Xx_Instroduction
- Ettercap is a man-in-the-middle attack(MITM) tool,kali take this tool,so,use front we are need configuration that configuration file.

Ax_Open
- vi /etc/ettercap/etter.conf

-
1 ############################################################################ 2 ## 3 # ettercap -- etter.conf -- configuration file # 4 # # 5 # Copyright (C) ALoR & NaGA # 6 # # 7 # This program is free software; you can redistribute it and/or modify # 8 # it under the terms of the GNU General Public License as published by # 9 # the Free Software Foundation; either version 2 of the License, or # 10 # (at your option) any later version. # 11 # # 12 # # 13 ############################################################################ 14 15 [privs] 16 ec_uid = 0 #nobody is the default 17 #haha userid and groupid gaiwei 0 18 ec_gid = 0 # nobody is the default 19 20 [mitm] 21 arp_storm_delay = 10 # milliseconds 22 arp_poison_smart = 0 # boolean 23 arp_poison_warm_up = 1 # seconds 24 arp_poison_delay = 10 # seconds 25 arp_poison_icmp = 1 # boolean 26 arp_poison_reply = 1 # boolean 27 arp_poison_request = 0 # boolean 28 arp_poison_equal_mac = 1 # boolean 29 dhcp_lease_time = 1800 # seconds 30 port_steal_delay = 10 # seconds 31 port_steal_send_delay = 2000 # microseconds 32 ndp_poison_warm_up = 1 # seconds 33 ndp_poison_delay = 5 # seconds 34 ndp_poison_send_delay = 1500 # microseconds 35 ndp_poison_icmp = 1 # boolean 36 ndp_poison_equal_mac = 1 # boolean 37 icmp6_probe_delay = 3 # seconds 38 39 [connections] 40 connection_timeout = 300 # seconds 41 connection_idle = 5 # seconds 42 connection_buffer = 10000 # bytes 43 connect_timeout = 5 # seconds 44 45 [stats] 46 sampling_rate = 50 # number of packets 47 48 [misc] 49 close_on_eof = 1 # boolean value 50 store_profiles = 1 # 0 = disabled; 1 = all; 2 = local; 3 = remote 51 aggressive_dissectors = 1 # boolean value 52 skip_forwarded_pcks = 1 # boolean value 53 checksum_check = 0 # boolean value 54 submit_fingerprint = 0 # boolean valid (set if you want ettercap to submit unknown finger prints) 55 checksum_warning = 0 # boolean value (valid only if checksum_check is 1) 56 sniffing_at_startup = 1 # boolean value 57 58 ############################################################################ 59 # 60 # You can specify what DISSECTORS are to be enabled or not... 61 # 62 # e.g.: ftp = 21 enabled on port 21 (tcp is implicit) 63 # ftp = 2345 enabled on non standard port 64 # ftp = 21,453 enabled on port 21 and 453 65 # ftp = 0 disabled 66 # 67 # NOTE: some dissectors have multiple default ports, if you specify a new 68 # one, all the default ports will be overwritten 69 # 70 # 71 72 #dissector default port 73 74 [dissectors] 75 ftp = 21 # tcp 21 76 ssh = 22 # tcp 22 77 telnet = 23 # tcp 23 78 smtp = 25 # tcp 25 79 dns = 53 # udp 53 80 dhcp = 67 # udp 68 81 http = 80 # tcp 80 82 ospf = 89 # ip 89 (IPPROTO 0x59) 83 pop3 = 110 # tcp 110 84 #portmap = 111 # tcp / udp 85 vrrp = 112 # ip 112 (IPPROTO 0x70) 86 nntp = 119 # tcp 119 87 smb = 139,445 # tcp 139 445 88 imap = 143,220 # tcp 143 220 89 snmp = 161 # udp 161 90 bgp = 179 # tcp 179 91 ldap = 389 # tcp 389 92 https = 443 # tcp 443 93 ssmtp = 465 # tcp 465 94 rlogin = 512,513 # tcp 512 513 95 rip = 520 # udp 520 96 nntps = 563 # tcp 563 97 ldaps = 636 # tcp 636 98 telnets = 992 # tcp 992 99 imaps = 993 # tcp 993 100 ircs = 994 # tcp 993 101 pop3s = 995 # tcp 995 102 socks = 1080 # tcp 1080 103 radius = 1645,1646 # udp 1645 1646 104 msn = 1863 # tcp 1863 105 cvs = 2401 # tcp 2401 106 mysql = 3306 # tcp 3306 107 icq = 5190 # tcp 5190 108 ymsg = 5050 # tcp 5050 109 mdns = 5353 # udp 5353 110 vnc = 5900,5901,5902,5903 # tcp 5900 5901 5902 5903 111 x11 = 6000,6001,6002,6003 # tcp 6000 6001 6002 6003 112 irc = 6666,6667,6668,6669 # tcp 6666 6667 6668 6669 113 gg = 8074 # tcp 8074 114 proxy = 8080 # tcp 8080 115 rcon = 27015,27960 # udp 27015 27960 116 ppp = 34827 # special case ;) this is the Net Layer code 117 TN3270 = 23,992 # tcp 23 992 118 119 # 120 # you can change the colors of the curses GUI. 121 # here is a list of values: 122 # 0 Black 4 Blue 123 # 1 Red 5 Magenta 124 # 2 Green 6 Cyan 125 # 3 Yellow 7 White 126 # 127 [curses] 128 color_bg = 0 129 color_fg = 7 130 color_join1 = 2 131 color_join2 = 4 132 color_border = 7 133 color_title = 3 134 color_focus = 6 135 color_menu_bg = 4 136 color_menu_fg = 6 137 color_window_bg = 4 138 color_window_fg = 7 139 color_selection_bg = 6 140 color_selection_fg = 6 141 color_error_bg = 1 142 color_error_fg = 3 143 color_error_border = 3 144 145 # 146 # This section includes all the configurations that needs a string as a 147 # parmeter such as the redirect command for SSL mitm attack. 