1.和社区版Istio的区别
OpenShift 4.2的Service Mesh和upstream的Istio项目的增强,除了产品化之外,借用官方文档,区别在于:
Red Hat OpenShift Service Mesh differs from Istio in ways that help resolve issues, provide additional features, and ease deployment on OpenShift Container Platform. An installation of Red Hat OpenShift Service Mesh differs from upstream Istio community installations in multiple ways:
-
OpenShift Service Mesh installs a multi-tenant control plane by default
-
OpenShift Service Mesh extends Role Based Access Control (RBAC) features
-
OpenShift Service Mesh replaces BoringSSL with OpenSSL
-
Kiali and Jaeger are enabled by default in OpenShift Service Mesh
关于istio多租户的架构和功能参考
https://blog.openshift.com/istio-multicluster-on-openshift/
2.架构

各个模块功能不再熬述。
3.安装和部署
- 基于OperatorHub部署service mesh,部署顺序为:elasticsearch Operator->Jaeger Opeartor->Kiali Operator->OpenShift Service Mesh Operator->OpenShift Service Mesh Controller Plane
详细可以参考
- 部署完control plane后,会在istio-system下生成如下Pod
[root@clientvm 0 ~]# oc get pods -n istio-system
NAME READY STATUS RESTARTS AGE
grafana-b67df64b6-2kp7h 2/2 Running 0 2d23h
istio-citadel-79979464d-kxpxw 1/1 Running 0 2d23h
istio-egressgateway-7d897695c4-c868b 1/1 Running 0 2d23h
istio-galley-6bb46858c5-pf476 1/1 Running 0 2d23h
istio-ingressgateway-8465bbf788-j9jgk 1/1 Running 0 2d23h
istio-pilot-54b65495c4-4tg6m 2/2 Running 0 2d23h
istio-policy-5fc74b8697-mk85l 2/2 Running 0 2d23h
istio-sidecar-injector-65cd4c8c6f-cnp5t 1/1 Running 0 2d23h
istio-telemetry-69cb778b9-qlpqj 2/2 Running 0 2d23h
jaeger-57776787bc-ljls5 2/2 Running 0 2d23h
kiali-6d6f9cf658-kzdwf 1/1 Running 0 2d1h
