add(x[1] == 0x20CAACF4)
f.add(x[5] == 0x84F30420)
f.add(x[0] == 0xDF48EF7E)
f.add(x[2] - x[3] == 0x84A236FF)
f.add(x[3] + x[4] == 0xFA6CB703)
f.add(x[2] - x[4] == 0x42D731A8)
if f.check() == sat:
for i in range(6):
print(hex(f.model()[x[i]].as_long()))
得到加密后的数据
再看加密部分

可以看出这应该是个魔改过的TEA
#include <stdint.h>
void decipher(unsigned int num_rounds, uint32_t v[2], uint32_t const key[4]) {
unsigned int i;
uint32_t v0=v[0], v1=v[1], delta=0x458BCD42, sum=delta*num_rounds;
for (i=0; i < num_rounds; i++) {
v1 -= (v0+sum+20)^((v0<<6)+key[2])^((v0>>9)+key[3])^0x10;
v0 -= (v1+sum+11)^((v1<<6)+key[0])^((v1 >> 9)+key[1])^0x20;
sum -= delta;
}
v[0]=v0; v[1]=v1;
}
int main() {
uint32_t v[3][2]={0xdf48ef7e,0x20caacf4,0xe0f30fd5,0x5c50d8d6,0x9e1bde2d,0x84f30420};
uint32_t const k[4]={2,2,3,4};
unsigned int r=64;
for(int i=0;i<3;i++){
decipher(r, v[i], k);
printf("%u 解密后的数据:%x %x
",r,v[i][0],v[i][1]);
}
return 0;
}
再转为字符串
def hex_str(x):
temp=''
for i in range(len(x)//2):
temp+=chr(int(x[2*i:2*i+2],16))
return temp
a = ["666c61","677b72","655f69","735f67","726561","74217d"]
for i in range(6):
print(hex_str(a[i]),end="")
得到flag
[ACTF新生赛2020]usualCrypt
改了表的base64
a="A B C D E F G H I J K L M N O P Q R S T U V W X Y Z a b c d e f g h i j k l m n o p q r s t u v w x y z 0 1 2 3 4 5 6 7 8 9 + /"
a=a.split()
for i in range(6,15):
temp = a[i+10]
a[i+10] = a[i]
a[i] = temp
for i in range(len(a)):
print(a[i],end="")
得到改后的表
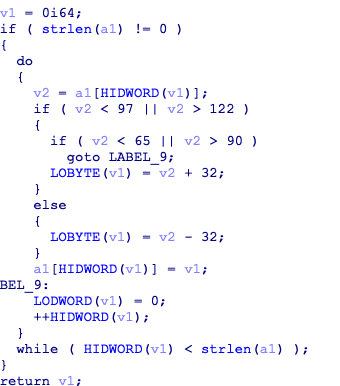
此处又进行了大小写转换,将密文转换后求base64得到flag
[HDCTF2019]Maze
简单的迷宫题
*******+********* ****** **** ******* **F****** **************
1111111211
1111111311
1111333311
1133311111
1131141111
1133331111
1111111111
//因为字体问题,改成了数字,由2开始到4结束,3为路1为墙
程序加了花,不能f5,不过也不需要,直接动调得到输入为wasd,走一遍得到flag
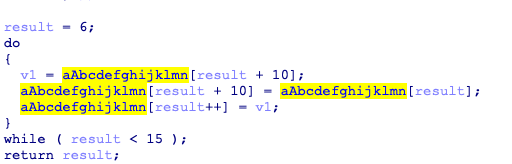
[BJDCTF2020]JustRE
搜索字符串
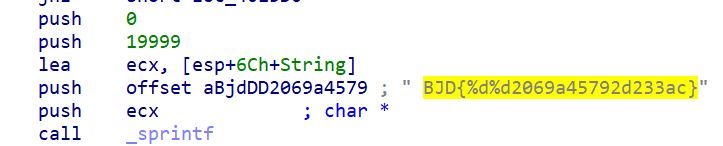
sprintf("bjd{%d%d2069a45792d233ac}",19999,0)
得到flag
[V&N2020 公开赛]strangeCpp
看字符串找到主函数,找到一段数据
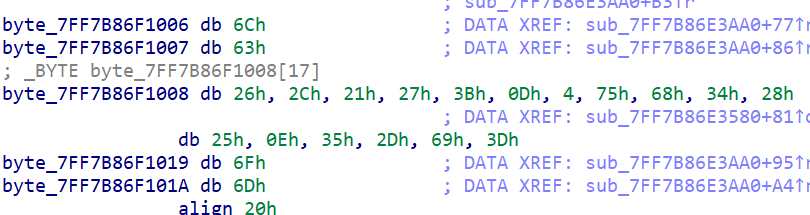
插了一段数组,找到调用
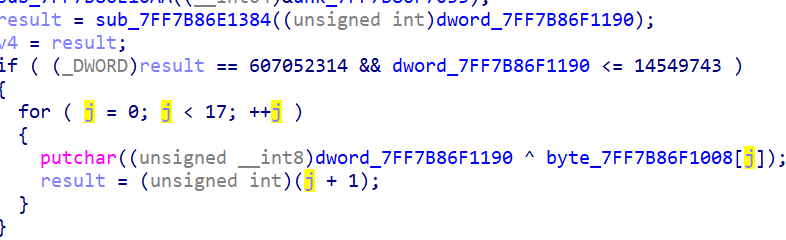
不知道dword_7FF7B86F1190的值,在sub_7FF7B86E1384中

可根据result爆破得到dword_7FF7B86F1190
# -*- coding:utf-8 -*-
a=[0x26,0x2C,0x21,0x27,0x3B,0x0D,0x04,0x75,0x68,0x34,0x28,0x25,0x0E,0x35,0x2D,0x69,0x3D]
result=607052314
n=0
for i in range(14549743):
v=(((i<<8)^(i>>12))*291)&0xffffffff
n=i
if(v==result):
print(str(i))
break
for i in range(17):
print(chr((a[i]^n)&0xff),end="")
得到
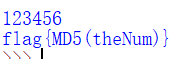
[ACTF新生赛2020]easyre
upx,脱壳后托入ida
逻辑十分简单,输入{}里作为索引替换表
# -*- coding:utf-8 -*-
table="~}|{zyxwvutsrqponmlkjihgfedcba`_^][ZYXWVUTSRQPONMLKJIHGFEDCBA@?>=<;:9876543210/.-,+*)('&%$# !""