148 # 149 [strings] 150 151 # the default encoding to be used for the UTF-8 visualization 152 utf8_encoding = "ISO-8859-1" 153 154 # the command used by the remote_browser plugin 155 remote_browser = "xdg-open http://%host%url" 156 157 158 ##################################### 159 # redir_command_on/off 160 ##################################### 161 # you must provide a valid script for your operating system in order to have 162 # the SSL dissection available 163 # note that the cleanup script is executed without enough privileges (because 164 # they are dropped on startup). so you have to either: provide a setuid program 165 # or set the ec_uid to 0, in order to be sure the cleanup script will be 166 # executed properly 167 # NOTE: the script must fit into one line with a maximum of 255 characters 168 169 #--------------- 170 # Linux 171 #--------------- 172 173 # if you use ipchains: 174 #redir_command_on = "ipchains -A input -i %iface -p tcp -s 0/0 -d 0/0 %port -j REDIRECT %rport" 175 #redir_command_off = "ipchains -D input -i %iface -p tcp -s 0/0 -d 0/0 %port -j REDIRECT %rport" 176 177 # if you use iptables: 178 redir_command_on = "iptables -t nat -A PREROUTING -i %iface -p tcp --dport %port -j REDIRECT --to-port %rport" 179 redir_command_off = "iptables -t nat -D PREROUTING -i %iface -p tcp --dport %port -j REDIRECT --to-port %rport" 180 181 #--------------- 182 # Mac Os X 183 #--------------- 184 185 # quick and dirty way: 186 #redir_command_on = "ipfw -q add set %set fwd 127.0.0.1,%rport tcp from any to any %port in via %iface" 187 #redir_command_off = "ipfw -q delete set %set" 188 189 # a better solution is to use a script that keeps track of the rules interted 190 # and then deletes them on exit: 191 192 # redir_command_on: 193 # ----- cut here ------- 194 # #!/bin/sh 195 # if [ -a "/tmp/osx_ipfw_rules" ]; then 196 # ipfw -q add head -n 1 osx_ipfw_rules fwd 127.0.0.1,1 tcp from any to any2 in via 3 197 # else 198 # ipfw add fwd 127.0.0.1,1 tcp from any to any 2 in via3 | cut -d " " -f 1 >> /tmp/osx_ipfw_rules 199 # fi 200 # ----- cut here ------- 201 202 # redir_command_off: 203 # ----- cut here ------- 204 # #!/bin/sh 205 # if [ -a "/tmp/osx_ipfw_rules" ]; then 206 # ipfw -q delete head -n 1 /tmp/osx_ipfw_rules 207 # rm -f /tmp/osx_ipfw_rules 208 # fi 209 # ----- cut here ------- 210 211 #--------------- 212 # FreeBSD 213 #--------------- 214 215 # Before OF can be used, make sure the kernel module has been loaded by 216 # kldstat | grep pf.ko. If the rusult is empty, you can load it by 217 # kldload pf.ko or add 'pf_enable="YES"' to the /etc/rc.conf and reboot. 218 219 # Check if the PF status is enabled by 220 # pfctl -si | grep Status | awk '{print $2;}'. If "Disabled", enable it with 221 # pfctl -e. 222 223 #redir_command_on = "(pfctl -sn 2> /dev/null; echo 'rdr pass on %iface inet proto tcp from any to any port %port -> localhost port %rport') | pfctl -f - 2> /dev/null" 224 #redir_command_off = "pfctl -Psn 2> /dev/null | grep -v %port | pfctl -f - 2> /dev/null" 225 226 227 #--------------- 228 # Open BSD 229 #--------------- 230 231 # unfortunately the pfctl command does not accepts direct rules adding 232 # you have to use a script which executed the following command: 233 234 # ----- cut here ------- 235 # #!/bin/sh 236 # rdr pass on 1 inet proto tcp from any to any port2 -> localhost port $3 | pfctl -a sslsniff -f - 237 # ----- cut here ------- 238 239 # it's important to remember that you need "rdr-anchor sslsniff" in your 240 # pf.conf in the TRANSLATION section. 241 242 #redir_command_on = "the_script_described_above %iface %port %rport" 243 #redir_command_off = "pfctl -a sslsniff -Fn" 244 245 # also, if you create a group called "pfusers" and have EC_GID be that group, 246 # you can do something like: 247 # chgrp pfusers /dev/pf 248 # chmod g+rw /dev/pf 249 # such that all users in "pfusers" can run pfctl commands; thus allowing non-root 250 # execution of redir commands. 251 252 253 ########## 254 # EOF # 255 ##########</pre>
Bx_Modificati
- Line 16 and line 18 will userid and groupid value instead 0

- Line 178 and line 179 do away with "#" ,in this way can pass iptables firewall function transmit part flow.
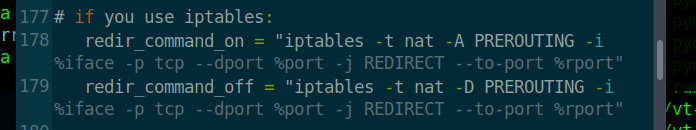
-
save,close,and ok