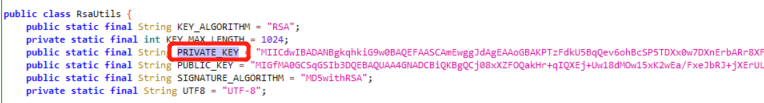
一、抓包分析

二、用jadx-gui打开
因没有加壳,所以可直接打开app分析
搜索关键字
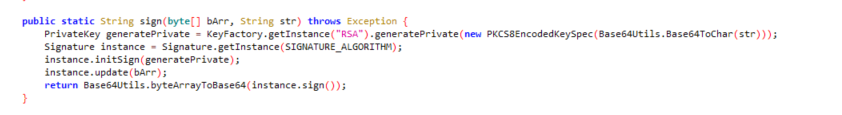
三、hook方法
上frida,hook RSA
frida脚本如下
hook.js
Java.perform(function () {
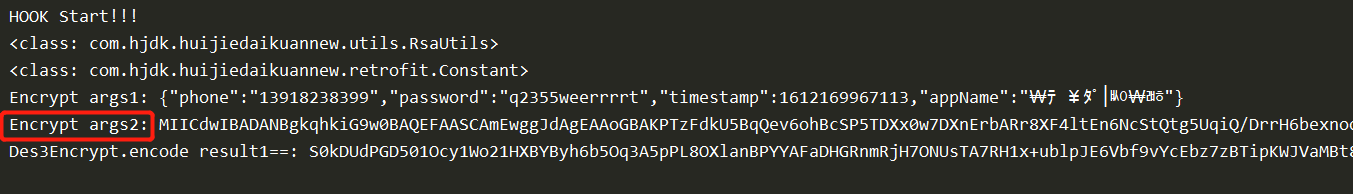
console.log('HOOK Start!!!');
var Des3Encrypt = Java.use("com.hjdk.huijiedaikuannew.utils.RsaUtils");
console.log(Des3Encrypt);
// 加密
Des3Encrypt.sign.overload('[B', 'java.lang.String').implementation = function (args1,args2) {
console.log("Encrypt args1:",Uint8ArrayToString(args1));
console.log("Encrypt args2:",args2);
// console.log("Encrypt args3:",args3);
//console.log("Encrypt args4:",args4);
var result1 = this.sign(args1,args2);
console.log("Des3Encrypt.encode result1==:", result1);
return result1;
};
});
python 脚本
import logging
import frida
import sys
logging.basicConfig(level=logging.DEBUG)
def on_message(message, data):
print(message)
with open('hook.js', 'r', encoding='utf-8') as f:
sta = ''.join(f.readlines())
rdev = frida.get_remote_device()
processes = rdev.enumerate_processes() # 安卓手机中的所有进程
# print(processes)
session = rdev.attach("com.hjdk.huijiedaikuannew")
# print(session)
script = session.create_script(sta)
script.on("message", on_message)
script.load()
sys.stdin.read()
四、hook结果
Encrypt args2 是 PRIVATE_KEY
PRIVATE_KEY = "MIICdwIBADANBgkqhkiG9w0BAQEFAASCAmEwggJdAgEAAoGBAKPTzFdkU5BqQev6ohBcSP5TDXx0w7DXnErbARr8XF4ltEn6NcStQtg5UqiQ/DrrH6bexnooVkBSy4fAAzY1G7Q5YVWs9pm13fJe38xXi4PlKbYciqvQq0K5sUr9IOovK6hQyb32E+Fz7NpGKZdb16nIzHYF0fdX9sCuN3VkCXbrAgMBAAECgYAmQu70ch/6GHbw8AYtoAAENc1uha62fISqDuABN3MzIccrh95K4tQ7v5eIeuQNtqAbzue32/fY6f1S5Qta+6hOXPOb7GKavnr1hAnJ5XFQmtpVpmzaNmUH0bkFAEcIzVfFBiHweAOHf7wtyGplDChdhgu9Mu+G7XyBrbAay0CRYQJBAOMyCIZObPOGG9KFY3GD+ctw55k/cqfEV+E4LNo9+o2keee2OWcDFavqTVyD3qDeN3S+mNn0dvbjeqxLfZtR/IMCQQC4mQ7/z8MJOwlxozM5AD8RNautgCHKSDBpM4cVZ7fcqOTJXYjf8zM5UExoypfwcFYn4LfDDSNNP5OTtF1I8d95AkAoFAZu8tzDZM/5pjAxsS9alRM19HxcXgWGpGs9IJvXasFaf8nGg0PKbO2yuUyHoku0G39JS5fE28IjLLn+sUrTAkEAhqHrFJu8zaCnNKAonawWU0DnozTOcC/STwfrv6rTqDXuFwcG6v7/Hw/3in4n7o6f55m3rKSKWK7DvXhQiQEPUQJBAMLqGejiiH9E18hDvDROp/KtaceqT7GFc0izJZ8Z9iUFWmAJVo3gy0CIvyvbjOPCTfm3QC8bI1/l7+zuFtKj9yQ="