ELK - X-Pack设置用户密码
enable X-Pack security
vi elasticsearch.yml
#首先开启x-pack插件
xpack.security.enabled: true
xpack.security.transport.ssl.enabled: true
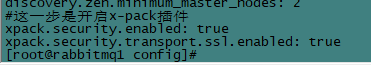
SSL也要同时enable,否则报错。
[2019-10-10T15:11:09,630][ERROR][o.e.b.Bootstrap ] [appserver01] node validation exception
[1] bootstrap checks failed
[1]: Transport SSL must be enabled if security is enabled on a [basic] license. Please set [xpack.security.transport.ssl.enabled] to [true] or disable security by setting [xpack.security.enabled] to [false]
# 进入容器
Docker exec -it id bash
cd bin
elasticsearch-setup-passwords interactive
[root@f18d8bc7b8f5 elasticsearch]# cd bin
[root@f18d8bc7b8f5 bin]# ls
elasticsearch elasticsearch-croneval elasticsearch-migrate elasticsearch-setup-passwords elasticsearch-syskeygen x-pack-watcher-env
elasticsearch-certgen elasticsearch-env elasticsearch-node elasticsearch-shard elasticsearch-users
elasticsearch-certutil elasticsearch-env-from-file elasticsearch-plugin elasticsearch-sql-cli x-pack-env
elasticsearch-cli elasticsearch-keystore elasticsearch-saml-metadata elasticsearch-sql-cli-7.6.2.jar x-pack-security-env
[root@f18d8bc7b8f5 bin]# elasticsearch-setup-passwords interactive #此步为手动设置密码
Initiating the setup of passwords for reserved users elastic,apm_system,kibana,logstash_system,beats_system,remote_monitoring_user.
You will be prompted to enter passwords as the process progresses.
Please confirm that you would like to continue [y/N]y
#在这里设置密码,注意最少六位,下面也一样可以看到Elasticsearch预置了许多角色和用户。
Enter password for [elastic]:
Reenter password for [elastic]:
Passwords do not match.
Try again.
Enter password for [elastic]:
Reenter password for [elastic]:
Enter password for [apm_system]:
Reenter password for [apm_system]:
Enter password for [kibana]:
Reenter password for [kibana]:
Enter password for [logstash_system]:
Reenter password for [logstash_system]:
Enter password for [beats_system]:
Reenter password for [beats_system]:
Enter password for [remote_monitoring_user]:
Reenter password for [remote_monitoring_user]:
Changed password for user [apm_system]
Changed password for user [kibana]
Changed password for user [logstash_system]
Changed password for user [beats_system]
Changed password for user [remote_monitoring_user]
Changed password for user [elastic]
[root@f18d8bc7b8f5 bin]# Ctrl+D 退出容器
重启容器
docker restart ******
默认用户名是elastic

如果用到Kibana ,则做如下设置
sudo vi /etc/kibana/kibana.yml
# sudo vi /etc/heartbeat/heartbeat.yml
elasticsearch.username: "elastic"
elasticsearch.password: "<password>"
sudo systemctl restart kibana.service
Or change data in Elasticsearch directly.
POST /_security/user/elastic/_password
{
"password": "admindev123$%^"
}
如果你要重新修改密码
这里会让你输入旧的密码即可
curl -H "Content-Type:application/json" -XPOST -u elastic 'http://47.254.19.211:9200/_xpack/security/user/elastic/_password' -d '{ "password" : "admindev123$%^" }'
要利用这个漏洞,最重要的就是查看数据,下面是elasticsearch基本的查询方法
2.1 查询所有的 index, type:
$ curl localhost:9200/_search?pretty=true
2.2 查询某个index下所有的type:
$ curl localhost:9200/films/_search
2.3 查询某个index 下, 某个 type下所有的记录:
$ curl localhost:9200/films/md/_search?pretty=true
2.4 带有参数的查询:
$ curl localhost:9200/films/md/_search?q=tag:good
{"took":7,"timed_out":false,"_shards":{"total":5,"successful":5,"failed":0},"hits":{"total":2,"max_score":1.0,"hits":[{"_index":"film","_type":"md","_id":"2","_score":1.0, "_source" :
{ "name":"hei yi ren", "tag": "good"}},{"_index":"film","_type":"md","_id":"1","_score":0.30685282, "_source" :
{ "name":"ma da jia si jia", "tag": "good"}}]}}
2.5 使用JSON参数的查询: (注意 query 和 term 关键字)
$ curl localhost:9200/film/_search -d '
{"query" : { "term": { "tag":"bad"}}}'
实战记录
1,直接访问该ip的9200端口,如下:
2,http://ip:9200/_cat/indices获取所有的index
3,http://ip:9200/_mapping?pretty=true 获取index下的所有type
4,http://ip:9200/pv_fun_all/school/_search?pretty=true 获取该index下该type下的内容