2019-01-02 14:14:45,161 ERROR [HiveServer2-Handler-Pool: Thread-37]: transport.TSaslTransport (TSaslTransport.java:open(315)) - SASL negotiation failure javax.security.sasl.SaslException: GSS initiate failed [Caused by GSSException: Failure unspecified at GSS-API level (Mechanism level: Specified version of key is not available (44))] at com.sun.security.sasl.gsskerb.GssKrb5Server.evaluateResponse(GssKrb5Server.java:177) at org.apache.thrift.transport.TSaslTransport$SaslParticipant.evaluateChallengeOrResponse(TSaslTransport.java:539) at org.apache.thrift.transport.TSaslTransport.open(TSaslTransport.java:283) at org.apache.thrift.transport.TSaslServerTransport.open(TSaslServerTransport.java:41) at org.apache.thrift.transport.TSaslServerTransport$Factory.getTransport(TSaslServerTransport.java:216) at org.apache.hadoop.hive.thrift.HadoopThriftAuthBridge$Server$TUGIAssumingTransportFactory$1.run(HadoopThriftAuthBridge.java:739) at org.apache.hadoop.hive.thrift.HadoopThriftAuthBridge$Server$TUGIAssumingTransportFactory$1.run(HadoopThriftAuthBridge.java:736) at java.security.AccessController.doPrivileged(Native Method) at javax.security.auth.Subject.doAs(Subject.java:356) at org.apache.hadoop.security.UserGroupInformation.doAs(UserGroupInformation.java:1673) at org.apache.hadoop.hive.thrift.HadoopThriftAuthBridge$Server$TUGIAssumingTransportFactory.getTransport(HadoopThriftAuthBridge.java:736) at org.apache.thrift.server.TThreadPoolServer$WorkerProcess.run(TThreadPoolServer.java:268) at java.util.concurrent.ThreadPoolExecutor.runWorker(ThreadPoolExecutor.java:1145) at java.util.concurrent.ThreadPoolExecutor$Worker.run(ThreadPoolExecutor.java:615) at java.lang.Thread.run(Thread.java:745) Caused by: GSSException: Failure unspecified at GSS-API level (Mechanism level: Specified version of key is not available (44)) at sun.security.jgss.krb5.Krb5Context.acceptSecContext(Krb5Context.java:788) at sun.security.jgss.GSSContextImpl.acceptSecContext(GSSContextImpl.java:342) at sun.security.jgss.GSSContextImpl.acceptSecContext(GSSContextImpl.java:285) at com.sun.security.sasl.gsskerb.GssKrb5Server.evaluateResponse(GssKrb5Server.java:155) ... 14 more Caused by: KrbException: Specified version of key is not available (44) at sun.security.krb5.EncryptionKey.findKey(EncryptionKey.java:588) at sun.security.krb5.KrbApReq.authenticate(KrbApReq.java:270) at sun.security.krb5.KrbApReq.<init>(KrbApReq.java:144) at sun.security.jgss.krb5.InitSecContextToken.<init>(InitSecContextToken.java:108) at sun.security.jgss.krb5.Krb5Context.acceptSecContext(Krb5Context.java:771) ... 17 more
先贴个比较搞笑的错误
这个错误字面上意思是说, Specified version of key is not available,指定版本的key不可用,我就奇了怪了我哪里指定key了,找度娘帮忙,找到一个貌似解释还可以的答案:https://stackoverflow.com/questions/24511812/krbexception-specified-version-of-key-is-not-available-44
答案:
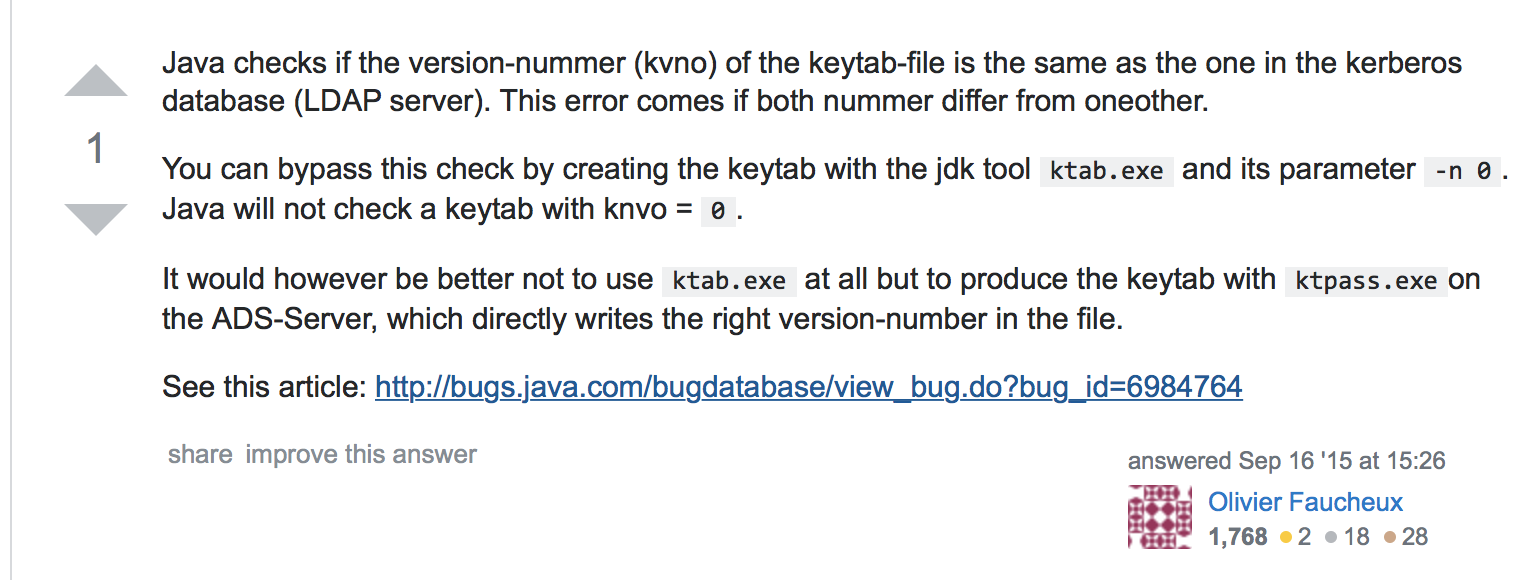
意思是说,keytab文件的版本号和kerberos中的版本号不一致导致的,需要在创建keytab文件时加上参数跳过该检查.我去实验了这个办法,在服务端和客户端比对keytab版本号,直到一直,然并卵还是报这个错误,直到我打开debug日志,才发现原因并不是这样子的.
打开debug日志只要修改日志文件就好了:
vi apache-hive-1.2.0-bin/conf/hive-log4j.properties
改为debug,就会发现有一个提示:在说验证的kerberos用户不同,最后证明是我的连接串写错了:
jdbc连接串:
jdbc:hive2://10.1.4.32:10000/default;principal=udap/host32@STA.COM
beeline连接串:
!connect jdbc:hive2://10.1.4.32:10000/default;principal=udap/host32@STA.COM
我的错误在于把连接串的后面principle当做了自定义用户,比如:
!connect jdbc:hive2://10.1.4.32:10000/default;principal=garfield/host32@STA.COM
这样子就会报上面那个错
done