prometheus-b8bdc6b77-rbxzs 2/2 Running 0 2d23h
和下面的服务
[root@clientvm 0 ~]# oc get svc -n istio-system
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
grafana ClusterIP 172.30.124.97 <none> 3000/TCP 2d23h
istio-citadel ClusterIP 172.30.122.114 <none> 8060/TCP,15014/TCP 2d23h
istio-egressgateway ClusterIP 172.30.60.175 <none> 80/TCP,443/TCP,15443/TCP 2d23h
istio-galley ClusterIP 172.30.167.213 <none> 443/TCP,15014/TCP,9901/TCP 2d23h
istio-ingressgateway ClusterIP 172.30.221.247 <none> 15020/TCP,80/TCP,443/TCP,15443/TCP 2d23h
istio-pilot ClusterIP 172.30.19.129 <none> 15010/TCP,15011/TCP,8080/TCP,15014/TCP 2d23h
istio-policy ClusterIP 172.30.99.48 <none> 9091/TCP,15004/TCP,15014/TCP 2d23h
istio-sidecar-injector ClusterIP 172.30.102.34 <none> 443/TCP 2d23h
istio-telemetry ClusterIP 172.30.229.205 <none> 9091/TCP,15004/TCP,15014/TCP,42422/TCP 2d23h
jaeger-agent ClusterIP None <none> 5775/TCP,5778/TCP,6831/TCP,6832/TCP 2d23h
jaeger-collector ClusterIP 172.30.66.202 <none> 9411/TCP,14250/TCP,14267/TCP,14268/TCP 2d23h
jaeger-collector-headless ClusterIP None <none> 9411/TCP,14250/TCP,14267/TCP,14268/TCP 2d23h
jaeger-query ClusterIP 172.30.84.61 <none> 443/TCP 2d23h
kiali NodePort 172.30.55.80 <none> 20001:31380/TCP 2d23h
prometheus ClusterIP 172.30.122.232 <none> 9090/TCP 2d23h
zipkin ClusterIP 172.30.189.90 <none> 9411/TCP 2d23h
查看对外暴露的路由
[root@clientvm 0 ~]# oc get route -n istio-system
NAME HOST/PORT PATH SERVICES PORT TERMINATION WILDCARD
grafana grafana-istio-system.apps.cluster-4674.sandbox580.opentlc.com grafana <all> reencrypt None