cmp="*F'"N,"(I?+@"
flag=""
print(len(cmp))
for i in range(len(cmp)):
for j in range(len(table)):
if(cmp[i]==table[j]):
print(chr(j+1),end="")
continue
#ACTF{U9X_1S_W6@T?}
emmm所以他给的另一个文件是啥
[ACTF新生赛2020]rome
没啥可说的
a="Qsw3sj_lz4_Ujw@l"
for j in range(len(a)):
for i in range(48,123):
if(i<90 and i>64):
t=(i-51)%26+65
if(ord(a[j])==t):
print(chr(i),end="")
break
elif(i>96):
t=(i-79)%26+97
if(ord(a[j])==t):
print(chr(i),end="")
break
else:
if(i==ord(a[j])):
print(chr(i),end="")
break
[MRCTF2020]Transform
还是没啥可说的题,先换顺序再异或
a="67 79 7B 7F 75 2B 3C 52 53 79 57 5E 5D 42 7B 2D 2A 66 42 7E 4C 57 79 41 6B 7E 65 3C 5C 45 6F 62 4D"
b="09 0A 0F 17 07 18 0C 06 01 10 03 11 20 1D 0B 1E 1B 16 04 0D 13 14 15 02 19 05 1F 08 12 1A 1C 0E 00"
flag=[]
a=a.split()
b=b.split()
for i in range(len(a)):
t="0x"+a[i]
a[i]=eval(t)
t="0x"+b[i]
b[i]=eval(t)
for i in range(len(a)):
a[i]=(a[i]^b[i])
for i in range(len(a)):
flag.append(0)
for i in range(len(a)):
flag[b[i]]=a[i]
for i in range(len(a)):
print(chr(flag[i]),end="")
[MRCTF2020]Xor
依然没啥可说的,直接异或
a="MSAWB~FXZ:J:`tQJ"N@ bpdd}8g"
for i in range(len(a)):
print(chr(ord(a[i])^i),end="")
[WUSTCTF2020]Cr0ssfun
没啥可说的,拼字符串
[WUSTCTF2020]level3
在init_array里base64换表,不过给了O_OLookAtYou就没什么意思了
[ACTF新生赛2020]Universe_final_answer
直接z3
from z3 import *
v1,v2,v3,v4,v5,v6,v7,v8,v9,v11=BitVecs('v1 v2 v3 v4 v5 v6 v7 v8 v9 v11',16)
f=Solver()
f.add(-85 * v9 + 58 * v8 + 97 * v6 + v7 + -45 * v5 + 84 * v4 + 95 * v2 - 20 * v1 + 12 * v3 == 12613)
f.add(30 * v11 + -70 * v9 + -122 * v6 + -81 * v7 + -66 * v5 + -115 * v4 + -41 * v3 + -86 * v1 - 15 * v2 - 30 * v8 == -54400)
f.add(-103 * v11 + 120 * v8 + 108 * v7 + 48 * v4 + -89 * v3 + 78 * v1 - 41 * v2 + 31 * v5 - (v6 << 6) - 120 * v9 == -10283)
f.add(71 * v6 + (v7 << 7) + 99 * v5 + -111 * v3 + 85 * v1 + 79 * v2 - 30 * v4 - 119 * v8 + 48 * v9 - 16 * v11 == 22855)
f.add(5 * v11 + 23 * v9 + 122 * v8 + -19 * v6 + 99 * v7 + -117 * v5 + -69 * v3 + 22 * v1 - 98 * v2 + 10 * v4 == -2944)
f.add(-54 * v11 + -23 * v8 + -82 * v3 + -85 * v2 + 124 * v1 - 11 * v4 - 8 * v5 - 60 * v7 + 95 * v6 + 100 * v9 == -2222)
f.add(-83 * v11 + -111 * v7 + -57 * v2 + 41 * v1 + 73 * v3 - 18 * v4 + 26 * v5 + 16 * v6 + 77 * v8 - 63 * v9 == -13258)
f.add(81 * v11 + -48 * v9 + 66 * v8 + -104 * v6 + -121 * v7 + 95 * v5 + 85 * v4 + 60 * v3 + -85 * v2 + 80 * v1 == -1559)
f.add(101 * v11 + -85 * v9 + 7 * v6 + 117 * v7 + -83 * v5 + -101 * v4 + 90 * v3 + -28 * v1 + 18 * v2 - v8 == 6308)
f.add(99 * v11 + -28 * v9 + 5 * v8 + 93 * v6 + -18 * v7 + -127 * v5 + 6 * v4 + -9 * v3 + -93 * v1 + 58 * v2 == -1697)
if f.check() == sat:
print(f.model())