istio-ingressgateway istio-ingressgateway-istio-system.apps.cluster-4674.sandbox580.opentlc.com istio-ingressgateway 8080 None
jaeger jaeger-istio-system.apps.cluster-4674.sandbox580.opentlc.com jaeger-query <all> reencrypt None
kiali kiali-istio-system.apps.cluster-4674.sandbox580.opentlc.com kiali <all> reencrypt None
prometheus prometheus-istio-system.apps.cluster-4674.sandbox580.opentlc.com prometheus <all> reencrypt None
值得注意的是instio-ingressgateway这个路由是OpenShift Service Mesh暴露给外端访问的路由。也就是通过这个唯一的链接,调用接入到Service Mesh服务网格。
基于Operator的安装和部署确实使得整个过程方便不少,但也封装了很多的架构的细节了,所以我们所需要做的就是对架构更加了解。
4.使用
部署完成sample的bookinfo项目以后,再部署一个自己的简单的tomcat服务。
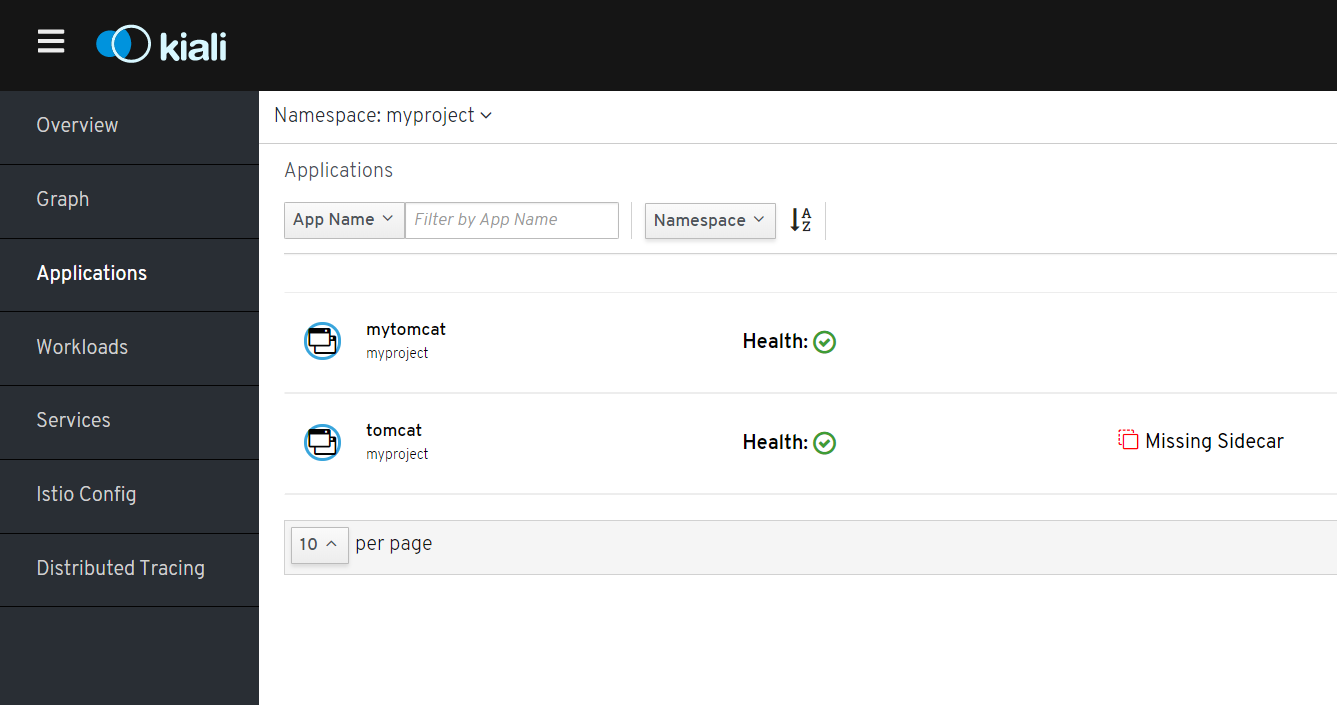
登录Kiali Console. myproject下面看到mytomcat情况
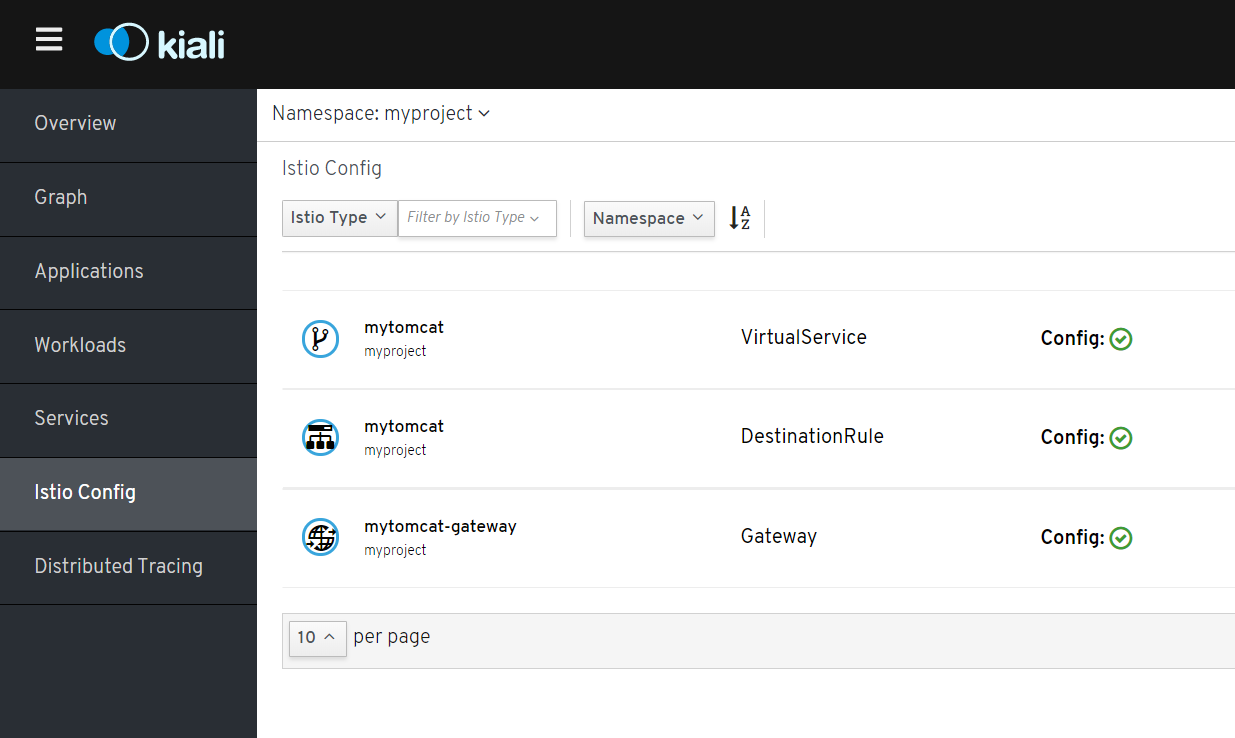
访问istio config,查看virtualservice mytomcat内容

然后访问发现访问不通。原本的想法是,如果uri是/mytomcat的化,就路由到mytomcat服务,结果出现的结果是:
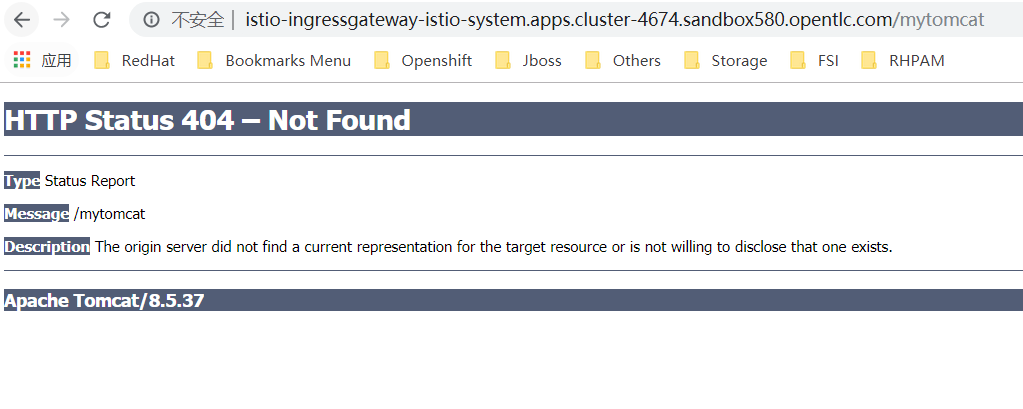
经过排查发现是virtualservice的路径问题。(因为对架构不熟悉,耗费了4,5小时啊...)
kind: VirtualService
apiVersion: networking.istio.io/v1alpha3
metadata:
name: mytomcat
namespace: myproject
selfLink: >-
/apis/networking.istio.io/v1alpha3/namespaces/myproject/virtualservices/mytomcat
uid: 834c4724-0812-11ea-b3a1-0a1bba0ac472
resourceVersion: '1631674'
generation: 8
creationTimestamp: '2019-11-16T01:43:39Z'
spec:
hosts:
- '*'
gateways:
- mytomcat-gateway
http:
- match:
- uri:
exact: /
route:
- destination:
host: mytomcat
port:
number: 8080
注意这个uri的配置,gateway会拼接uri,也就是/到你的service的路径,如果你填入mytomcat,其实真实访问路径是http://mytomcat:8080/mytomcat,就会出现找不到应用的状况。
再度访问 http://istio-ingressgateway-istio-system.apps.cluster-4674.sandbox580.opentlc.com/ 也就是根目录啦

发现图片没有出来。:(